In this blog post, we are going to cover how to perform container
image scanning for CircleCI using Sysdig Secure. Image scanning allows DevOps teams to detect and resolve issues, like known vulnerabilities and incorrect configurations, directly in their CI/CD pipelines.
Using Sysdig Secure, you can enforce image policies to block vulnerabilities before they reach production environments and fix them faster while the developer still has the context.
Image scanning can detect problems like:
- No USER command specified which will cause the container to run as root.
- Use “latest” tagged base images that reduce the tracking of the built images.
- Unsafe Dockerfile instructions.
- Vulnerabilities in the base image OS.
- Vulnerabilities in the libraries your language is using (Python pip, Java JARs, Ruby gems, Javascript npm, etc)
- Compliance violations for the NIST 800-190 or PCI standards.
One of the unique benefits of Sysdig Secure inline scanning is that only the results will be sent to the Sysdig Secure backend, where you can review them and have a full tracking of vulnerabilities and configuration checks. Sysdig’s backend is available as SaaS or air-gapped in your own environment. With this approach, you won’t lose control over your images as they don’t need to be sent to the backend or exposed to any staging repository.
Sysdig Secure allows you to embed security and compliance into the build, run and respond stages of the Kubernetes lifecycle. This means using a single workflow to
scan for vulnerabilities and misconfigurations in your CI/CD pipeline but also
block threats at runtime using native Kubernetes controls, like PSPs. Additionally, Sysdig enables faster
incident response and container forensics.
Vulnerability scanning in CircleCI
CircleCI is a Continuous Integration and Continuous Delivery platform that allows teams to rapidly build quality projects by automating the build, test and delivery process. You can integrate other steps in this pipeline, like scanning the image before sending it to the container registry using Sysdig’s inline scanning.
CircleCI setup for image scanning with Sysdig Secure
In this example, you will create an OCI image with Docker, and CircleCI will trigger the scanning before sending the image to the container registry, preventing non-compliant images from reaching production.
Prerequisites for security scanning on CircleCI
To reproduce the following example, you will need the following:
- A CircleCI CI/CD pipeline and an account.
- A git repository for your pipeline with your application.
- A Sysdig Secure DevOps Platform account.
- A container repository (in this example we will use DockerHub).
Configuring the CircleCI project
A CircleCi project links together your code repository, the CI/CD pipeline, and some extra configuration. In CircleCI you first set your repository information, then you set up a project for a given repository.
If you logged into CircleCI using your GitHub account, you github repositories will already appear in the repositories list. You can then use the “Set Up Project” button to start working on your pipeline
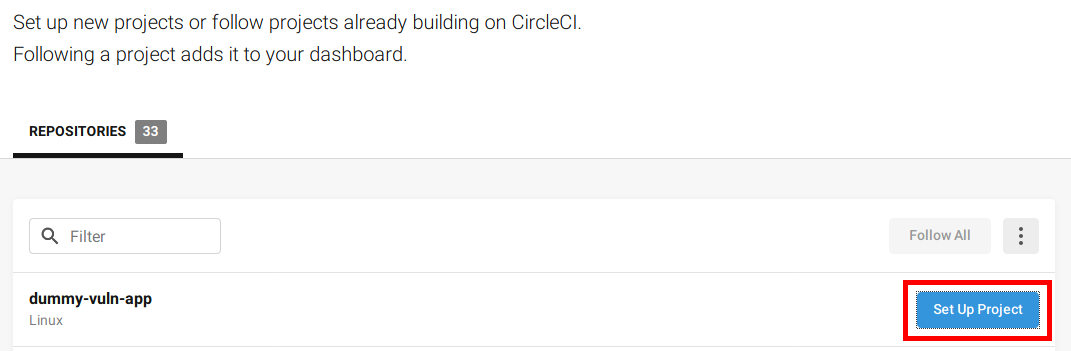
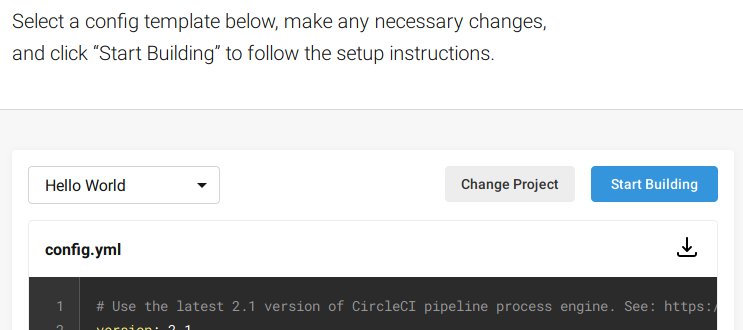
In the next screen you will see some pipeline templates, most of them work out of the box to build simple projects. In our case we will build a new pipeline from scratch.
CircleCI pipeline definition
We’re ready to define the pipeline we want to execute. You can edit it in CircleCI or create a file in your code repository in the folder .circleci/config.yml:
version: 2
jobs:
build:
machine: true
environment:
IMAGE_NAME: "sysdiglabs/dummy-vuln-app:latest"
SCAN_IMAGE_NAME: "sysdiglabs/secure-inline-scan:latest"
steps:
# checkout the source code
- checkout
# login
- run: |
docker login --username "$DOCKER_USER" --password "$DOCKER_PASS"
# build the application image
- run: docker build -t "$IMAGE_NAME" .
# scan the image
- run: docker run --rm -v /var/run/docker.sock:/var/run/docker.sock $SCAN_IMAGE_NAME -s https://secure.sysdig.com -k "$SYSDIG_SECURE_TOKEN" "$IMAGE_NAME"
# deploy the image
- run: docker push "$IMAGE_NAME"
Build stage
The image will be built using Docker, and the Dockerfile in the root of the repository, with the previously environment variable defined as “IMAGE_NAME”:
docker build -t "$IMAGE_NAME" .
Scanning stage
The vulnerability scanning will happen after the image has been built, and only if the build has been successful. The scanner is running inside a container as well to make it easy to scan anywhere:
docker run --rm \
-v /var/run/docker.sock:/var/run/docker.sock \
$SCAN_IMAGE_NAME \
analyze \
-s https://secure.sysdig.com \
-k "$SYSDIG_SECURE_TOKEN" \
"$IMAGE_NAME"
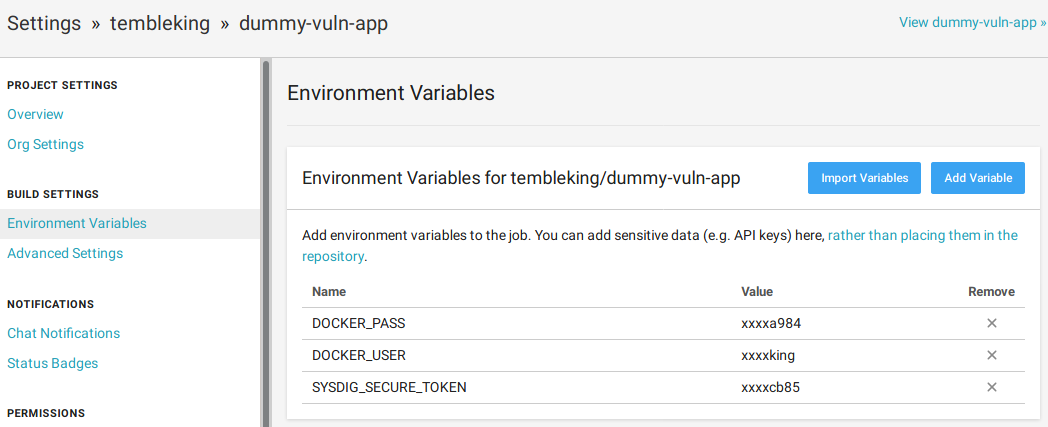
Configuring access credentials
Before starting the pipeline, we will define some environment variables (the container registry credentials and the Sysdig Secure API token) that will be referenced in the pipeline. Since these are credentials, we don’t want to save them in the code of the pipeline itself, and we want to avoid having them in the logs of the pipeline execution.
Pipeline execution for Image Scanning
The security scanning is completely done in the same runner the image was built, before it’s pushed to the registry and the results are sent to Sysdig Secure backend. Here, you can see the results of the image scanning:
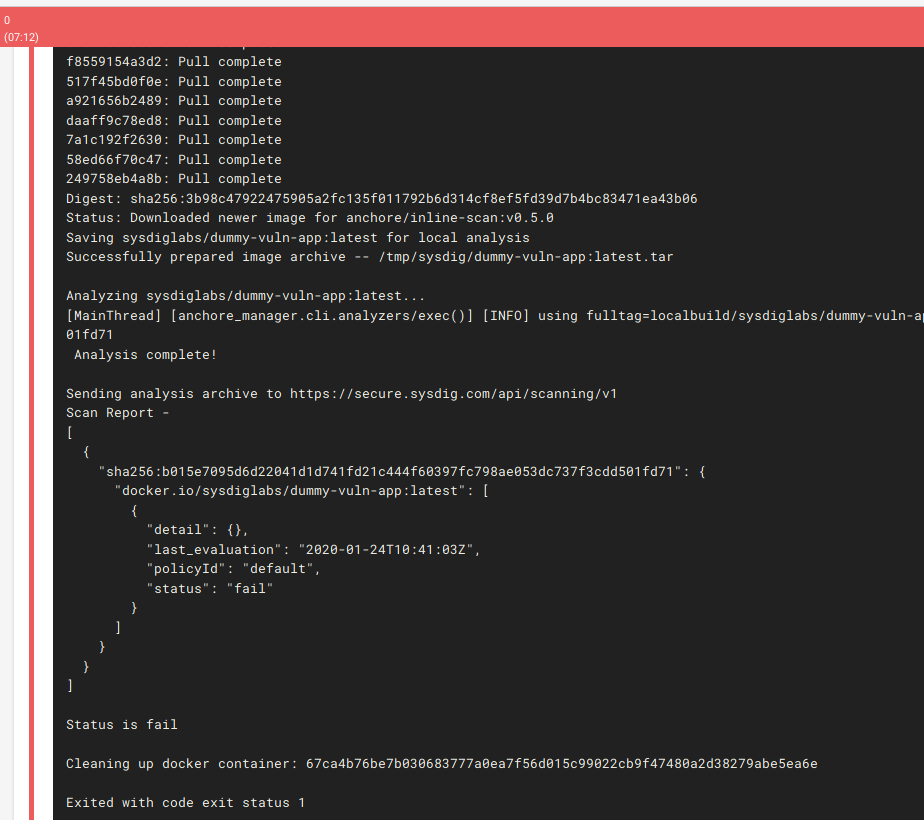
In this case, the scanning has failed and the script returns an error code different from 0. This happens because the final image fails to validate against the configured policy, so the pipeline is automatically stopped and won’t execute the next step, pushing the image to the image registry.
If we want more information about the vulnerability scanning results, we can see them in Sysdig Secure:
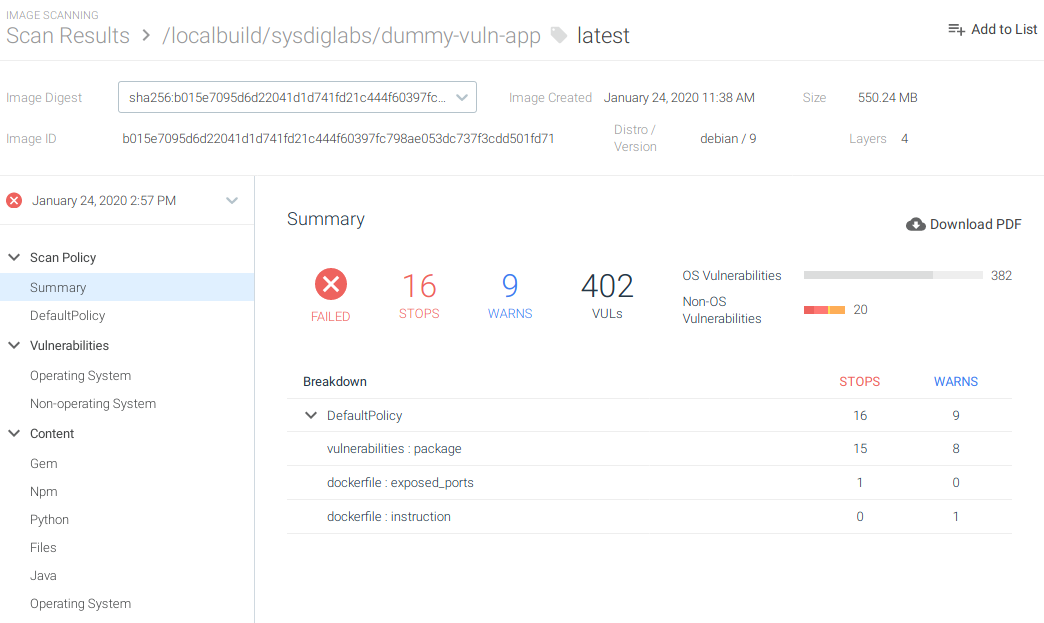
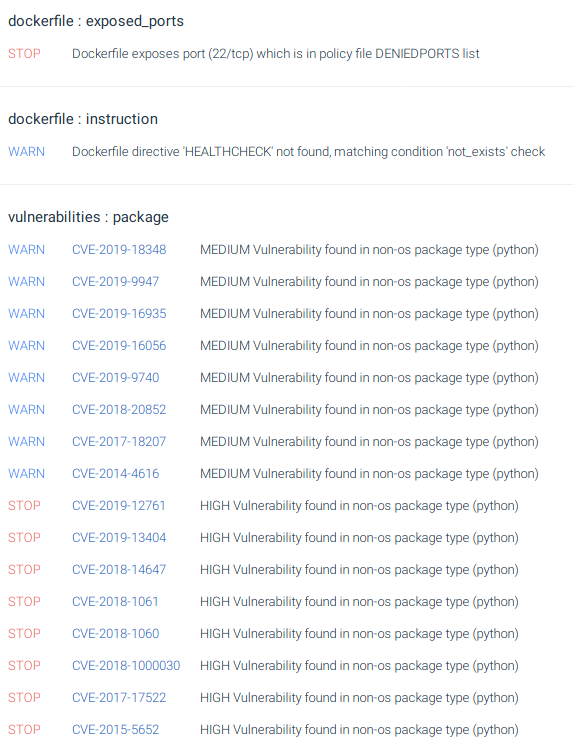
There are 402 vulnerabilities with 15 of them considered high severity. Also, you can see that the Dockerfile is exporting a port which has been blacklisted. The policy was configured to stop the process in these conditions:
Publishing stage
If the scanning in CircleCI is successful, the pipeline will continue it’s execution and the image will be published to the image repository:
docker push "$IMAGE_NAME"
Conclusion
Using Sysdig Secure image scanning, you can find known vulnerabilities and validate configuration against security best practices. That includes Dockerfile instructions, whitelist or blacklist specific packages, and 3rd party libraries installed on top of the base image, such as Java JAR/WAR files or language specific package managers like Javascript’s npm, Python’s pip or Ruby’s gem.
Scan your container images within your CircleCI CI/CD pipeline without sending them out of your infrastructure to a public or staging registry, validating configuration and preventing vulnerabilities from reaching your Kubernetes environments.
To try Sysdig Secure yourself,
request a demo today!
 In the next screen you will see some pipeline templates, most of them work out of the box to build simple projects. In our case we will build a new pipeline from scratch.
In the next screen you will see some pipeline templates, most of them work out of the box to build simple projects. In our case we will build a new pipeline from scratch.


 In this case, the scanning has failed and the script returns an error code different from 0. This happens because the final image fails to validate against the configured policy, so the pipeline is automatically stopped and won’t execute the next step, pushing the image to the image registry.
If we want more information about the vulnerability scanning results, we can see them in Sysdig Secure:
In this case, the scanning has failed and the script returns an error code different from 0. This happens because the final image fails to validate against the configured policy, so the pipeline is automatically stopped and won’t execute the next step, pushing the image to the image registry.
If we want more information about the vulnerability scanning results, we can see them in Sysdig Secure:
 There are 402 vulnerabilities with 15 of them considered high severity. Also, you can see that the Dockerfile is exporting a port which has been blacklisted. The policy was configured to stop the process in these conditions:
There are 402 vulnerabilities with 15 of them considered high severity. Also, you can see that the Dockerfile is exporting a port which has been blacklisted. The policy was configured to stop the process in these conditions:



