The Sysdig Secure 1.5 release furthers our goal of unifying security, performance monitoring, and forensics. This release includes a new UI and workflows to make security &
Kubernetes compliance accessible to application developers as well as security teams. Sysdig Secure 1.5 brings feedback about what AppDev’s, Platform Operators, and Security Operations teams want: An easy way to configure policy, detect events, and mitigate threats as quickly as possible.
We’ve updated the interface of both Sysdig Monitor and Sysdig Secure to bring a more modern look and feel to our products, while also providing more real estate within the app to what matters most: Your data. Switching between monitor and secure is just a click and any grouping configuration, notification channels, or integration work is automatically shared and can be used across products.
Kubernetes Security for the App Developer
Sysdig Secure allows users to scope policies by any piece of relevant metadata in their environment. If an app developer is responsible for a specific image, or an orchestrated service they can easily apply a single policy to protect all the containers associated with a given label or tab. The same goes for Platform Operators or SecOps teams who need to configure policies to an availability zone or Security group for compliance reasons.
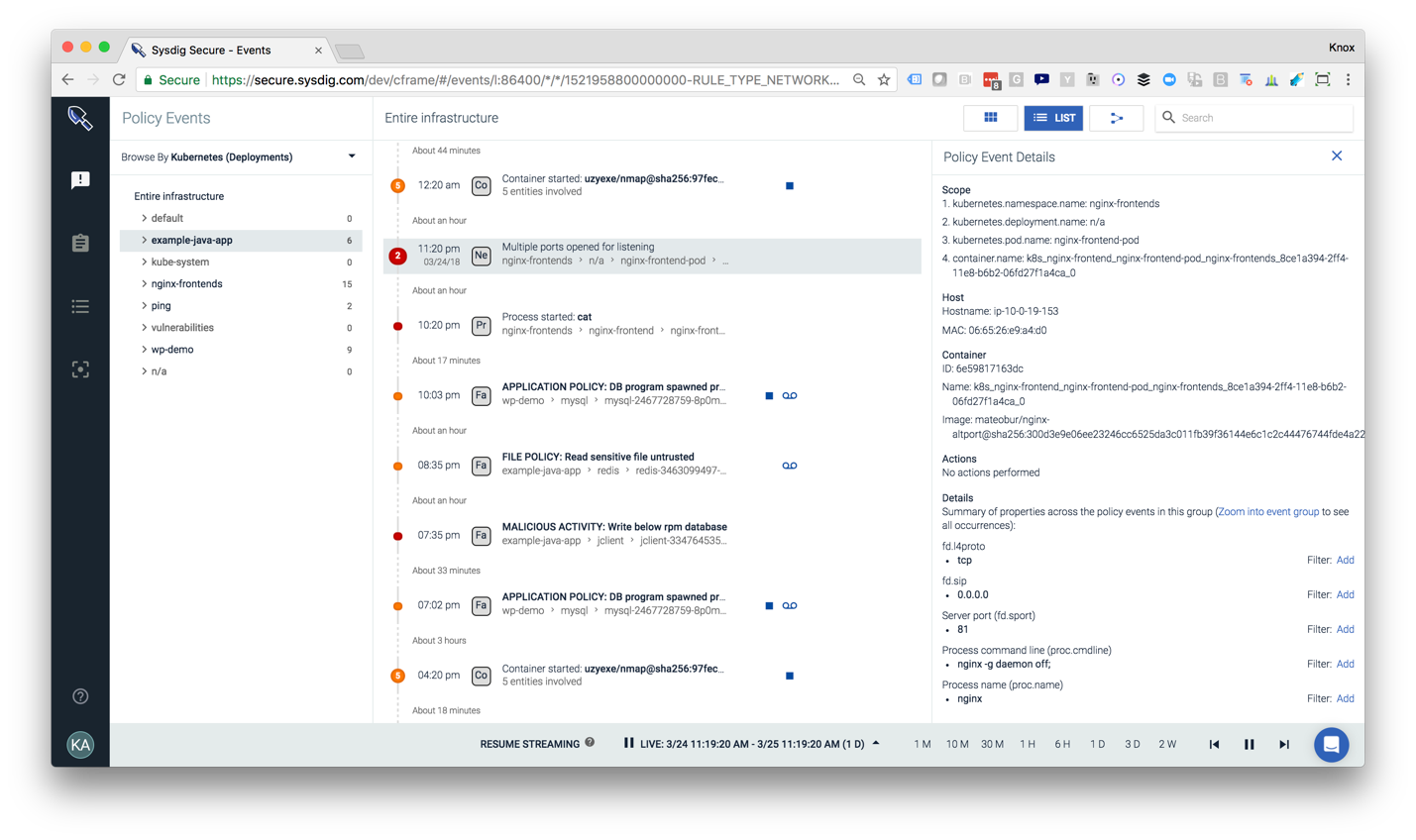
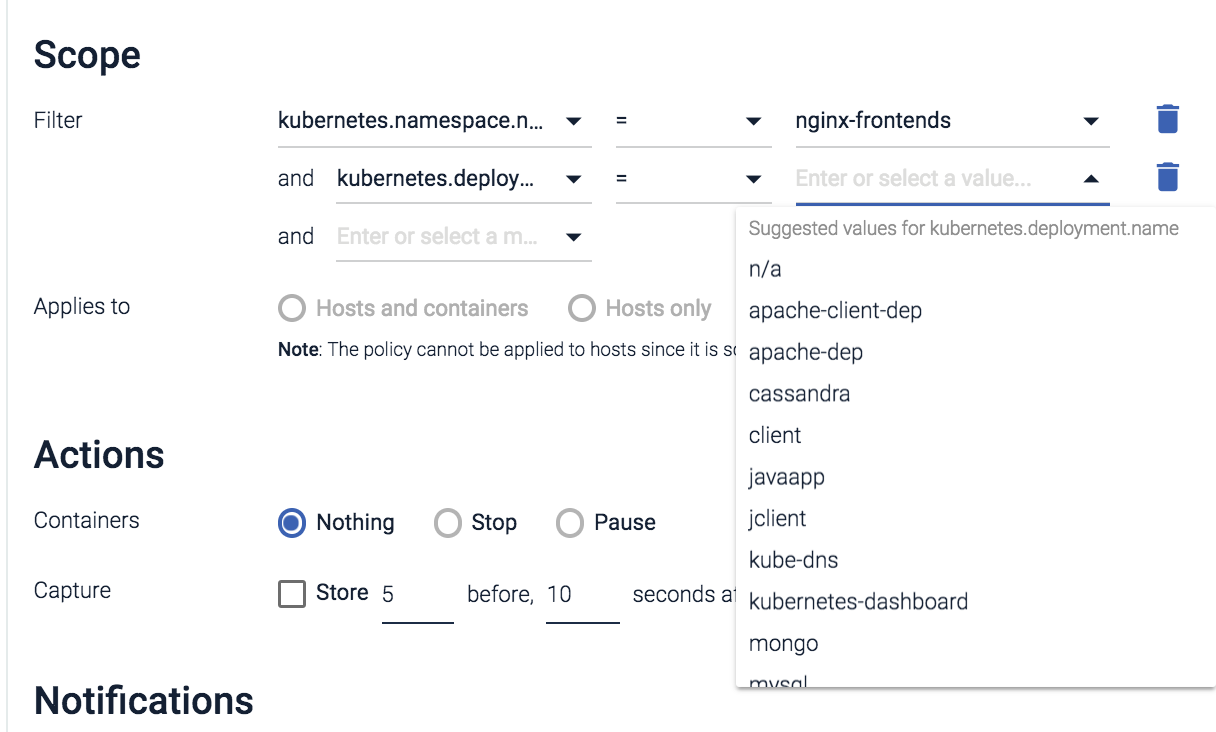 In this screenshot you can see the different kubernetes deployment options that can be used to scope policies to help protect containers at scale.
In this screenshot you can see the different kubernetes deployment options that can be used to scope policies to help protect containers at scale.
Besides being able to scope policies by metadata our customers wanted a simple way to configure policies so that everyone in the organization can understand them. This falls in nicely with the DevSecOps mantra of
you build it, you secure it, you run it. Our new enhanced policy rules let you easily whitelist and blacklist processes, container images, files, ports, and more, while still allowing you to cover advanced scenarios with Falco based rules.
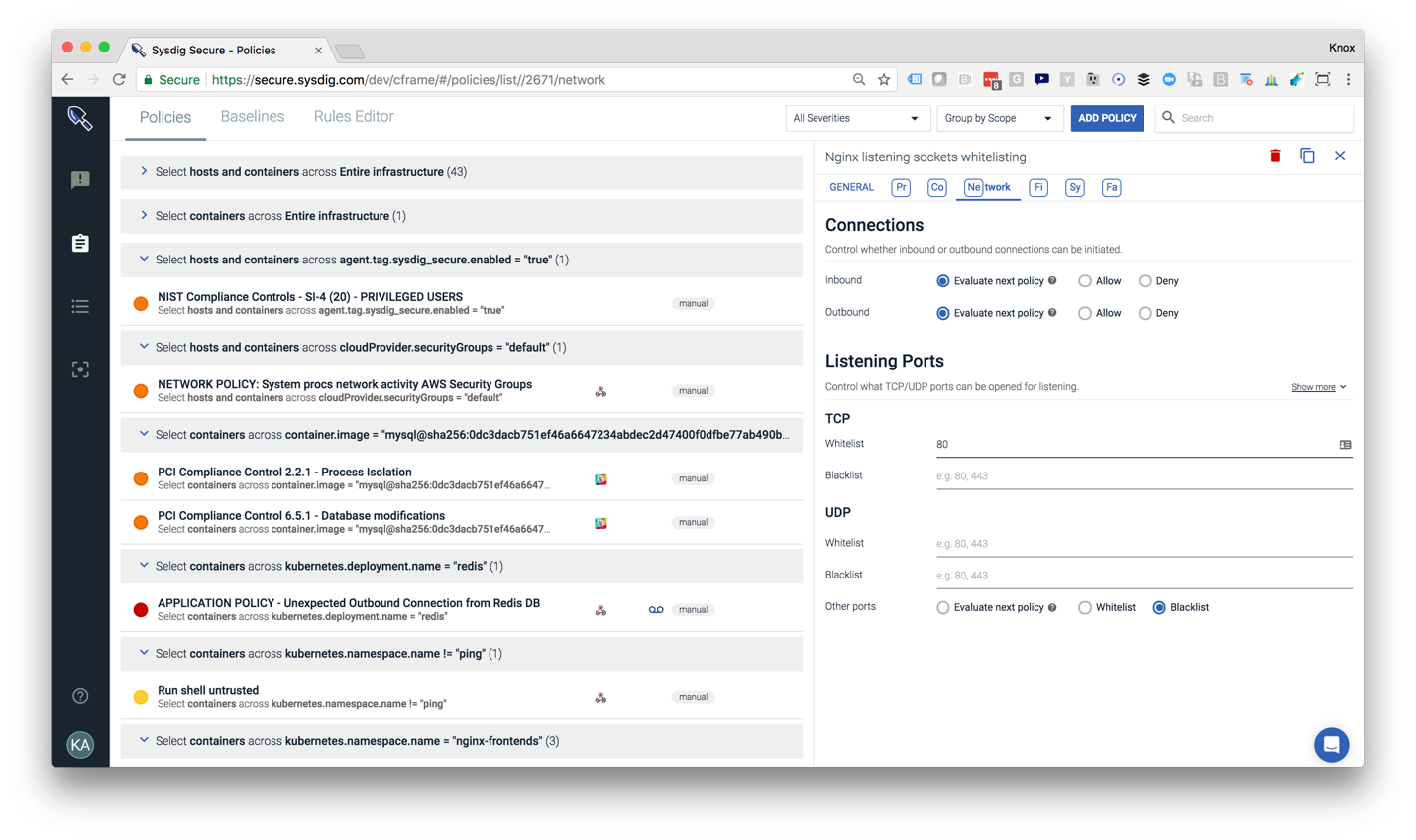 This screenshots shows all the different policies configured based on scope in your environment. The policy editor shows how users can easily limit inbound/outbound connections or detect unwanted activity on a range of ports.
This screenshots shows all the different policies configured based on scope in your environment. The policy editor shows how users can easily limit inbound/outbound connections or detect unwanted activity on a range of ports.
Default Policies mapped to Compliance Frameworks
Sysdig Secure makes it easier to ensure that your organization is meeting its compliance regulations in many ways. One new method by which we achieve this is by mapping our default policies to common compliance regulations. That means the secops team or a developer can more easily understand why a rule is being applied, and if a violation occurs, what the potential impact of that violation is.
Sysdig secure comes with dozens of out-of-the-box policies today, that typically cover 90%+ of an enterprise’s needs. With the new policy editor, creating that last 10% is a simple task for any cybersecurity or devops professional.
Increased Investigation efficiency
If a policy condition is met and an event is triggered a security analyst must quickly understand if the event is malicious activity, if the existing policy must be tuned, or if there is no issue. We’ve expanded our event feed to group related events in the same timeframe as well as provide a robust summary to make the event classification process easier.
All events are also enriched with full kubernetes context, meaning no additional manual log correlation is needed to find out all the services a particular image may relate to.
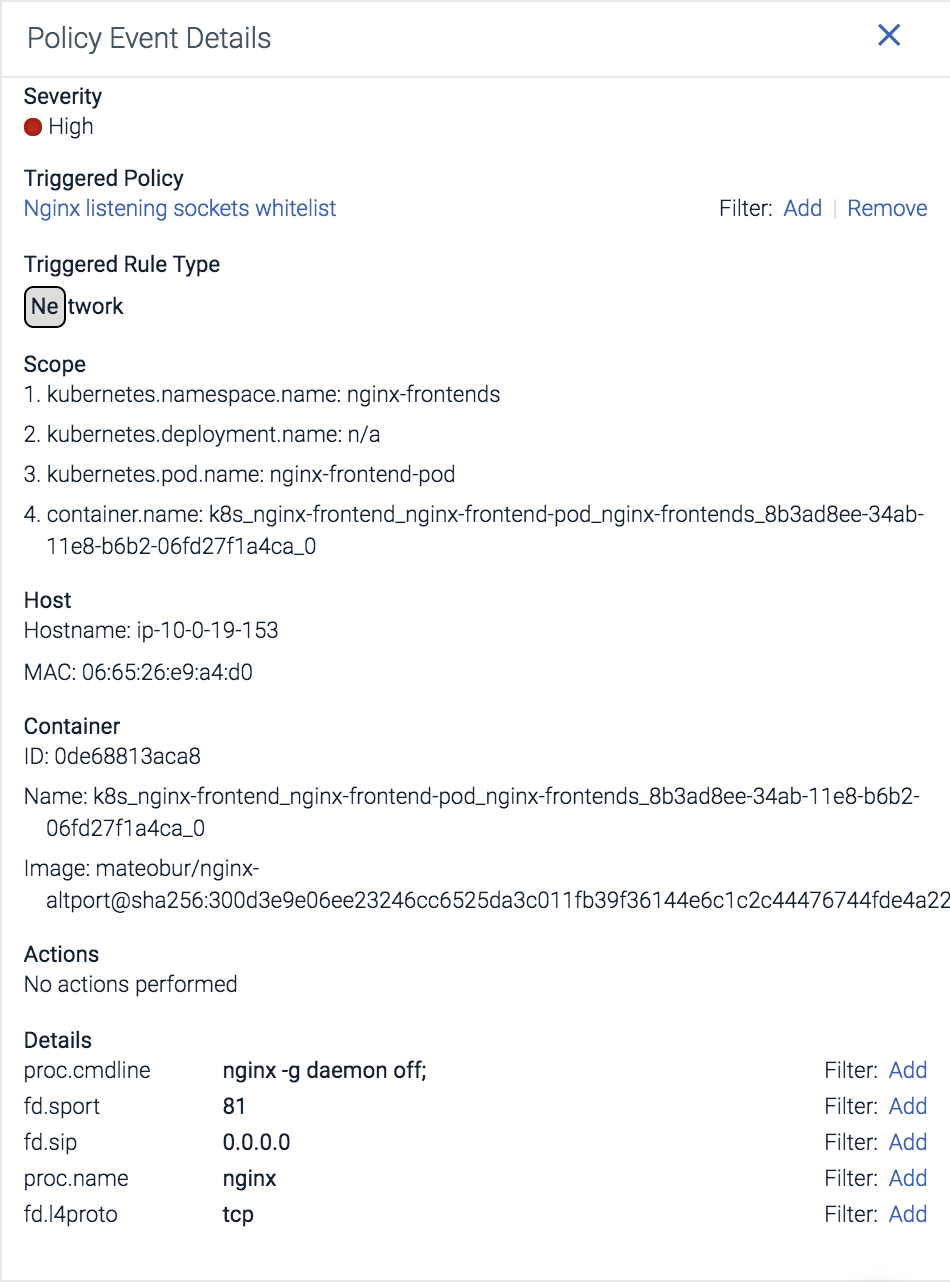 Within the details section a user can quickly see full details about why a policy violation occurred and how it can relate to the rest of your environment. Here we can quickly see the connect was attempted on port 81 by the nginx – g daemon off; command.
Within the details section a user can quickly see full details about why a policy violation occurred and how it can relate to the rest of your environment. Here we can quickly see the connect was attempted on port 81 by the nginx – g daemon off; command.
Sysdig Secure + Cloud Security Command Center
Google’s Cloud Security Command Center helps security teams gather data, identify threats, and act on them before they result in business damage or loss.
In this latest release we’ve added an integration between
Sysdig Secure and the Cloud Security Command Center. Sysdig events will be correlated to 2 kinds of resources from Google Cloud Platform: compute instances, either launched manually or part of a GKE instance pool, and also container images from the
Google Container Registry.
Sysdig Secure enriches all events from containers with all the relevant instance, container image, Kubernetes scope, and cloud metadata. To make events more meaningful to
Kubernetes Security teams add the different custom Kubernetes properties from Sysdig into the findings table, including cluster id, namespace, deployment or pod.
Check out what customers are saying about the integration:
“We chose to develop on Google Cloud for its robust, cost-effective platform. Sysdig is the perfect complement because it allows us to effectively secure and monitor our Kubernetes services with a single agent,” said Ashley Penny, VP of infrastructure, Cota Healthcare. “We’re excited to see that Google and Sysdig are deepening their partnership through this product integration.”
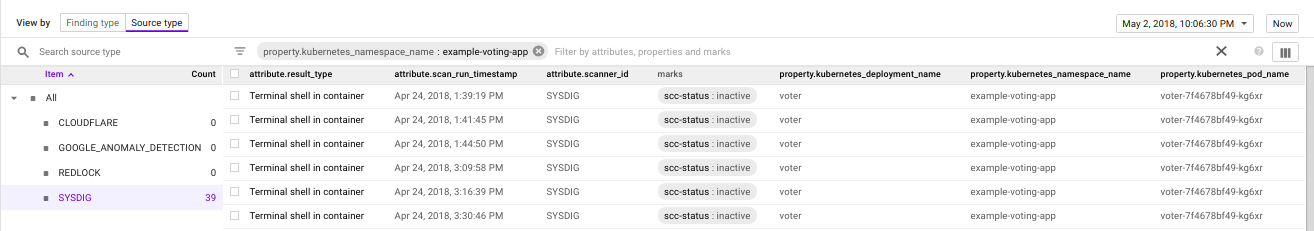 Sysdig Secure enriches all events from containers with all the relevant instance, container image, Kubernetes scope, and cloud metadata. To make events more meaningful to Kubernetes Security teams add the different custom Kubernetes properties from Sysdig into the findings table, including cluster id, namespace, deployment or pod.
Sysdig Secure enriches all events from containers with all the relevant instance, container image, Kubernetes scope, and cloud metadata. To make events more meaningful to Kubernetes Security teams add the different custom Kubernetes properties from Sysdig into the findings table, including cluster id, namespace, deployment or pod.
Conclusion
If you want to hear about some of the benefits directly from customers who have unified monitoring and security operations check out these case studies from
SunRun and
Quby. We’re constantly releasing new features to and resources to help organizations meet compliance and security needs in their new containerized environments.

 In this screenshot you can see the different kubernetes deployment options that can be used to scope policies to help protect containers at scale.
Besides being able to scope policies by metadata our customers wanted a simple way to configure policies so that everyone in the organization can understand them. This falls in nicely with the DevSecOps mantra of you build it, you secure it, you run it. Our new enhanced policy rules let you easily whitelist and blacklist processes, container images, files, ports, and more, while still allowing you to cover advanced scenarios with Falco based rules.
In this screenshot you can see the different kubernetes deployment options that can be used to scope policies to help protect containers at scale.
Besides being able to scope policies by metadata our customers wanted a simple way to configure policies so that everyone in the organization can understand them. This falls in nicely with the DevSecOps mantra of you build it, you secure it, you run it. Our new enhanced policy rules let you easily whitelist and blacklist processes, container images, files, ports, and more, while still allowing you to cover advanced scenarios with Falco based rules.
 This screenshots shows all the different policies configured based on scope in your environment. The policy editor shows how users can easily limit inbound/outbound connections or detect unwanted activity on a range of ports.
This screenshots shows all the different policies configured based on scope in your environment. The policy editor shows how users can easily limit inbound/outbound connections or detect unwanted activity on a range of ports.
 Within the details section a user can quickly see full details about why a policy violation occurred and how it can relate to the rest of your environment. Here we can quickly see the connect was attempted on port 81 by the nginx – g daemon off; command.
Within the details section a user can quickly see full details about why a policy violation occurred and how it can relate to the rest of your environment. Here we can quickly see the connect was attempted on port 81 by the nginx – g daemon off; command.
 Sysdig Secure enriches all events from containers with all the relevant instance, container image, Kubernetes scope, and cloud metadata. To make events more meaningful to Kubernetes Security teams add the different custom Kubernetes properties from Sysdig into the findings table, including cluster id, namespace, deployment or pod.
Sysdig Secure enriches all events from containers with all the relevant instance, container image, Kubernetes scope, and cloud metadata. To make events more meaningful to Kubernetes Security teams add the different custom Kubernetes properties from Sysdig into the findings table, including cluster id, namespace, deployment or pod.


