We’ve been busy this New Year (a rather warm one in San Francisco) to bring you exciting new ways to secure your DevOps journey. Highlights include:
- Vulnerability management is dramatically simplified with a new feature that elegantly tracks vulnerability changes across different image versions
- Auditing gets more comprehensive with the introduction of file-activity as a stream in the Activity Audit feature
- And much more!
Read on for the details and see how you can put them to use! For a demo sign up here.
Image Vulnerability Diff Reports

The challenge for all vulnerability management teams is handling and prioritizing very large vulnerability reports. Navigating across a huge list of tens of thousands of vulnerabilities manually through an excel report is a security team’s worst nightmare.
Sysdig Secure’s latest feature enhancements in image scanning allow vulnerability management teams to compare vulnerabilities across different versions of an image and discover new, fixed or shared vulnerabilities quickly.
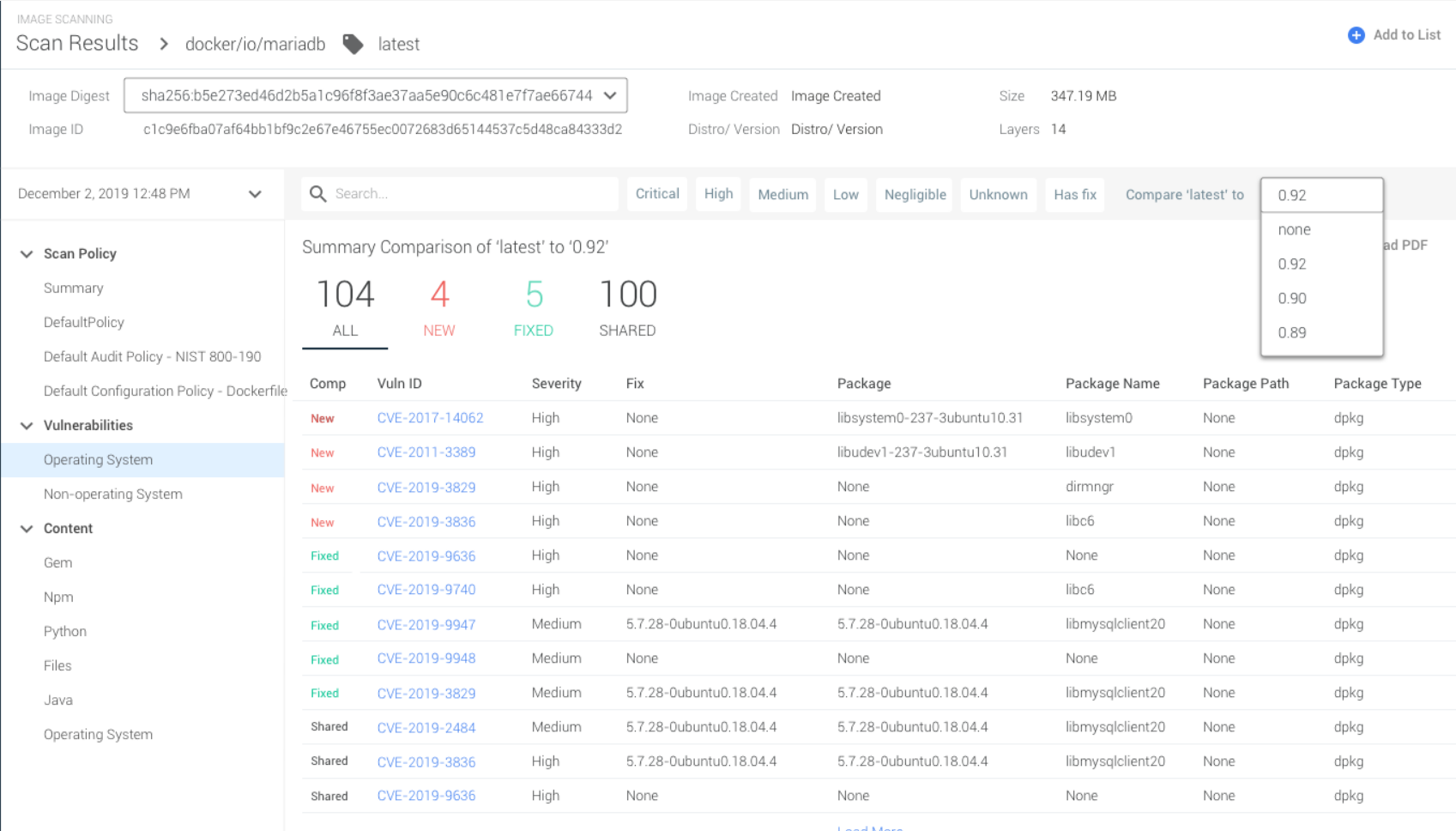
When you upgrade your image, how do you know your image risk posture is better or worse? Are you confident that you have not introduced new vulnerabilities? Or which existing vulnerabilities have been addressed? With Sysdig Secure, there is a clear way to compare vulnerabilities for different tags directly from the UI. By doing a diff across the new release, by checking different tags (ex. latest vs an older tag per repository) you can discover new and/or fixed vulnerabilities quickly without perusing through tens of 1000s of lines of excel reports.
Vulnerability Diff reports in Sysdig Secure!. Click to tweetNew Image Scanning Policies for File Integrity Monitoring
File attributes can now be verified as part of the image scan analysis. With this new policy, you can:
- Check if the file exists or not and trigger alert based on the condition
- A specific file can be validated against its SHA256 hash
- Validate file permissions. For example, if this file has an executable bit, we can flag that as an alert
- Check for filenames based on regex.
- Inspect contents (ex. Malware signatures, exposed passwords, credential leaks etc)
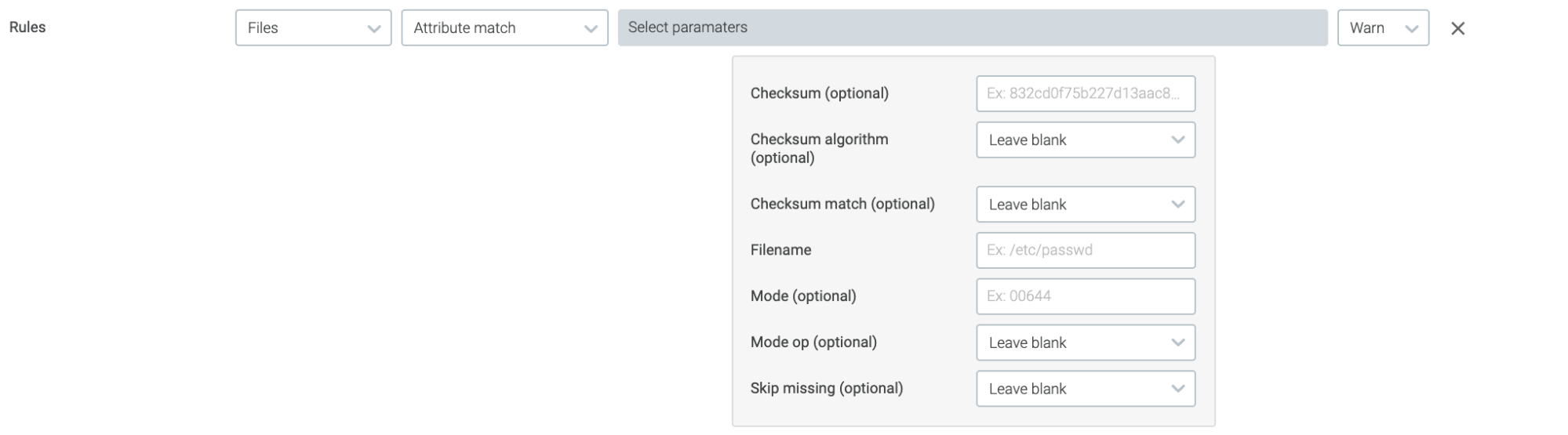
File Data type part of Activity Audit
Sysdig’s Activity Audit speeds incident response and enables audit for Kubernetes. Sysdig captures relevant information like:
- executed commands inside the container
- network connections
- Kubernetes API events, like users executing kubectl exec
By correlating this information with Kubernetes application context, the SOC team can spot abnormal activity and understand faster what happened during a security incident: who did what.
With Activity Audit 1.5, we’ve added a new “file” data type. You can now filter the audit trail by file type or specific file attributes:
- File name
- Directory
- Command (used to access the file)
- Access mode
This feature enables further File Integrity Monitoring (FIM) capabilities and the ability to audit tampering with sensitive files, such as:
- Container binaries (/usr/sbin/nginx, /usr/bin/java)
- Configuration files (/etc/passwd, /etc/shadow, /etc/ssh/sshd_config)
- Kubernetes secrets injected in the pod (/var/run/secrets)
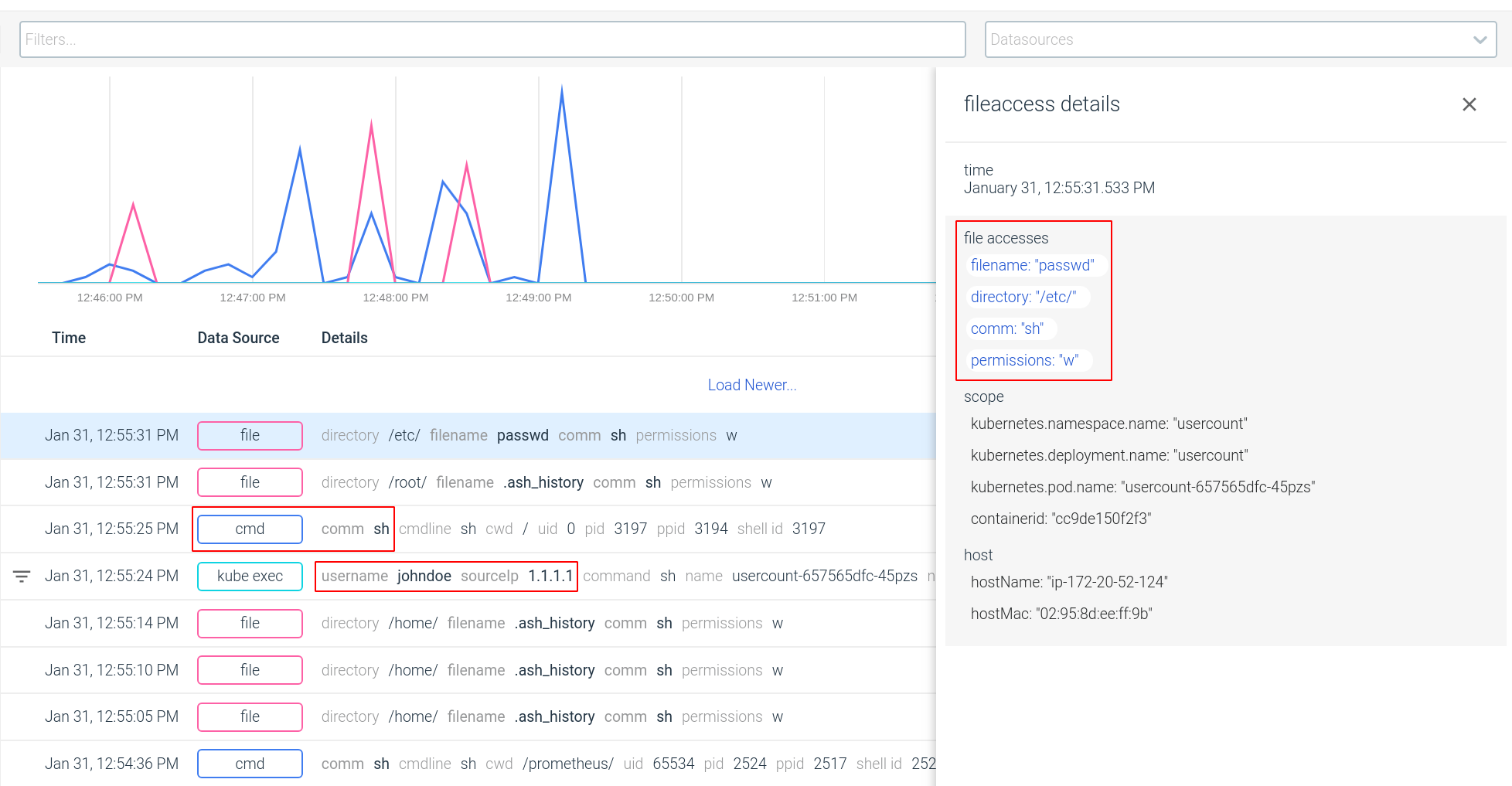
Activity Audit allows you to recreate a full audit trail correlating this action with the command that executed it, the user inside the container that launched the command and even the actual Kubernetes user and external IP that initiated the connection from outside your cluster.
Usability and visual improvements
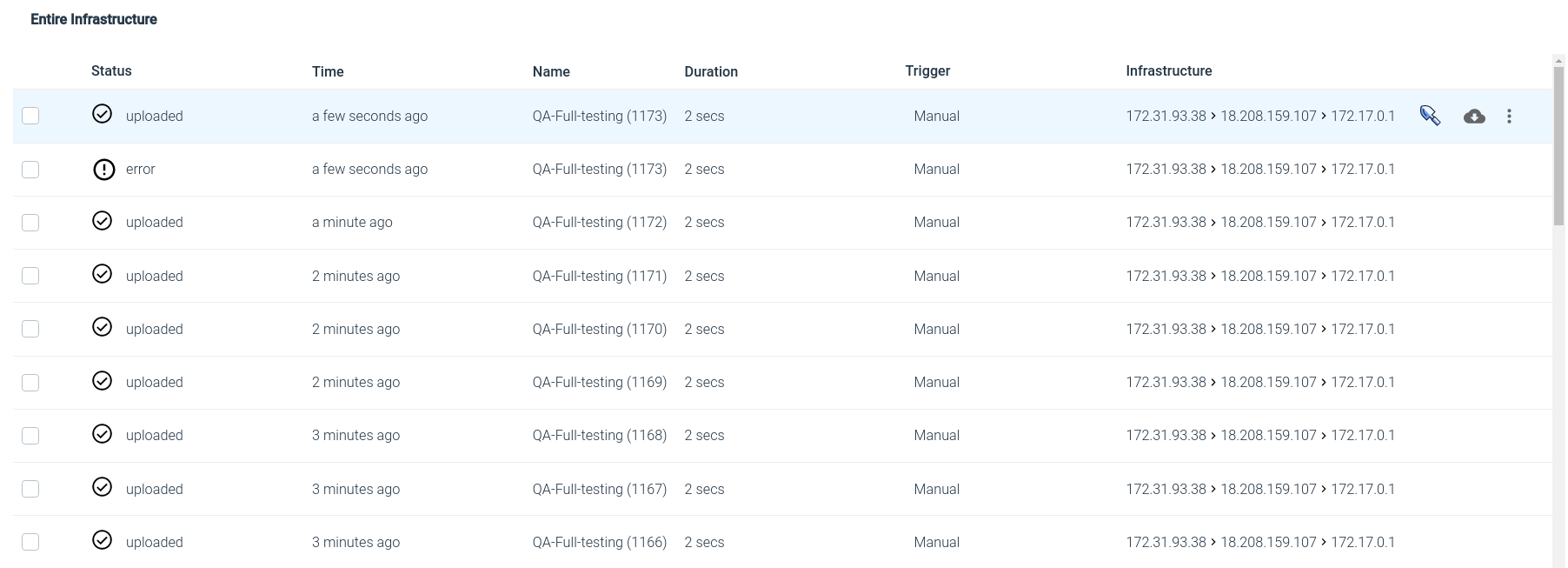
We also introduced an update to capture files as part of the Kubernetes forensics capabilities in Sysdig Secure. This allows for:
- The ability to see if a capture was triggered manually or from a policy
- Search across all capture files
Additional features
CRI-O support for the stop and pause actions associated with Policy Events (in addition to currently supported Docker containers) This is part of our efforts towards extending our integration with RedHat OpenShift.
To learn more, visit our page on Kubernetes security or sign up for a free trial


