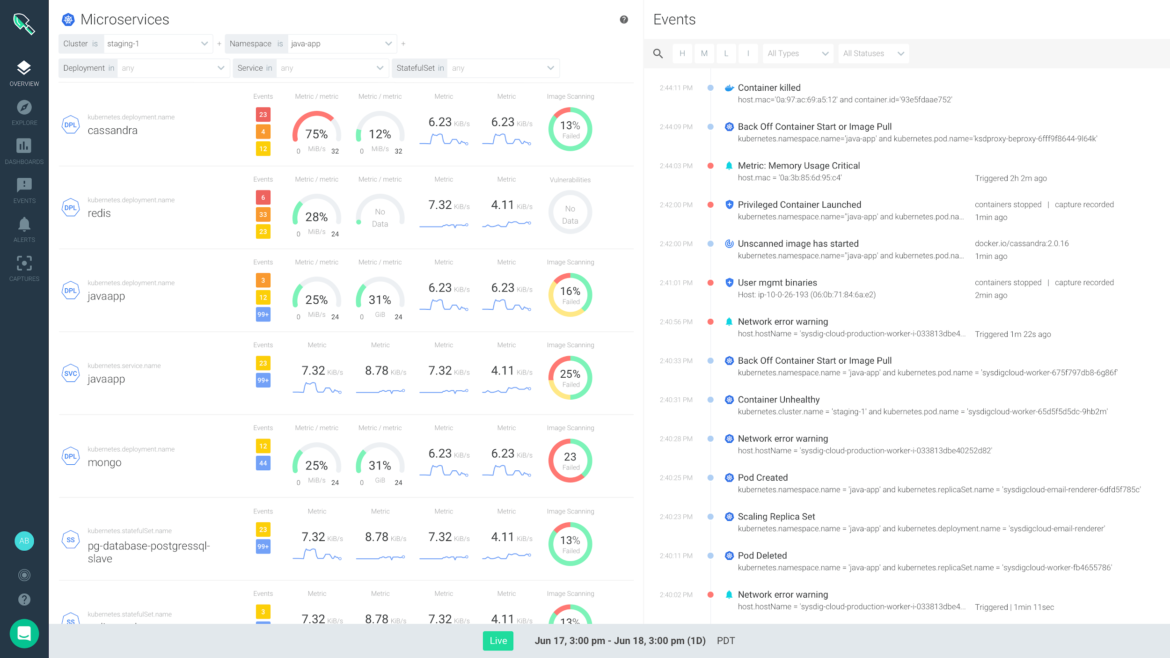
Today we’re announcing version 2.0 of the Sysdig Cloud-Native Visibility + Security platform. It provides a more powerful and significantly simpler way for enterprises to see the health, risk, and performance of their cloud-native environments in a single unified view.
With this unified, data-rich platform, enterprises can solve a broad array of use cases for their cloud native environments, including image scanning, compliance, performance monitoring, run-time security, troubleshooting, auditing, forensics, and more. The Platform’s new release now operates at 10x greater scale than before, with management and control that the largest organizations in the world require. (Many of these banks, government agencies, and media companies are already Sysdig customers.)
With our new approach to visibility and security, our customers report that they can transform to cloud-native 3x faster, increase devops efficiency by 67%, and improve risk mitigation by up to 95%. Read on to find out how we’ve solved for these issues in our new product release.
If you’d rather watch the product in action first, here you go:
Blinded by the (Cloud-Native) Light
The desire to take advantage of cloud-native benefits has forced many enterprises to rush into production with Kubernetes and containerized applications. The assumption was that operations teams would easily be able to apply their existing security and operational infrastructure to the new software platform and everything would be fine. Unfortunately, legacy tools are fundamentally ill-suited to support your cloud-native infrastructure. That could leave your developers, devops teams, and security teams blind as they made the leap to cloud-native architectures. Let’s discuss why that is.
Decision makers assumed that the millions they had spent on APM tools, SIEMs, intrusion detection systems, vulnerability management…. They would all just port over with a few adjustments. It turns out the real story is a bit more complicated. Adapting to the new models around containers, Kubernetes, and microservices isn’t simply a check-box feature. Rather, the underlying constructs of container and orchestrator driven microservices are so different from VM-based applications that in most cases legacy security and performance management tools cannot create enough visibility to understand the risk, health, and performance of your systems.
Let’s take a look at 4 core reasons why your legacy visibility and security tools won’t be able to adapt to your cloud native infrastructure:
- There is 10x more data in cloud-native environments. Compared to operating the equivalent monolithic software, teams will see an order of magnitude more data because there are simply more elements to be aware of. With this increase in elements comes a massive increase in the number of interconnections and relationships. This complexity alone is overwhelming for legacy tools.
- There is 100x more context needed. Containers and microservices add new abstractions that make it very hard to understand what is going on in your applications. The way to solve this is through metadata – the context to not only say what happened, but be able to reorganize the data on the fly by service, pod, cloud, and even host is absolutely critical to be able to understand all of this data. Most legacy security and monitoring tools were built with the assumption that your software had a 1:1 relationship with the infrastructure it was running on. They fundamentally cannot capture this metadata or give the user a meaningful way to consume it.
- It’s here today, and gone in 10 seconds. The ephemeral nature of containers, combined with the black-box nature of the technology means that the ability to capture deep data for analyzing security incidents, compliance violations, or performance issues becomes incredibly hard to come by. Legacy tools assumed that the application and infrastructure was static – even if there were a problem, everything would still be running in its place so you could access it for follow up. That’s simply not true in cloud-native environments.
- It’s not just the tools, it’s the process. With the move to CI/CD and DevOps, teams are looking to work in a much faster, more agile methodology. In order to do so, they need complete visibility into the performance, security, and compliance of their software earlier in the development cycle. This allows them to deliver more reliable, secure code the first time. The heavyweight, static nature of legacy tools aren’t suited to this model.
So while we have seen most vendors put “Containers” or “Kubernetes” on their roadmap like a simple checkbox item, we know that they will not be able to deliver the capabilities needed to truly, deeply understand your cloud-native applications. They have to rebuild their software both to support the data, but also to support the scale needed in cloud-native.
Sysdig built its products to support cloud-native environments from day one. Today we’re excited to announce the next evolution of our platform, where we bring together all our rich security and monitoring data sources to give you unmatched visibility into your applications.
Visibility through the entire container lifecycle as the foundation for security and performance
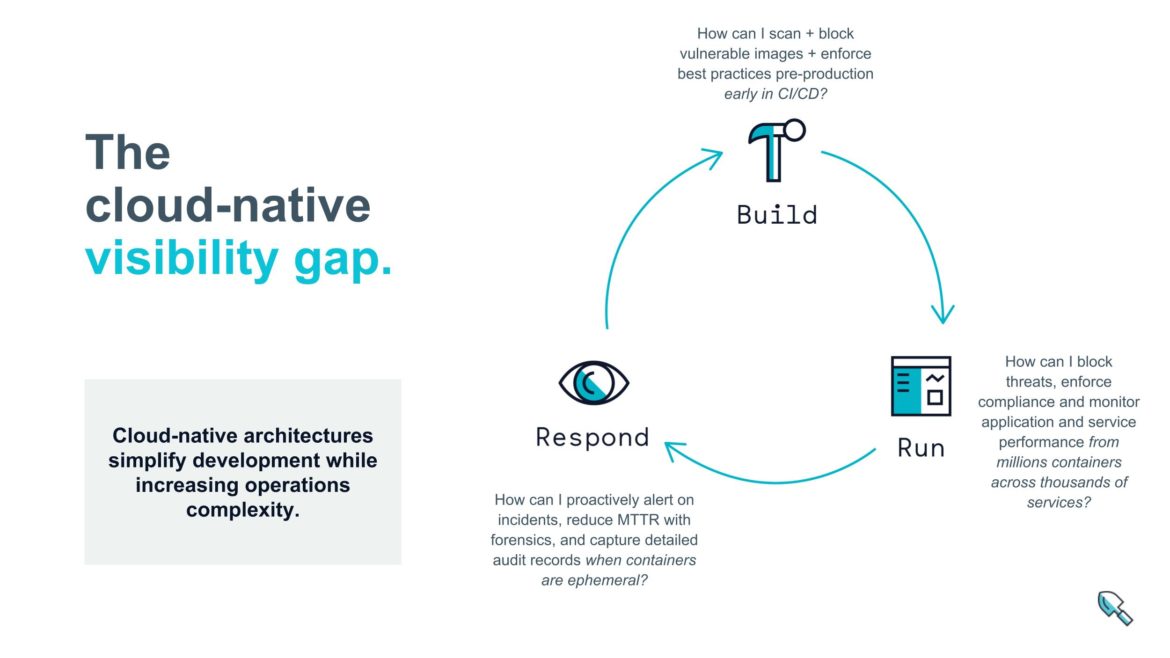
While cloud-native focuses on making it easier to build software, it shifts complexity to operating software. The nature of cloud-native, microservice driven applications means that your software is comprised of smaller atomic units, more highly distributed, and using machine automated orchestration. This makes it really hard to see what your services are actually doing (or what’s being done to them). So how do we architect to solve this problem, and fill in the visibility gap when legacy solutions simply cannot?
Visibility turns out to be the missing essential component needed across the entire lifecycle of your cloud-native journey. We need visibility and data to answer simple questions like:
- “Which services are slowing down and impacting other services?”
- “Which clusters are starved for resources?”
- “Which services are running with newly discovered vulnerabilities?”
- “Which of my services has the most compliance violations?”
- “Which containers accessed the file that was found to have been leaked a week ago?”
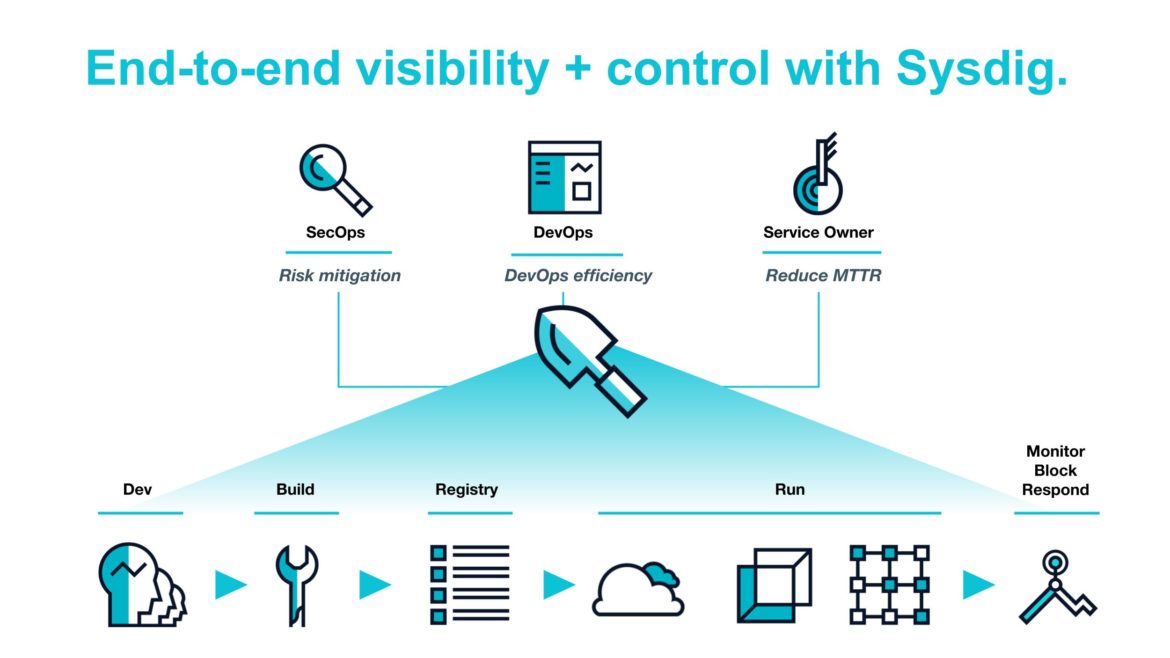
Without the right insight, this becomes incredibly challenging. This is true almost regardless of your role in software development process: the devops team looking at the underlying platform, the service owner considering their own software, or the security teams looking across the entire system.
Think about this simple framework for development, and the questions you might ask along the way that require deep insight into your applications. We call it (not too creatively) the Build/Run/Respond Framework.
- Build: As an application or service owner building a new application or microservice, what can I do to ensure my code and its components are both reliable and vulnerability-free before going to production? And as DevOps, how do I know that services are being implemented with devops best-practices across all containers?
- Run: As I push my services into production, how can I be sure they meet compliance requirements? How do I know if users (bad actors or otherwise) are violating my operational security policies? How do I know these services are performing well and not a bottleneck for downstream services?
- Respond: When something goes wrong, how quickly can I predict or discover it? Can I isolate the right data based on the context of the specific services, container, or clouds that are relevant? Can I get forensics and troubleshooting data even as the orchestrator automatically kills off poorly performing containers?
All of these questions are fundamentally data questions: can I see deeply enough into my software and infrastructure to understand how it’s performing and what it’s doing?
This of course assumes you’re actually creating your applications in a cloud-native environment today. When we engage many of our clients, they are still in the process of making the transformation to cloud-native. They are asking questions such as:
- How does my software actually perform when it is ported to containers or re-written for cloud-native?
- How can I best visualize our complex, distributed microservices in a multi-cloud environment?
- How do I plan capacity for this new environment?
Regardless of where you are in the cycle, solving the visibility gap within your infrastructure and applications is absolutely critical to successfully making the leap into cloud-native applications.
Sysdig Platform 2.0: The First Unified Management Plane for Risk, Health, and Performance for Cloud-Native Applications
So how do enterprises actually address these pains, and do it in a way that isn’t just about making team members work harder, or buying more and more software to solve the issue? That was the core focus for 2.0 of our visibility and security platform, and we’re proud to show you what that looks like.
As with many solutions to hard problems, it tends to be helpful to throw out existing constructs and start with a fresh piece of paper. It’s fair to say Kubernetes was able to do that on the development side, but until now the analog hasn’t happened on the operations side.
We started by/thinking about visibility as the core issue here – not monitoring, not APM, not image scanning, not run-time security, not forensics…. You get the idea. Each of those vantage points, eg “container security,” is just too narrow to solve the problem in a broad strategic sense.
The problem in container environments tends to be how to get enough data, how to get the right data, and how to get enough context around your data to actually understand what it means. We knew if we could solve that, we could create far more extensible solutions for enterprises.
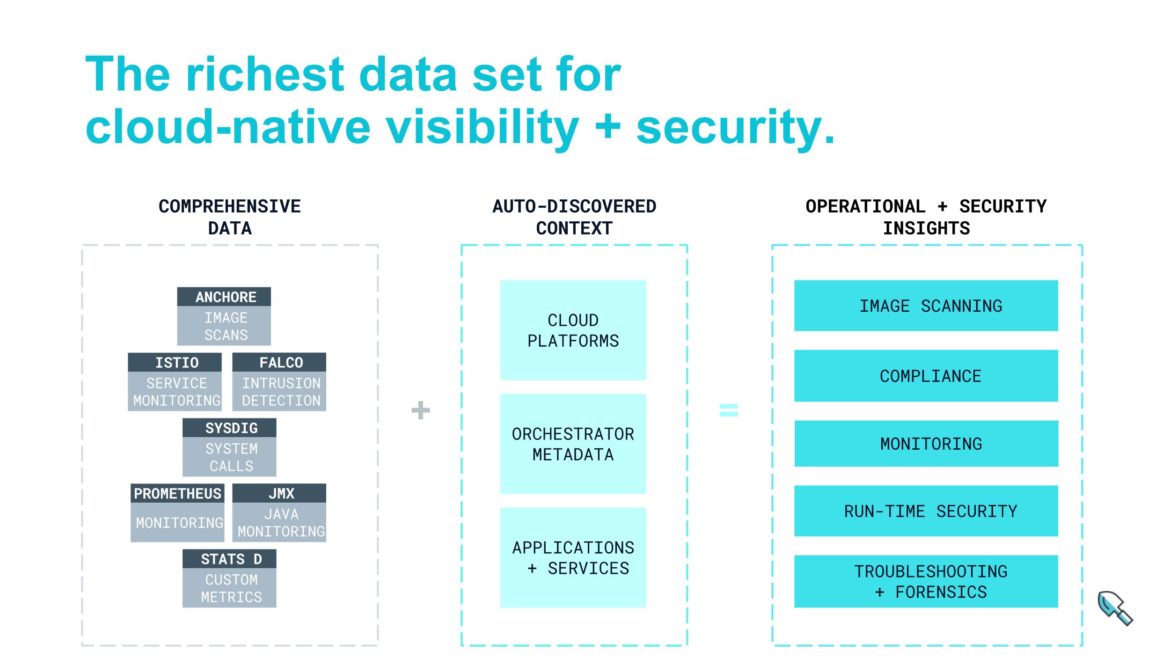
If you’ve been following Sysdig you know that we’re a big fan of system calls. From our original instrumentation, to our just-released eBPF capabilities, we think they are a great source of information for everything happening on your system, and a source that you can rely on in the cloud and on your own servers. They give you visibility into containers, processes, host, and networks from one instrumentation point. Over time, however, we leveraged this instrumentation to also consume many other sources of data in your system (think Prometheus, JMX, StatsD, Istio, Kube-Audit Feeds…. The list goes on). We’ve coined this ContainerVision, as it’s the most complete way to look into the atomic building block of today’s services.
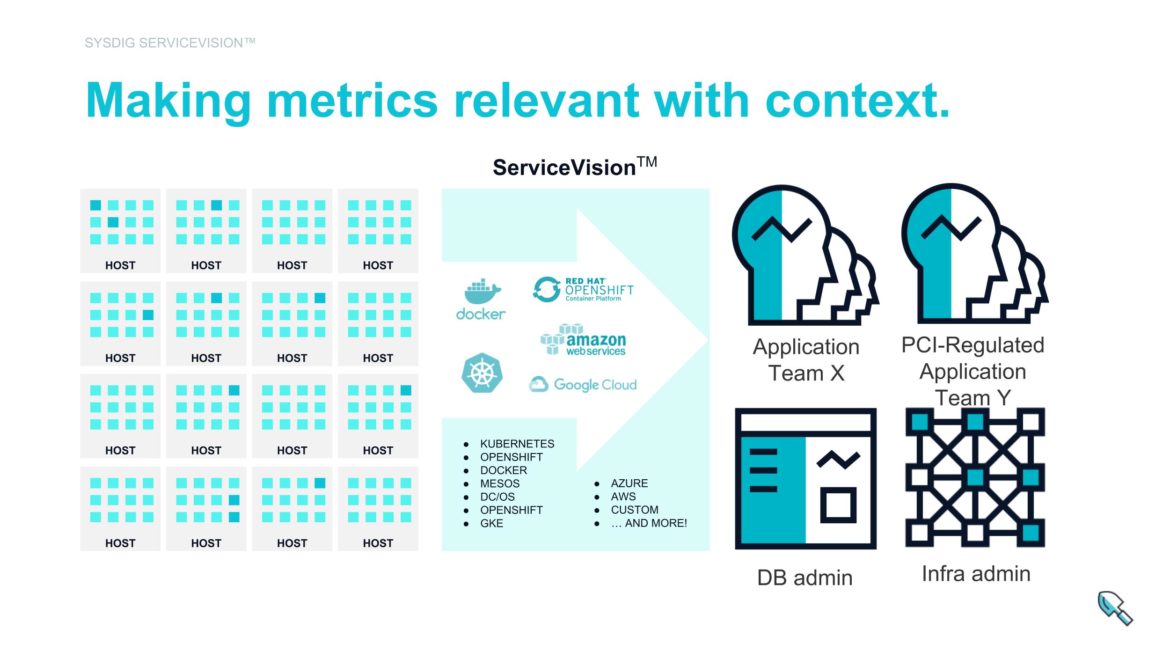
We combine ContainerVision with ServiceVision, our methodology to automatically grab massive amounts of context around your application and container metrics – namespaces, pods, clouds, clusters, availability zones, and your own special data. This allows you to slice data any way you see fit and even isolate data so users only see what is relevant for them. This gives security teams, platform teams, and service owners the right data and the right context for their view of the world.
The end result is a combination of the most important data – whether it’s for security analysis, health monitoring, or performance management – for key users on your team. And it’s all scoped to expose only the data relevant to their software, while giving the DevOps team one platform to manage this massive amount of data at scale.
Designed for Multi-Cloud (or Any Cloud)
Another interesting aspect of our product release is that it’s not only about what we’re collecting for you, it’s about where we are collecting it and where we are storing it.
One of the big opportunities enabled by containers is the ability to go multi-cloud. While development teams are still truly trying to figure out what it means for their software (and processes) to be multi-cloud, it is clear that they want to be prepared to go in that direction. So whether it’s simply to leverage public cloud in addition to their private infrastructure; avoid being locked into AWS; or take advantage of cloud specialities like Watson on IBM or TensorFlow on Google, enterprises are looking for a consistent way to secure and monitor their applications across all the clouds they might utilize.
That’s a particular advantage of Sysdig compared to other approaches. Our agent has been put through the test across AWS, Google, Azure, and IBM*. And most of our large enterprises use us for visibility and security across their private infrastructure as well.
Creating a multi-cloud strategy isn’t just about your application building blocks, but also about your operational toolset. As opposed to being locked into your cloud provider and their limited monitoring or security tools, Sysdig provides a strategy that gives you more consistency and more flexibility. Consistency to apply the same technology across clouds, to get the same high-quality results; flexibility in case you change clouds and want to do so without missing an operational beat.
In addition to where enterprises are collecting the data, we also provide customers flexibility of where the would like to store the data.
Sysdig provides two separate deployment models:
- Cloud – Sysdig runs a multi-tenant backend as a service for you
- Software – You deploy and run Sysdig wherever you like
For customers who are comfortable storing security and performance related data in a 3rd party cloud service, Sysdig gives you a completely hands-off way to operationalize data about your cloud-native applications.
Those who have greater data restrictions or other imperatives can run our back-end software in their data center or their virtual private clouds. The beauty here is that because we operate our own SaaS, we actually know what it’s like to operate our software at scale, and are continually improving that experience. Ask those other small container security companies if they can claim to run a SaaS that manages Tens of Millions of containers a day.
*IBM Cloud’s observability service is built on Sysdig. Not surprisingly, that means you can easily leverage IBM’s service as an alternative version of Sysdig’s cloud offering.
New Product Packaging: Enabling Scale for the Enterprise
Sysdig will also be rolling out an order of magnitude increase in the amount of data Sysdig’s platform can store and that users can query in real-time. This increased scale will be available in SaaS next month and on-premises in the later part of the year.
Sysdig has been – and continues to be – licensed by the number of underlying nodes (or VMs) being secured and monitored. Sysdig starts at $30/ host billed annually, and prices vary based on various customizations like container density, custom metrics scale, hosts secured, and which applications you want to use.
- “Platform” Packages. To enable enterprises to take advantage of everything we have to offer, while eliminating the need to deploy niche container security or monitoring products, we now offer a Platform Package. This package gives you:
- Access to the new, unified view of risk, health, and performance across your services
- Access to all applications that run on the platform: Secure, Monitor, Inspect
- Ability to deploy in the cloud or on premises
- Product Tiers: All packages will have two tiers: Pro and Enterprise based on container density and number of custom metrics. Based on the tier, we’ll be offering up to 5x greater container density, and up to 10x greater metrics consumption. Prices are customized based on your desired scale, so please reach out to Sysdig to learn more.
- Continued availability Sysdig Secure and Sysdig Monitor for stand-alone purchase. The bulk of Sysdig customers already purchase Sysdig Secure and Sysdig Monitor together – that’s why we’re so excited to announce the streamlined Platform packages. At the same time, we do provide our key applications as stand-alone offerings in both SaaS and On-Premise.
We’ll be rolling out SaaS changes this spring, and On-premise software changes after that.
What’s next
We’re excited to be making cloud-native a simpler process for enterprises. By giving you a rich, data-centric platform that provides deep visibility and security across your applications, containers, and hosts, we are confident that you’ll have an easier time transitioning to containers, and be able to do so with confidence.
Our approach means that you won’t have to deploy niche container security tools, nor container monitoring, forensics, capacity planning… you get the idea.
Moreover, with this unified dataset, you will see that Sysdig can help you do more. What you have to look forward to is Sysdig leveraging this data to not just provide visibility, but also insight and predictive intelligence. We look forward to working with you to make the promise of reliable, secure cloud-native applications a reality.