Recently, we have been facing a recurring problem related to cloud security – breaches based on credentials leak or breakage. Users tend to log into their accounts using a single factor system, such as a user and password combination. This introduces a single point of failure in your account’s security. You should always enable MFA on your cloud accounts.
Weeks ago, we read a tweet about a person dealing with a huge AWS bill due to a stolen key that was taken by attackers to use AWS Lambda functions for crypto mining. After a month, they faced a $45,000 AWS bill. Even if their case is not strictly a stolen password, it is a single-factor authentication example.
It’s very interesting to learn how it all happened and how they would have protected themselves by activating the MFA in their cloud account.
Based on true events
The first thought could be, “That’s a problem of those Cloud Provider centric companies/users.” But then, several end-user-centric use cases came to mind.
We remembered that, several years ago, we attended a MOOC which required us to register for Google Cloud Platform. Since then, We’ve been receiving a monthly $0.00 bill from Google.
Think about when you are preparing for a Certification in a Cloud Provider. Or consider that NAS you bought that offers storage synchronization with a storage solution like AWS Glacier, Google Nearline, or Azure Storage that you configured with your Amazon account. There are several ways for you to have registered for a cloud provider.
Are those thoughts keeping you up at night?

How easy it is to break your authentication without Cloud MFA
Could someone with just your password login launch a machine (or a lambda function), install cryptomining software, and let it run until you notice it?
If you aren’t familiar with the huge_amount_of_options when using different cloud providers, it’s easy to not notice, for example, that there could be an extra instance running in a region that you don’t normally use. And if you (like us) don’t have cost alarms set up for your personal account, it could be a month until the bill arrives and you notice you’ve been hacked.
We did a test and tried creating an instance in my Google Cloud Platform account from an incognito web browser window (to do the full login process). Then voilà, it asked us to enter the code sent to our cell phone (thanks to Google for insisting on enabling MFA).
Even though we were more relaxed after knowing MFA was enabled for my cloud account, We think it is important to be conscious of its relevance. Single authentication accounts are vulnerable to several types of attacks:
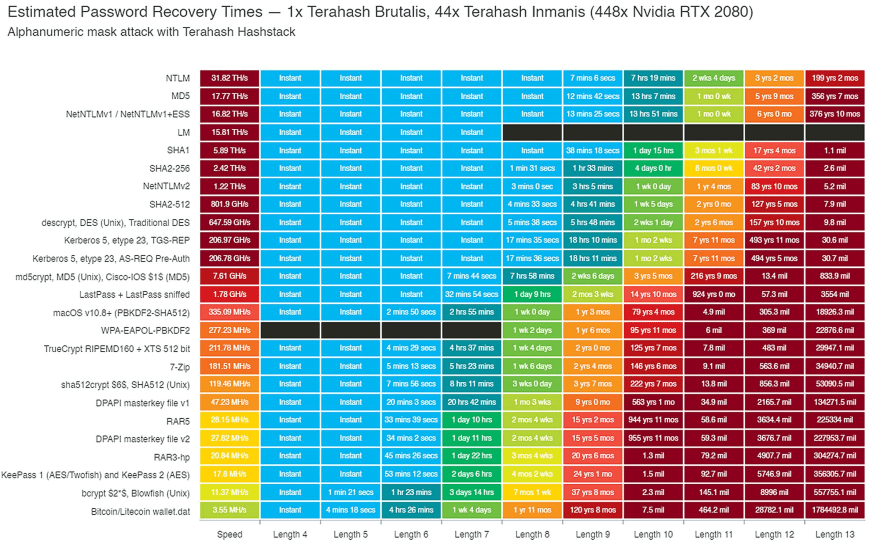
Brute Force attacks
This table takes a look at the times it takes to crack a password via brute force.
In addition, several tools help on brute force attacks (not only user/password combination, but port scanning or even known vulnerabilities), like Burp suite or Hydra.
Credential leaks
Post It’s on your display, credentials uploaded by error, oversight into Github repos, or even on social network profiles all fall in the social engineering category and are ways for attackers to get your precious passwords.
Phishing attacks
A very common example of a phishing attack is when you receive an email asking you to “Reset your password,” ironically, due to a security issue. However, once you reset your password, they got you.
Enable Multi-Factor Authentication – MFA cloud
It is clear that just enabling a multiple-factor authentication (MFA) increases the level of complexity for your account to be hacked. It’s obvious, isn’t it?

Authentication scenarios observe three different ways of checking identity:
- Something you know: a password
- Something you own: cell phone, physical key, coordinates card
- Something you are: fingerprint, iris
Passwords are the most spread by far as they are the easiest and generate the least friction for user acquisition. But passwords are the weakest, as we can easily try to guess them from anywhere and the only thing the attacker needs to break your password is time.
According to Microsoft, 99.9% of these attacks can be prevented by just enabling MFA for your accounts.
From a corporate point of view, MFA can should be forced for all the accounts in your organization. Cloud providers such as Amazon AWS, Google Cloud Platform, and Azure register both incorrect login attempts and successful logins without MFA in their logging services.
Lessons learned about MFA Cloud
If you want to sleep peacefully at night, to reduce the risks of your account being hacked, you need to set up a second authentication factor.
Enable and enforce the usage of MFA for both personal and corporate cloud accounts.
Even if long and complex passwords are secure, relying on a single authentication method isn’t. A password can be stolen instead of guessing. Using multiple-factor authentication enhances the security of your company or even your personal account.
Here at Sysdig, we decided to trigger important events to be registered, so we set up two alarms:
- An alarm that triggers when a user logs in with an account that has MFA disabled.
- An alarm that triggers after x incorrect login attempts in a y time window (x and y can be defined by you). We implemented that kind of “state” because triggering an event every time a user failed login was too noisy.