What is DFIR? Digital Forensics & Incident Response
Digital Forensics and Incident Response (DFIR), a specialized cybersecurity functional sub-field that combines digital investigative services with incident response expertise, was created to address the growing complexity of modern cybercrime. The primary objectives of DFIR are to investigate, detect, contain, and remediate cyberattacks.
DFIR
What you'll learn
-
Why DFIR matters
-
The two main components of DFIR, and how they’re different
-
DFIR tools to consider, and how to pick the right one for your organization
DFIR, as the name implies, combines two major components:
- Digital forensics: A subset of computer forensics that examines system data, user activity, and other digital components of an individual or business to determine whether or not a cyberattack occurred and who might bear the responsibility. Digital forensics entails gathering, analyzing, and presenting digital evidence (such as user activity or system data) to help determine what happened to the system.
- Incident response: A set of procedures used by organizations to anticipate, detect, contain, and recover from a data breach. Once an incident has been identified, incident response procedures are implemented as a security measure for containment, recovery, and issue resolution.
Why is DFIR important?
Over the years, there has been an increase in both the number of endpoints and the occurrence of cybersecurity attacks. These have necessitated the evolution of cybersecurity solutions such as threat hunting, XDRs, and SIEMs, which aid in the identification and remediation of threats. One thing these tools have in common is that they all aim to assist organizations in recovering from an incident. However, they are unable to eliminate the threat and prevent it from recurring. This is where Digital Forensics and Incident Response (DFIR) comes in. DFIR thoroughly investigates cybersecurity incidents and provides a narrative of what happened, thereby helping teams achieve an in-depth understanding.
DFIR experts go above and beyond to collect and investigate voluminous data on cyberattacks in search of any information pertaining to the precise damage caused, the attackers’ method of entry, the resources and data points affected, as well as the profile of the cybercriminals. Advanced artificial intelligence and machine learning techniques are used by DFIR to analyze this data and stop incidents from happening again. Organizations can file lawsuits against identified attackers using the digital forensic data gathered during the DFIR process.
Organizations benefit from using Digital Forensics and Incident Response in a variety of ways, including:
- Organizations can respond to incidents more quickly and accurately with the help of DFIR.
- DFIR improves a company’s overall understanding of its attack surfaces and threat environment.
- DFIR helps businesses recover quickly from security incidents by locating the root cause and eliminating the threat across all their systems. It also helps prevent the recurrence of such incidents.
- Organizations use the data gathered from DFIR processes as evidence when bringing legal action against attackers through the legal system.
How is DF different from IR?
Although both incident response and digital forensics address the same issue—responding to a cyberattack or breach—they differ in process implementation. For example, digital forensics entails collecting and thoroughly examining attack surface data to gain a comprehensive understanding of the scope of the breach in order to remediate the attack and prevent a recurrence. In contrast, incident response focuses on the remediation and containment of a threat or attack.
What is Digital Forensics and its process?
Following an attack, digital forensics is used to answer two main questions: “how did the attack happen?” and “how can we prevent it from happening again?” To accomplish this, digital forensics performs several steps, including identifying and collecting evidence from affected devices (such as latent data from systems), then analyzing it. Once the evidence has been gathered and described, it is examined further to provide a detailed analysis of the root cause of the attack, the scope of the breach, and the extent to which the systems have been compromised.
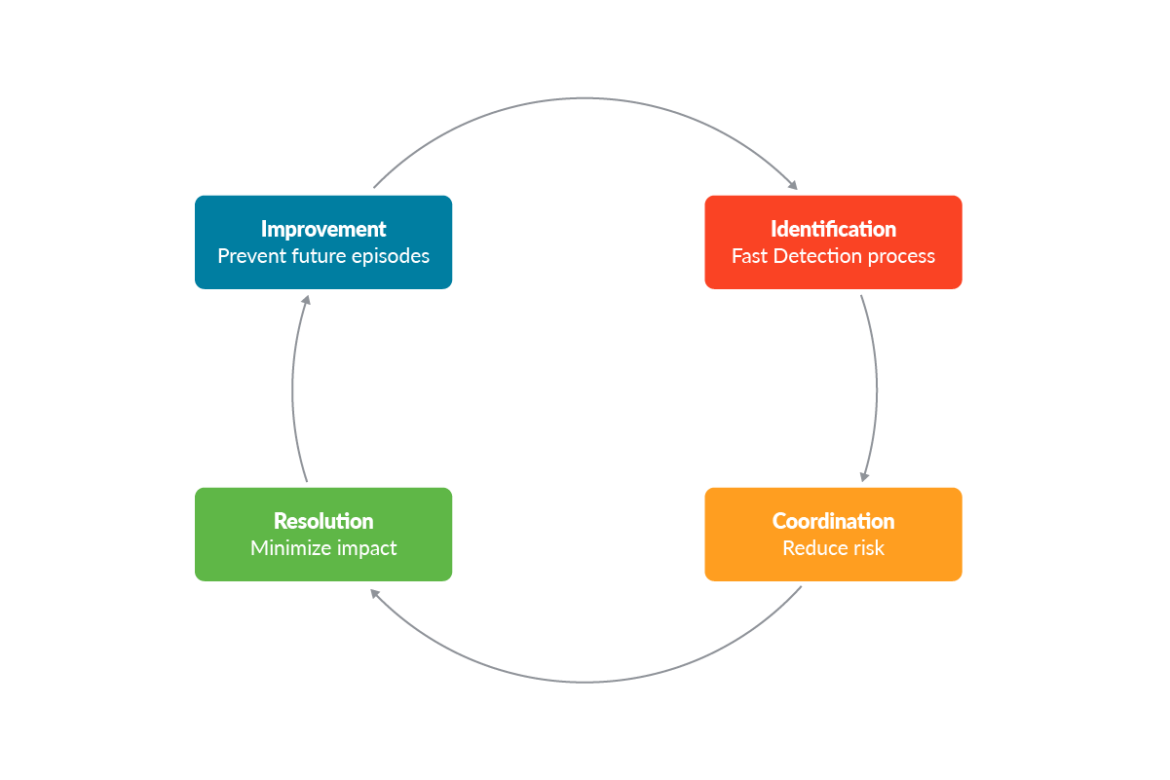
To identify signs of compromise and indicators of an attack based on anomalous events, digital forensics may include log analysis as well as file system, network, and memory forensics.
Typically, the digital forensics process includes several steps, including:
- Identification of security incidents: During the identification phase, technical experts detect the incident and collect evidence concerning when and how it occurred, as well as in which systems. This step necessitates a thorough examination of digital media in order to determine the type of attack that has occurred.
- Evidence preservation: After identifying the security incident and collecting digital attack data, the next step is to isolate, secure, and preserve this evidence for further investigation as well as for regulatory or litigation purposes.
- Forensic data analysis: The collected evidence is then reviewed and analyzed in order to better understand the scope of the attack and draw conclusions about the security incident.
- Documentation of evidence: At this stage, the relevant evidence is documented in order to conduct a thorough investigation.
- Reporting and communication: At the conclusion of the process, the forensics incident manager must communicate the investigation’s findings to the relevant stakeholders while maintaining transparency in accordance with forensics protocols (including the methodology and procedures used for the analysis).
What is Incident Response and its process?
After a security breach or compromise, incident response services are used to manage the incident in real time. Incident response refers to the actions taken immediately following an attack to contain the incident and preserve all evidence for later analysis. A successful incident response requires a team of experts who can handle complex breach events quickly and precisely while preserving the evidence.
A typical incident response procedure includes the following steps:
- Determining scope: The first step in incident response is to assess the incident’s scope in terms of the breadth and severity of the compromise indicators.
- Investigation: Once the scope is determined, the search and investigation process begins. At this stage, teams use advanced systems and threat intelligence to identify threats, gather evidence, and provide detailed information.
- Containment: In order to keep the incident from spreading to other systems, incident managers must secure the active threats and close any identified security gaps.
- Remediation: An incident resolution plan is implemented at this stage to protect the artifacts from the identified threats.
- Incident recovery: At this stage, the organization begins to resume regular operations with policies in place that effectively harden system security weaknesses and mitigate vulnerabilities to strengthen the organization’s overall security posture.
How do you choose the right DFIR tool?
The following are the main factors to consider when deciding between DFIR tools.
DFIR Expert Support
A DFIR tool is only as good as the operators who use it—DFIR experts. When selecting a DFIR tool, consider the level of expert support offered by the service provider to assist in investigations, breach recovery, forensic audits, deep-dive analysis, and other DFIR services.
Forensic Capabilities
A critical purpose of DFIR is to provide a thorough understanding of a security incident while preserving forensic evidence. It is important to assess how a DFIR tool handles such evidence during forensic analysis, considering the challenges in recovering data from a compromised system.
Geographical Reach
Many DFIR cases require onsite support, so global organizations should consider tools from vendors with a physical presence in their geographic location for faster assistance.
Scope of Services Offered
When evaluating DFIR tools, you should consider whether your DFIR use case is proactive or reactive. Some DFIR tools, for example, can be used to prevent future cyberattacks by providing proactive services such as threat hunting, security education, and vulnerability testing. If you want to address a security breach, you should consider reactive tools that aid in incident response and real-time attack investigation.
Affordability
Different DFIR services are priced differently based on coverage and ownership. If you want a free tool, consider an open-source product that is widely supported by a developer community. Some companies may also offer a prepaid, subscription-based pricing model for their DFIR tools.
Accessibility
Regardless of the nature of your organization, you should always select a DFIR tool that is widely available. Some proprietary brands only sell DFIR services to specific law enforcement entities, for example, and they may be inaccessible to other organizations.
Different DFIR tools to consider
Among the most popular DFIR tools available today are:
Volatility
The Volatility Foundation is a non-profit organization whose primary software, the Volatility Framework, is used to promote memory analysis and forensics. The Volatility Framework is open-source software that uses volatile memory (RAM) forensics to respond to incidents and detect malware. This ensures the preservation of evidence located in memory, which would otherwise be lost during system shutdown. Furthermore, the data found in RAM allows you to test the compromised system’s runtime state. The Volatility Framework includes features such as the ability to quickly find Page Table Entry (PTE) flags, the ability to run the Failure command automatically when a service fails to start multiple times, and the availability of custom plugins for Mac. The Volatility tool is available for free on GitHub.
DumpIt
DumpIt is a memory acquisition tool that allows you to take a snapshot of the physical memory of the system. DumpIt is a utility developed by Comae Technologies that combines two tools, win32dd and win64, and allows for the acquisition of both 32-bit (x86) and 64-bit (x64) Windows machines.
YARA
YARA is a free and open-source tool designed to assist security personnel in detecting and classifying malware. It is a multi-platform application that runs on Windows, Mac OS X, and Linux. It can be accessed via its command-line interface or from your own Python scripts using the yara-python extension. YARA employs rules to detect specific files containing specific content.
FTK Imager
AccessData’s FTK Imager is a forensic toolkit that enables you to gather and compile evidence by making numerous copies of the data without changing the original. It detects cybercrime using a wizard-driven method and lets you manage reusable profiles for different investigative needs.
Other examples of DFIR tools include Wingman, ELK Stack, Offline Registry Finder, RegRipper, Plaso, and Sysmon. Finally, if you are working on Kubernetes environments, we recommend to follow the practical guide for DFIR Kubernetes.
DFIR best practices
Some of the best practices that organizations should consider when implementing DFIR include:
- Examine and identify threats in the organization’s systems through the use of forensic telemetry and artifacts (such as file events and operating system artifacts). Examples include event logs, registry files, memory dumps, transaction information, and threads.
- Conduct a thorough post-mortem attack analysis to determine the root cause of security incidents.
- Use a variety of criteria to search for, locate, and collect all information relevant to a specific security breach from systems, endpoints, and any suspicious files.
- Remediate and deal with the various components of a threat while also closing any security gaps to prevent recurrences.
Organizations trying to reduce cyberthreats and strengthen their security posture must implement Digital Forensics and Incident Response procedures. Adopting a powerful DFIR tool will give them the ability to manage security across their entire system infrastructure and also help them investigate, analyze, and prevent cyberattacks.


