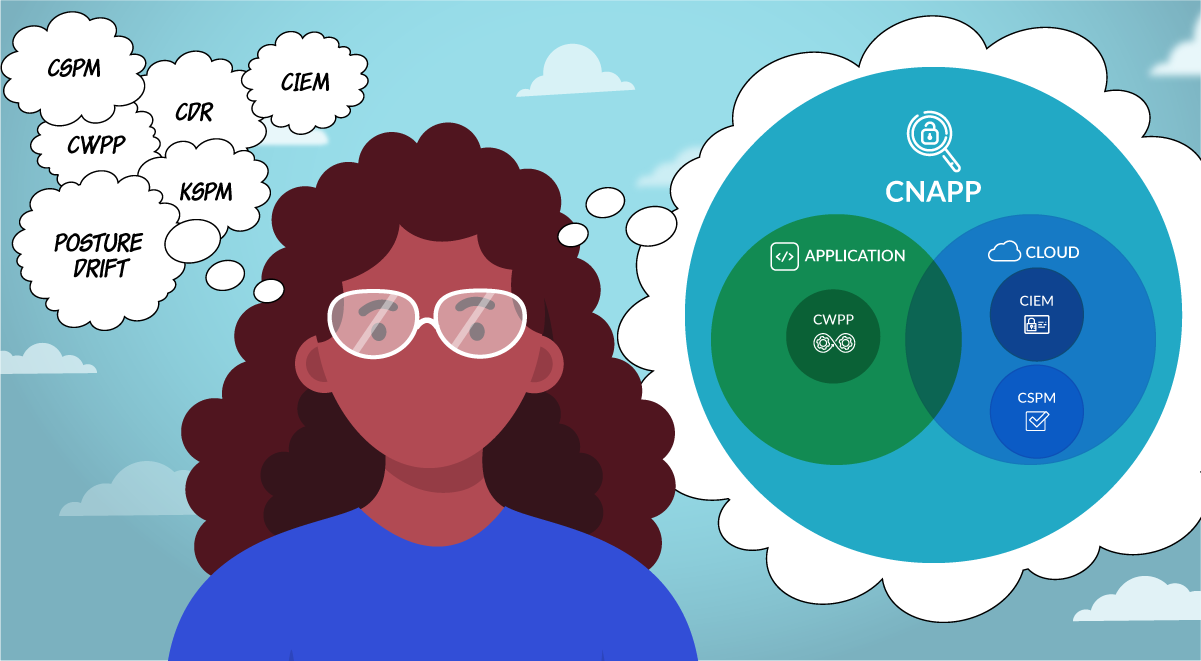
Cloud Native Application Protection Platforms – or CNAPP solutions – are steadily gaining traction as the best solutions to address Cloud Native security.
Regardless of your cloud adoption maturity (whether you’re PoC-ing some services in the cloud, running a few applications, or fully embracing this new era), we’re sure you have likely already noticed that cloud-native security is different from IT-managed data center security. But how exactly is it different? A recent Gartner survey found that 50% of participating organizations indicated a lack of internal knowledge about cloud-native security. That’s no surprise if we think about how rapidly things evolve in the cloud.
In this blog post, we are going to review some of the terms you keep hearing from vendors, cloud providers, and security training courses so you understand what to focus on to really protect your cloud environments.
Gartner, Forrester, IDC, and 451 Group are some of the most well-known analyst firms that identify and describe emerging trends in the market and create definitions for new technologies. They have coined terms you know, like SIEM, CRM, and WAF. But they’ve also coined Posture Management or CSPM, Vulnerability Management, CWPP, Entitlements and Permissions or CIEM, among others.
The 2023 Gartner® Market Guide for Cloud-Native Application Protection Platforms (CNAPPs) has generated a stir among security leaders. Do you need another tool? What is CNAPP? Where does this new term fit in? Is Posture Management no good anymore? Can we forget about CWPP?
The truth is that CNAPP is just the logical convergence between Vulnerability Management, CSPM, and identity-based security, plus some other goodies. With so many tools working in silos, it was getting harder and harder to prioritize risk within cloud-native applications and its associated infrastructure. CNAPP’s offerings are bringing together multiple disparate security and protection capabilities into a single platform.
Let’s find out step by step.
Vulnerability Management
It all started with DevOps teams moving their workloads to the cloud.
In order to secure the whole DevOps workflow, security teams needed to make sure those applications were safe for the final user, and that’s what Vulnerability Management tools focus on. They protect cloud workloads from security flaws, like vulnerabilities, that bad actors can abuse to gain access to sensitive data for their shady purposes.
Use cases behind Vulnerability Management:
- Vulnerability scanning: Detecting OS and non-OS vulnerabilities from running images in production.
- CI/CD and Registry scanning: Scan from container images stored in CI/CD and registries before deploying to production. Adopt in-line scanning to maintain control of images and only ship scanned results to production.
- Vulnerability prioritization: Prioritization of vulnerabilities tied to active packages.
- System hardening: Protecting Linux hosts or VM-based workloads running on top of the host by reducing its vulnerability surface with restrictive configurations as a preventive control.
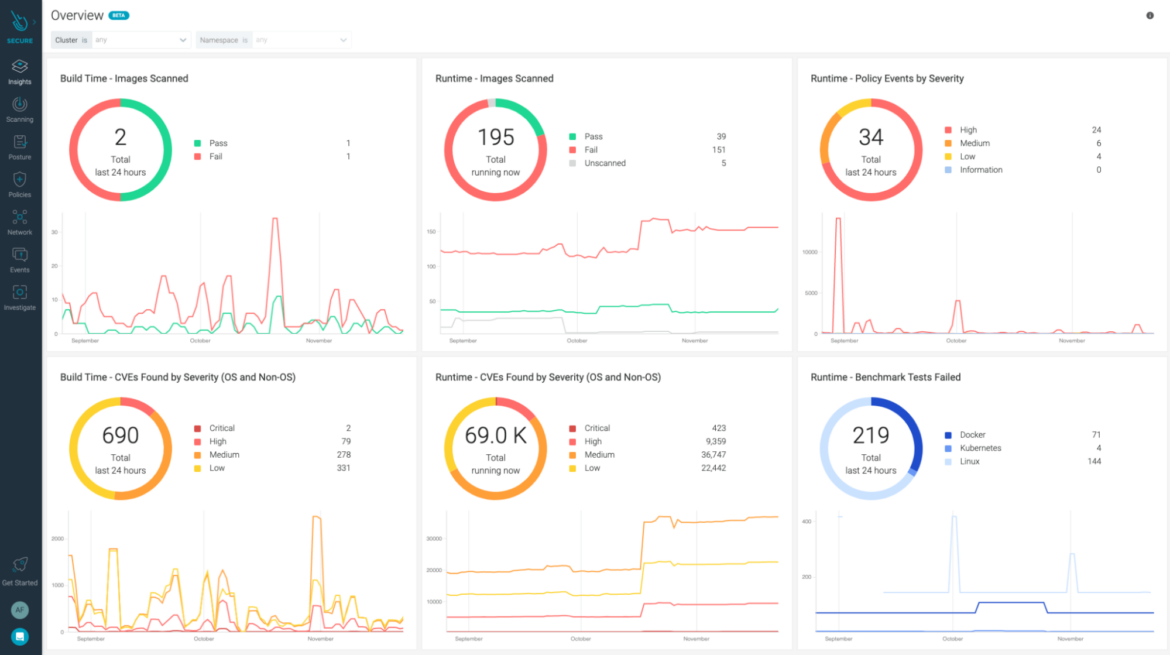
As everything in the cloud is interconnected, let’s see how the combination of other tools in a CNAPP solution generates a better outcome than what we would have with single isolated products.
Cloud Detection and Response or CDR
CDR stands for Cloud Detection and Response. CDR aims to protect the dynamic, expanding attack surface of cloud environments with real-time detection of misconfigurations, vulnerability exposures, and suspicious activities. So, it’s the real-time detection piece that comes into play when we talk about CDR.
Common use cases for CDR would be:
- Workload runtime detection: Preventing and detecting suspicious behavior at runtime in containers and microservices.
- Cloud Threat detection: Warning us about unusual activity in the cloud, like an S3 bucket with sensitive data made public or a privileged account accessed without MFA.
- Network security: Visualizing network traffic inside containers and Kubernetes, and enforcing Kubernetes-native network segmentation.
- Incident Response: Conducting forensics and incident response for containers and Kubernetes even after the container is gone. Automating response for container threats.
CDR itself can be the difference between an attack contained and a massive breach. However, combining it with vulnerabilities, misconfigurations, or identities insights increases SOC team speed by providing detection events with full context, reducing the time to understand what, where, who, and root cause.
Are you starting to see the power of correlating insights between the different siloed tools?
Posture Management or CSPM
As workloads moved to the cloud and DevOps teams began to provision their own infrastructure, security teams that used to have a controlled environment in on-premises data centers found themselves losing control over who did what in the cloud. The perimeter had widened. Like in local data centers, security professionals had to ensure compliance in the host instances, user accounts, and data privacy. But the lack of visibility to know what assets they have in the cloud makes it really difficult to keep track of misconfigurations in those assets.
Cloud-bound teams must also quickly adapt to the new paradigm of the cloud infrastructure environment (immutable infra, policy as code, and identity as the new perimeter, among others). Thus, cloud security teams needed a different approach.
Modern Posture Management is the tool that unifies different use cases aimed at protecting the cloud control plane, essentially tracking cloud resources and verifying the static configuration of the cloud.
What use cases does Posture Management cover?
- Compliance: Validating container and cloud compliance and ensuring File Integrity Monitoring inside containers and hosts.
- Misconfiguration Management: Scanning for misconfiguration early in the pipeline, integrating security and compliance seamlessly and transparently into modern DevOps, and avoiding dragging errors to production environments.
- Prioritization and Remediation: Extended capabilities, like providing better identification, prioritization, and remediation of cloud-native application risk.
- Real-time Posture Drift detection: Detecting in real-time when you deviate from your security posture at runtime.
Getting notified if a violation occurs lets teams take action to prioritize its remediation.
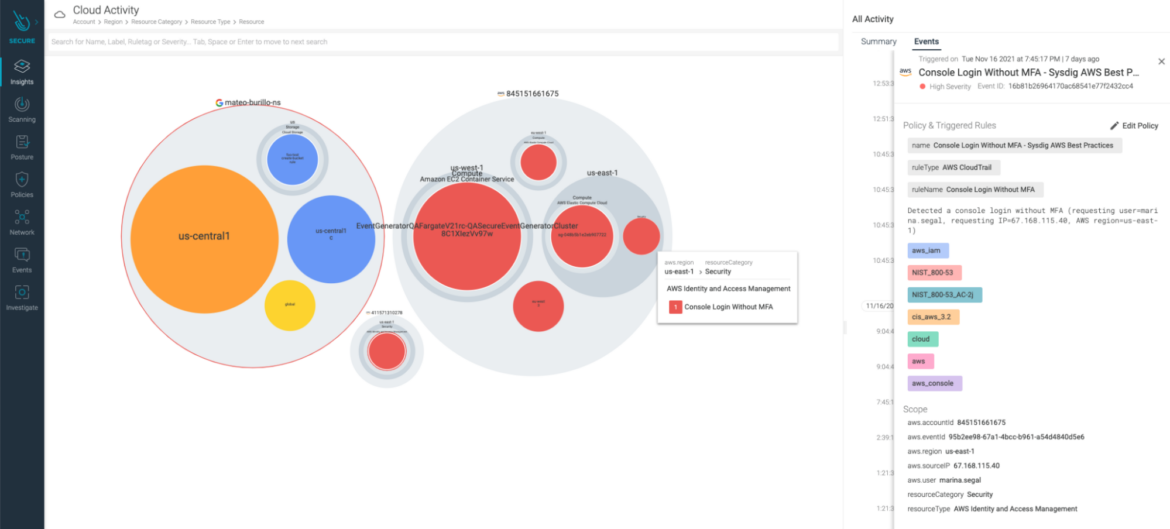
CIEM
Identity Management and data privacy are also important aspects of a cloud security program.
As mentioned, when the perimeter was the local data center, it was easier to control who had access to what. Now, even serverless functions can act like users accessing data.
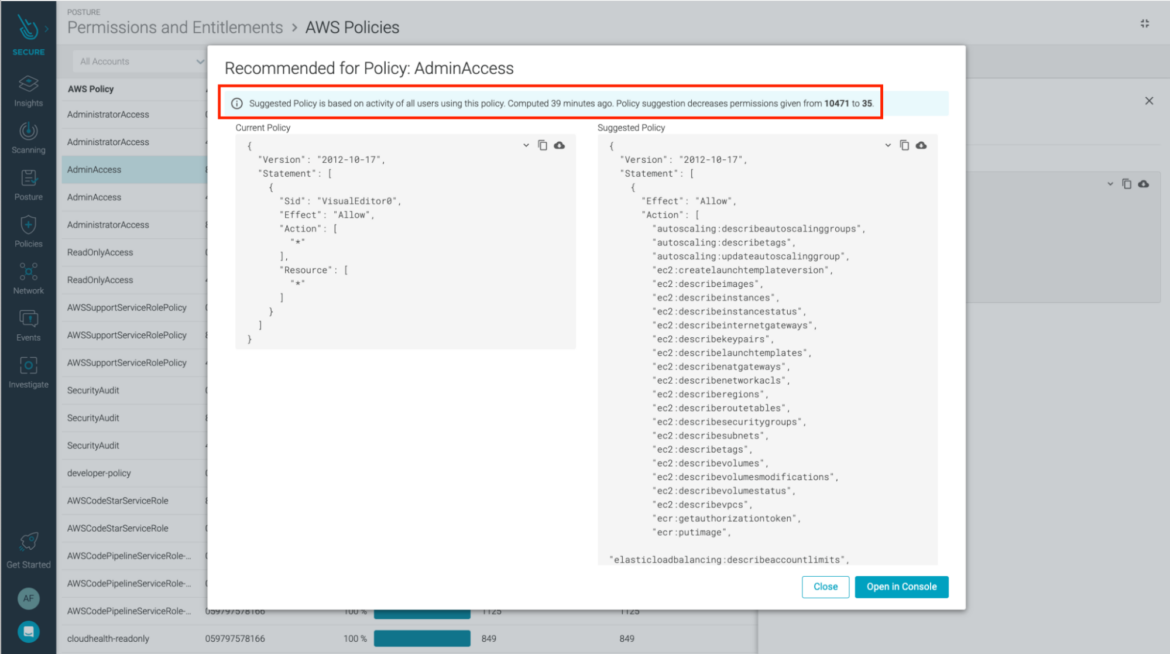
To address the cloud permissions gap, we have Cloud Infrastructure Entitlement Management (CIEM). With CIEM, you would not only know which human and non-human identities can access which resource, but what permission they are using on a daily basis. You can also suggest policy modifications to enforce least privilege access.
Let’s say we have a group of users who are part of a project. These users are responsible for uploading images into an ECR repository and running those containers in EC2 instances, as well as a number of auto-scaling actions. There’s no need for them to have all the permissions an administrator has, even though that approach may be the simplest to configure. Are they going to be deleting VPCs? That is not one of their tasks. Getting rid of excessive permissions is the first step to reducing collateral damage from credential theft.
Finally: CNAPP
If you made it here, congratulations! You are about to uncover the figure after connecting the dots. CNAPP is the combination of different use cases that fall into the Vulnerability, Posture, and Identity Management categories, but let’s go to the source:
“CNAPPs consolidates a large number of previously siloed capabilities, including container scanning, cloud security posture management, infrastructure as code scanning, cloud infrastructure entitlement management, runtime cloud workload protection, and runtime vulnerability/configuration scanning.”
Gartner, Inc., Market Guide for Cloud-Native Application Protection Platforms, Neil MacDonald, Charlie Winckless, Dale Koeppen, 14 March 2023.
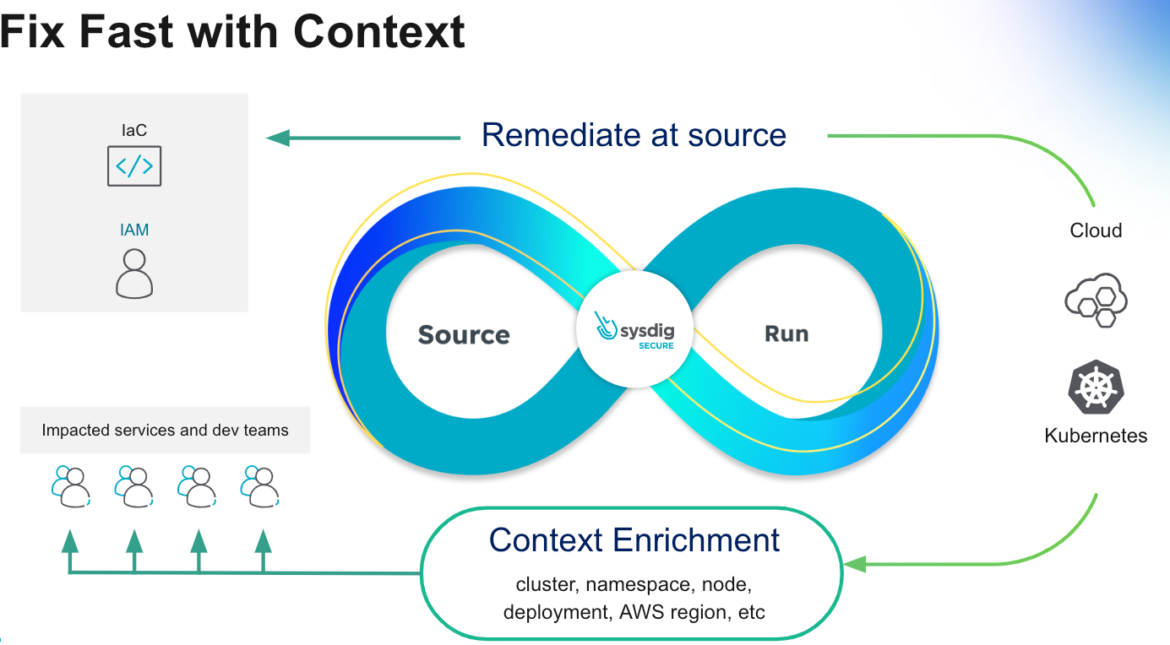
We hope CNAPP and the rest of the terms make more sense now than when you started reading the article.
Conclusion
CNAPP solutions will promote collaboration between teams (SecDevOps, DevOps, and cloud security operations) by incorporating common workflows, data correlations, meaningful insights, and remediation that’d reduce friction between the personas.
True CNAPP solutions will provide interrelationships between the different insights of the use cases. It’s totally useless to have a nice UI that provides vulnerability scanning if you don’t enrich it with the cloud context of where those images are stored/running. We are not talking about isolated tools put together to call it a day, but rather a comprehensive security platform that enriches data and workflows with meaningful context on every step.