VMware Tanzu Security from Source to Run
Get a single view of risk across containers, Kubernetes, and cloud
Security and Visibility for VMware Tanzu
Sysdig is driving the standard for cloud and container security. With our platform, VMware customers find and prioritize software vulnerabilities, detect and respond to threats, and manage cloud configurations, permissions, and compliance.
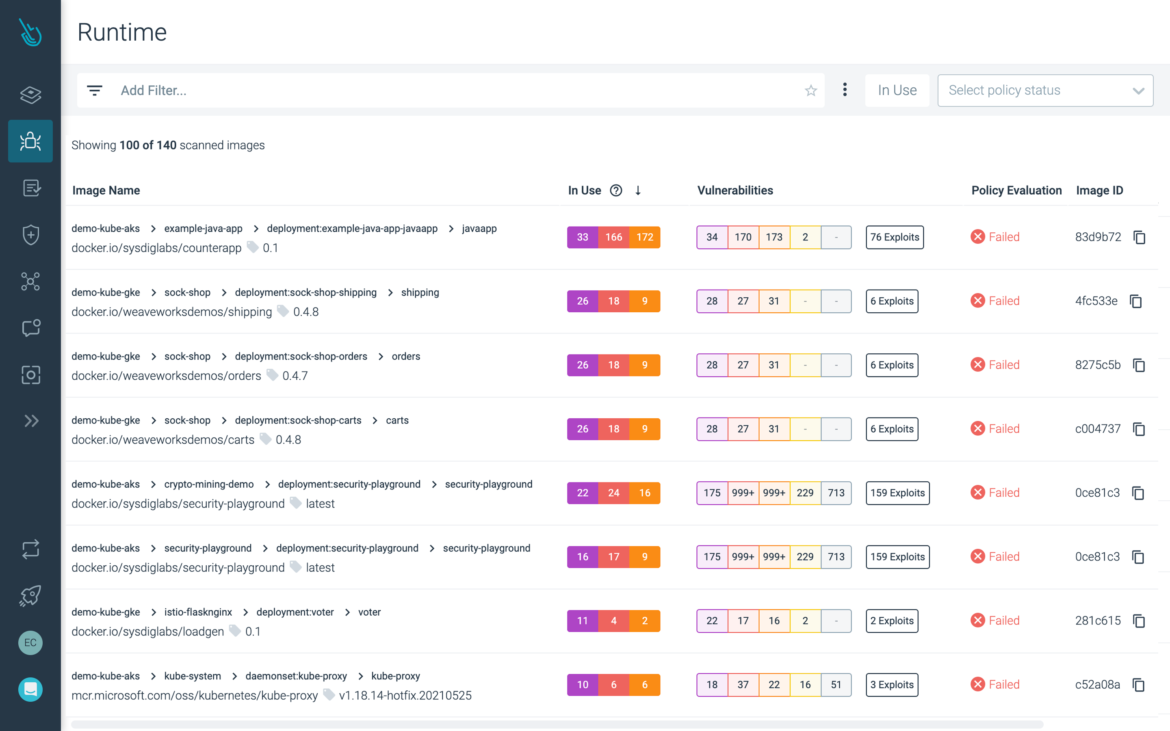
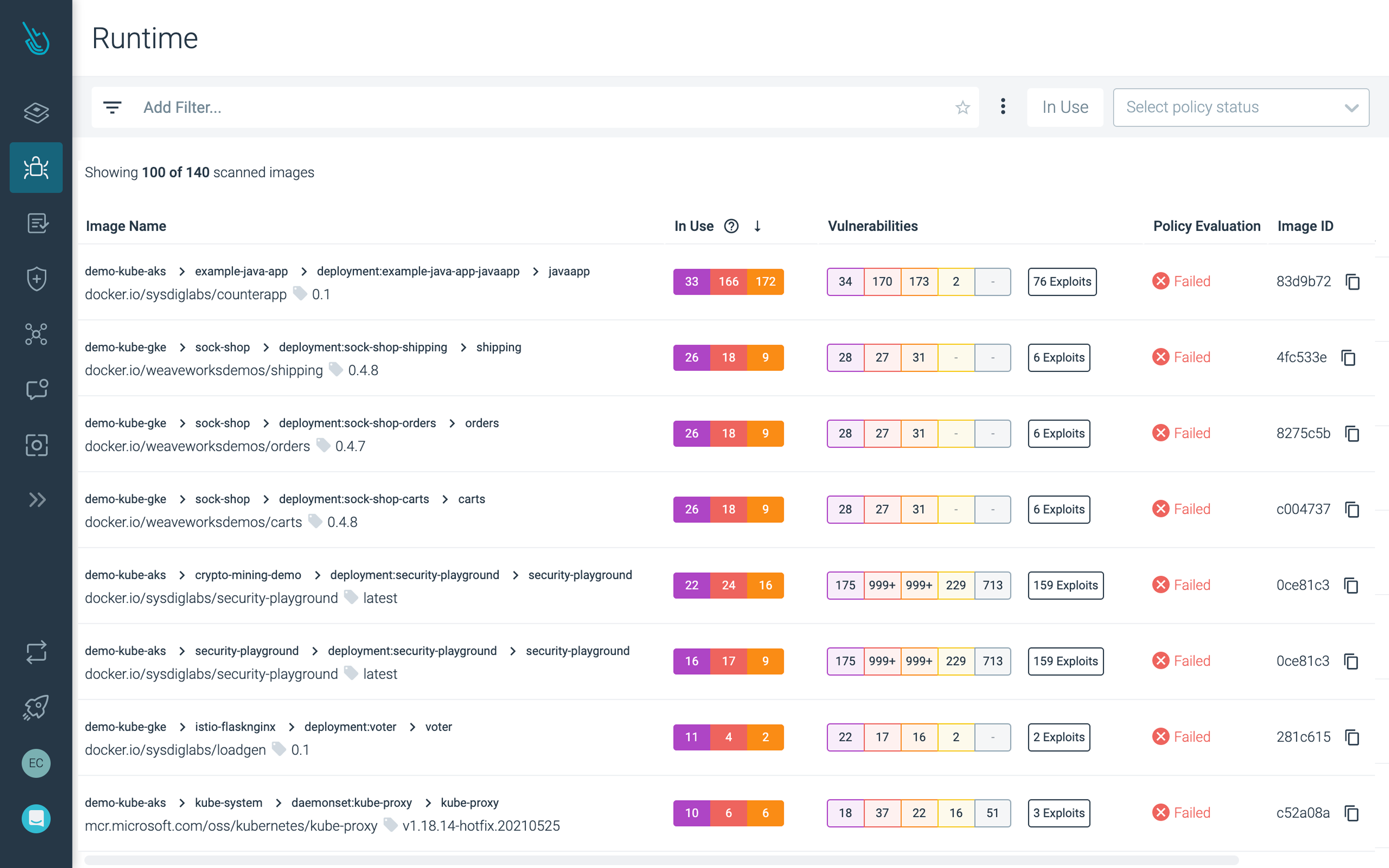
Find and prioritize vulnerabilities
Automate image scanning in CI/CD pipelines and registries. Prioritize vulnerabilities based on runtime context and risk.
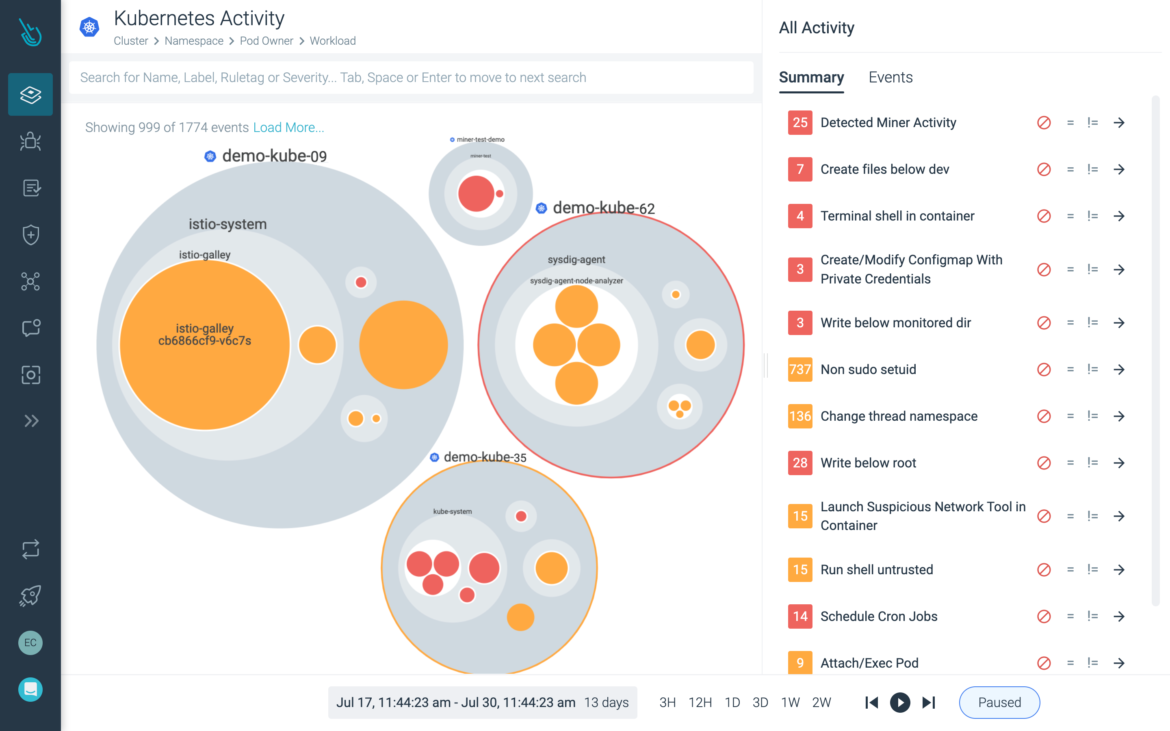
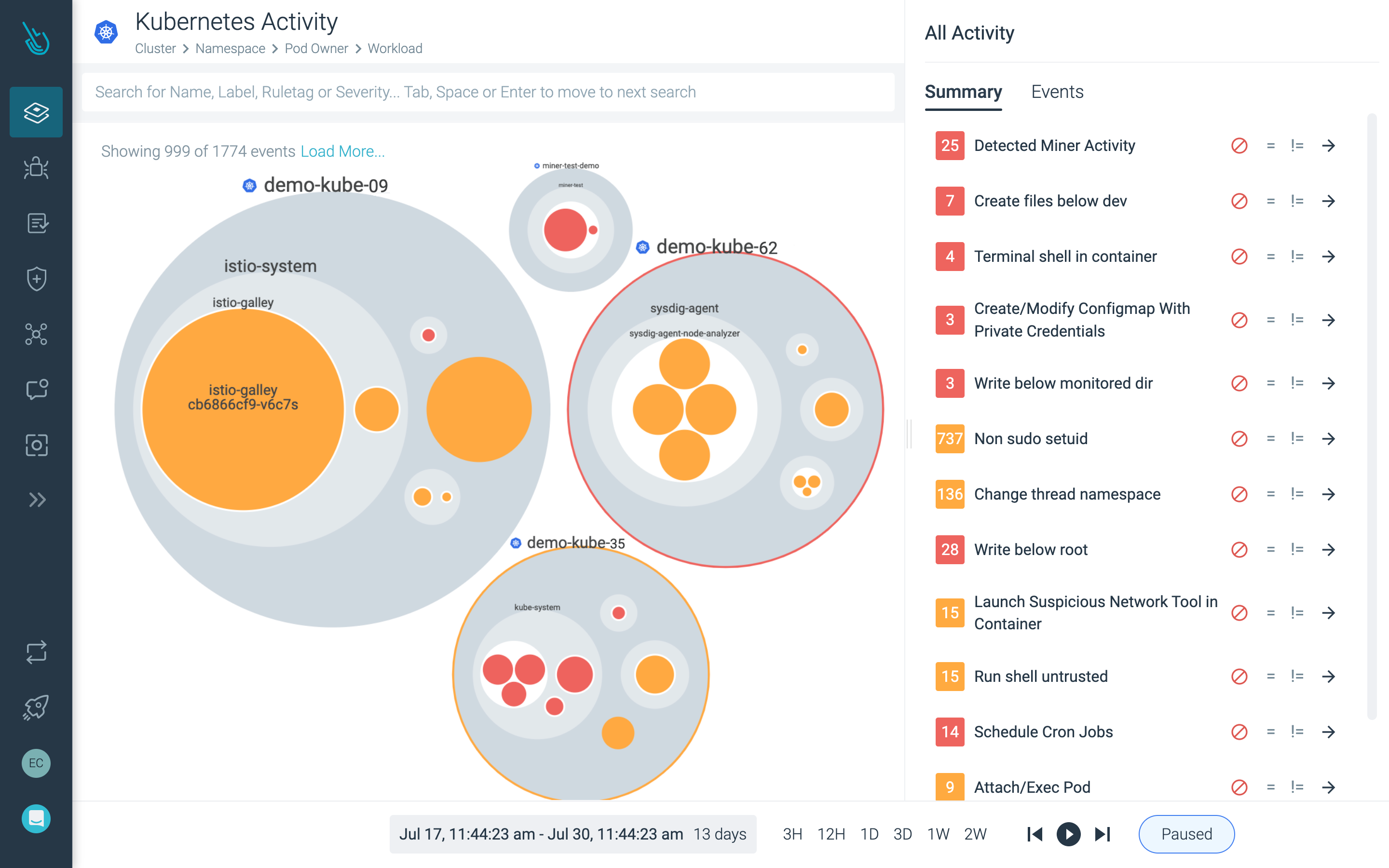
Detect and respond to runtime threats
Identify suspicious activity across your VMware Tanzu infrastructure and workloads with threat detection based on open source Falco.
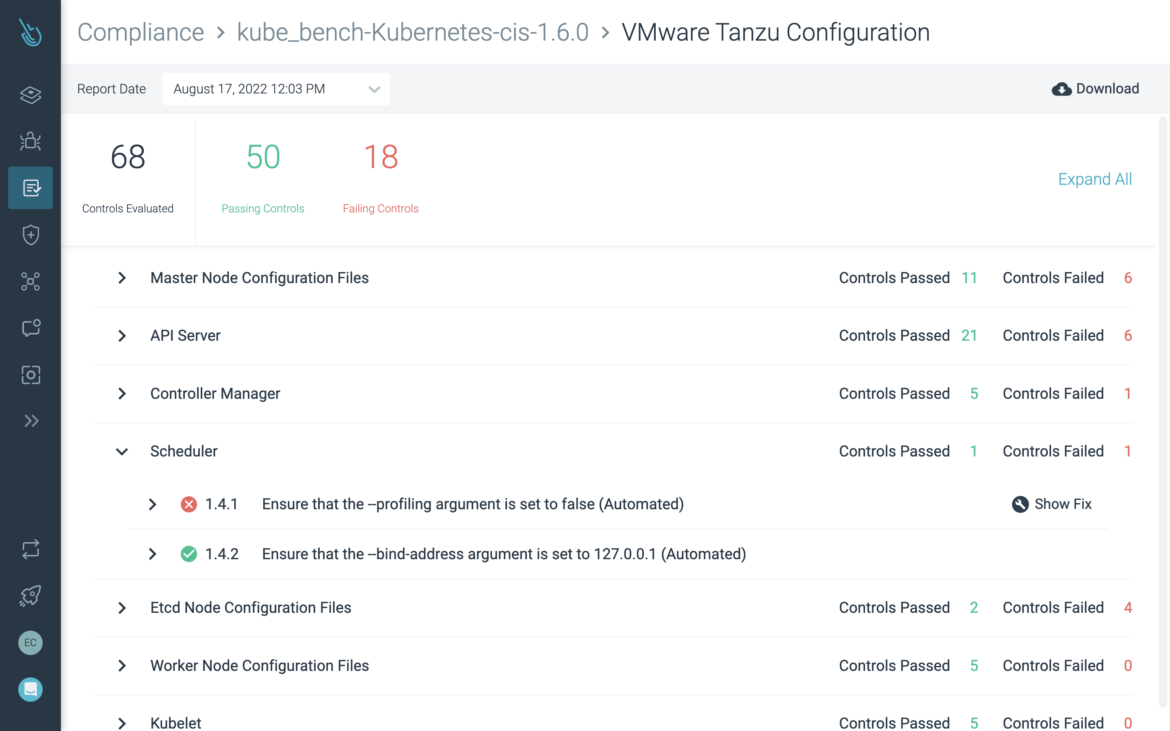
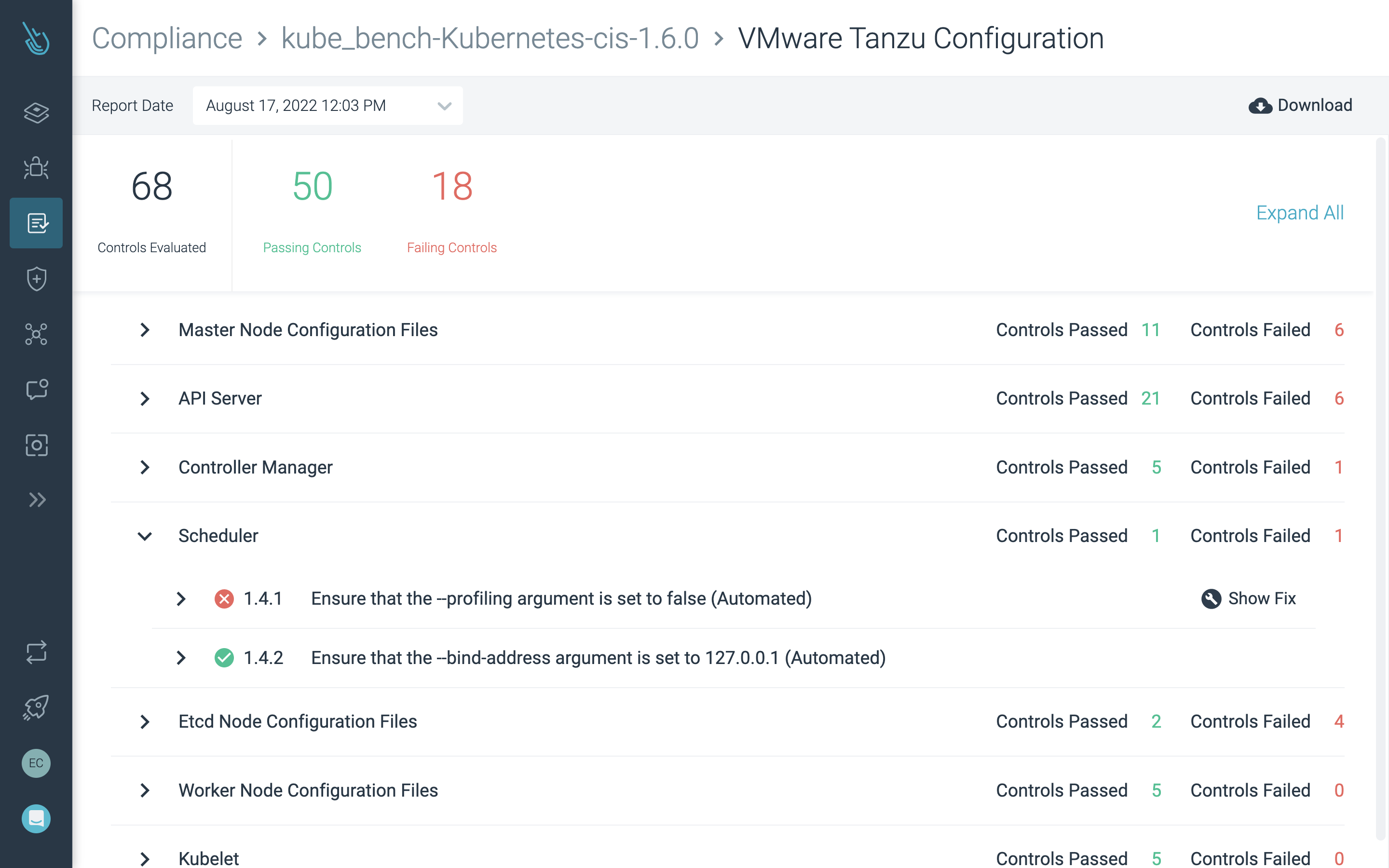
Continuously validate configurations and compliance
Automate Kubernetes, container, and cloud compliance for PCI, NIST, SOC2, and more. Quickly identify and fix misconfigurations.
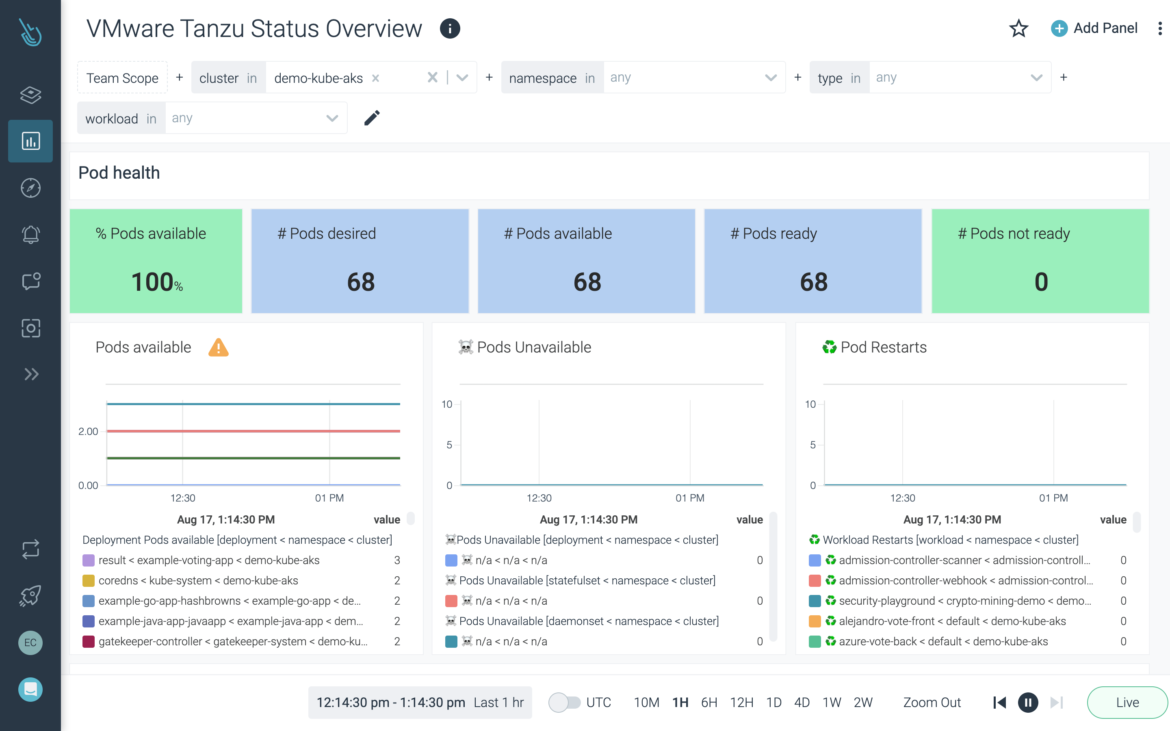
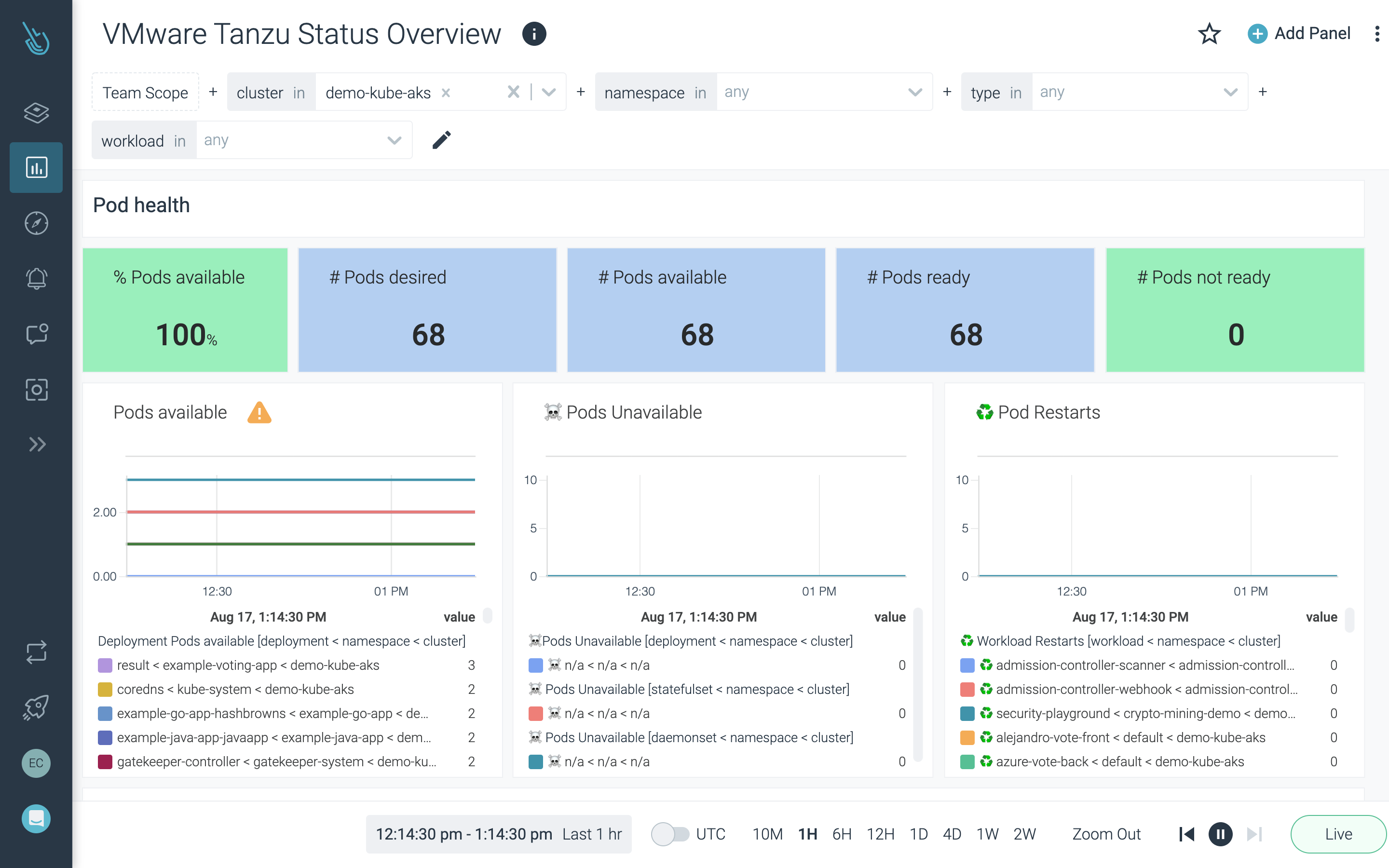
Maximize performance and availability
Scale container and Kubernetes monitoring with full Prometheus compatibility to troubleshoot and resolve issues faster.
Security and Monitoring Use Cases for VMware Tanzu
VMware
Integrations
Converging security and compliance with performance and capacity monitoring to create a secure DevOps workflow
Click on a logo to view the integration.Featured Resources
Take the Next Step!
See how you can secure every second in the cloud.





