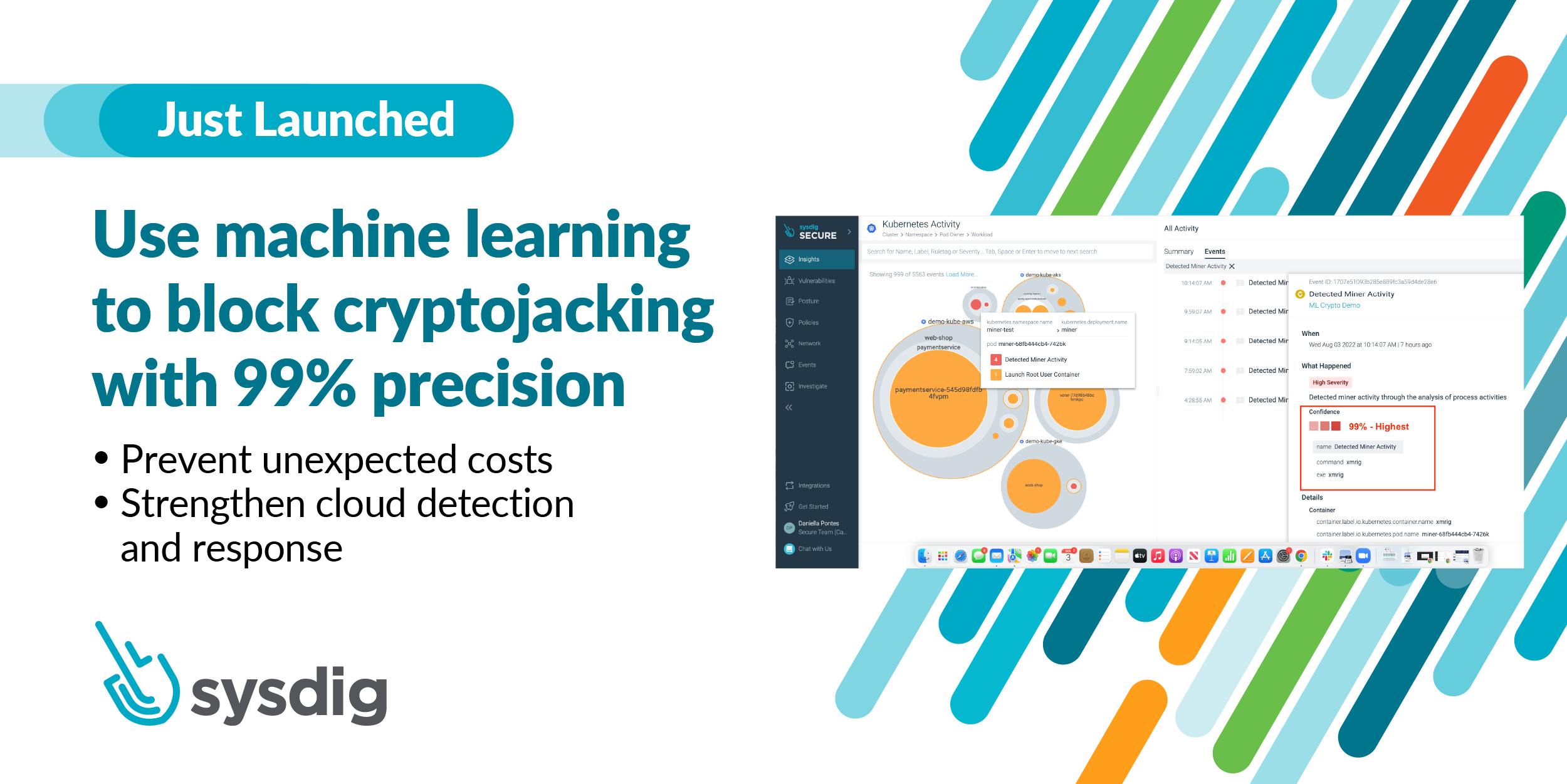
Company strengthens cloud detection and response to prevent unexpected cloud costs
LAS VEGAS — BLACK HAT (Booth #1760) — August 10, 2022 – Sysdig, the unified container and cloud security leader, today announced machine learning-powered cloud detection and response (CDR) to combat cryptojacking. The company’s threat engine and detection algorithms block cryptojacking in the cloud with 99% precision. Cryptojacking is the unauthorized use of someone else’s compute resources to mine cryptocurrency. According to the Google Cloud Threat Horizons Report, 86% of compromised Google Cloud instances were used for cryptocurrency mining. Cryptojackers use low-and-slow attack techniques to mask what they are doing so those impacted do not realize until they receive their cloud bill. The longer cryptojacking goes undetected, the greater the financial impact. While the average increase in a monthly bill varies by report, it is not uncommon for cryptojackers to run up a $100,000 – $500,000 bill in a single month. Time is of the essence.
While the cloud and on-premises security challenges seem similar, the attack patterns and detection techniques are fundamentally different and require different approaches. Traditional tools lack the visibility into container environments and breadth of coverage needed to identify threats and anomalies at runtime. A multi-layered approach that includes curated rules and machine learning is better suited to address the complex threats in cloud environments. To detect threats like cryptojacking, teams need machine learning algorithms that are trained and tuned to recognize cryptocurrency mining patterns immediately to avoid unexpected cloud fees, which can have a significant financial impact.
Read “Cryptominer detection: a machine learning approach” to learn how Sysdig trained its machine learning detection model.
Sysdig Machine Learning-Powered Cloud Detection and Response
- Block cryptominers with 99% precision: Sysdig Secure machine learning is trained to automatically detect cryptominers. Even as new cryptojackers come into play, highly precise and continually evolving algorithms keep the model up-to-date and drastically reduce false positives.
- Prevent unexpected costs: Early detection is the only way to avoid hefty cryptojacking bills and reputation damage due to an attack. Sysdig is able to detect behavior patterns even if the cryptominer slowly ramps up use of cloud resources.
- Strengthen security with a multi-layered approach to cloud detection and response: Effective protection in today’s threat landscape requires multiple protection layers. Sysdig threat detection uses machine learning to complement a rules-based approach based on Falco. Easily customizable out-of-the-box policies curated by the Sysdig Threat Research Team maximize coverage. Adding defense techniques, such as profiling, comprehensive indicators of compromise (IOCs), and Drift Control further strengthen security.
“Machine learning is not a silver bullet for detecting threats. Many vendors throw around ‘ML’ quite loosely for solutions that are not true machine learning,” said Omer Azaria, Vice President of Engineering at Sysdig. “Cryptojacking is a specific use case where machine learning provides effective detection. Sysdig developed an ML algorithm that is specifically tuned to detect cryptojacking before your cloud bill skyrockets.”
Availability
Sysdig Secure customers have access to the machine learning-powered threat detection now and for new customers, it is included in Sysdig Secure at no additional cost.
Resources
- Read: Cryptominer detection: a machine learning approach
- Read: Detect cryptojacking with Sysdig’s high-precision machine learning
- Read: The beautiful lies of machine learning in security
Media Contact
Amanda McKinney Smith[email protected]
703-473-4051
In the cloud, every second counts. Attacks unfold in minutes and security teams must protect the business without slowing it down. Sysdig, named Customers’ Choice in Gartner® “Voice of the Customer” report for Cloud-Native Application Protection Platforms (CNAPPs), stops cloud attacks in seconds and instantly detects changes in risk with real-time insights and open source Falco. Sysdig Sage™, the industry’s first AI cloud security analyst, uplevels human response and enables security, developers, and DevOps to work together, faster. By correlating signals across cloud workloads, identities, and services, Sysdig uncovers hidden attack paths and prioritizes real risk. From prevention to defense, Sysdig helps enterprises focus on what matters: innovation.
Sysdig. Secure Every Second.