Recently, IBM announced the IBM Z and Cloud Modernization Center for the acceleration of hybrid cloud and to help IBM Z clients accelerate the modernization of their applications, data, and processes in an open hybrid cloud architecture. By pairing IBM Z systems built for transactional integrity, throughput, reliability, and availability with hybrid cloud development, IBM is combining the best of both worlds. To ensure that this new generation of modern mission-critical applications is secure and compliant, Sysdig is introducing its world-class cloud-native monitoring and security platform for IBM Z and IBM LinuxONE.
Modernizing IBM Z applications implies the use of modern DevOps practices, open-source technology, and Kubernetes managed containers to simplify the deployment of microservices. In using Kubernetes, however, clients need to be aware that:
- IBM Z development teams are increasingly using the same Docker, Jenkins, Red Hat OpenShift, Github, Tekton and other CI/CD pipeline tools utilized in DevOps
- Traditional Endpoint Detection Response (EDR) which relies on signature scanning is simply ineffective in a container environment
- The security risks associated with cloud applications now represent a real threat
This last point deserves special attention. In the Red Hat State of Kubernetes Security Report, Red Hat found that 94% of the respondents to their survey experienced a security incident over the last 12 months. Likewise, the 2021 IBM Security X-Force Cloud Treat Security Landscape Report revealed that 100% of their penetration tests of cloud environments found issues with passwords or policies.
Furthermore, in the Sysdig 2022 Container Security and Usage Report we found that 75% of our client’s container images contained patchable vulnerabilities of “high” or “critical” severity across third-party libraries and standard operating system packages. As today’s application ecosystem is highly dependent on these images and technologies, this has serious implications in terms of opening the door to malicious attacks.
Strengthening the security of hybrid cloud with IBM Z and Sysdig
IBM Z provides always-on encryption of data, both at rest and in flight, with hardware security modules that meet the highest levels of FIPS certification (FIPS 140-2 level 4). Modernizing on IBM Z requires expanding the inherent IBM Z security capabilities to cloud-native and container environments.
In developing the cloud-native security and monitoring capability for IBM Z, Sysdig focused on:
- Leveraging the same tools, techniques, and platforms that DevOps teams have been using for years
- Employing a simple, lightweight security agent based on system calls vs. batch analysis of log files
- Utilizing the same open-source distributions of Falco, Sysdig, and Prometheus that are already in widespread use
Sysdig’s overall objective is to ensure that container-based IBM Z systems applications are safe, secure, and compliant. Sysdig also believes there is a high degree of synergy between the Sydig and IBM client base. For example, over 75% of enterprises have adopted Kubernetes-managed containers. Given the fact that Sysdig is already installed in over 40 banks and insurance companies that are using Kubernetes, and that IBM Z powers most of the world’s major financial institutions, Sysdig expects rapid adoption of this innovative security approach.
A new and different approach to security
Today’s CI/CD pipelines are built primarily on open-source toolings such as Kubernetes, Docker, Jenkins, GitLab, and Tekton. Sysdig advocates for open source and strives for the adoption of open-source standards. Sysdig has an engineering team dedicated to contributing to some of the top open-source cloud security and monitoring tools. Sysdig incorporates the power of open sources tools and standards for its SaaS solution – Falco for runtime security, Sysdig for incident response, Cloud Custodian for cloud governance, Open Policy Agent for policy control, and Prometheus for collecting metrics.
Sysdig Secure is based on Falco, an open-source activity monitoring platform for containers. In fact, Falco has become the de facto Kubernetes threat detection engine with over 40M downloads. Falco is the first runtime security project to join CNCF as an incubation-level project. Falco acts as a security camera detecting unexpected behavior, intrusions, and data theft in real-time. Sysdig created Falco on the premise that behavioral approaches were superior for detecting what is happening on a system vs. attempting to identify each possible exploit, vulnerability, or attack.
Conventional EDR looks at network packets and malware signatures in a never-ending game of catch-up. These traits severely reduce the effectiveness of traditional host and network-based security in the cloud. In contrast, our approach alerts you when suspicious or anomalous activity is occurring vs. attempting to prevent intrusion, to begin with.
Within the behavioral space, the fundamental novelty of Sysdig Secure lies in the fact that our agent sits at the OS interface level. This allows Sysdig to monitor virtually every interaction with potential security implications via system calls. For example, processes are created through syscalls, file and network IO happens through syscalls, and signalling is done through syscalls. Sysdig is distinctly different in other ways:
- File integrity monitoring: One way to do file integrity monitoring is to periodically scan all files of interest, compute their checksums, and compare with the checksums of the previous phase. Because scanning every file constantly is impractical, they are run periodically. With Falco, we can watch for any OS activity that is written to every file of interest and receive alerts in real-time.
- Network monitoring: As workloads moved to VMs and then containers, it has become increasingly hard to reconcile network traffic with application activity using network-based IDS systems. Furthermore, these EDS systems are inextricably tied to signatures, since you can only observe a small slice of system behavior from network traffic. With Falco, one can see I/O “from the inside”, with an immediate correlation between applications and traffic.
Architectural considerations in adapting Sysdig Secure to IBM Z
Sysdig Secure is available on Linux on IBM Z and IBM LinuxONE and its lightweight agent interrogates containers, orchestration APIs (Kubernetes, OpenShift) and metrics from Prometheus endpoints, as well as the host itself and maintains a permanent communication channel with our backend database in the cloud or on-premises.
That channel is protected using standard TLS encryption for transmitting data to and receiving configurations from our backend, including runtime policies or compliance benchmarks. Once agent messages are received, they are processed as time series, infrastructure and security events, and metadata. The use of agents allows clients to respond immediately by blocking the execution of malicious processes, logging forensic information, and capturing telemetry about the potentially nefarious activity.
Because cloud workloads are often ephemeral, lightweight, and highly dynamic, Sysdig developed a highly scalable database well suited for enterprise-scale deployments. Given that 44% of containers live less than five minutes as reflected in our usage report, Sysdig has seen high levels of churn in factors like container id or pod name, resulting in even small clusters generating thousands of data points and hundreds of thousands of time series. As a result, the Sysdig platform has been tested in production with over 100,000 nodes, 100 million time-series, and billions of data points from containers, images, processes, and network connections.
Visualizing results
The Sysdig agent taps into the stream of IBM Z events and checks each event against the list of rules in its configuration file. This security, performance and forensics data is combined into intuitive dashboards that can be leveraged for multiple use cases. For example, the below dashboard summarizes activities pertaining to Kubernetes clusters on the IBM Z infrastructure; This quickly gives the user an idea about any suspicious activity happening at the workload/pod/namespace or the cluster level.
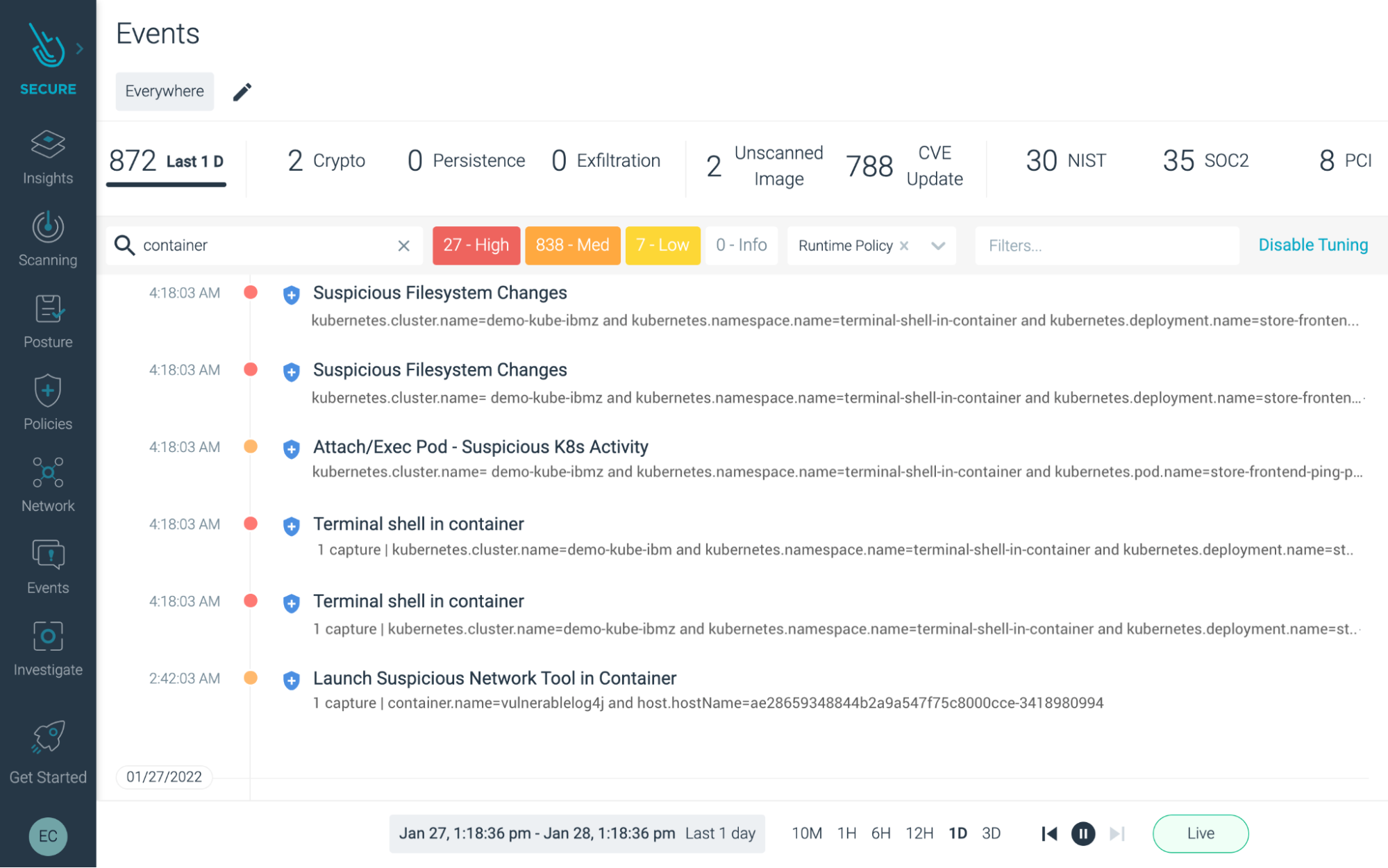
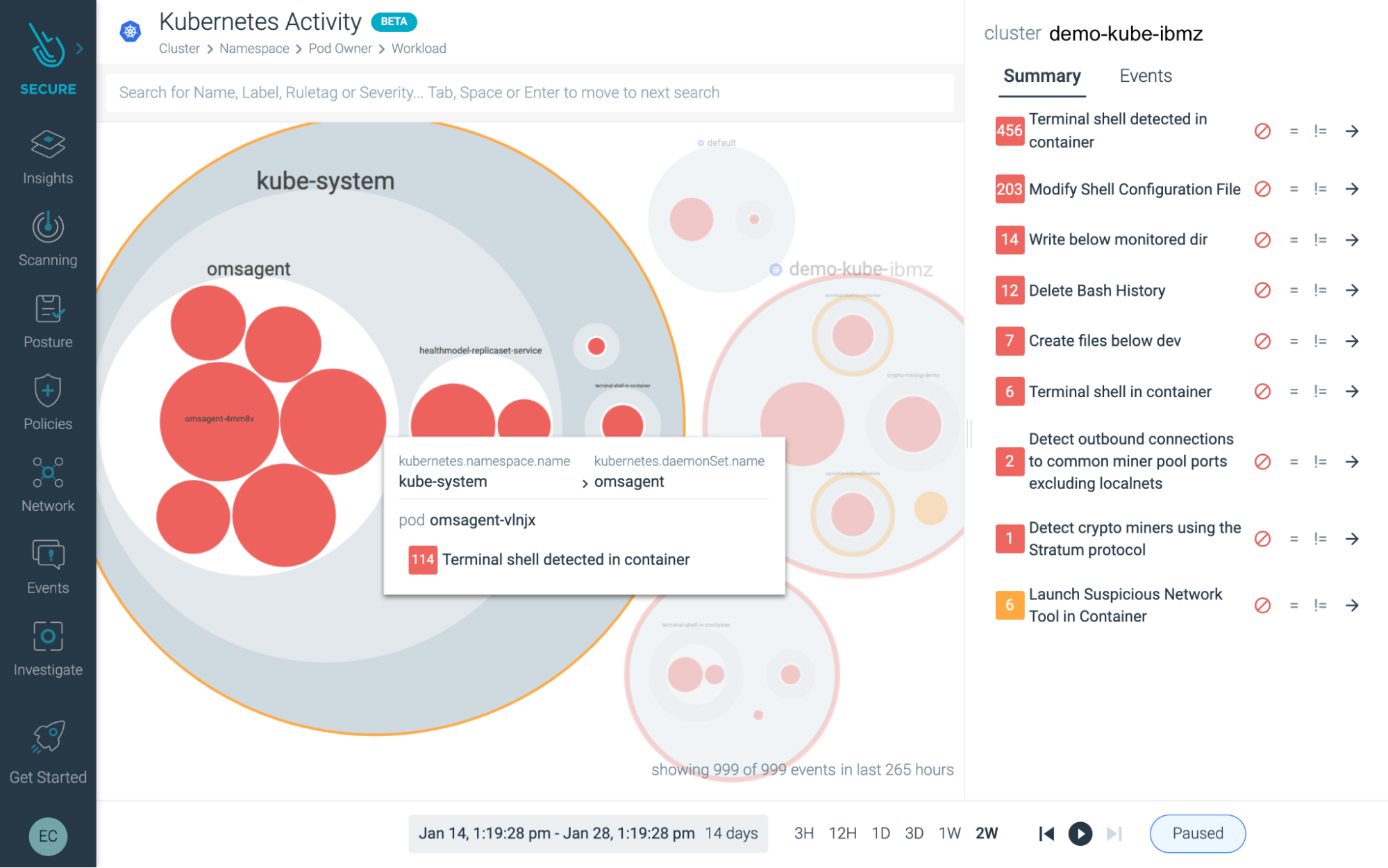 Then the user can “dig deeper” and take a look at all the events that transpired in the background during that timeframe to conduct further forensic analysis.
Then the user can “dig deeper” and take a look at all the events that transpired in the background during that timeframe to conduct further forensic analysis.
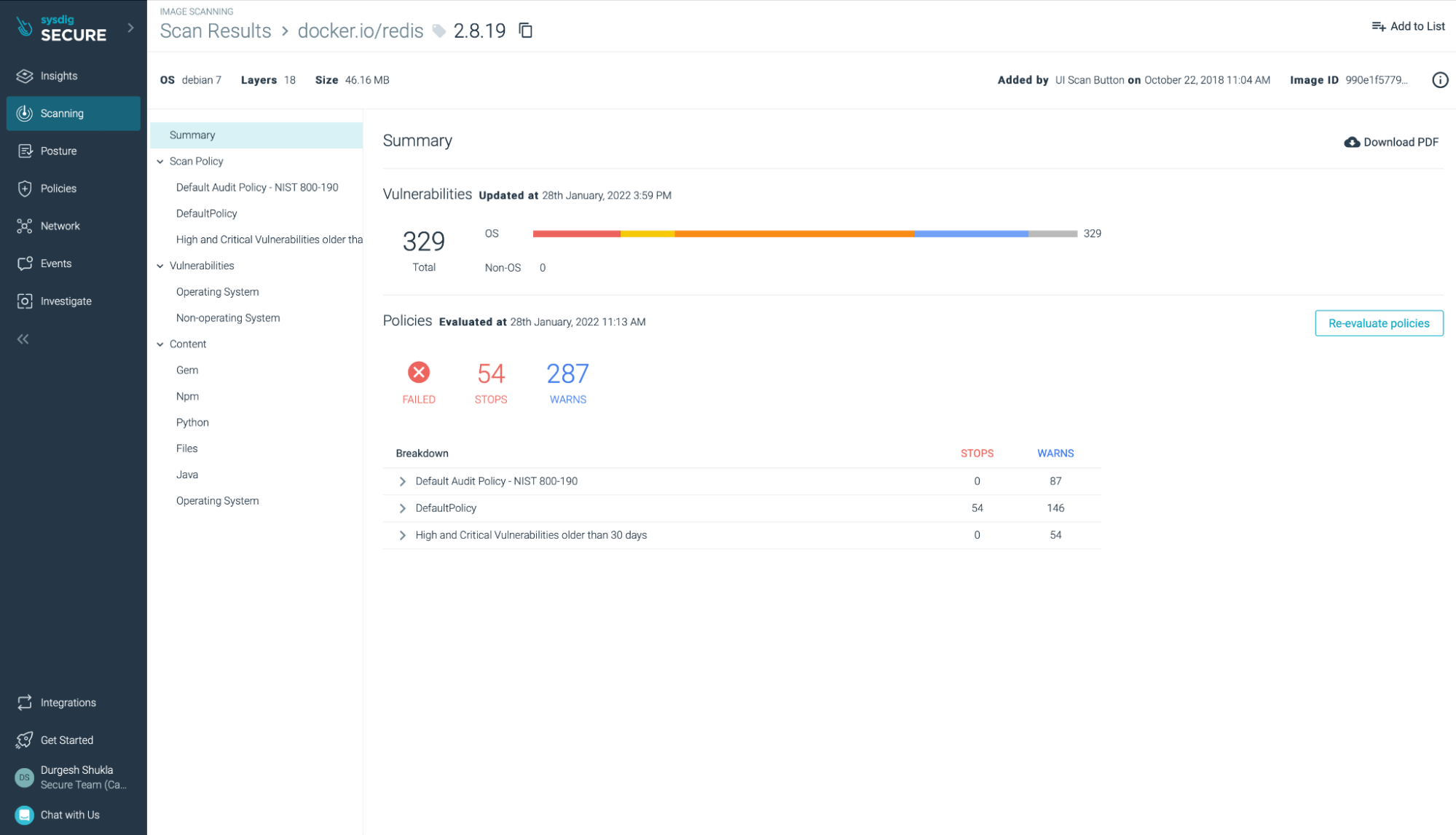
Further, for runtime (and build time) Sysdig Secure provides scan results that show vulnerabilities present in images for any registry, OS or Non-OS settings. These scans can include policies as necessitated by the compliance requirements.
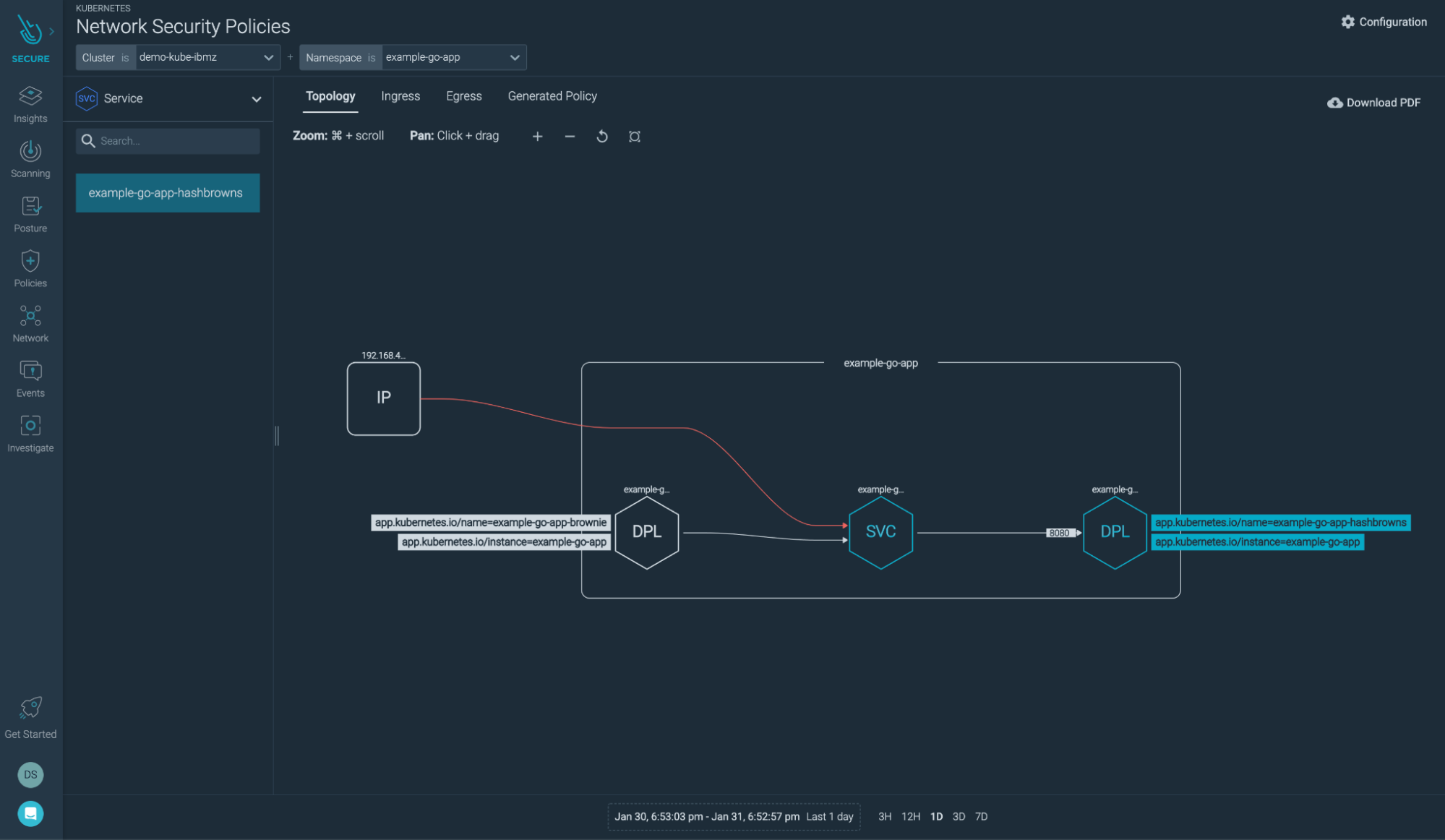
Another interesting feature that Sysdig Secure has is showing the network topology view for various apps running across different clusters and namespaces:
Please note that you can supplement your security events data and actions with some really in-depth data and metrics about different workloads from the Sysdig Monitor tool as well. The Sysdig Monitor and Secure tools share the same agent for these data and metrics collection activities.
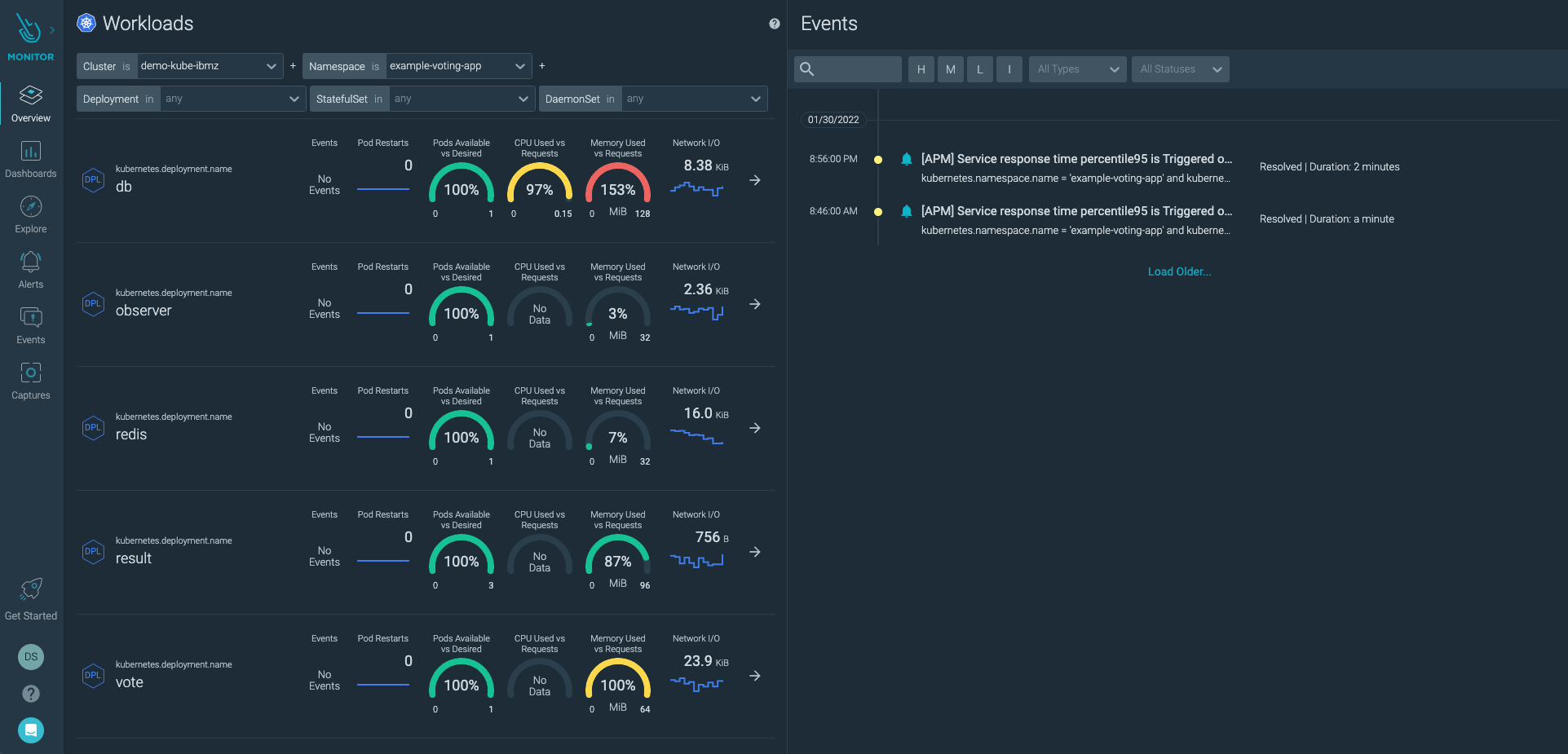
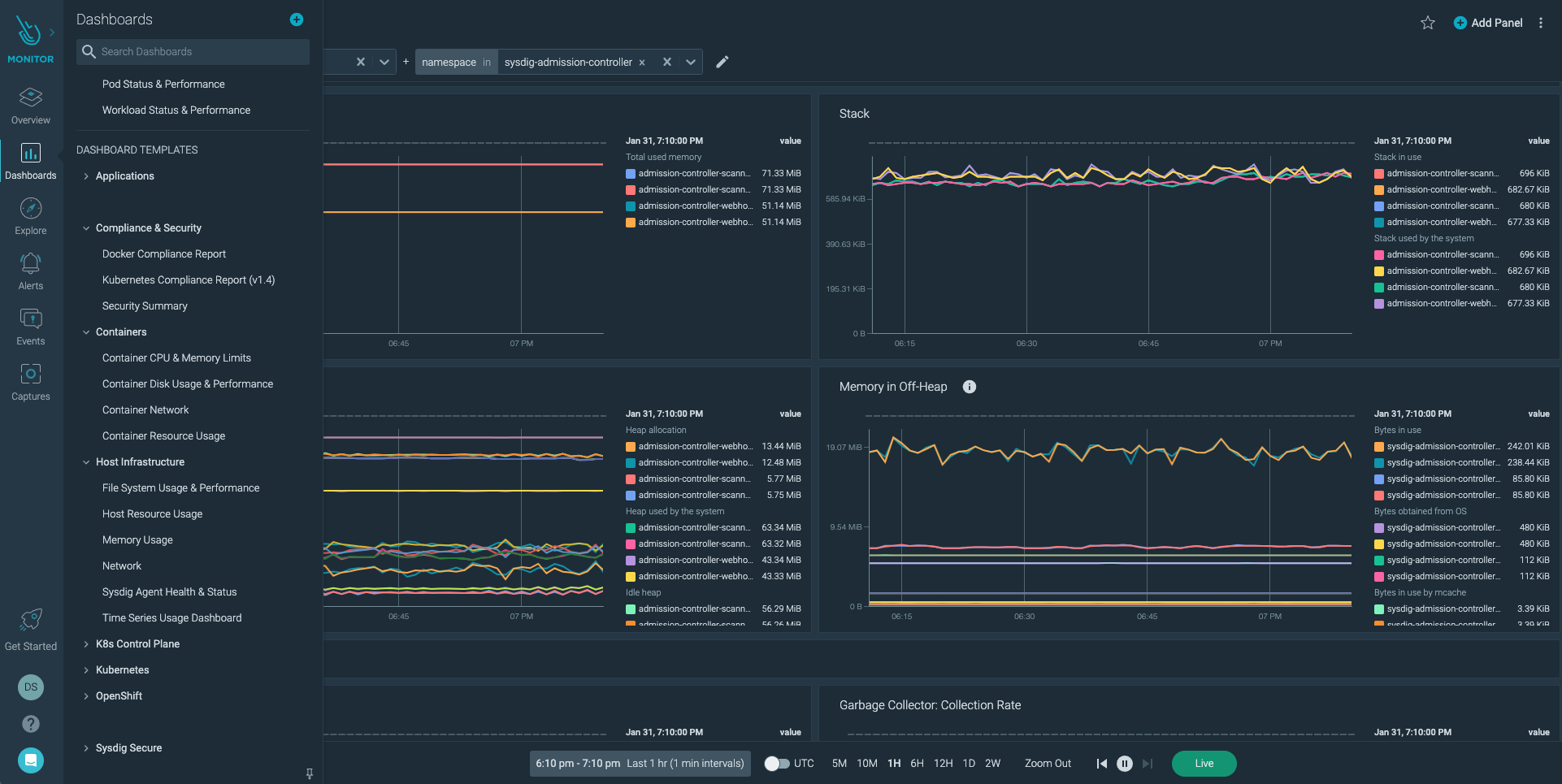
A rich set of dashboards based on the required metrics can be built within Sysdig Monitor and several of these dashboards templates come pre-built and ready to use right out of the box.
Sysdig and IBM Z and IBM LinuxONE – Partnering for customer success
The advent of a new open-source, cloud-based security platform for Linux on IBM Z and IBM LinuxONE represents a breakthrough for the modernization of applications, data, and processes. Sysdig believes that will fill a critical gap in behavioral security monitoring by using an agent that is lightweight, easy to configure, works seamlessly with containers and scales to billions of events. Sysdig is pleased to join the IBM Z and Cloud Modernization Center and support enterprises in their digital transformation and modernization journey with the adoption of this mutual solution.
In this new paradigm, programmers contribute code and security teams contribute rules for detecting threats and validating compliance, while commercial versions add features, integration, visualization, analysis, workflows, and machine learning. Sysdig and IBM partnership will be at the forefront of that new open-source security wave.
Resources
- IBM Partner Page on Sysdig.com → https://sysdig.com/ecosystem/ibm/
- Red Hat Partner Page on Sysdig.com → https://sysdig.com/ecosystem/red-hat/
- Sysdig Secure Product details → https://sysdig.com/products/secure/
- Sysdig Monitor Product details → https://sysdig.com/products/monitor/
About Sysdig
Sysdig is driving the standard for securing the cloud, empowering organizations to confidently secure containers, Kubernetes, and cloud services. The Sysdig platform enables teams to secure the build, detect and respond to runtime threats, and continuously manage cloud configurations, permissions and compliance. Sysdig is a SaaS platform built on an open-source stack that includes Falco and Sysdig OSS, the open standards for runtime threat detection and response. The largest and most security-conscious companies rely on Sysdig for container and cloud security. Learn more at sysdig.com.


