There’s an important shift happening in the cloud security industry: organizations are looking for an integrated platform that connects the dots between several key security use cases from source through production. Whether it is for tool consolidation, consistent end-to-end experience, or “one throat to choke,” customers are increasingly choosing a platform-based approach to address critical cloud security risks.
This line of thinking is why Sysdig has been laser-focused on providing a unified cloud and container security experience for our customers. From our perspective, with the introduction of the 2023 Gartner® Market Guide for Cloud-Native Application Protection Platforms (CNAPPs), this trend is finally becoming the mainstream approach.
What Is a CNAPP?
Cloud Native Application Protection Platforms (CNAPPs) combine functionality for Cloud Security Posture Management (CSPM), Cloud Workload Protection (CWP), Cloud Infrastructure Entitlement Management (CIEM), and Cloud Detection and Response (CDR) security into one security platform. These integrated capabilities allow DevOps to ship applications fast without security becoming a bottleneck while also allowing security teams to manage risk and defend against attacks.
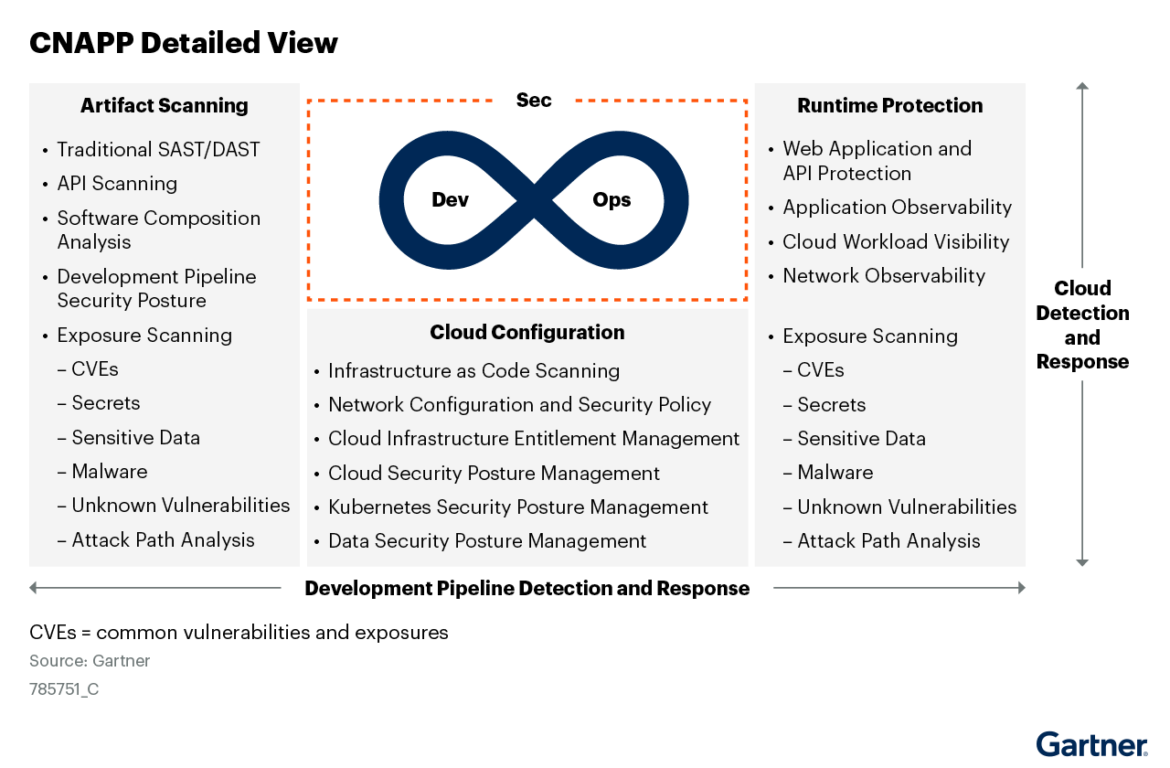
Why Do Security and DevOps Teams Need a CNAPP?
Visibility gap when moving to cloud and containers: Empowered developers are configuring infrastructure at will and deploying containerized microservices with the click of a button. Now you have dynamic workloads with 10–100X more containerized compute instances, large volumes of cloud assets with dynamic activity to track, and messy and overly permissive IAM permissions to manage. Without a single tool that analyzes these data sources, blind spots emerge and risk abounds.
Point solutions don’t work: Oftentimes customers must choose from among multiple solutions, or even choose vendors that stitch together a workflow from multiple acquisitions. Regardless of the approach, these tools don’t communicate with each other and share context. Teams are stuck wading through disparate vulnerability findings, posture violations or threats, forcing them to deal with issues as one-off issues vs addressing them as a priority stacked-rank list based on risk and impact.
Talent shortage. Development teams and infrastructure expanded faster than security teams, and there is a shortage of cloud-native security talent. Customers are looking to partner with a trusted leader in this space, one that can provide an opinionated workflow to address these challenges.
Why CNAPP Needs Runtime Insights
A CNAPP by definition is a data platform that ingests and analyzes multiple data sources. The data volume is exploding, as you factor in the adoption of microservices built on containers/Kubernetes. This can quickly result in a gargantuan volume of both high and low fidelity signals, ultimately resulting in the question: how do I focus on the most critical risks in my cloud native infrastructure?
This is where having deep knowledge of what’s running right now can help you shrink down the list of things that need attention first. Simply put, knowledge of what’s running (a.k.a. runtime insights) is the necessary context needed by security and DevOps teams to take action on the most critical risks first. Ultimately, this context can be fed back early in the development lifecycle to make “shift-left” use cases of CNAPP better with actionable prioritization.
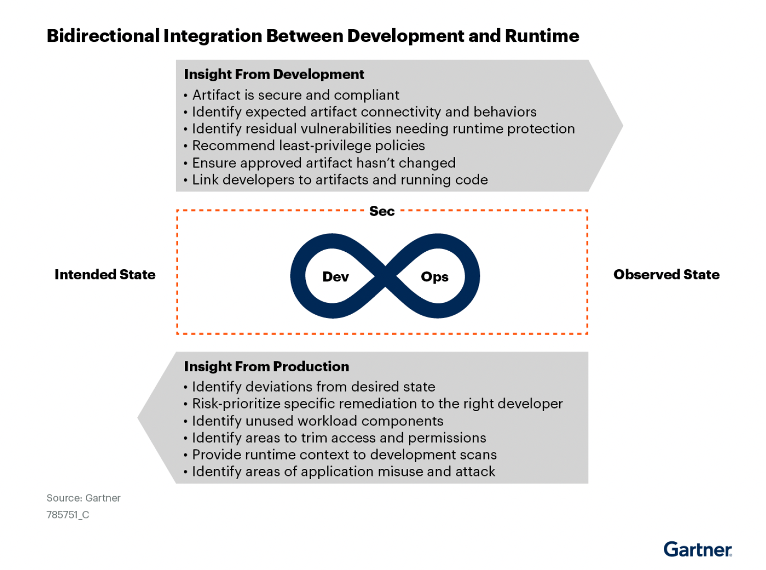
In addition, many customers are starting to see detection and response as a first class citizen within CNAPP. Their need is starting to expand beyond just workload runtime security, and address the cloud control plane (via analyzing cloud logs) to detect suspicious activity across users and services. This subset of CNAPP is seen more as cloud detection and response, and will also evolve further to fill the gaps left by EDR or native capabilities from cloud and platform providers.
Recommendations for Security Professionals When Evaluating a CNAPP
In the Market Guide for Cloud-Native Application Protection Platforms (CNAPP), Gartner® shares several recommendations for security and risk management leaders. Based on our understanding from the report, we’ve provided several questions to help you navigate the buying process.
Do they address a broad set of security use cases from source to production? This includes capabilities such as:
- IaC security
- Scanning IaC manifests to identify misconfigurations and security risks before deployment while preventing drift
- Vulnerability management / Supply chain security
- Identifying, prioritizing, and fixing vulnerabilities across your software supply chain (SCM, CI/CD, registry and runtime environments)
- Configuration and access management
- Hardening posture by managing misconfigurations and excessive permissions across cloud environments (cloud resources, users and even ephemeral services like Lambda)
- Threat detection and response across cloud workloads, users and services
- Multi-layered detection approach that combines rules and ML based policies, enhanced with threat intelligence, along with a detailed audit trail for forensics/IR.
- Compliance
- Meeting compliance standards for dynamic cloud/container environments against PCI, NIST, HIPAA etc
Can they accurately prioritize what matters? Prioritizing the most critical vulns, configuration or access mistakes based on in-use risk exposure is key. For example:
- Understanding which packages are in-use at runtime, helps you prioritize the most critical vulnerabilities to fix. Our research shows that 87% of container images have high or critical vulnerabilities, but only 15% of vulnerabilities are actually tied to loaded packages at runtime.
- Real-time cloud activity helps immediately spot anomalous behavior/posture drift that are most risky
- Runtime access patterns help to highlight the excessive permissions to fix first.
Also the ability to provide remediation guidance that ultimately helps teams to make informed decisions directly where it matters most – at the source.
Can they maximize coverage but also give deep visibility? Evaluate whether CNAPP vendors provide deep visibility and insights across your entire multi cloud footprint, including IaaS and PaaS, extending across VM, container, and serverless workloads. This often includes both agentless for visibility and control, as well as deep runtime visibility based on instrumentation approaches like eBPF.
Are they truly getting a consolidated view of risk? Some vendors acquire multiple companies to check the box, and this results in a poor disjointed experience. Look for a CNAPP vendor that tightly integrates the source to production use cases, replacing multiple point products with a comprehensive picture of risk across configurations, assets, user permissions, and workloads.
Are they allowing customizations? Every organization is different. The ability to customize policies, filter results and accept risk based on the organization’s unique environment is key to successfully adopting a solution.
Are they tightly integrated with the DevOps and security ecosystem? The CNAPP tool must integrate with CI/CD tools and scan for misconfigurations and vulnerabilities pre-deployment as well as with SIEM/notification tools trigger alerts / forward events so teams can act immediately. Guidance on how to fix is key; the tool needs the ability to map the violation back to the IaC file, provide situational awareness when investigating an alert through rich context, and give suggestions (in the form of pull request for example) to fix it where it matters: at the source.
Sysdig’s strength at runtime manifests as real-time visibility for detection and response and provides rich context that is required to prioritize what matters. Without it, organizations are left blind and overwhelmed, and ultimately less secure. You can download the complimentary report, and review the full set of recommendations for yourself.
Gartner, Market Guide for Cloud-Native Application Protection Platforms, Neil MacDonald, Charlie Winckless, Dale Koeppen, 14 March 2023.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.


