As organizations continue to look for consolidated platforms to address their security needs, an important shift has happened. Customers have discovered that traditional tools focusing exclusively on static risks (such as misconfigurations, policy/control failures, and network exposure) are not enough to address today’s dynamic cloud threats. What’s needed is a solution with runtime visibility that can help prioritize active risks – like real-time configuration changes and in-use packages with critical vulnerabilities – and tell them what to focus on now.
The 2024 Gartner Market Guide for Cloud-Native Application Protection Platforms (CNAPPs) examines this dynamic as well as other trends in the CNAPP space. It’s clear that CNAPP is no longer a new trend – it’s essential to consolidate security tooling, reduce complexity and costs, and improve agility across the pipeline.
Sysdig has continued to expand real-time capabilities across CNAPP to provide a comprehensive platform for cloud security that prioritizes the risks that matter. With CNAPP adoption continuing to increase, it’s important for customers to consider what is most important when it comes to evaluating a solution.
What is a CNAPP?
According to Gartner, “Cloud-native application protection platforms (CNAPPs) are a unified and tightly integrated set of security and compliance capabilities, designed to protect cloud-native infrastructure and applications.”
CNAPP capabilities help you:
- Prioritize and remediate cloud risks through a consolidated platform that can communicate across multiple areas of cloud security.
- Reduce the chance of a misconfiguration, a mistake, or mismanagement of a resource as cloud-native applications are rapidly developed, released into production, and iterated.
- Converge and reduce the number of tools and vendors involved in the continuous integration/continuous delivery (CI/CD) pipeline.
- Improve developer acceptance with security-scanning capabilities that seamlessly integrate into their development pipelines and tooling.
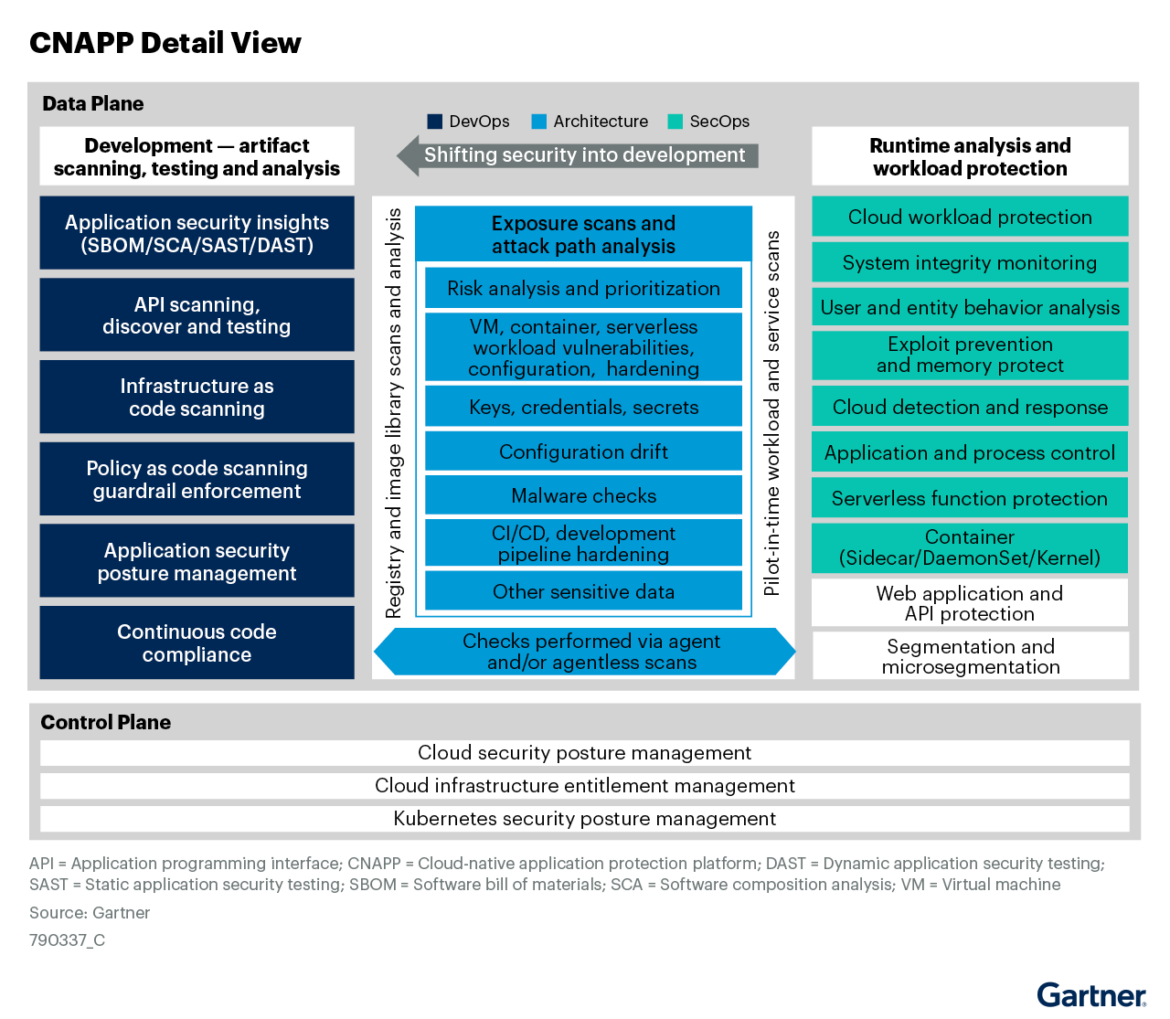
Benefits of a CNAPP
Increased end-to-end visibility: A successful CNAPP must process substantial volumes of data from diverse sources. This encompasses data from Linux system calls, Kubernetes audit logs, cloud logs, identity and access tools such as Okta, and more. Further, cloud environments can span many types of workloads running on public, private, on-prem, or hybrid infrastructure. Extensive coverage is crucial due to the many potential entry points for attacks, as well as the potential for attackers to move laterally. Legacy tools may provide visibility of a portion of your environment, but CNAPPs can provide end-to-end visibility across workloads, cloud services, Linux/Windows, identities, and third-party apps.
Rapid prioritization of risk with runtime insights: The key for security teams to prioritize the most impactful issues across cloud environments is runtime insights. Runtime insights provide actionable information on the most critical problems in an environment based on the knowledge of what is running right now. This provides a lens into what’s actually happening in deployments, allowing security and development teams to focus on current, exploitable risks. From vulnerabilities tied to active packages to real-time detections, a CNAPP solution must be able to correlate findings in real time to uncover hidden attack paths and risks. By connecting the dots across cloud domains, security teams can make informed decisions on which risks are the most critical to address. This helps teams eliminate alert fatigue, provides deep visibility, and enables them to identify relevant suspicious activity.
Ability to detect and respond to cloud threats in real time: EDR and XDR tooling are fundamentally unsuited for the cloud, and the security teams that still rely on them find themselves struggling with incomplete and siloed data that lacks cloud context, dramatically slowing detection, investigation, and response. Cloud detection and response (CDR), as part of a CNAPP, automatically correlates posture and runtime insights for true cloud-native context, accelerating workflows and eliminating skill gaps. Prevention alone is no longer enough. As threat actors evolve and develop unique and unknown attacks, defenders must prioritize detecting and stopping unknown attacks in real time. No organization can effectively defend against zero-day exploits without a purpose-built solution for the cloud.
How CNAPP helps security and DevOps teams
A single purpose-built platform can break silos and streamline downstream activities. Security becomes a valuable business partner by delivering relevant, high-context guidance across key stakeholders. Rapid investigation findings enable prescriptive guidance for response actions across incident response, platform, developer, and DevSec teams. These accelerated findings allow response teams to initiate a response within 5 minutes, adhering to the 5-minute response standard outlined in the 555 Benchmark for Cloud Detection and Response.
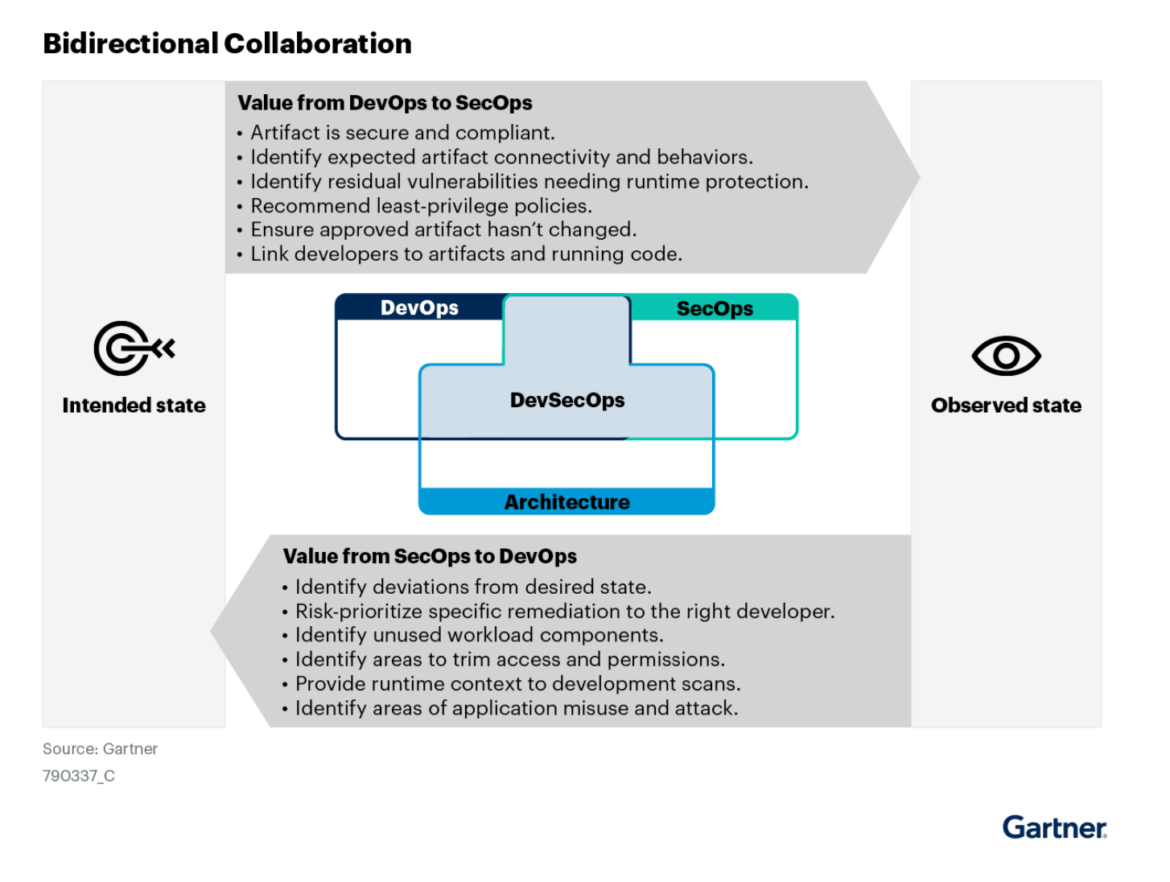
There’s also value in “closing the loop” between security and platform/dev teams. The ability for security teams to leverage findings from investigations (such as what misconfigurations, permissions, and vulnerabilities were abused to perpetuate the attack) and then share those insights to tune and harden preventive controls are critical for enterprise to stay secure – from prevention and hardening to detection and response. This focus on perpetual improvement to preventative controls helps ensure incidents are non-recurring, which reduces organizational cloud risk.
Why CNAPP must have cloud detection and response
The expansive nature and complexity of modern cloud operations warrant new and practical security approaches, with cloud services extending far beyond operating systems and associated processes, the core domains of endpoint detection and response (EDR) tools. Sophisticated threat actors often leverage AI and automated techniques to exploit cloud services in near real-time.
Identity and access management, vulnerability management, and other preventive controls are important for building a robust defense, but defenders must have the ability to stop attacks in motion. To effectively combat cloud threats, security teams need a comprehensive and actionable cloud detection and response solution — one that is purpose-built for the complexities and speed of the cloud. The solution should correlate findings across the entire cloud estate in real time, matching or even outpacing the speed of cloud threats.
At the end of the day, EDR and XDR tools are fundamentally not suited for cloud security. They lack the cloud context to understand the who, what, where, and how of an attack before a breach can occur. Without this context, teams can’t communicate effectively to effectively respond, greatly increasing the potential for missed threats and a material breach. Without a shared platform that prioritizes CDR, security teams will always be left playing catch-up.
Recommendations for evaluating a CNAPP
In their 2024 Market Guide for Cloud-Native Application Protection Platforms, Gartner shares several recommendations for security and risk management leaders. Based on our understanding from the report, we’ve provided several questions to help you navigate the buying process.
Do they address a broad set of security use cases from source to production?
This includes capabilities such as:
- Cloud detection and response – Enabling real time multi-cloud correlation, context, and visibility into identity, workload, and cloud activity, including the control plane.
- IaC security – Scanning IaC manifests to identify misconfigurations and security risks before deployment while preventing drift.
- Vulnerability management and supply chain security – Identifying, prioritizing, and fixing vulnerabilities across your software supply chain, such as SCM, CI/CD, registry, and runtime environments.
- AI workload security – Uncovering active AI risk by flagging any suspicious activity or changes to workloads that contain AI packages that are in-use.
- Optimize identities and access in the cloud – Because suspicious user activity is often the first indicator of a breach, it’s critical to be able to detect compromise in seconds, contain compromised identities, and prevent future identity abuse.
- Kubernetes security posture management (KSPM) – Ensuring that governance, compliance, and security controls are included for Kubernetes.
- Configuration and access management – Hardening posture by managing misconfigurations and excessive permissions across cloud environments, such as cloud resources, users, and even ephemeral services like Lambda.
- Threat detection and response across cloud workloads, users, and services – Multi-layered detection approach that combines rules and ML-based policies, enhanced with threat intelligence, along with a detailed audit trail for forensics and incident response.
- Universal compatibility with eBPF – Simplifying deployment and giving organizations greater flexibility regarding where and how they develop cloud-native applications with extensive coverage of Linux hosts, Windows hosts, and Kubernetes nodes.
- Compliance– Meeting compliance standards for dynamic cloud/container environments against PCI, NIST, and HIPAA.
Can they accurately prioritize what matters?
Prioritizing the most critical vulnerabilities, configuration or access mistakes based on in-use risk exposure is key. For example:
- Understanding which packages are in-use at runtime, helps you prioritize the most critical vulnerabilities to fix. Our research shows that 87% of container images have high or critical vulnerabilities, but only 15% of vulnerabilities are actually tied to loaded packages at runtime.
- Real-time cloud activity helps immediately spot anomalous behavior/posture drift that are most risky
- Runtime access patterns help to highlight the excessive permissions to fix first.
Also the ability to provide remediation guidance that ultimately helps teams to make informed decisions directly where it matters most – at the source.
Can they maximize coverage but also give deep visibility?
Evaluate whether CNAPP vendors provide deep visibility and insights across your entire multi cloud footprint, including IaaS and PaaS, extending across VM, container, and serverless workloads. This often includes both agentless for visibility and control, as well as deep runtime visibility based on instrumentation approaches like eBPF.
Are they truly getting a consolidated view of risk?
Some vendors acquire multiple companies to check the box, and this results in a poor disjointed experience. Look for a CNAPP vendor that tightly integrates the source to production use cases, replacing multiple point products with a comprehensive picture of risk across configurations, assets, user permissions, and workloads.
Do they allow customizations?
Every organization is different. The ability to customize policies, filter results and accept risk based on the organization’s unique environment is key to successfully adopting a solution.
Are they tightly integrated with the DevOps and security ecosystem?
The CNAPP must integrate with CI/CD tools and scan for misconfigurations and vulnerabilities pre-deployment as well as with SIEM/notification tools trigger alerts / forward events so teams can act immediately. Guidance on how to fix is key; the tool needs the ability to map the violation back to the IaC file, provide situational awareness when investigating an alert through rich context, and give suggestions (in the form of pull request for example) to fix it where it matters: at the source.
CNAPP requires runtime insights
Prioritizing CNAPP with runtime insights empowers security teams to span the spectrum of prevention and hardening to detection and response, which ultimately allows all teams in the cloud to handle issues with greater efficiency and confidence. As organizations increasingly navigate cloud security complexities, runtime insights provide a decisive advantage by offering comprehensive visibility, enabling rapid risk prioritization, and mitigating alert overload.
By addressing the challenges of end-to-end visibility and alert fatigue, CNAPPs equipped with runtime insights enable security and development teams to swiftly identify, prioritize, and address critical vulnerabilities, ensuring the organization’s cloud security posture aligns seamlessly with the pace of innovation.
Gartner, Market Guide for Cloud-Native Application Protection Platforms, Dale Koeppen, Charlie Winckless, Neil MacDonald, Esraa ElTahawy, 22 July 2023.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.