The cloud moves fast.
Your security should too.
from prevention to real-time defense —
rooted in open source and trusted
by teams who move fast.
Unlock the value of a CNAPP
Accelerate how you prioritize risks, detect threats, investigate incidents, and ship secure code. With deep visibility and rich context, your teams work smarter — and your business moves faster, without sacrificing security.
Learn More
End-to-end cloud security
powered by deep runtime visibility
Purpose-built for the scale, speed, and complexity of the cloud, the Sysdig platform helps you prioritize active risks and stop threats in real time.
Cloud security posture management
Identify, prioritize, and reduce risks across your cloud environments.
Vulnerability management
Focus on real risk and reduce vulnerability noise up to 95% with runtime intelligence.
Container & Kubernetes security
Detect, prioritize, and resolve threats and vulnerabilities with speed and context.
Cloud detection & response
Detect and respond to threats with deep visibility, automated action, and built-in intelligence.
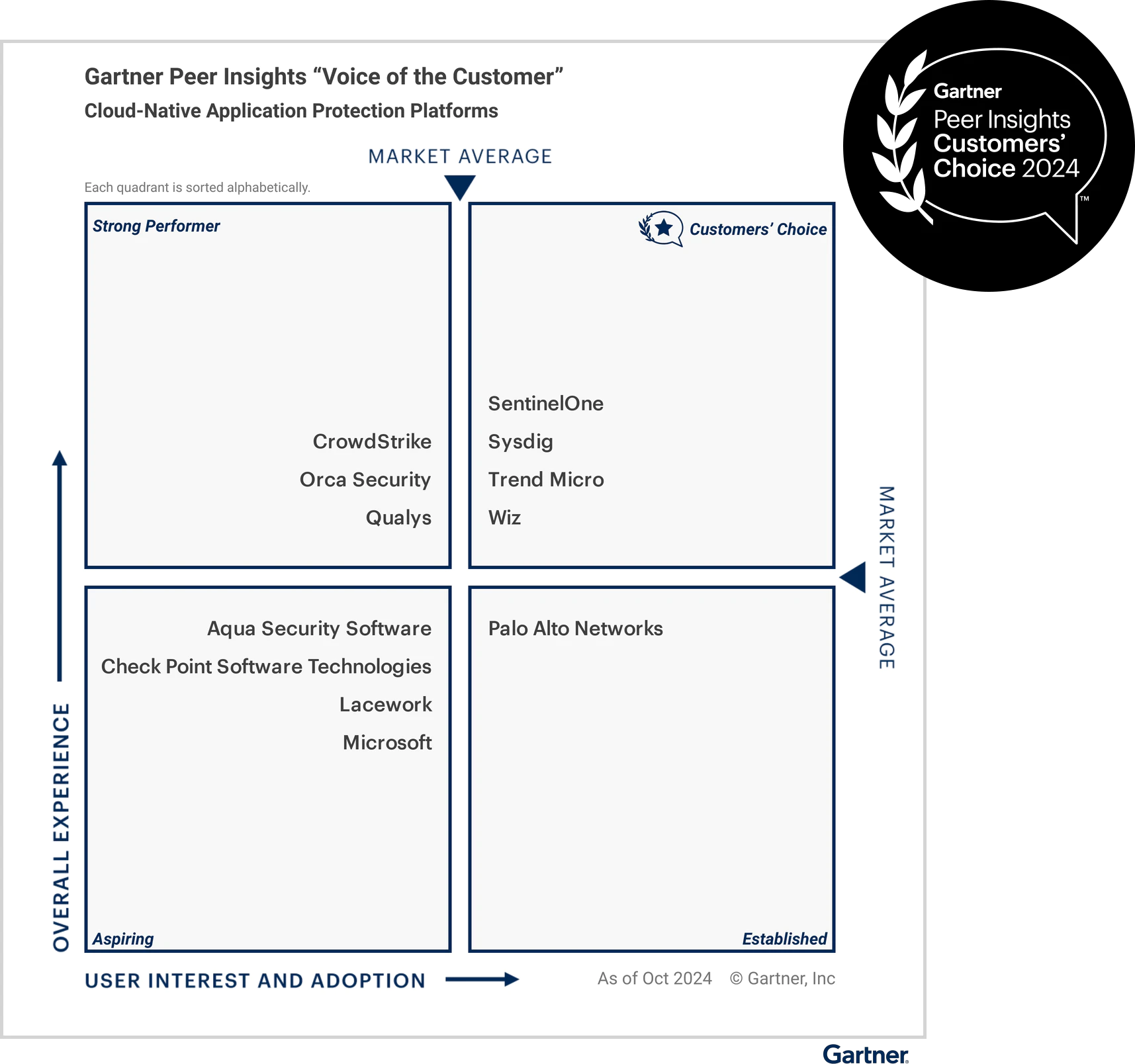
Why customers choose sysdig
A single view of cloud risk
Powered by our Cloud Attack Graph, Sysdig correlates assets, activity, and risks across domains, giving you real-time visibility into attacks.
Prioritization based on runtime insights
Generate a prioritized list of risks using multi-domain correlation to identify risky combinations across environments. Risk prioritization is powered by runtime insights such as in-use vulnerabilities and in-use permissions.
Uncover attack paths
Visualize exploitable links across resources to uncover attack paths to sensitive data. With runtime insights, real-time detections reveal active lateral movement, helping you stop attacks in their tracks.
Built for a multicloud world
Our platform supports multi-cloud environments and addresses risk across all of your cloud accounts and deployments.
See Sysdig in Action
Test drive our real-time cloud defense platform with a security expert