
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

This week, Linux maintainers and vendors disclosed a heap overflow vulnerability in the Linux Kernel. The vulnerability has been issued a Common Vulnerability and Exposures ID of CVE-2022-0185 and is rated as a High (7.8) severity.
The flaw occurs in the Filesystem Context system when handling legacy parameters. An attacker can leverage this flaw to cause a DDoS, escape container environments, and elevate privileges.
The problematic code was introduced into the Linux Kernel in version 5.1-rc1 nearly three years ago in March of 2019. A patch released on January 18th fixes this issue. All Linux users are advised to download and install the latest version of the Kernel.
Researchers Jamie Hill-Daniel and William Liu are credited with the discovery and responsible disclosure of the vulnerability.
The CVE-2022-0185 issue
The specific flaw in CVE-2022-0185 is caused by an integer underflow condition found in the FIlesystem Context system (fs/fs_context.c) in the legacy_parse_param function. The Filesystem Context system is used when creating a superblock for mounting and remounting filesystems. Superblocks record the characteristics of a filesystem, such as block and file sizes, and any storage blocks.
By sending more than 4095 bytes to the vulnerable function, an input length check can be bypassed and lead to an out-of-bounds write. This allows attackers to write to other parts of memory, causing a system to crash or run arbitrary code to increase their privilege on a vulnerable system.
Attackers can also leverage this in a container escape move. If successful, an attacker can gain full control of the host OS and all containers running on the system. Once in control, they can attack resources on the internal network segment and deploy malicious containers inside the production environment.
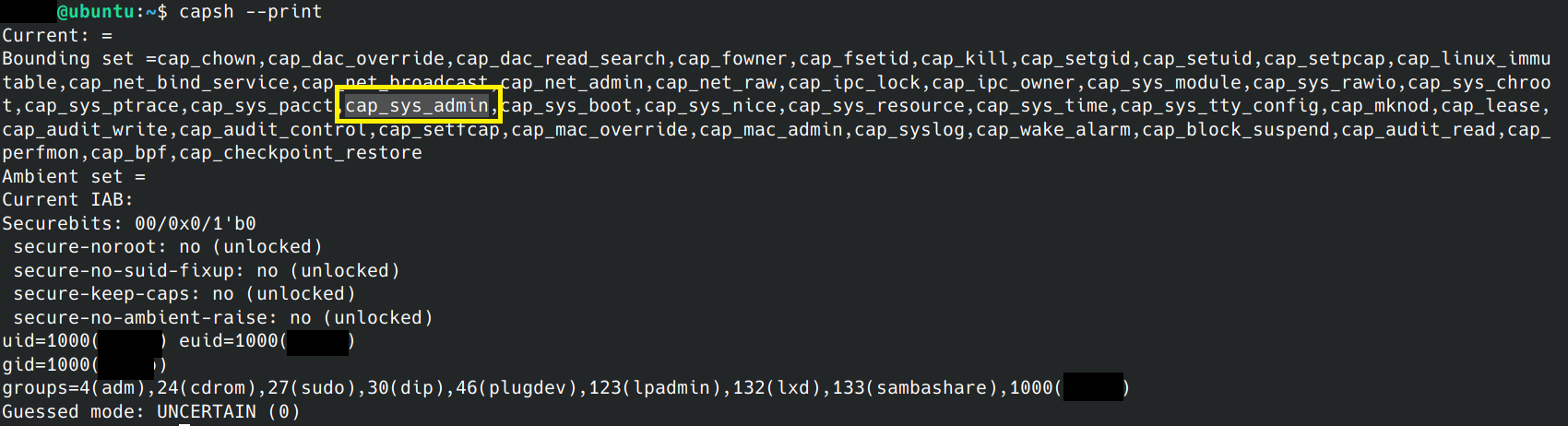
The command "capsh –print" can be used in the context of the current user to list enabled capabilities. The attacker doesn't need the CAP_SYS_ADMIN capability because it can be acquired using unshare, unless the use of seccomp blocks it.
The impact of CVE-2022-0185
The severity of the flaw is rated High with a score at 7.8. It has a high impact and is easy to exercise by local attackers.
To learn more about how a vulnerability score is calculated, Are Vulnerability Scores Tricking You? Understanding the severity of CVSS and using them effectively
Namespaces are a fundamental aspect of containers on Linux. This feature of the Linux kernel partitions kernel resources and allows for one set of processes to see one set of resources, while another set of processes sees a different set of resources, potentially in multiple spaces.
If an attacker can exploit remotely accessible services and establish a foothold on a compromised container, they can leverage this flaw to escape a container environment and gain root privileges on the host system.
While no specific exploits have been released publicly at this time, researchers are able to demonstrate the vulnerability reliably. It is only a matter of time before publicly available exploits are released.
Mitigating CVE-2022-0185
CVE-2022-0185 can be mitigated by installing the Linux Kernel patch.
If patching is not possible, Linux users can also disable unprivileged user namespaces without needing to reboot. WARNING: These commands may affect the host's ability to run containers.
On Ubuntu and most distributions, you can use the following sysctl command to disable it:
sysctl -w kernel.unprivileged_userns_clone = 0On Red Hat Linux, you can mitigate the flaw by changing the user.max_user_namespaces setting:
echo "user.max_user_namespaces = 0" >> /etc/sysctl.d/userns.conf
sysctl -p /etc/sysctl.d/userns.confCheck your Linux distribution's recommended steps if unsure.
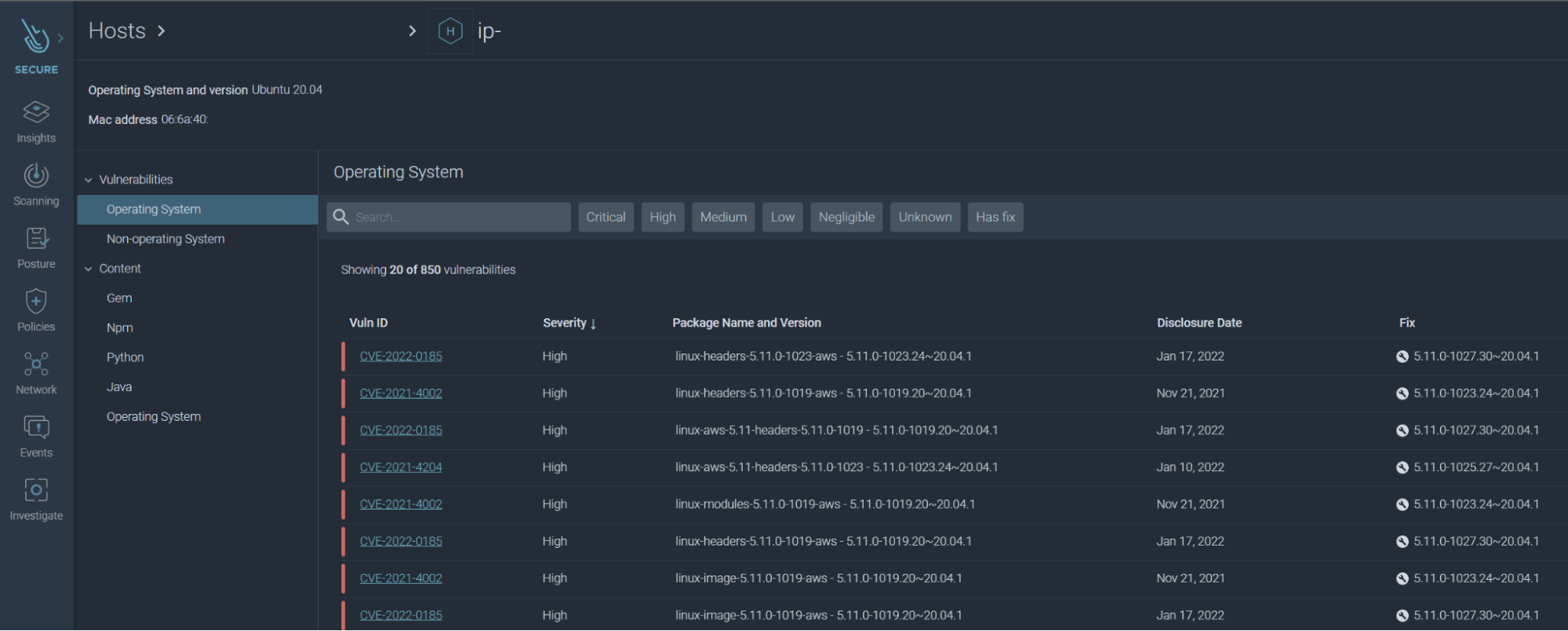
Sysdig Secure's Scanner feature can detect vulnerable versions of kernel installed on hosts and consequently, the running containers sharing the kernel. This can assist administrators with detecting unpatched systems that need updating.
As seen below, each host is monitored for vulnerabilities and displays if a fix is available.
Conclusion
Luckily, the vulnerability, CVE-2022-0185, was discovered and patched before malicious attackers released an exploit publically.
Administrators and users need to be vigilant in keeping their systems up to date with the latest security patches. Depending on the environment, patching can be a time consuming process. Fortunately, Sysdig Secure can help track down unpatched systems before attackers can.
At Sysdig Secure, we extend Falco with out-of-the-box rules along with other open source projects, making them even easier to work with and manage Kubernetes security. Register for our Free 30-day trial and see for yourself!


