Sysdig has validated its security, monitoring, and compliance capabilities with multiple Azure-related services. The latest is Microsoft Sentinel, a SIEM(Security Information and Event Management) solution on Azure that works really well with Sysdig’s cloud workload protection capabilities. Sysdig and Microsoft have a common goal of helping customers ship cloud apps faster by helping them see more, secure more, and save time in troubleshooting deployed microservices.
Prerequisites for a successful SIEM implementation
Prerequisite 1: Source asset identification
A good SIEM strategy includes the identification of critical assets that send key data, plus the context, logs, and events around the data into the SIEM.
Prerequisite 2: Data quality
Garbage in, garbage out. To get the right type of data fed into your SIEM, you need to get it from the correct sources.
Prerequisite 3: Logging levels
You also need to ensure that the rules controlling the event stream flowing into the SIEM do not cause too many false positives, but maintain a deep level of visibility.
Thus, the policies, rules, and filters with regard to event streams become critical to your SIEM’s success. You must consider whether you have the right systems in place to send the right event streams to your SIEM.
Why is Sysdig Secure & Microsoft Sentinel a winning partnership?
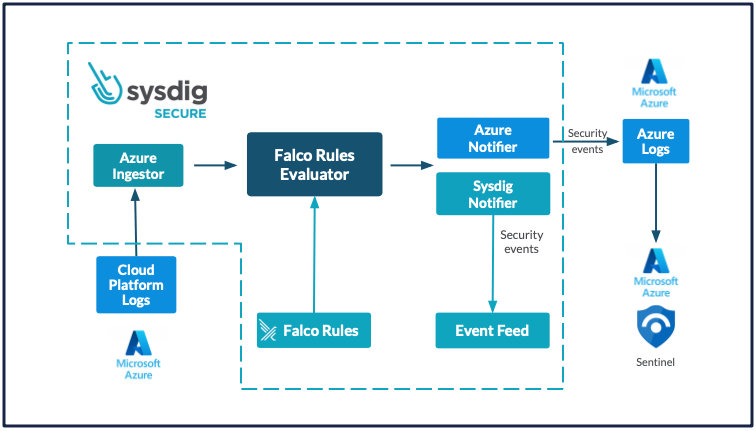
Sysdig Secure with Microsoft Sentinel – Block Diagram
Reason 1: Sysdig Secure has powerful threat detection capabilities
At Sysdig’s core is the open-source Falco rules engine. This makes it easy to look for suspicious activity and then send enriched events from Sysdig onward to your SIEM setup, such as Microsoft Sentinel.
Reason 2: Sysdig lends deep and contextual visibility to Microsoft Sentinel
For example, Falco can identify any container-related activity and then alert on it. However, this may include legitimate activities happening within the container. Sysdig Secure is able to look into system call level detail and offers rules to detect activity, such as the spawning of a terminal shell within a container. In addition to Falco, Sysdig Secure leverages core Kubernetes features and has access to Kubernetes API calls as another important data source. By monitoring Kubernetes API calls together with system calls, it can detect suspicious activity and then send the details, including Kubernetes context, over to Microsoft Sentinel.
Other sophisticated rules within Sysdig Secure cover data manipulation, SSH tampering, and even detect drift with regard to your deployed images in production. Sysdig truly takes Falco capabilities to the next level and is becoming the choice cloud detection and response tool in the market.
Reason 3: Microsoft Sentinel allows for extensive forensic activities based on the data provided by Sysdig Secure
These capabilities can be summarized as follows:
- Data visualization on dashboards
- Correlation with other data points and further investigations
- Alerting based on advanced forensics
This Microsoft Sentinel partnership is a key part of Sysdig’s broader initiative to enhance cloud security and container security for organizations.
What are the various events/datasets that can be analyzed by Microsoft Sentinel (sent from Sysdig Secure)?
Sysdig Secure provides an event forwarding feature that sends different types of security data to third-party SIEM platforms and logging tools. This enables you to view and correlate Sysdig security findings directly in the tools you use for analysis. The list of events can be enumerated as follows:
- Activity Audit: A list of events containing commands, file activity, network activity, and kubectl activity.
- Audit Tap: Using these events, DevOps teams can fingerprint every process connection, giving full process-level visibility into the entire environment, including every network connection attempt. Teams can monitor every connection made by a process, even if a connection is unsuccessful.
- Sysdig Platform Audit: If one needs to audit and report on the use of Sysdig secure itself.
- Benchmark Events: When your infrastructure fails certain benchmarks, such as CIS (Center for Internet Security).
- Secure Events Compliance – How you are doing with regards to tracking with regards to compliance mandates such as HIPAA (Health Insurance Portability and Accountability Act), PCI-DSS (Payment Card Industry Data Security Standard), and NIST (National Institute of Standards and Technology).
- Host and Container Vulnerabilities: Image and host vulnerability information discovered by scans during build and runtime
- Runtime Policy Events: Events detected that violate configured Falco runtime security rules.
How to set up Sysdig Secure to forward events to Microsoft Sentinel?
We validated a proof-of-concept for connecting Sysdig Secure with Microsoft Sentinel. Follow the below-mentioned steps (and prerequisites as required) to quickly integrate these two security systems.
(Prerequisite steps)
A. Set up Sysdig Secure account
It’s easy to get started with Sysdig Secure. Just go to Start Free Trial | Sysdig to begin with a free 30-day trial.
B. Configure the Microsoft Sentinel instance
On your Microsoft Azure portal, make sure you have enabled an instance of Microsoft Sentinel. This instance will allow you to perform SIEM-related tasks.
C. Set up a log analytics setup within your Microsoft Sentinel
This basically sets up Azure Monitor Logs for data collection with regard to Microsoft Sentinel.
D. Create a dedicated workspace ID and token from your Azure Portal
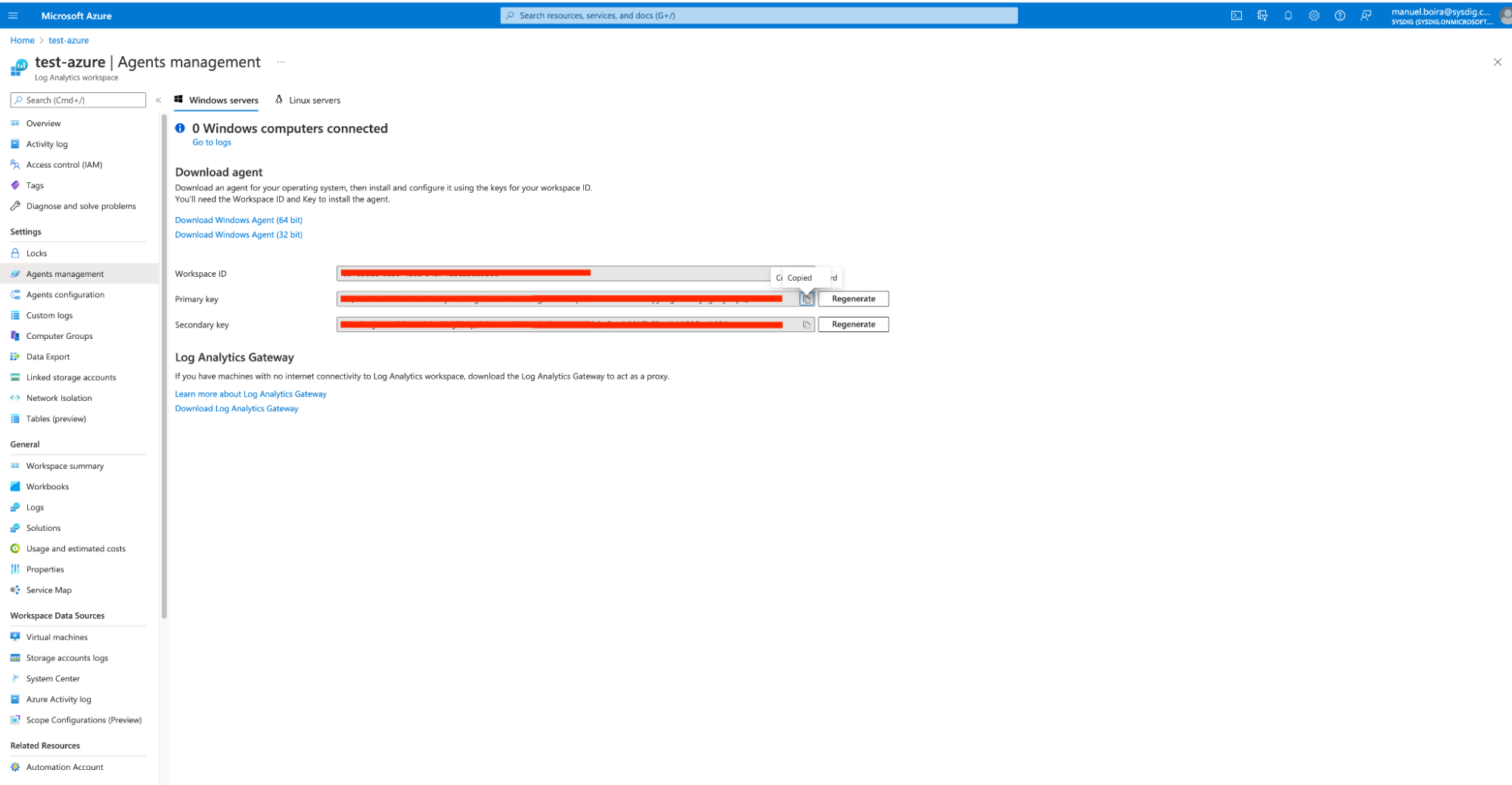
Azure Workspace & Agents management
This workspace ID and token are necessary for setting up a secure integration to exchange data between Microsoft Sentinel and any other SaaS software, such as Sysdig Secure.
(Main steps)
Step 1 – Set up the Microsoft Sentinel integration within Sysdig
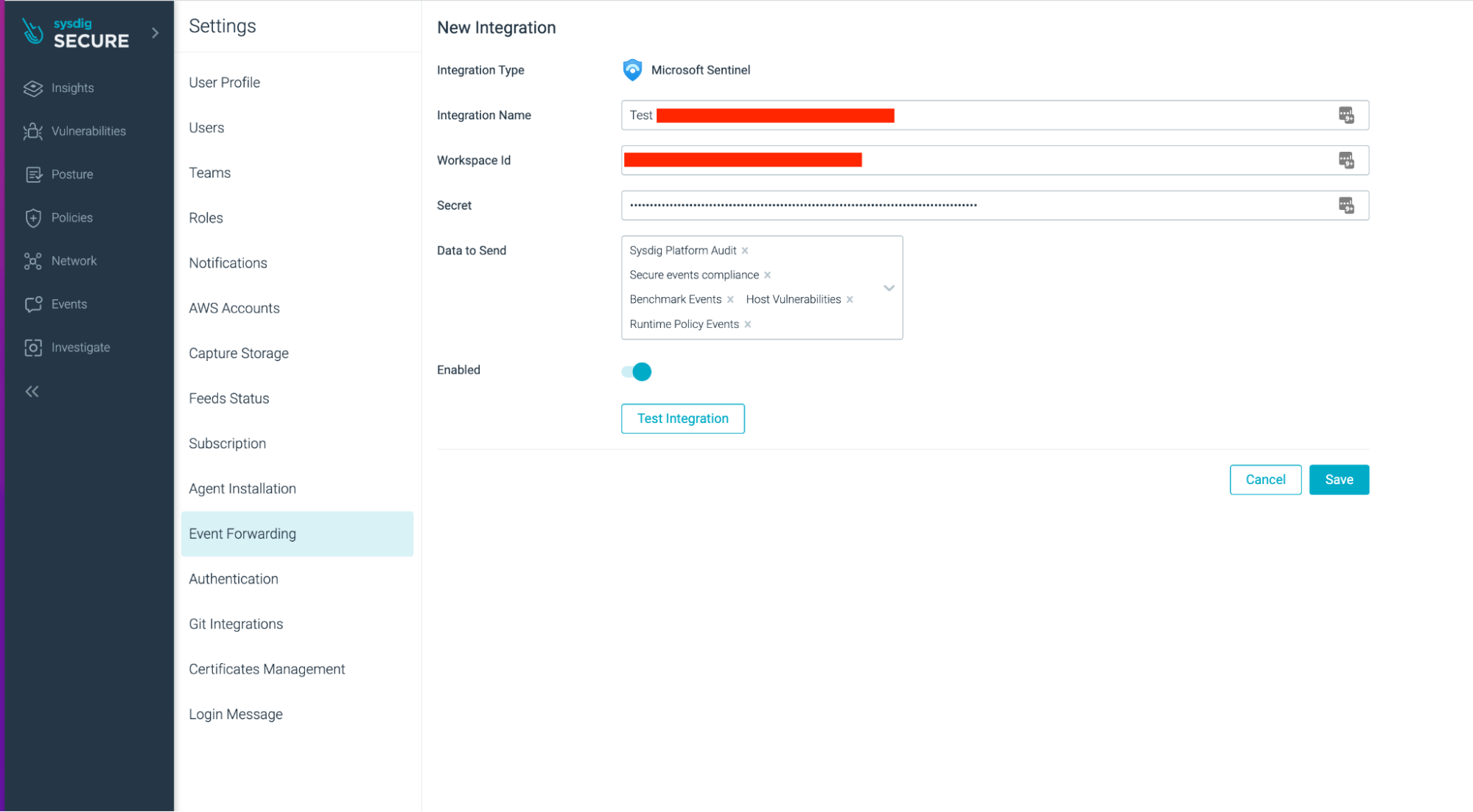
Sysdig Secure Integrations Setup
Within Sysdig Secure, go to “Settings” > “Event Forwarding” and select “Add Integration.” Choose Microsoft Sentinel. Then, enter the integration name, the workspace ID, and the secret key. Also, select what type of event data you wish to send to Microsoft Sentinel.
Step 2 – Set up the Microsoft Sentinel query
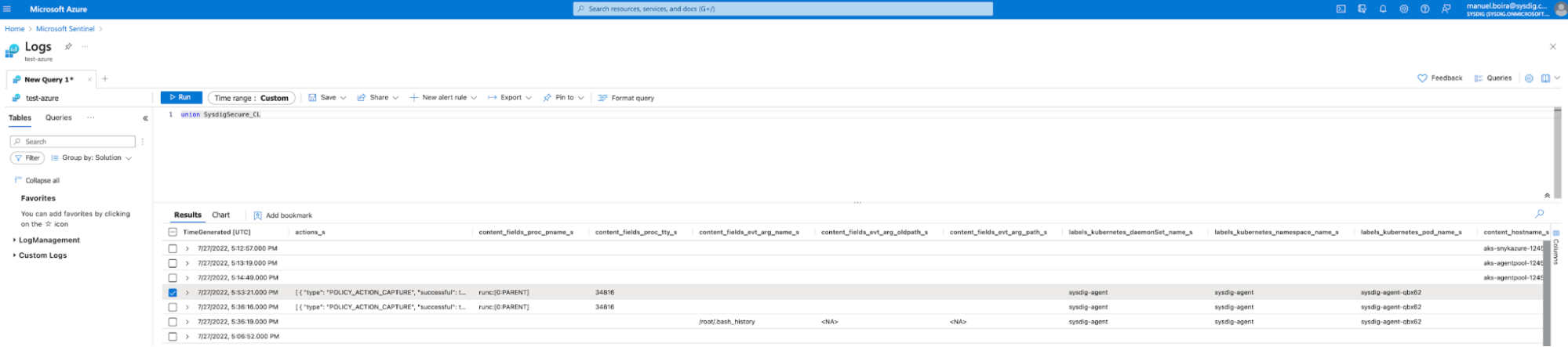
Microsoft Sentinel – Query Setup
In the Microsoft Sentinel UI, go to “Logs>>New Query.” Then, select the list of all Sysdig Secure events and run the query. This gives you a list of all Sysdig events, including events from Falco runtime threat detections.
Step 3 – Dive into event details from Sysdig on Microsoft Sentinel
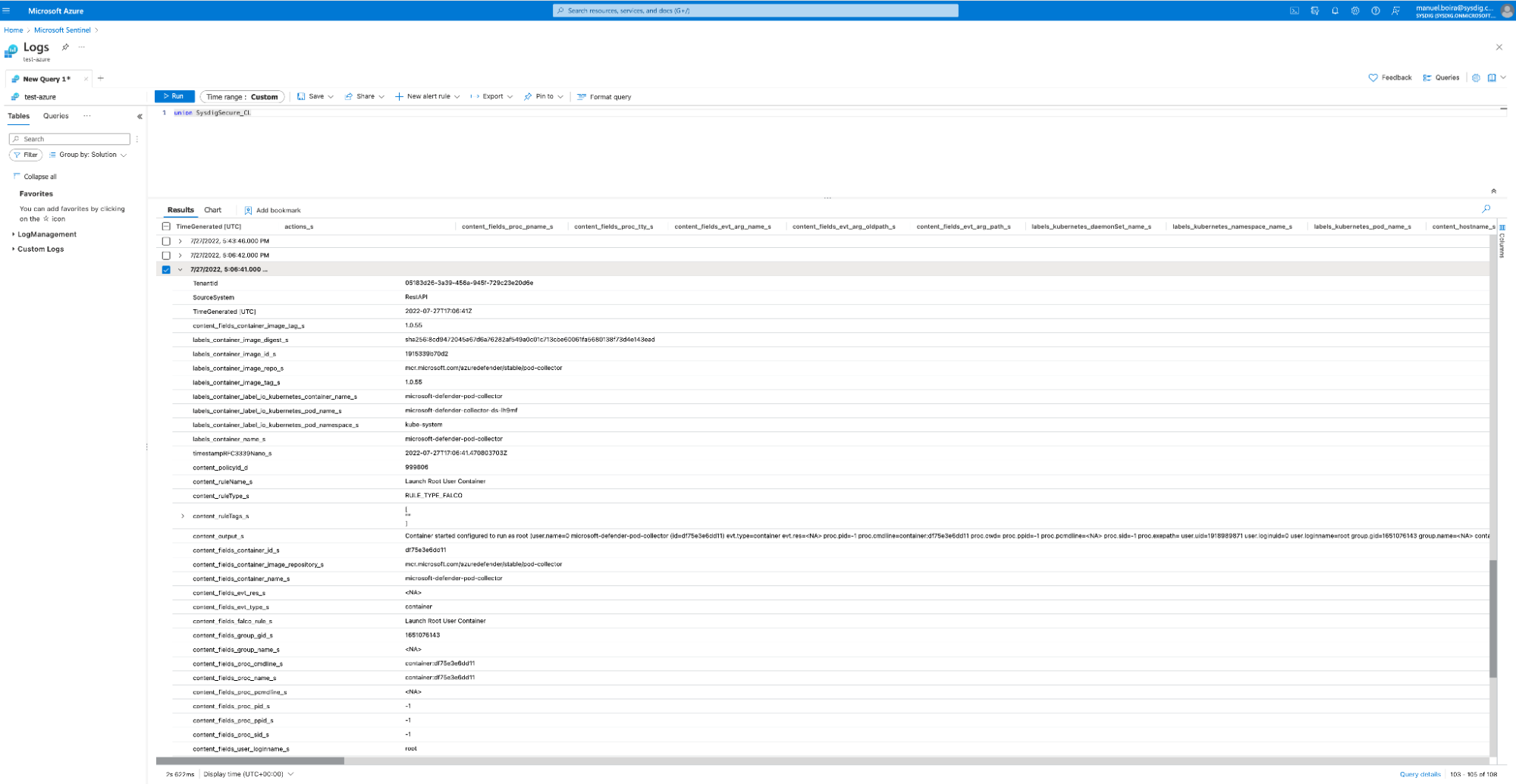
Microsoft Sentinel – Event Details
In the Microsoft Sentinel UI, you can dive deeper into any event from the list of all Sysdig events, and then use it for further forensic investigations.
Step 4 – Set up Microsoft Sentinel visualizations for Sysdig events
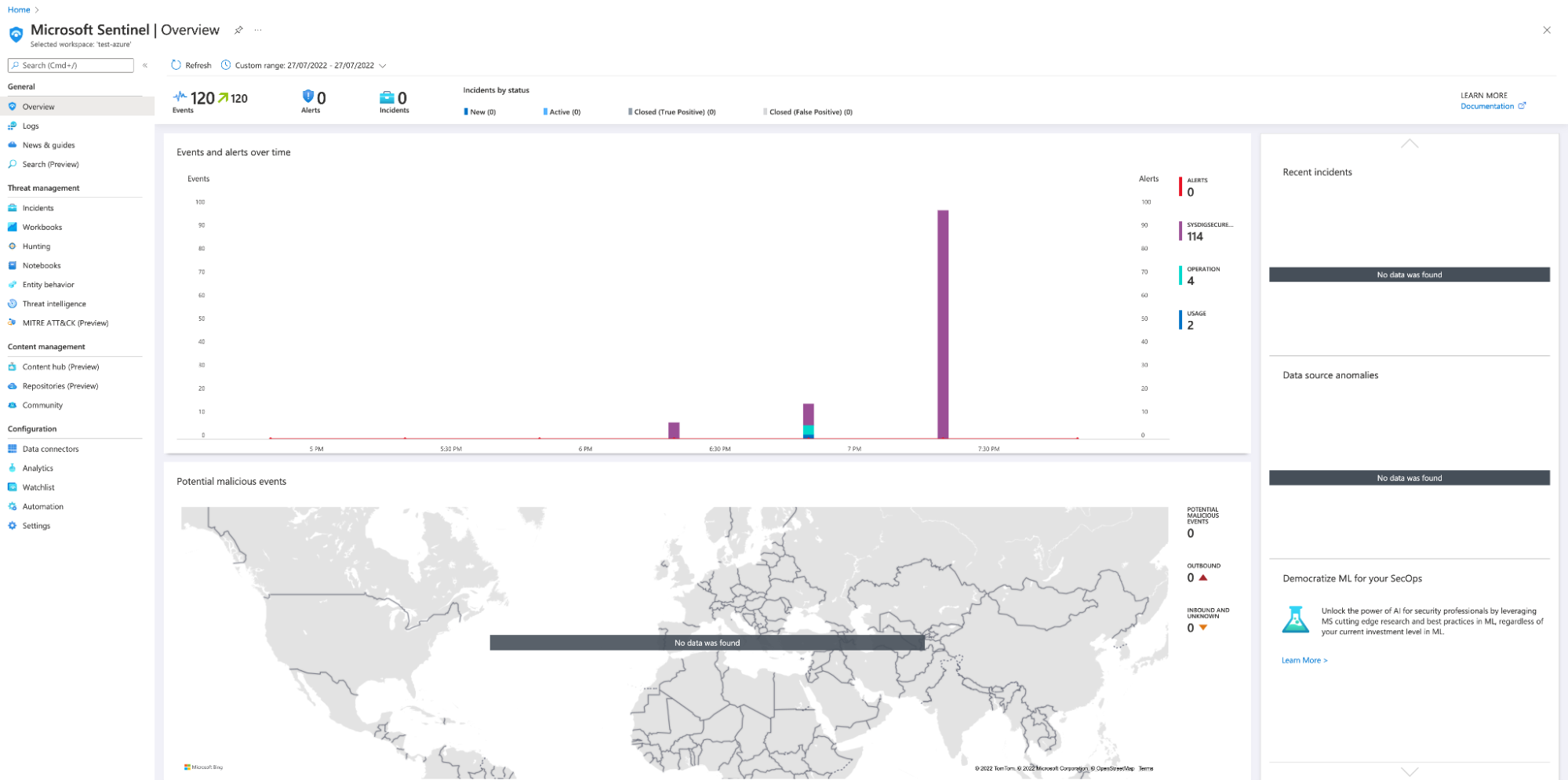
Microsoft Sentinel – Dashboard
Besides forensics, you can also visualize all the Sysdig events within Microsoft Sentinel. These visualizations can then be added to relevant threat investigation dashboards.
Conclusion
A Microsoft Sentinel SIEM (or any SIEM for that matter) is only as useful as your organization’s efforts to understand and leverage it regularly. Its effectiveness is primarily based on your security team’s ability to see suspicious events tracked by monitoring and logging systems – and also on how these events present and elevate different business risks. Give Sysdig Secure a try with your Microsoft Sentinel setup to fully extract value from your SIEM setup and SecOps teams!


