In the early days of 2022, two extremely popular JavaScript open source packages, colors.js, and faker.js, were modified to the point of being unusable. The reason behind this can be traced to various motivations, but it is worth mentioning that several applications that employed those dependencies were involved.
The two impacted packages can be used for different purposes in JavaScript applications. colors.js enables color and style customization in the node.js console. faker.js is widely used for testing purposes, generating massive amounts of fake data. Both of them were downloaded hundreds of millions of times throughout their lifetime, and this is why the impact is huge.
In this article, you will understand how these projects have been corrupted, how the malicious changes can affect JS apps, and how to detect their presence with Sysdig Secure to be prepared in case this scenario happens again.
Compromises of the software supply chain
faker.js
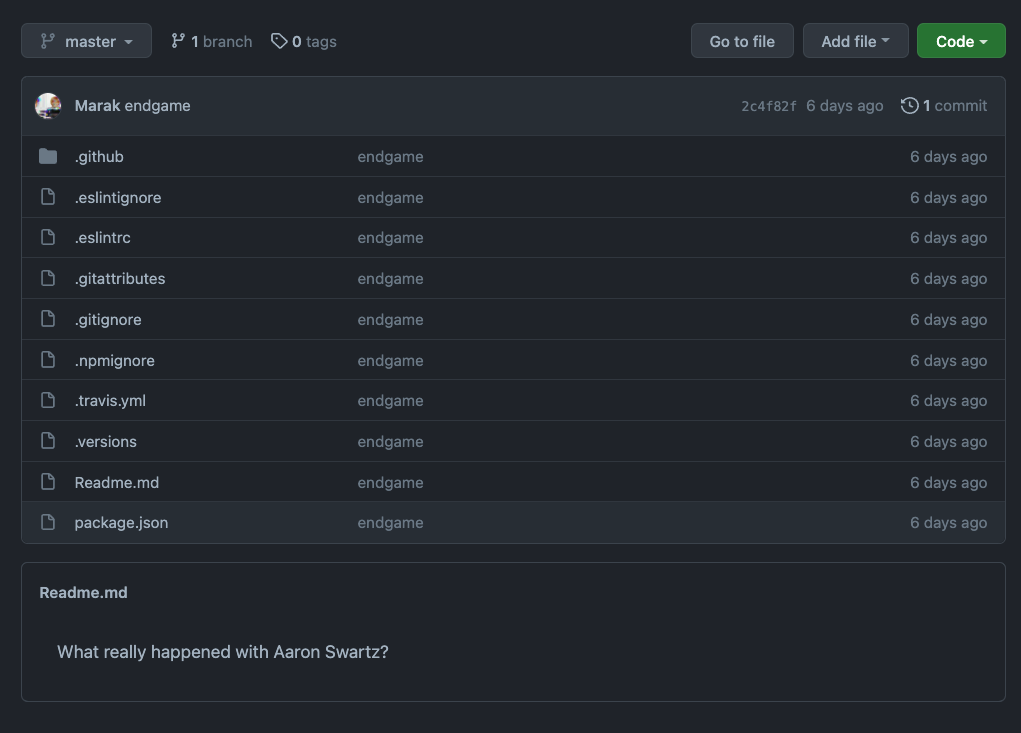
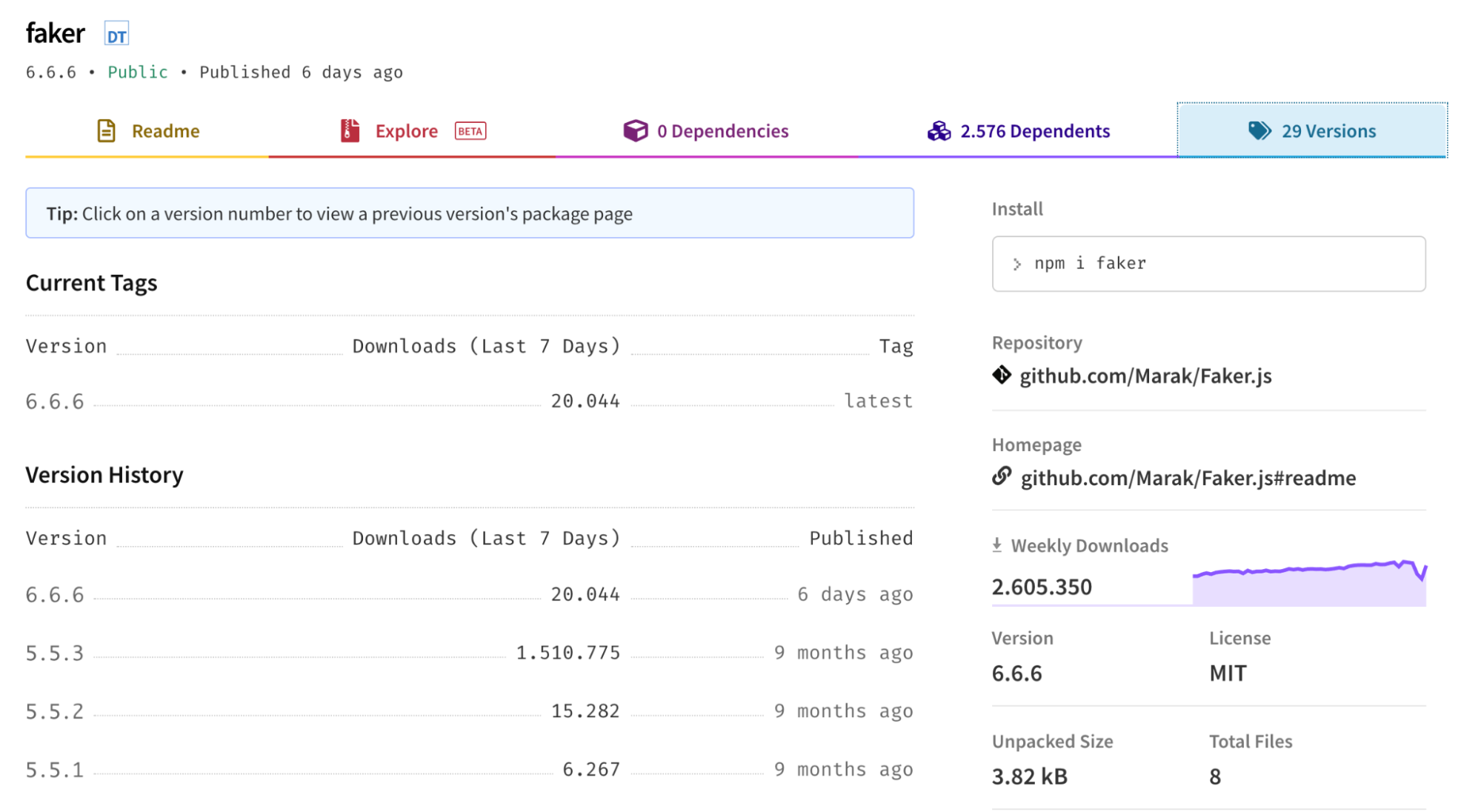
The latest version of faker.js 6.6.6 (suspicious numbers) has been tampered with. The affected version no longer functions and will cause projects using it to work improperly. The readme file was also altered to mention a popular Internet hacktivist.
The reported image shows that the functional code inside this GitHub repository was completely deleted by its owner, along with their commit history. However, the npmjs official website has kept track of the various versions of this package, which allows users to fetch the older stable versions.
colors.js
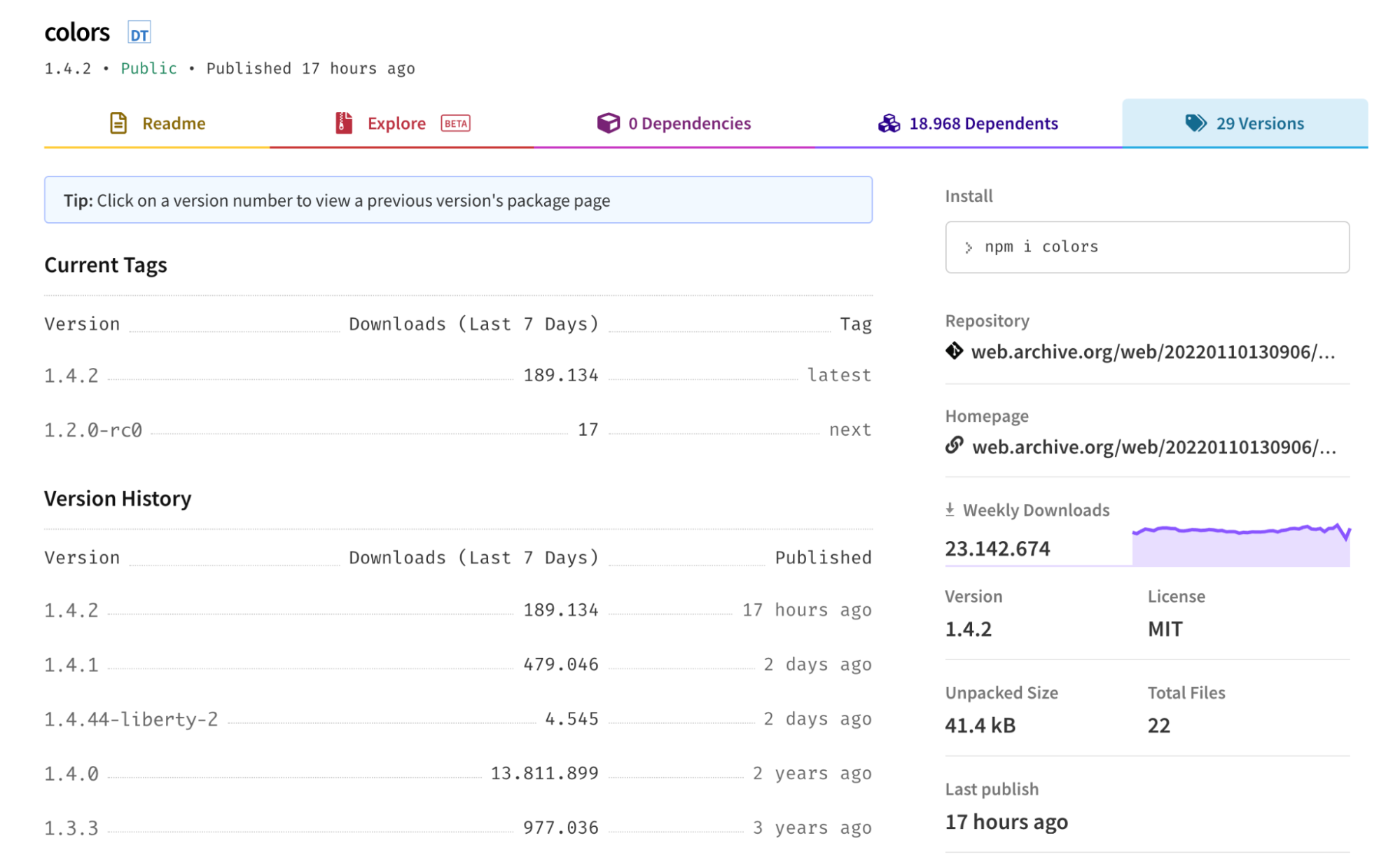
A few days later, the colors.js package was corrupted as well, but in this case, the bug drove the user’s console into an infinite loop. The bug is mainly attributable to this piece of code:
…
require('./extendStringPrototype')();
/* remove this line after testing */
let am = require('../lib/custom/american');
am();
for (let i = 666; i < Infinity; i++) {
if (i % 333) {
// console.log('testing'.zalgo.rainbow)
}
console.log('testing testing testing testing testing testing testing'.zalgo)
}
The affected package versions were 1.4.1, 1.4.2, and 1.4.44-liberty-2.
Fortunately, a few hours after their releases, the npmjs official website removed the traces of the affected versions. Then, they restored version 1.4.0 as the latest and stable one.
The impact
The faker.js package was simply rendered unusable in its latest version.
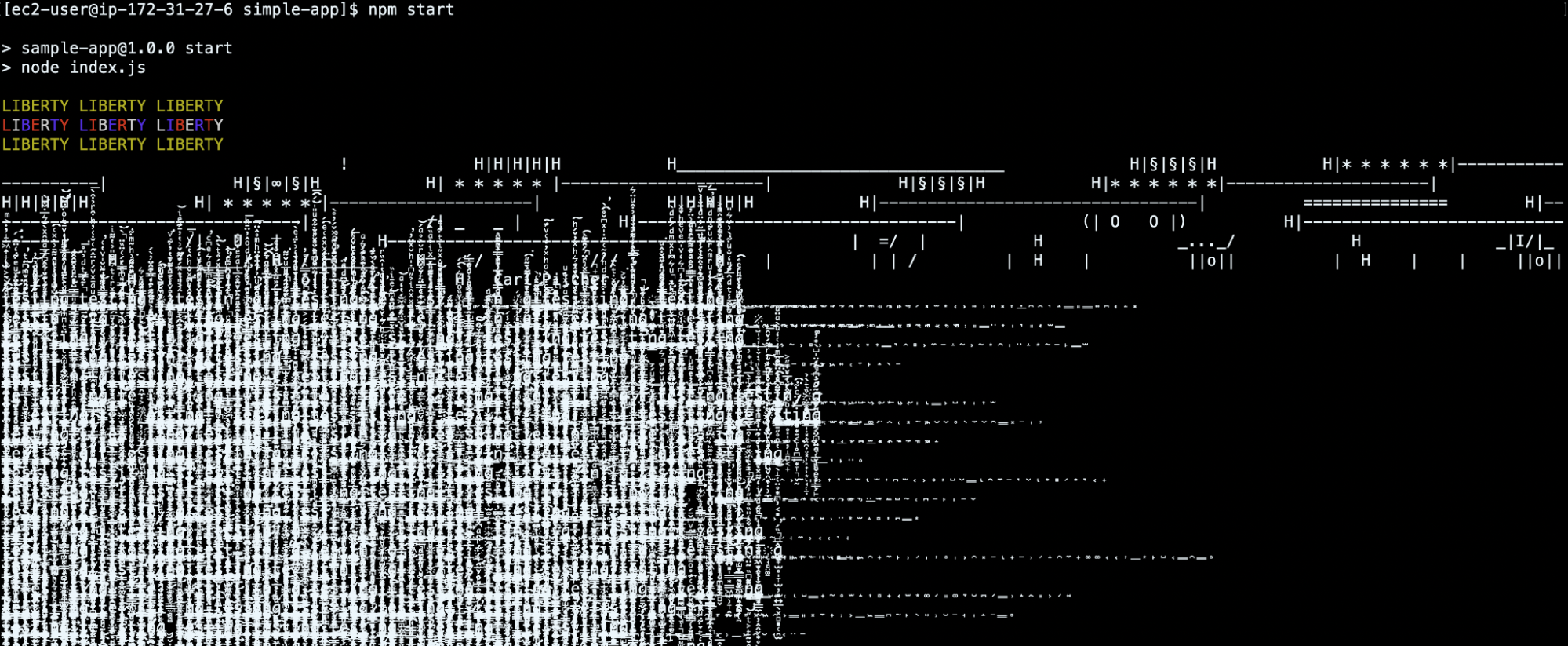
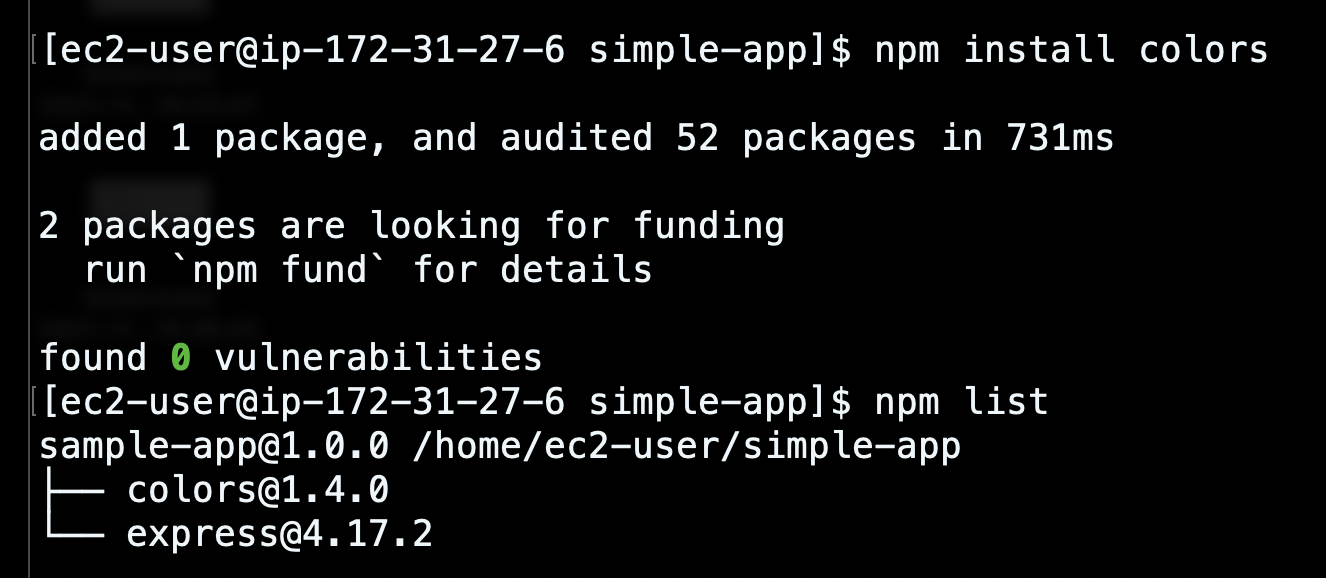
Worse yet, the latest color.js release could drive the user’s console into an infinite loop, printing Zalgo text symbols: a sequence of combining Unicode characters that make the text look creepy.
The image below shows how the console may look after the npm start command.
Although the damage caused is almost negligible, it seems to have involved several JS applications. The affected package versions were already downloaded hundreds of thousands of times in the last few days.
This means that many users may have already experienced some issues while being unable to take advantage of those widely known features.
Mitigation
If you have already installed these two packages with these versions, you have to remove them from your environment and then install the stable releases.
If you want to use the faker.js package, keep in mind that the latest release doesn’t work anymore. Thus, you should install one of the older versions. The most recent stable one is version 5.5.3.
The stable colors.js package release can be downloaded without any bugs since the affected versions were already removed from the npmjs repository.
Detecting attacks to the software supply chain
In order to inspect if a container image is impacted by the affected packages, you can use Image Scanning.
Image scanning refers to the process of analyzing the contents and the build process of a container image in order to detect security issues, vulnerabilities, or bad practices.
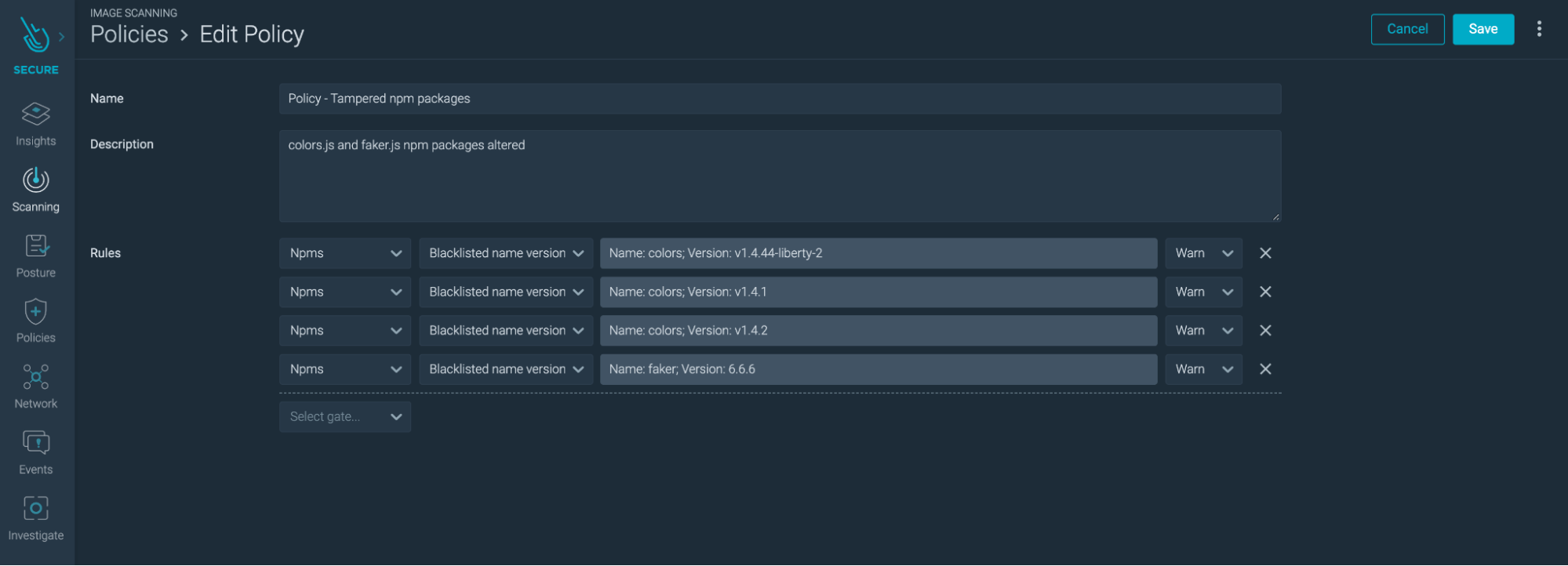
With this functionality, you can be automatically warned of all packages associated with well-known well-known Common Vulnerabilities and Exposures (CVE). Additionally, you can set your own Scanning Policies to find any other potential risks within your container images. The following image shows a custom Scanning Policy able to detect the compromised npm packages. For each package version, you can define the action to take (Warning or Stop).
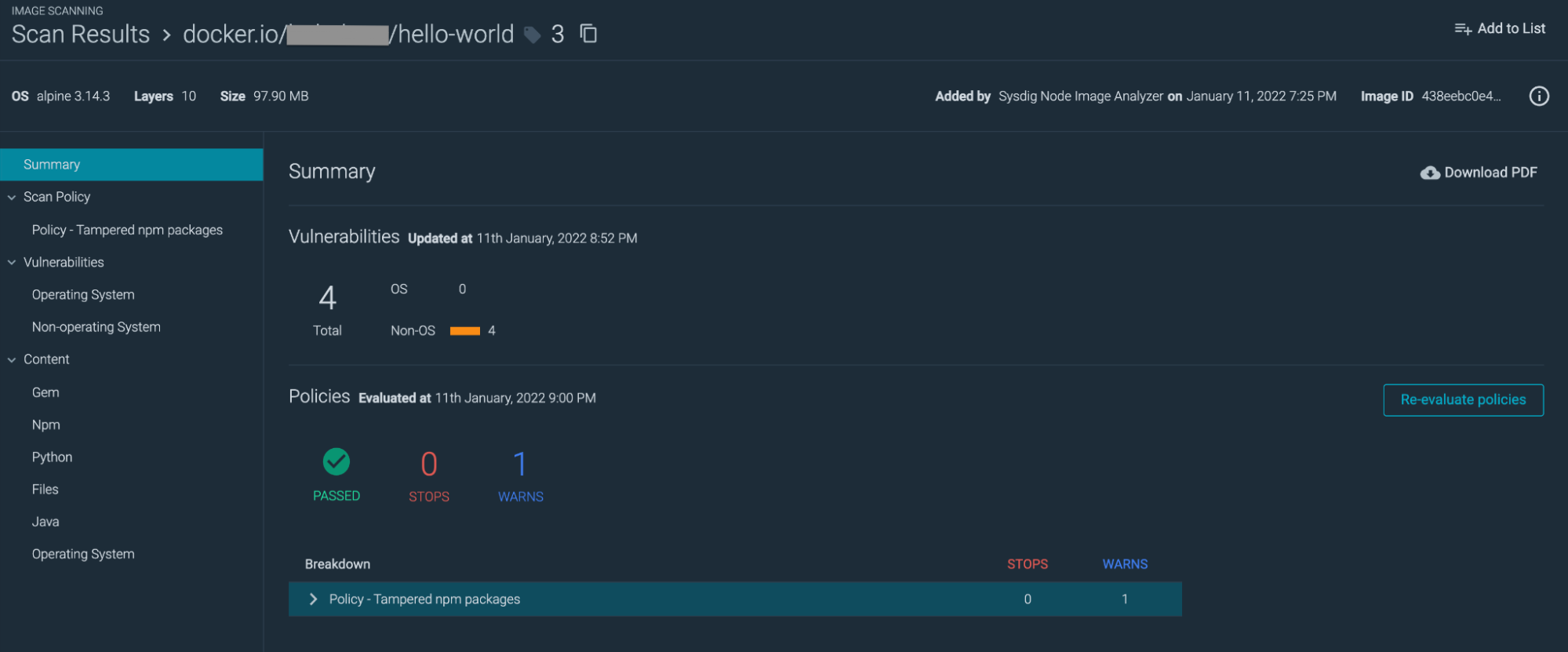
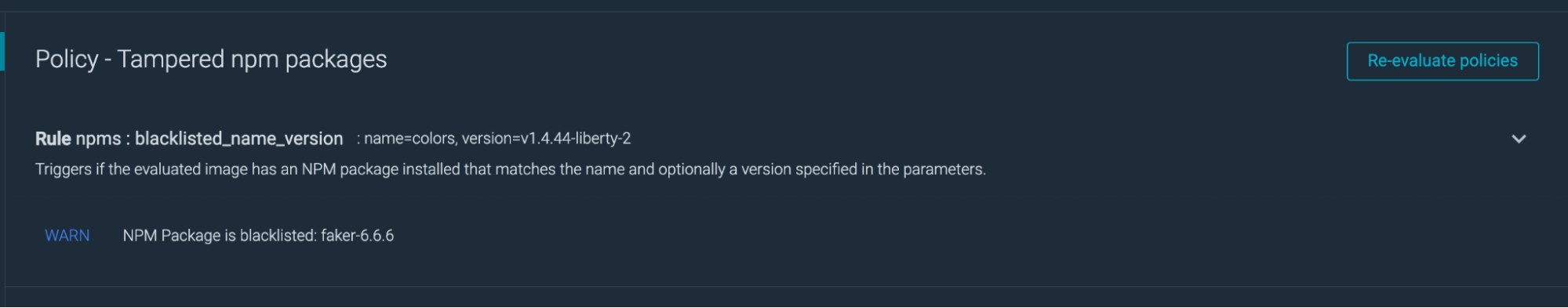
The image scan will yield the following results.
Notes for the future
This is an example of how deliberate modification of a single open source project affects thousands of applications. These types of events highlight the importance of maintenance or support of these projects. It can happen again.
In this article, we covered the compromise of two well-known and popular open source projects. Mitigating the presence of the damaged components requires attention to the versions that can be installed. Instead, you can detect the employed npm packages using Image Scanning.
Sysdig includes advanced image scanning features, like inline image scanning, continuous scanning, and vulnerability reporting. With Sysdig’s guided onboarding, you will be set in less than five minutes. Try it today!