While the cloud serves as a powerful accelerator for businesses, it also speeds up threat actors.
Automation and an ever-increasing level of sophistication allow threat actors to execute complex attack chains in merely minutes, sometimes even less. The risk factors are amplified by the ability to chain together exploits and quickly move laterally in cloud environments, where a single breach could lead to a business critical compromise.
Blue teams need to rapidly visualize and understand risks, correlate those risks with real-time events, and pinpoint critical paths that malicious actors might take to breach their systems.
Enter Risk Prioritization and Attack Path Analysis, a powerful solution designed to tackle these challenges head-on and provide invaluable insights into cloud security.
Powered by the Cloud Attack Graph, the new Risks page shows a prioritized list of the potential risks in your cloud infrastructure.
The risks in the page are not merely just another list of prescriptions: they are periodically re-evaluated and re-prioritized based on the findings in your infrastructure.
It is effectively a constantly updated assessment on your current risk factors, augmented with context derived from Sysdig’s runtime agent and detections.
Let’s see how you would assess a potential critical risk for your infrastructure.
Step 1) Identifying Critical Risks: Begin by navigating to the Sysdig platform’s Risk page, where the most critical risks are highlighted.
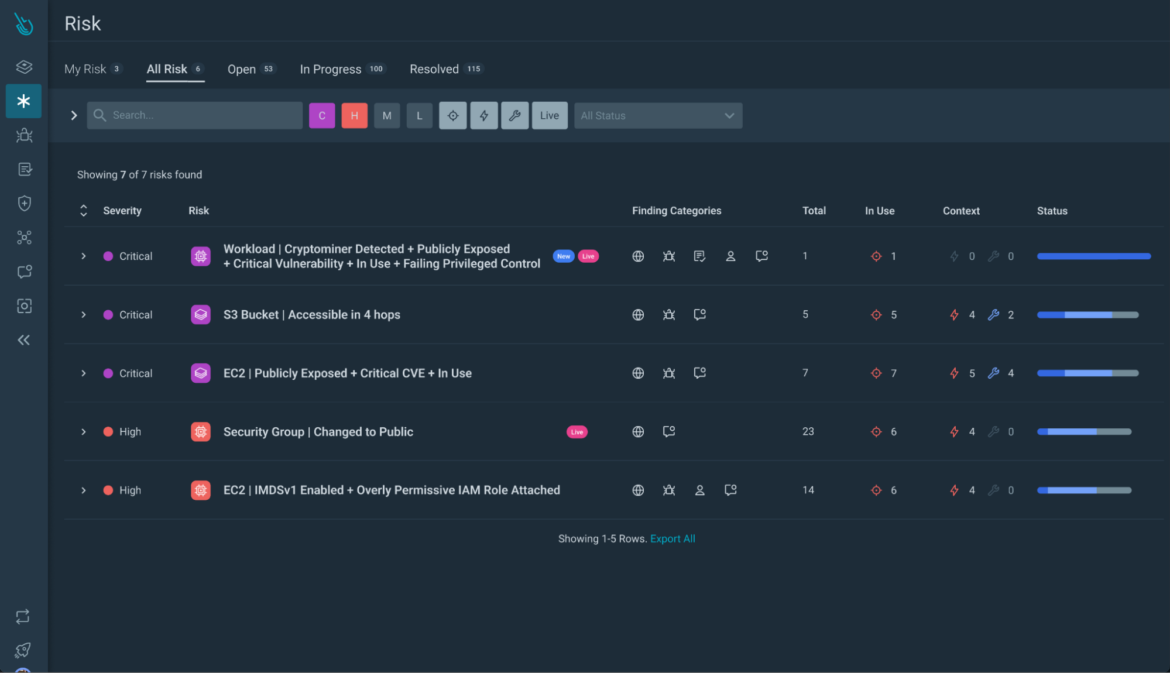
Risks is a curated list that combines Sysdig Secure findings and scores them as risk factors.
The findings that contribute to a risk can be of different types, for example:
- Vulnerabilities found through scanning
- Detections coming from the runtime agents
- Insecure configurations or identities
- Public exposure
The findings are also augmented with relevant context: you can see at a glance if the vulnerability is exploitable, fixable, and whether it involves packages actually in use.
Labels help you identify the risks that involve recent runtime events and new risks that weren’t there before.
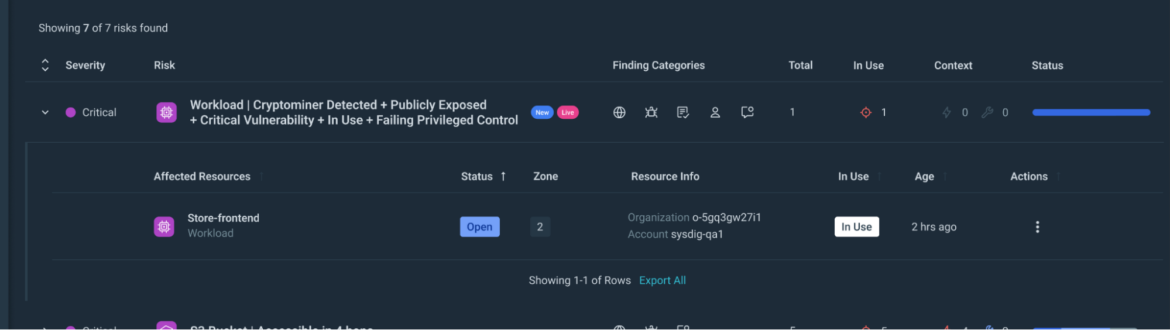
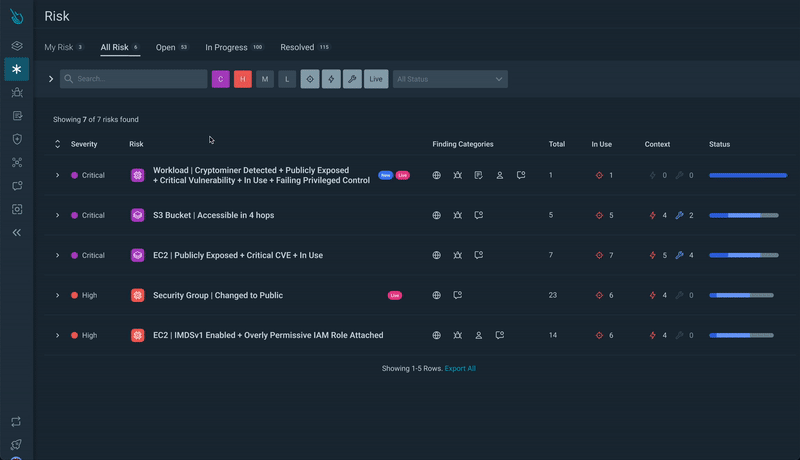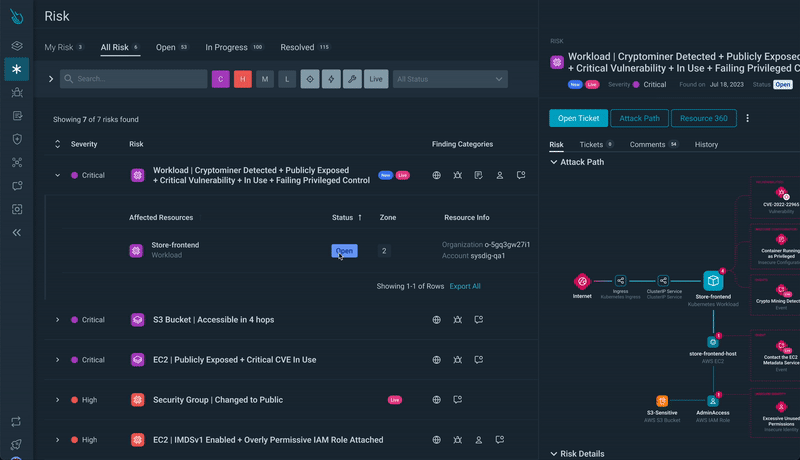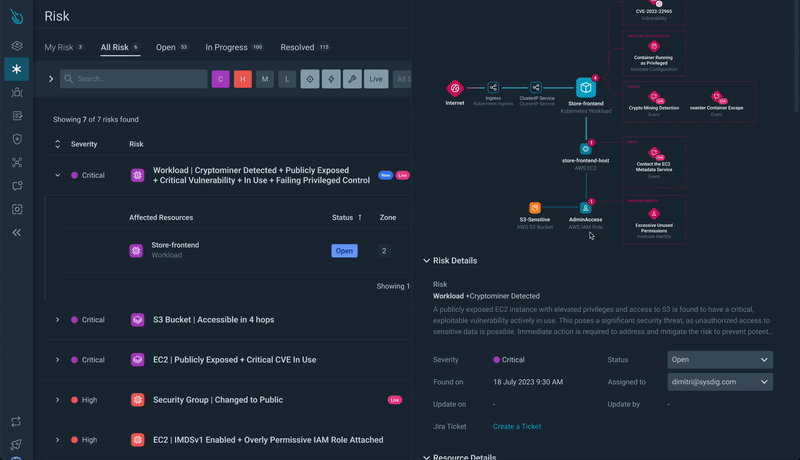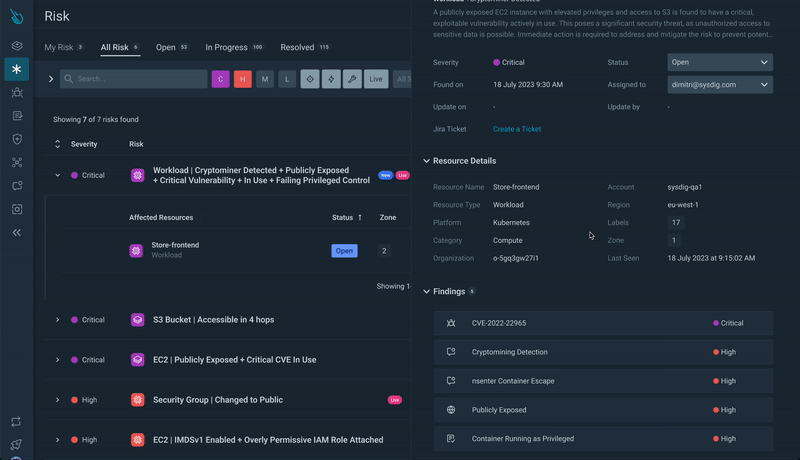
Step 2) Resource Identification: From the risk page, you can identify the resources involved in these critical risks.
Clicking on a risk gives you details on the affected resources:
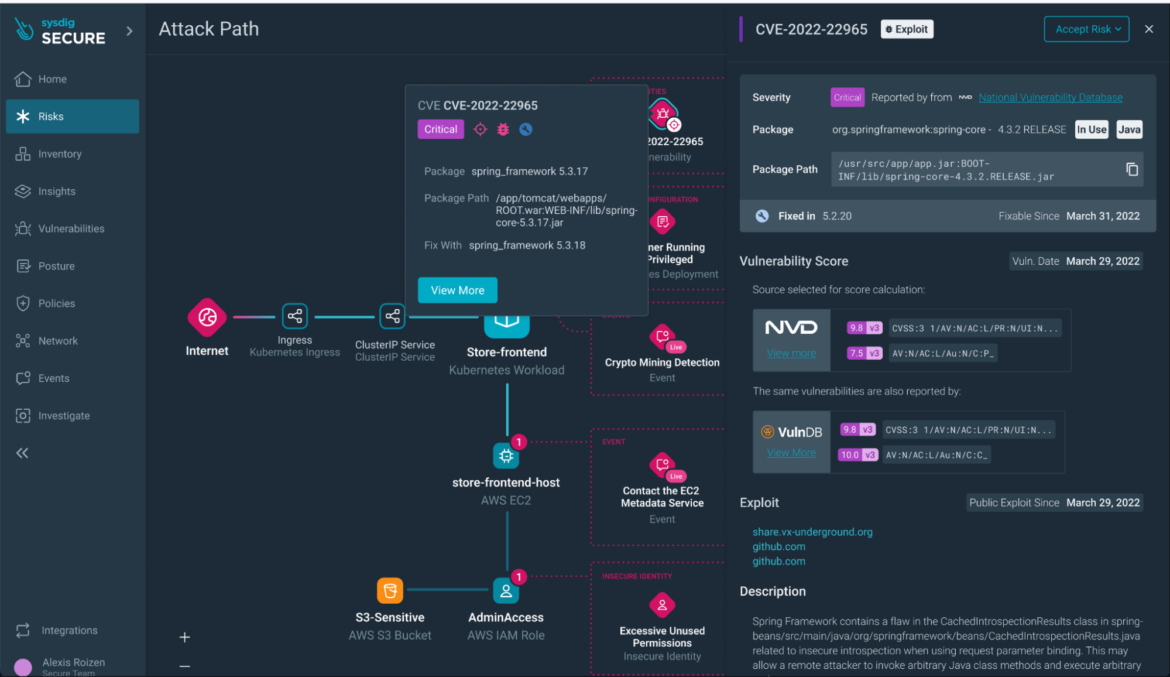
Step 3) Resource Analysis: Clicking on a resource, you’ll get a drawer with quick access to detailed information on the risk.
From there, you’ll get access to Attack Path Analysis.
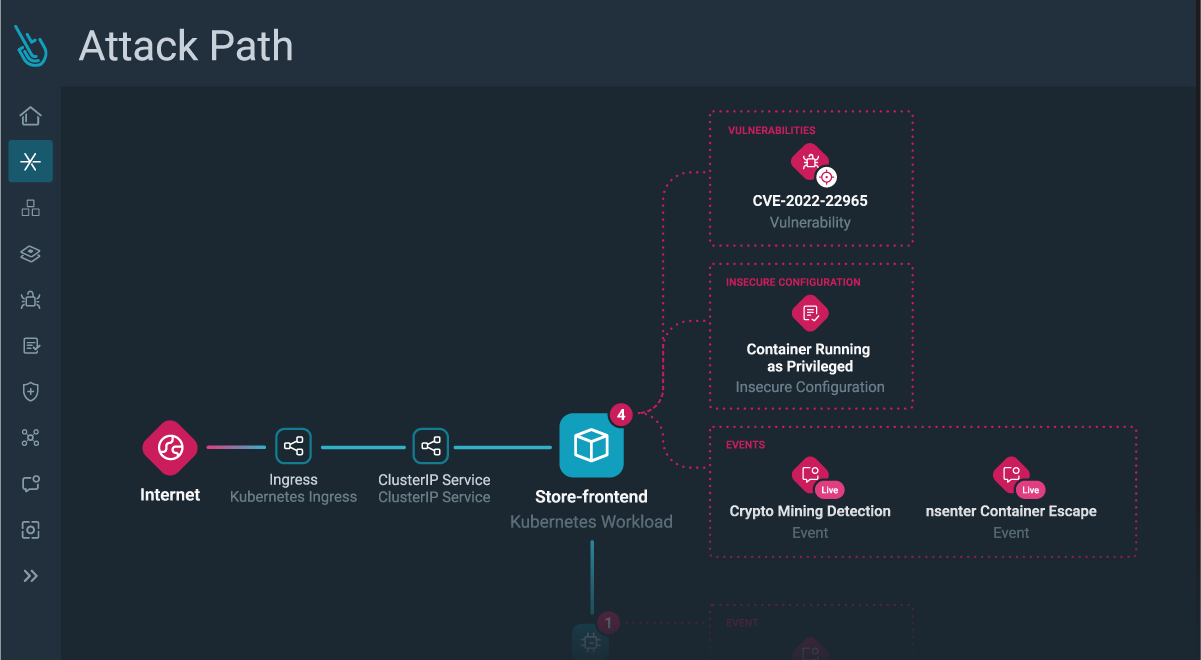
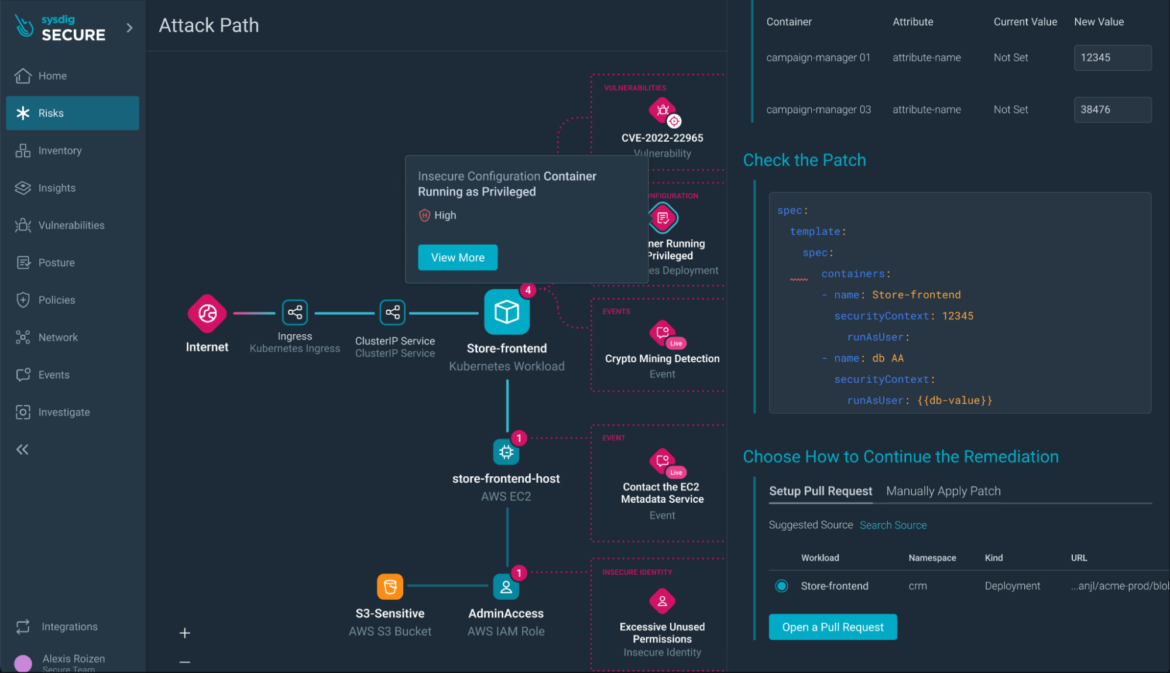
Step 4) Exploring Attack Paths: Delve deeper by opening the resource details, which lead you to the Attack Path. Here, you gain a comprehensive visualization of the risk, the associated resources, and the opportunity to explore further.
Attack Path Analysis offers a quick and efficient means to visualize security risks and provides several key benefits:
- Identifying Critical Paths: It goes beyond identifying individual risks and uncovers the critical paths that attackers might exploit to reach valuable assets. This proactive approach allows you to prioritize your security efforts effectively.
- Correlation of Risks and Runtime Events: Attack Path Analysis bridges the gap between potential risks and real-time events, allowing you to stop attacks before they can move laterally.
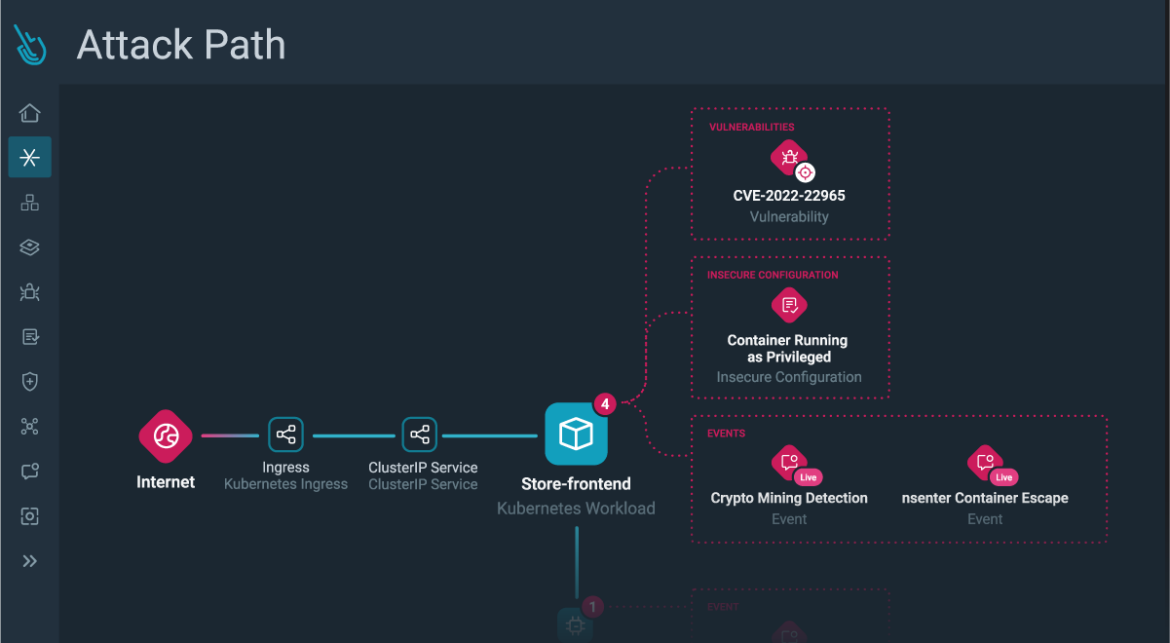
With Attack Path, you can identify at a glance the resources involved in the risk, their findings (including related runtime events), and the critical path an attacker may take when exploiting these weaknesses.
Step 5) Runtime Event Insights: Dive into runtime events, such as xmrig execution or a container breakout, for a granular understanding of the security situation.
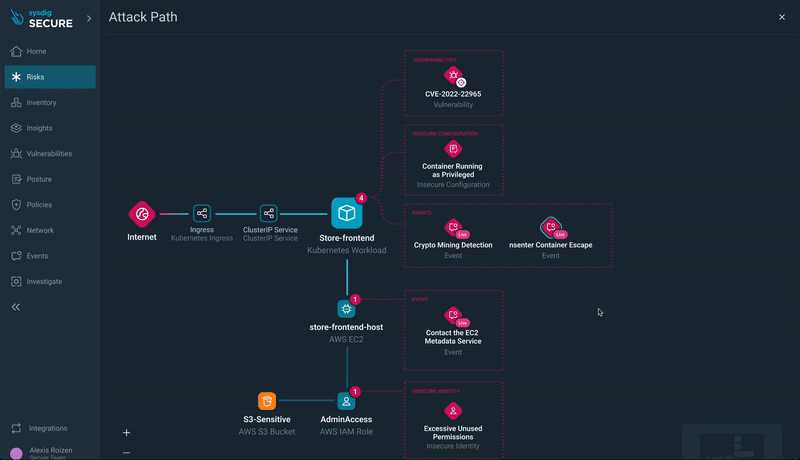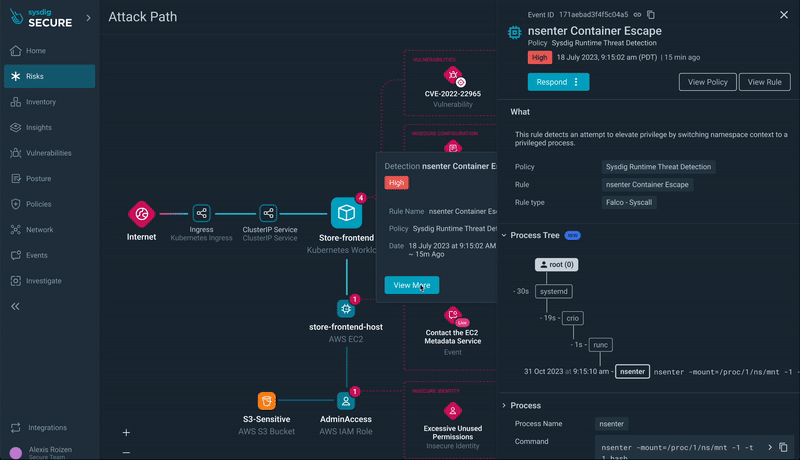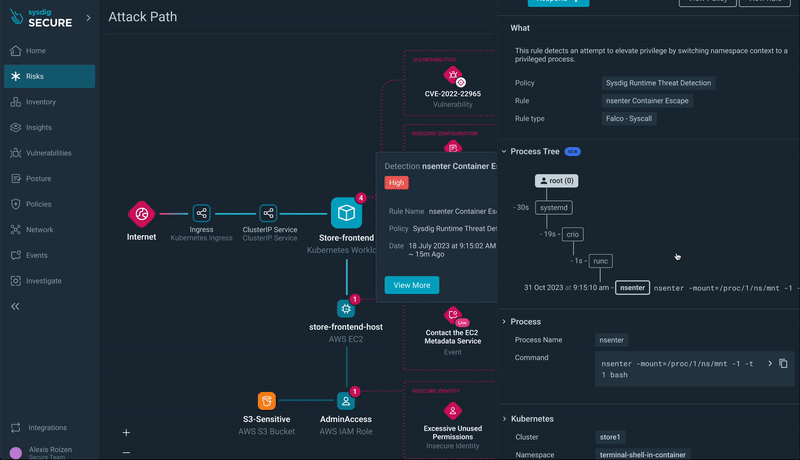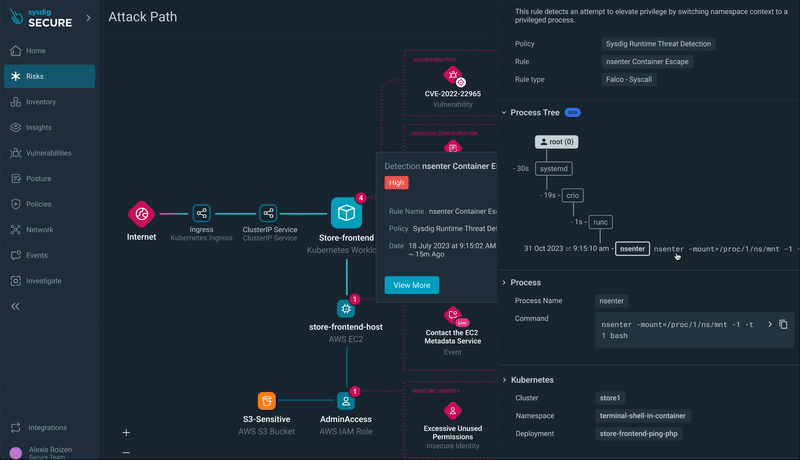
Step 6) Progressing through the Attack Path: Move to other resources in the attack path, such as the EC2 instance hosting the workload with a container escape event.
All resources with findings involved in the risk are displayed and quickly accessible from the Attack Path visualization:
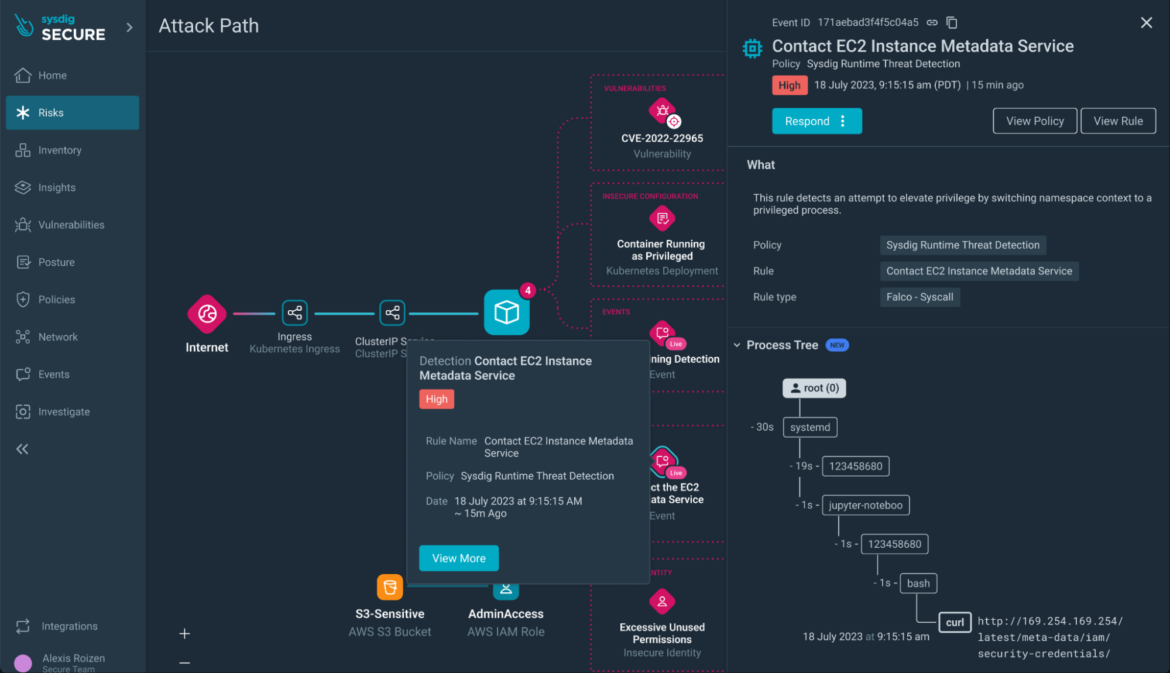
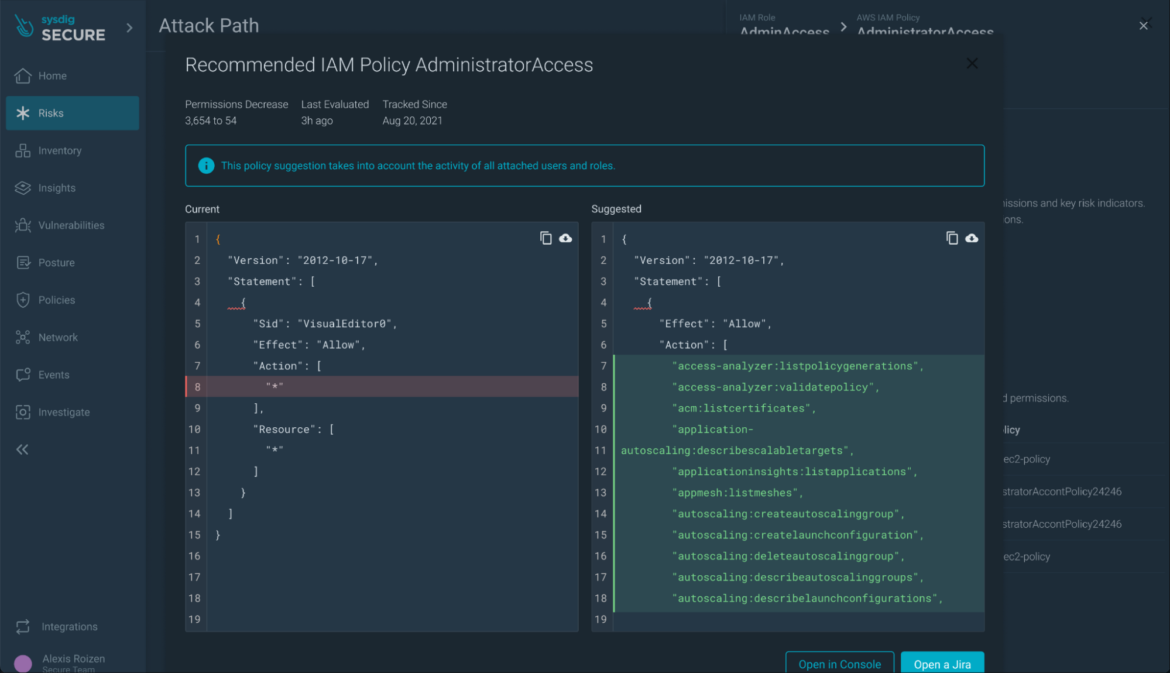
Step 7) IAM Role Analysis: Investigate the IAM role’s posture findings (e.g., overprivileged full admin access) and explore remediation options.
Resources in the attack path analysis are not limited to containers or compute workload. Overly permissive IAM roles, for example, can be part of an attack path that leads to lateral movement towards leaking sensitive data.
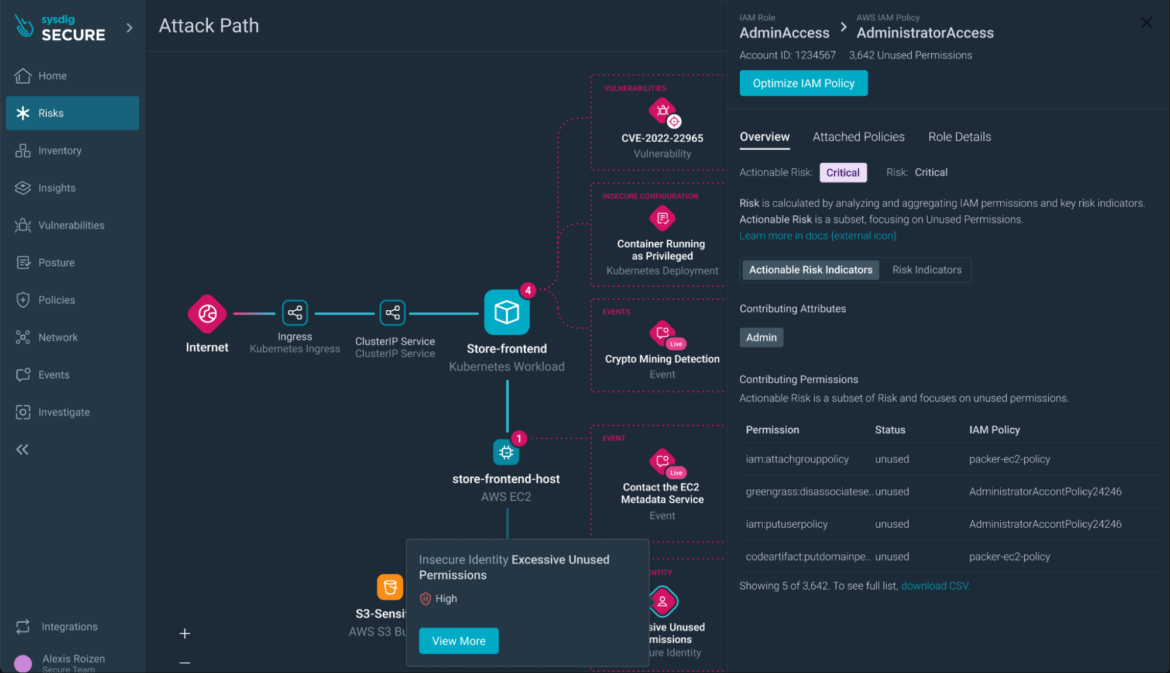
Step 8) Remediation time: Once you understand the risks, you can take immediate action to remediate them and prevent exploits.
Sysdig’s Attack Path Analysis simplifies the remediation process.
From the drawer of the IAM policy or the container resource, you can tailor policies to adhere to the least privilege principle.
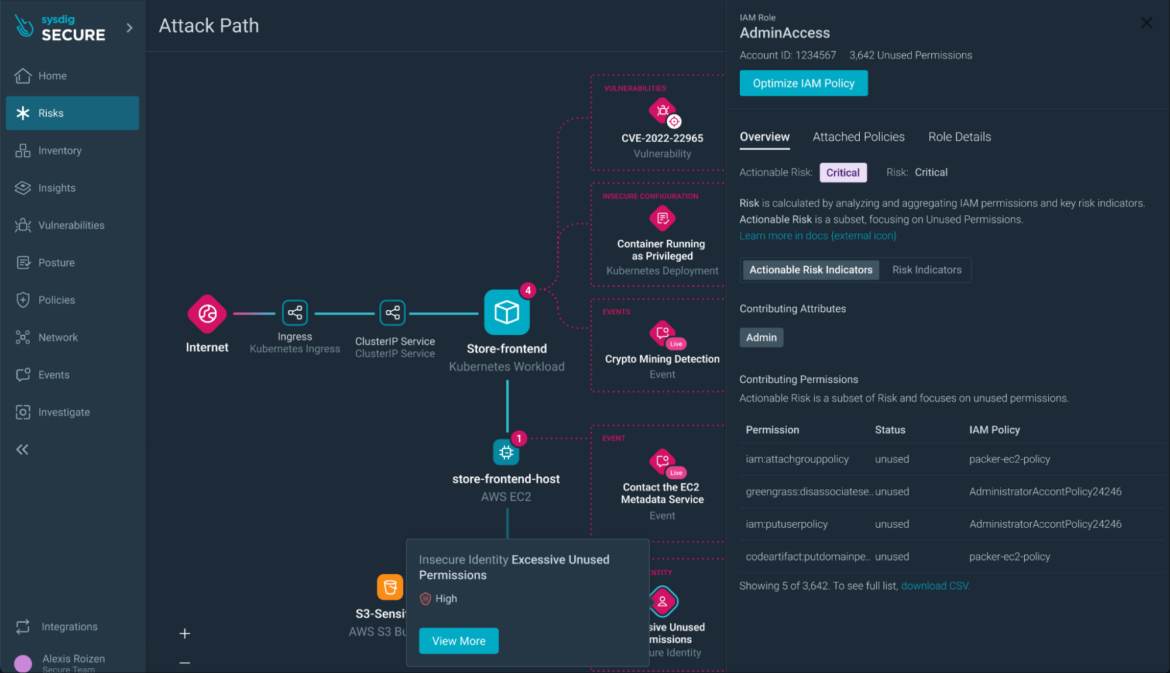
You can also seamlessly fix misconfigurations, such as privileged containers, directly at the code level, with precompiled PRs to the code repository.
Conclusion
In summary, Attack Path Analysis is a step up from traditional visualization methods, effectively correlating static and runtime details.
Its graphical representation empowers you to quickly understand and mitigate cloud security risks comprehensively.
It integrates the advanced features of Sysdig Secure in an easy to navigate UI, allowing you to rapidly take action where it is more effective.
The Risks page allows you to prioritize the most critical issues effectively with its curated list, and lets you keep track of the remediation process so you have an up-to-date view of your risks.
If you want to learn more about Attack Path Analysis:
- Read more about what is behind these features in our Cloud Attack Graph article.
- Learn more about our newest CNAPP features in this article.
- Don’t miss our webinar: Elevating Cloud Security with a Shift-Left and Shield-Right Strategy.
- If you want to see it in action, you can request a live personalized demo with a Sysdig expert.