Welcome to another monthly update on what’s new from Sysdig. Ramadan Kareem to all observing the holy month of Ramadan. Our team continues to work hard to bring great new features to all of our customers, automatically and for free! This last month was a big month for security with our release of Cloud Security Posture Management (CSPM), and we had lots of fun designing and releasing our new Cloud Chaos game!
The power of combined cloud and container security
Using different cloud and container security tools requires a manual correlation of logs to catch the breach and uncover the systems impacted. By unifying the incident timeline and adding risk-based insights, Sysdig reduces the time to detect threats across clouds and containers from weeks to hours. Cloud development teams can see exactly where the attacker started and each step they took as they moved through the environment.
Read “Cloud lateral movement: Breaking in through a vulnerable container” for more on the steps involved in this type of lateral cloud movement attack.
New continuous CSPM from Sysdig
Cloud security posture management for AWS based on Cloud Custodian: Sysdig adds cloud asset discovery, cloud services posture assessment, and compliance validation. Cloud security teams can manage their security posture by automatically discovering all cloud services, as well as flagging misconfigurations and violations of compliance and regulatory requirements. These new features are based on Cloud Custodian, an open source tool for securing cloud infrastructure.
Multi-Cloud Threat Detection for AWS and GCP Based on Falco: Sysdig adds support for cloud threat detection via GCP audit logs, in addition to the AWS CloudTrail integration from last year. Security teams can continuously detect suspicious activity or configuration changes across their infrastructure without relying on a periodic configuration check. Sophisticated attackers can take advantage of exposed configurations to access the cloud, then revert it immediately once inside. A static check could miss these changes, leaving openings for attackers, and also overlook indicators that an attacker has breached the environment.
Sysdig uses open source Falco, the Cloud Native Computing Foundation de facto runtime security project, and alerts based on continuously inspecting cloud audit logs. It performs the analysis within the user’s cloud account, which protects sensitive data and eliminates costs tied to exporting logs. Currently, there are more than 200 out-of-the-box CloudTrail rules, and the database continues to grow as Sysdig and the community contribute at a rate of 20-50 new rules per month.
All Sysdig events, including CSPM, compliance, container runtime, and AWS CloudTrail events can be sent to AWS Security Hub to allow security teams to respond to threats faster.
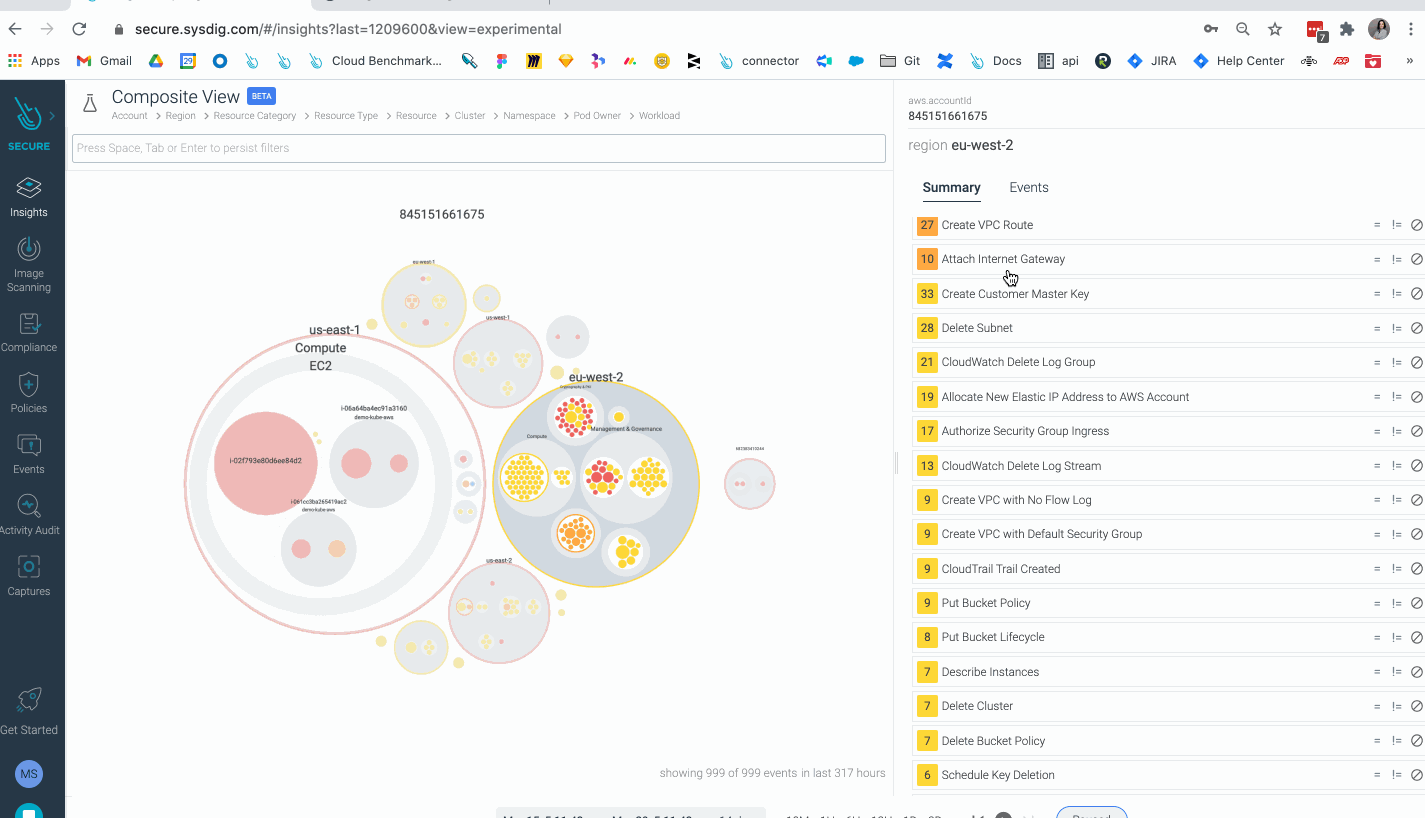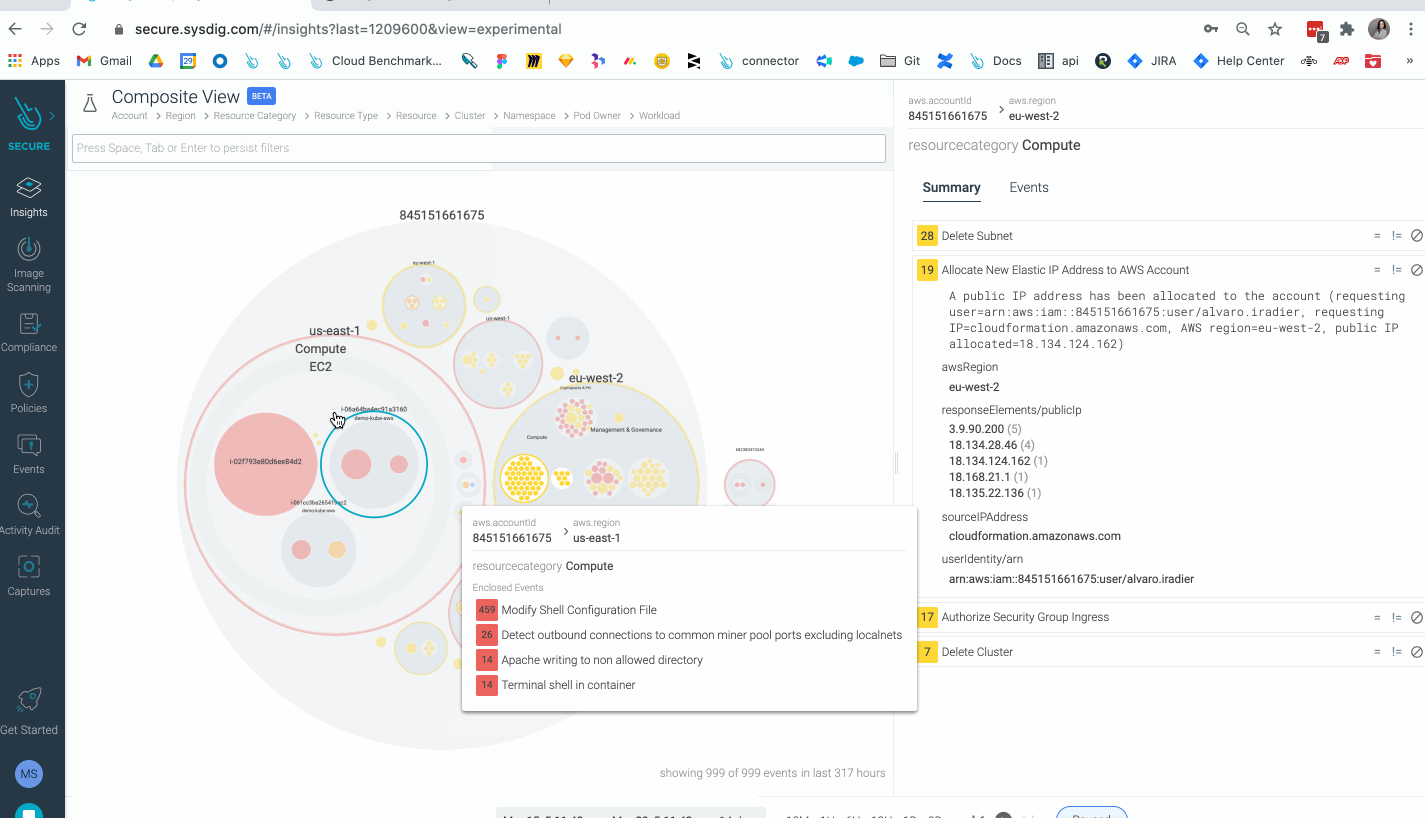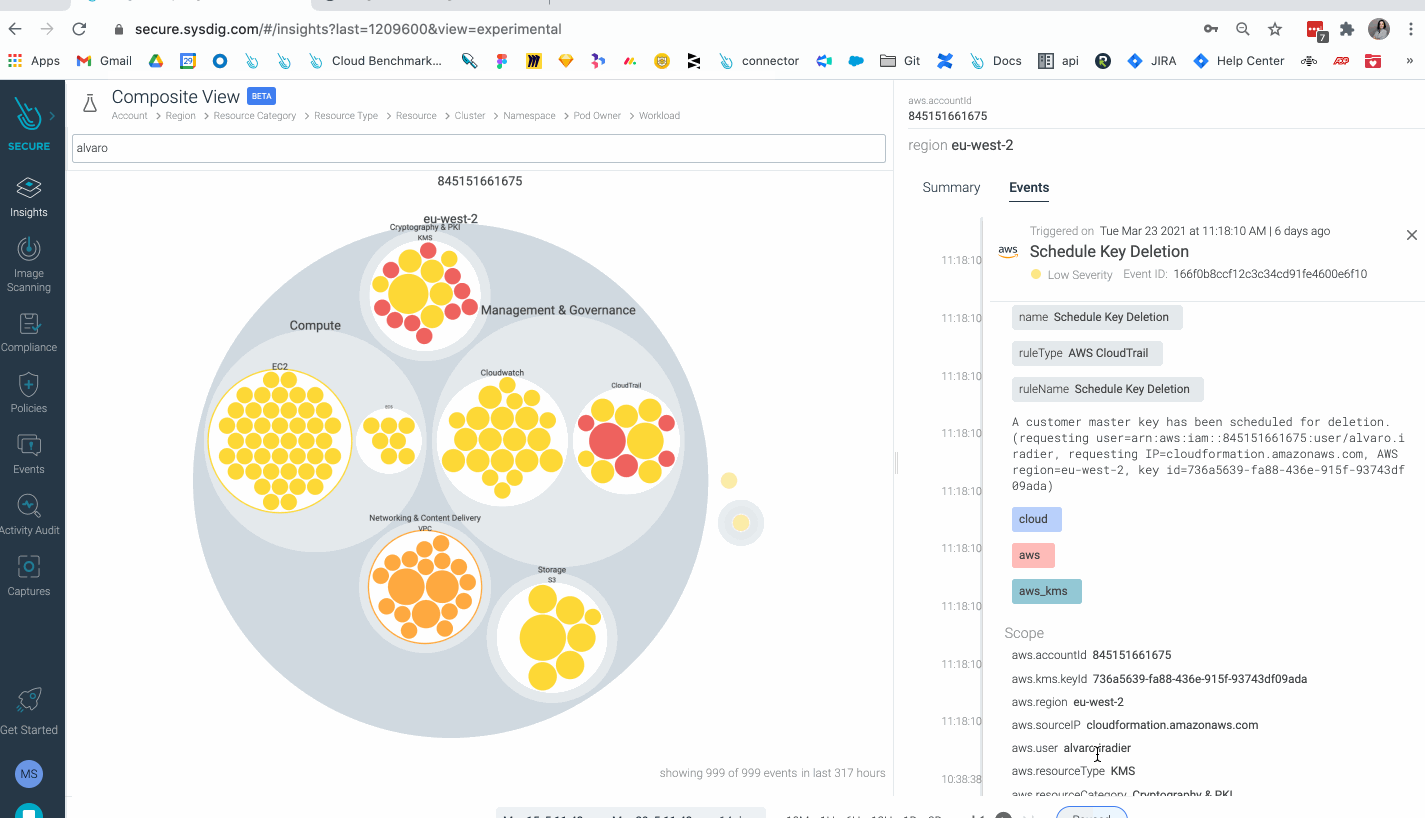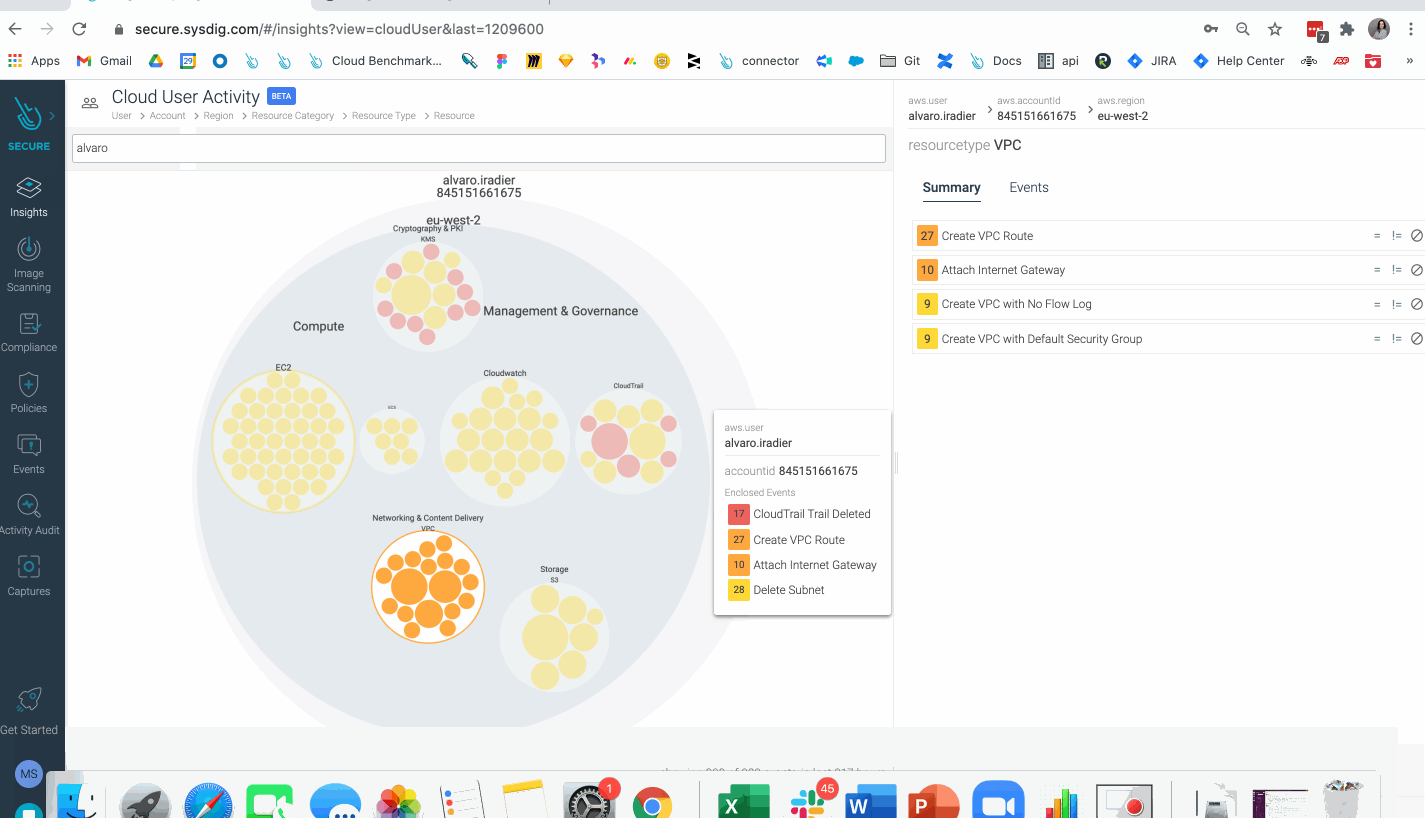
Cloud Risk Insights: Sysdig provides new visual insights across interconnected cloud and container security incidents, prioritized by risk levels. Sysdig reduces alert noise and provides instant visibility to see the entire cloud attack chain, from a hacker exploiting a container vulnerability and accessing the cloud, to elevating privileges and performing catastrophic actions, such as cryptomining on a Kubernetes cluster. Classifying incidents based on severity levels allows teams to prioritize what to investigate and respond to first. Teams can then investigate all suspicious activity performed by a user to see the breadth of impact and quickly begin incident response activities.
Free tier for cloud security
Sysdig is offering continuous cloud security for free, forever, for a single account. With easy onboarding, users can begin to manage cloud posture within minutes. The free tier includes a daily check against CIS benchmarks and continuous threat detection to ensure the cloud environments remains in a secure, compliant, and hardened state at all times. It also includes inline scanning for Fargate and ECR images, up to 250 images a month.
Open-standards approach to cloud security
Sysdig believes the future of security is open. Open source security delivers better security through faster innovation. Organizations can be confident they are adopting an accepted standard that will last. With this in mind, Sysdig chose to build its CSPM capabilities on top of Falco and Cloud Custodian. Sysdig selected the Cloud Custodian open source project because it has strong momentum in adoption, a rapidly growing database of rules, auto-remediation capabilities, and multi-cloud support.
Continue reading for more details on CSPM, as well as other new features that we have released this last month.
As always, please go checkout our own release notes for more details on product updates, and ping your local Sysdig contact if you have questions about anything covered in here.
Sysdig Secure
Sysdig Secure for cloud
Sysdig Secure for cloud is available with Cloud Risk Insights for AWS, Cloud Security Posture Management based on Cloud Custodian for AWS, and multi-cloud threat detection for AWS using Falco.
What’s Included in this release:
- Insights: A powerful new visualization tool for threat detection, investigation, and risk prioritization, helping you identify compliance anomalies and ongoing threats to your environment. With Insights, all findings generated by Sysdig across both workload and cloud environments are aggregated into a visual platform that streamlines threat detection and forensic analysis.
- Threat Detection based on AWS CloudTrail: To detect threats, anomalies, and suspicious activities with the flexible Falco engine. By leveraging AWS CloudTrail and the Falco language, you can detect any unexpected or unwanted behavior in your AWS accounts. Sysdig Cloud Connector leverages AWS CloudTrail as the source of truth for enabling governance, compliance, operational auditing, and risk auditing for your AWS account. Every API action over your infrastructure resources is recorded as a set of CloudTrail entries. Once the integration is deployed in your infrastructure, the Sysdig Cloud Connector can analyze these entries in real-time and provide AWS threat detection by filtering them against a flexible set of security rules. For more details, see the Sysdig Cloud Connector. Example detection rules include:
- Attach a user to an Administrator Policy.
- Create an HTTP Target Group without SSL.
- Deactivate MFA for user access.
- Delete S3 bucket encryption.
- Cloud Security Posture Management with AWS Benchmarks: The AWS CIS Benchmarks assessment evaluates your AWS services against the benchmark requirements and returns the results and remediation activities you need to fix misconfigurations in your cloud environment. We’ve included several UI improvements to provide additional details, such as: control descriptions, affected resources, failing assets, and guided remediation steps, both manual and CLI-based.
- Image Scanning for AWS ECR: One-click deployment using a CloudFormation template. Automatically scan images pushed to your Amazon Elastic Container Registry (ECR) using AWS-native technologies and Sysdig Secure. Sysdig image scanner integration is deployed as a CloudFormation template that listens to ECR registry events and uses AWS resources to streamline the image scanning process.
- ECR itself will trigger the scan, no need for your CI/CD pipelines to actively pull from the registry.
- Deployed in a few clicks, you just provide basic configuration parameters, such as the Sysdig API token or the Sysdig backend URL.
- No need to configure registry scanning credentials on the Sysdig Secure side.
- Image Scanning for AWS ECS & Fargate: One-click deployment using a CloudFormation template. Bringing the Sysdig Inline Scanning capabilities to automatically analyze the base images used for any task created using AWS Elastic Container Service (ECS or Fargate). Inline scanning living inside your AWS account means improved security:
- No need to expose or configure private AWS registries.
- Only image metadata is sent to Sysdig Secure, not the actual image contents.
- No sensitive information ever leaves your AWS account.
- An ephemeral task will be spawned to analyze each discovered image, in parallel.
- Fully automated.
- Scan results and scanning policies are still controlled from a single security governance point using Sysdig Secure.
How customers are using this
It’s no surprise that many Sysdig customers are container and Kubernetes users. Over the years, we’ve seen more and more people moving to managed container & Kubernetes platforms in cloud environments, and expanding their use of native cloud services. Our customers are now using these CSPM capabilities to extend the visibility and control that they had across their containerized applications into their whole cloud, and cloud native services. Our customers tell us this is allowing them to start thinking about tooling consolidation as well as providing a centralized view for all cloud consumers, including the security teams who often feel alienated by cloud native initiatives.
Free-forever cloud security tier
Sysdig is launching a new free-forever cloud security tier for one single account.
- Easy onboarding in minutes.
- Manage cloud posture with a daily run of CIS Benchmarks.
- Detect threats with out-of-the-box CloudTrail detection rules based on Falco.
- Scan containers (ECR/Fargate scanning) automatically and within your cloud environment for up to 250 images a month
How customers are using this
Many end-users we speak to that are considering Sysdig aren’t yet ready for a full tool, or they just need some simple use cases covered while they ramp up their cloud transformation and migration work. We’ve heard that while they are looking at the long-term picture, they still need something to help them with the short-term challenges and to start implementing some ‘quick wins.’ Our free tier is helping folks get a basic understanding of where they could improve their security, and start making those smaller improvements.
Image scanning reports v3 [BETA]
The Image Scanning Reports feature has been thoroughly updated and has moved from a synchronous model to an asynchronous mode, in which you schedule the reports you need and then receive them through your normal notification channels (e.g., email, Slack, webhook). The new version also includes:
- A preview function to check report structure in the UI.
- A more advanced query builder.
- Extended set of data columns (e.g., CVSS base score and vector) and extended set of available filters (e.g., package type).
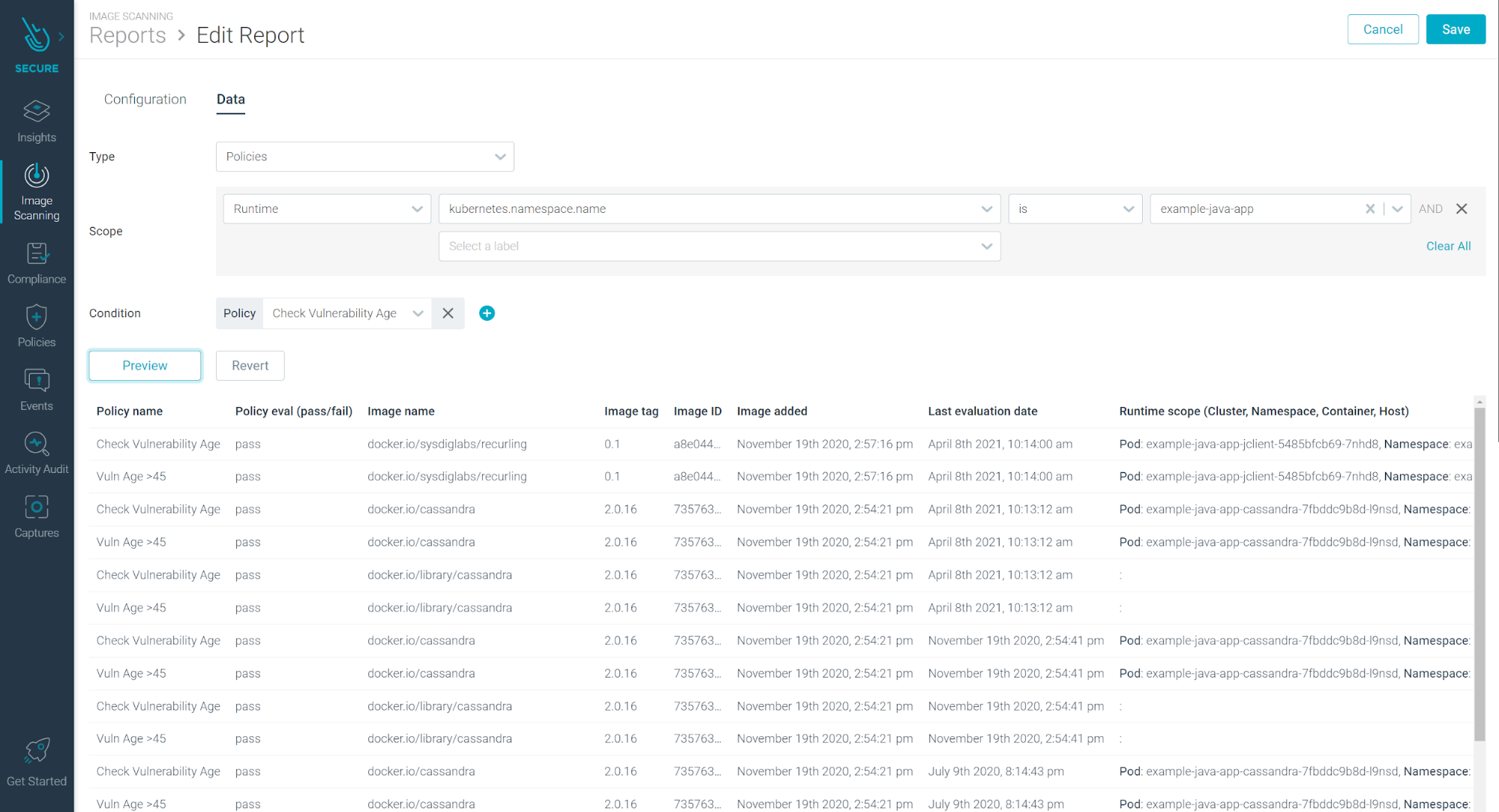
Reporting v3 supports two different types or reports:
- Vulnerability report: Containing vulnerability, package, and image data. For example, vulnerabilities in my runtime with
Severity ≥ High, a Fix available, and not included in a vuln exception list. - Policy report: Containing scanning policies and evaluated images data. For example, images in my internal registry failing the “NIST” scanning policy.
You need to enable this feature from the Sysdig Labs setting on the User Profile page.
How customers are using this
We’ve been listening to many customers ask for scheduled reports and the power to do complex reports that can take minutes if relying on real-time responses. Moving to asynchronous reporting has allowed the searching to be optimized and given customers more simplicity in the workflow. We’re hearing customers use these reports as part of their daily or weekly review tasks. They don’t need to leave their email inbox and can already start prioritizing security fixes and action new vulnerability notifications.
Feature enhancement: Falco policy types
Sysdig Secure has introduced Policy Types, a separation of policies into logical groups, based on the sources used in the policy engine. When creating a policy, you choose a type and then only the relevant scopes and container actions will be presented. We have also introduced a new policy type to support threat detection with AWS CloudTrail rules.
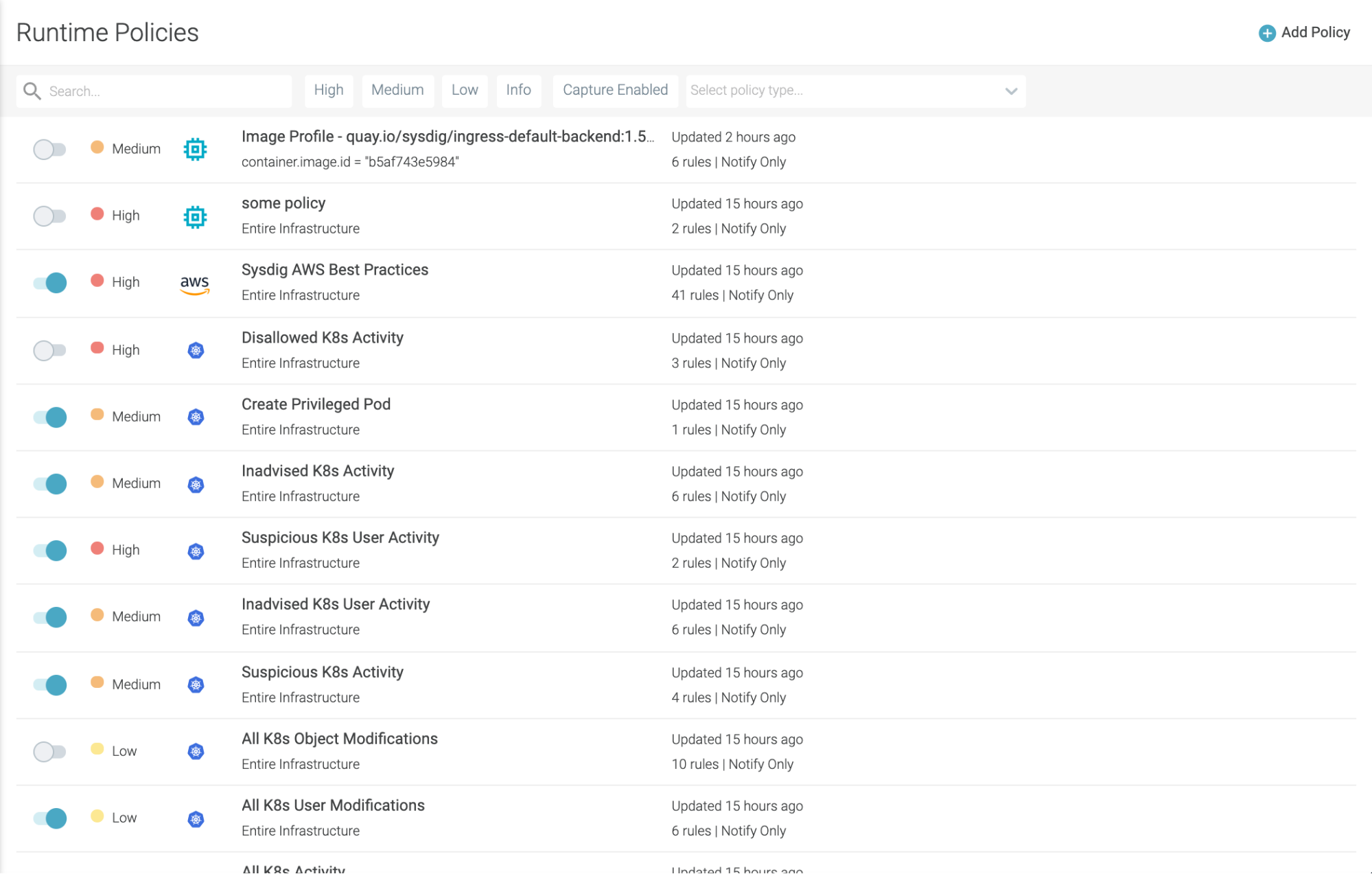
For full details, see Manage Policies.
How customers are using this
This has simplified the workflow for our customers. CSPM introduced a large number of new rules, so it has become important to allow users to quickly and visually filter through the policies to see the relevant policies for the task in hand. As they scale the usage, this becomes important for policies scoped and deployed across potentially thousands of hosts and dozens of cloud environments.
Sysdig Serverless Agent 1.0.0 for Fargate ECS
The “container-as-a-service” serverless environment calls for new agent models, and Sysdig provides them. Whereas in ECS, users still manage the underlying instances, with AWS Fargate the host is never visible and users simply run their workloads. And while this model is convenient, it can introduce risk as many people leave the containers unattended without monitoring security events that can exfiltrate secrets, compromise business data, impact performance, and increase AWS costs. In addition, it is impossible to install a standard agent in an environment where you do not have access to a host.
For these reasons, Sysdig has introduced a new “serverless agent” model that can be deployed in these container-based cloud environments. The first implementation is for Fargate (ECS).
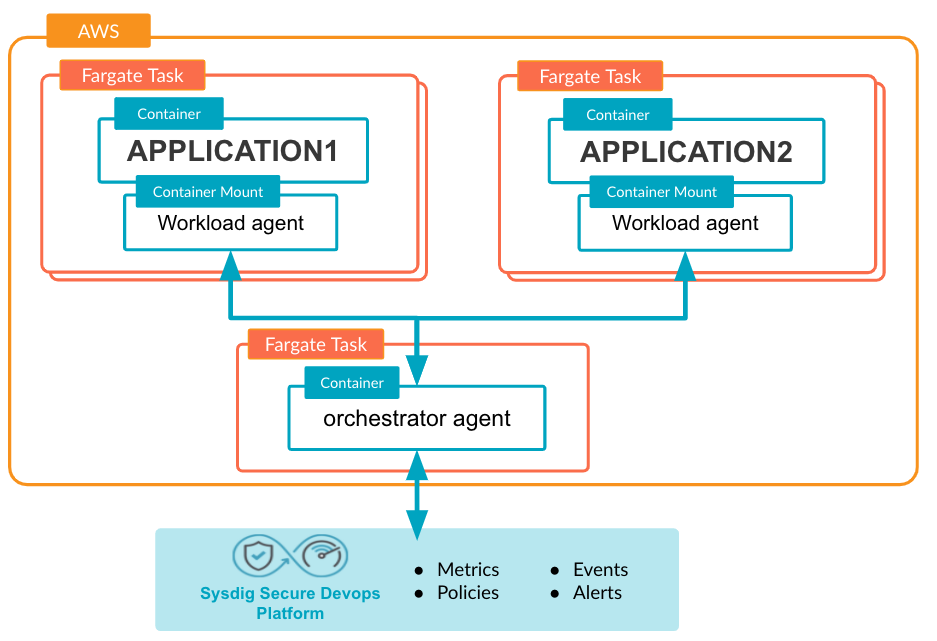
Sysdig will be rolling out security features on the serverless agent over time. In v1.0.0, users will see:
- Runtime Policies and Rules.
- Secure Events.
To obtain secure event information, and the associated Falco policies and rules in the Sysdig Secure UI from a Fargate environment, users install the serverless agent using a CloudFormation Template. Then, log in to Sysdig Secure and review the events in the UI.
See also: AWS Fargate Serverless Agents.
How customers are using this
This provides Sysdig users with much needed visibility and control of their Fargate workloads. We’re seeing more people migrating to managed Kubernetes platforms, but they don’t want to compromise on the visibility they have when using a fully deployed variant. We’re hearing this helps accelerate the adoption of fully managed Kubernetes like Fargate, which comes with other advantages around operational efficiencies.
Falco rules
v0.12.1 is the latest version. Below is a diff of changes from v0.10.5, which we covered last month.
- Fixed a defect that could prevent deploying rules to several older Sysdig backend versions.
- Added new versions of
falco_rules.yaml/k8s_audit_rules.yamlthat use exceptions instead of collections of macros and long condition strings. The rules coverage should be identical to older versions. - Fixed minor problems with the rules installation script.
- Added 164 rules that detect suspicious/anomalous/notable behavior from a stream of AWS CloudTrail events. This requires a Sysdig backend that supports policy types and running the Cloud Connector.
- The new policy, Sysdig AWS Best Practices, includes 41 of the above rules that Sysdig recommends using for the AWS environments.
Sysdig Monitor
PromQL cheatsheet
Since releasing PromQL support in Sysdig Monitor, we’re seeing many customers make great use of this feature and leverage their existing Prometheus skills investments. Some fantastic use-cases are being built out and it’s great to see users get the most out of our native enterprise support. However, for every PromQL expert, there are 10 other users who haven’t used Prometheus before or don’t know where to start. We’re doing things to make the transition easier, including the release of a PromQL Cheatsheet to help folks get started. Whether you’re new to PromQL or just need a handy reference guide, this should be a really useful resource to have in your toolkit.
Sysdig Agents
Sysdig Agent
The latest Sysdig Agent release is 11.1.2. Below is a diff of updates since 11.0.0, which we covered in our last update.
- Enhanced Connection with Kubernetes API Server
- Kubernetes reconnect logic has been improved to automatically back off (1 min, 2 min, 4 min… 1hr) if the connection is continuously dropped when using Thin Cointerface. This reduces the load that the agent imposes on the Kubernetes API Server in clusters with heavily burdened API servers.
- Reduced Load on Kubernetes API Server
- The agent’s readiness probe has been improved to not report ready until after the agent connects to the Kubernetes API server. This reduces the load that the agent imposes on the Kubernetes API server when starting up during RollingUpdate.
- Agent Reports Memory Usage Accurately for Containers
- Fixed an issue where the agent would incorrectly report
memory.bytes.usedfor containers that use more than 4GB.
- Fixed an issue where the agent would incorrectly report
- Runtime Policies Work as Expected
- The runtime policies that have a policy type and capture action are handled as expected.
- Agent Tags in Policy Scopes
- Agent tags are supported in runtime policy scopes.
- Metric Limits Are Updated As Expected
- Fixed a problem where metric limits were not updated from the defaults. This is unlikely to happen if agents are connected to the SaaS backend.
- Configured Tags in Prometheus Scraper
- Fixed a problem in the old Prometheus scraper (used when promscrape is disabled) to ensure that configured tags are properly added to the metrics.
- JMX Metrics for Short-Lived Java Processes
- Fixed an issue where short-lived Java processes could cause the Sysdig Agent to stop collecting JMX metrics.
- Misconfiguration No Longer Leads to Agent Constantly Querying Kubernetes API Server
- Fixed a problem where the agent would continuously send requests to the Kubernetes API server to query the endpoints API. This occurs when the agent’s clusterrole is incorrectly configured. With this fix, the agent will no longer repeat the attempt if it is unable to connect to the Kubernetes API during boot.
- Scope Runtime Policies
- The runtime policies are now correctly scoped by kubernetes.cluster.name. The fix in 10.6.0 was incomplete.
- Agent Correctly Reports Replicasets
- Fixed an issue where the agent could lose track of a replicaset and report incomplete metadata.
- Agent Issues Over HTTP Proxy
- Fixed an agent connection issue over plaintext HTTP proxy with encryption.
- Fixed an agent connection issue via HTTP proxy connections over SSL.
Sysdig Serverless Agent
Introduced this last month, the current version is v1.0.0.
The “container-as-a-service” serverless environment calls for new agent models, and Sysdig provides them. Whereas in ECS, users still manage the underlying instances, with AWS Fargate the host is never visible and users simply run their workloads. And while this model is convenient, it can introduce risk as many people leave the containers unattended without monitoring security events that can exfiltrate secrets, compromise business data, impact performance, and increase AWS costs. In addition, it is impossible to install a standard agent in an environment where you do not have access to a host.
For these reasons, Sysdig has introduced a new “serverless agent” model that can be deployed in these container-based cloud environments. The first implementation is for Fargate (ECS).

Sysdig will be rolling out security features on the serverless agent over time. In v1.0.0, users will see:
- Runtime Policies and Rules
- Secure Events
To obtain secure event information, and the associated Falco policies and rules in the Sysdig Secure UI from a Fargate environment, users install the serverless agent using a CloudFormation Template. Then, log in to Sysdig Secure and review the events in the UI.
See also: AWS Fargate Serverless Agents.
Sysdig Agent – Helm chart
The Helm Chart 1.11.11 is the latest version. Below is a diff of updates since v1.11.7, which we covered in our last update.
- Use the latest image for Sysdig Agent (11.1.2).
- Fix in the
imageanalyzer extravolumes. - Improvements and fixes in README for installation instructions (use
sysdig-agentnamespace by default).
Node image analyzer
Version 0.1.11 was released, and contains the following diff updates since v0.1.10, which we covered in our last update.
- Fixed a bug that prevented the Origin field from being populated on the UI for images analyzed by NIA on containerd environments.
- Fixed an issue that resulted in some unscanned images with “unknown media type during manifest conversion” error logs on containerd environments.
- Fixed an issue that caused the NIA container to report “unhealthy” status.
Node image analyzer can be installed as part of the Sysdig Agent install.
Inline scanning engine
Version 2.3.2 is still the latest release, which we covered in our last update.
See also: Integrate with CI/CD Tools.
SDK, CLI and Tools
Sysdig CLI
v0.7.8 is the latest release. Below is a diff of updates since v0.7.5, which we covered in our last update.
- Add runtime security policy types support (as discussed in the Secure section above).
- Update
sdc-cli event getto use theget_eventmethod in SDK (This allows the retrieval of an event via its ID even if it’s very old). - Add dashboard import from PromCat format.
- Allow restore policy type from backups.
See also: Sysdig CLI page.
Python SDK
v0.15.1 is the latest release. Below is a diff of updates since v0.14.13, which we covered in our last update.
- Add
get_eventby ID method to Events client v1 and v2. - Add policy types support (as discussed in the Secure section above).
- Add
delete_sysdig_capturemethod. - Add user provisioning without email confirmation.
Terraform provider
v0.5.14 has been released. Below are the diff changes from v0.5.11, which we covered last month:
- Allow to use
aws_cloudtrailpolicies. - Add policy types support (as discussed in the Secure section above).
- Add Falco rule type ‘
aws_cloudtrail‘. trigger_after_pctnot handled correctly insysdig_monitor_alert_downtimeresource.
See also: Sysdig Terraform provider documentation.
Falco VS Code extension
v0.1.0 is still the latest release.
Sysdig Cloud Connector
v0.6.4 was released. Below is a diff of updates since v0.5.1, which we covered last month:
- When the loader finds a duplicated rule/macro/list, override it.
- Allow rules exceptions when validating.
- Added CIS GCP Foundation Benchmark rules for Virtual Machines.
- Added CIS GCP Foundation Benchmark rules for Networks and DNS.
- Added CIS GCP Foundation Benchmark rules for LOGGING (sinks).
- Enable Secure integrations by default.
- Enable sending the header with the account ID to Secure.
- Added CIS GCP Foundation Benchmark rules for IAM and APIKEYS.
- Use
aws.*fields instead of plain jevt on rules. - Added “
@type“-like compatibility to jsonpath in rule files. - breaking change: Add support for ‘@’ character in
jevt.eventrules (currently Falco OSS implementation does not support this, but we do need it for the GCP accounts). - When segment key is not specified, return an error.
- GCP Rules for: Describe Instance, Super Admin Executing command.
- GCP Rules for: Buckets.
- Add
gcp.userandgcp.callerIpto GCP events scope. - Add
gcp.locationto GCP events scope. - Add default notifiers (metrics, console, and tracking) to cloud-scanning.
- Allow query scopes using the event
getField. - Show rule name alongside policy name on Secure Event Feed.
- Do not exit when loading rules on incorrect order, but log it.
- Filter out unneeded logs on
auditlog. - Integrate with Secure Account Registration.
- Add pagination to the gcp logging reader.
- Add
policy_idto the event in secure. - Notifiers set the event timestamp to the event occurrence date instead of alert creation.
- rules-validator: Only print error info on error.
- Update AWS SDK to v2.
- Use the same args/output than OSS Falco in rules validator.
- rules-validator: Allow empty files.
- Filter events on the pipeline according to the Secure settings.
- Add GCP Stackdriver notifier.
- Allow specifying the log level.
- New ECS Exec rules.
- Display the Falco rule name in the event for Sysdig Secure, in addition to policy.
- Ignore non-
aws_cloudtrailrules when validating. - Include build and version info.
- rules-validator: Fix output message while reading rules file.
See also: Sysdig Cloud Connector documentation.
Sysdig Secure inline scan for Github Actions
v3 is still the latest version.
Sysdig Secure Jenkins plugin
v2.1.7 was released. Below is a diff of updates since v2.1.4, which we covered last month:
- Support some edge cases where the digest in the report doesn’t match the local digest and makes the execution fail.
- Error with Dockerfile when the Docker daemon is running in a different host instead of in the agent.
- Improve environment variable handling for inline-scan.
See more: Sysdig Secure Jenkins plugin homepage.
Deprecation Notices
Legacy commands audit & legacy policy events
- The “Commands Audit” feature was deprecated in favor of Activity Audit in Nov. 2019. This feature will be completely removed from the SaaS product in April 2021.
- Sysdig agent version 0.93+*, released in Nov. 2019, is required by the Activity Audit feature.
- The “Policy Events” feature was deprecated in favor of the new Events feed in June 2020. This feature will be completely removed from the SaaS product in April 2021.
* Sysdig agent version 10.3.0+ is recommended.
Training & education
We released several new training courses related to cloud security this month. You can find them in our training portal, and they cover the following topics:
- Amazon ECR Image Registry Scanning.
- Amazon ECS & Fargate Image Scanning.
- Cloud Security Posture Management and Compliance.
- Threat Detection based on CloudTrail.
- Deploying Sysdig Cloud Security for AWS.
- Sysdig Cloud Security on AWS Workshop (which covers several of the above areas).
We’ve also released a couple of labs on image vulnerability scanning:
- Image Scanning: Sysdig Admission Controller: Learn how to scan your images at the last security barrier with the Sysdig Admission Controller.
- Image Scanning: Malware Detection: Learn how to protect your deployments from malware and harmful files coming from untrusted image sources.
New website resources
Blogs
- What’s new in Kubernetes 1.21?
- Unified threat detection for AWS cloud and containers
- AWS CIS: Manage cloud security posture on AWS infrastructure
- Cloud lateral movement: Breaking in through a vulnerable container
- Detect suspicious activity in GCP using audit logs
- AWS S3 security with CloudTrail and Falco
- ECS Fargate threat modeling
- Running commands securely in containers with Amazon ECS Exec and Sysdig
- Getting started with PromQL – Includes Cheatsheet!
Webinars
- Supercharging Kubernetes Labels And Metrics – Watch on demand
- Top Dockerfile Best Practices – April 22, 2021 10am Pacific | 1pm Eastern
- Fighting Fraud – Worldpay Protects Cardholder Data – April 29, 2021 10am Pacific | 1pm Eastern
- Securing Serverless Containers on AWS Fargate – May 13, 2021 10am Pacific | 1pm Eastern
- Preparing for the Certified K8s Security Specialist (CKS) Exam – May 20, 2021 9am Pacific | 12pm Eastern



