
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

The Sysdig Windows agent is a game-changer for cloud infrastructure, particularly when it comes to securing Windows containers in Kubernetes environments. While many endpoint protection agents are designed to provide security for traditional Windows hosts, Sysdig goes a step further by incorporating Kubernetes-specific context into its system introspection. This integration is critical as enterprises increasingly adopt hybrid cloud and containerized infrastructure, and securing both Linux and Windows workloads within Kubernetes becomes a necessity.
What is the Sysdig Windows agent?
Your Windows system is a high security museum with priceless artifacts (like the Louvre) and our agent is a team of specialized guards, constantly patrolling the halls, stopping patrons from touching artifacts, and ensuring everyone follows the strict rules to keep your treasures safe. Leveraging the power of open-source Falco, the agent ensures robust workload security by detecting unexpected behaviors and enforcing compliance policies.
What makes Sysdig's approach unique is that it brings the same visibility & security traditionally found in Kubernetes pods running on Linux nodes to workloads running on Windows servers.
Why the Sysdig Windows agent is critical for modern cloud environments
In a cloud-native world, organizations have already rapidly adopted Kubernetes and containers to scale their applications and services. While Linux has been the dominant player in cloud environments, Windows workloads remain a crucial component for many businesses, and are only growing in significance, especially when running legacy applications or specific enterprise services with hyperconverged infrastructure (HCI) solutions that host Windows and Linux containerized workloads and hosts.
With the Sysdig Windows agent, enterprises gain visibility and security for Windows workloads running in Kubernetes environments, ensuring that security policies are uniformly applied across all workloads. This consistency is vital for maintaining compliance with regulations like PCI, GDPR & HIPAA, as well as for ensuring that Windows workloads aren't the weak link in your security posture.
Moreover, by integrating with Sysdig's backend, the Windows Agent can seamlessly collect and analyze data, enabling real-time detection and prevention of malicious activities such as unauthorized access, file tampering, and runtime anomalies.
What sets the Sysdig Windows agent apart from a typical EDR agent?
1. Native Kubernetes support: One of the standout features of the Sysdig Windows agent is its ability to run natively in Kubernetes. This capability differentiates it from other Windows endpoint protection agents on the market, which may focus solely on standalone Windows systems. By operating directly within a Kubernetes node, the agent can collect Kubernetes-specific context, such as pod metadata, enabling more granular visibility into Windows containers.
2. Uniform detection rule semantics across multiple clouds: This capability is crucial for enterprises operating complex multi-cloud or hybrid environments that combine Linux & Windows containers. With Sysdig, organizations can ensure consistent detection rules across diverse workloads, whether they are running on Linux or Windows in the same Kubernetes cluster.
3. Non-intrusive instrumentation via ETW: Finally, the Sysdig agent leverages Event Tracing for Windows (ETW) in a non-intrusive way to interface with the Windows Kernel, eliminating the need for an extra kernel probe or driver to collect telemetry data. The ETW API offers a way to trace & log events generated by both user-mode apps and kernel-mode drivers. Integrated directly in the Windows OS, ETW provides developers with a fast and flexible approach to Windows detection and response.
Sysdig Windows agent prerequisites and installation
The Sysdig Windows Agent currently supports the latest Windows builds, with Windows Server 2019 and above being the minimum required version. This applies to both standalone Windows server deployments and Kubernetes-based deployments using Helm.
Installing the Sysdig Windows agent via CLI
For those who prefer the command line, the installation process is straightforward. You can install the Sysdig Windows Agent in silent mode using the following Command Line or PowerShell command:
msiexec /i sysdig-agent.msi COLLECTOR_URL=<COLLECTOR> COLLECTOR_PORT=6443
ACCESS_KEY=<AGENT_ACCESS_KEY> ACCEPT_TERMS_CONDITIONS=True /qnIn this command:
- Replace
<COLLECTOR>with the URL of your Sysdig collector. - Replace
<AGENT_ACCESS_KEY>with your Sysdig access key.
Installing Sysdig Windows agent on Kubernetes via Helm
For Kubernetes users, Sysdig offers a Helm chart that enables the installation of the Windows Agent with ClusterShield enabled. ClusterShield enhances Kubernetes metadata enrichment, providing more detailed insights into your workloads.
Here's the Helm command to install the Sysdig Windows Agent:
helm repo add sysdig https://charts.sysdigv5.wpenginepowered.com
helm install sysdig-agent --namespace sysdig-agent --create-namespace \
--set global.sysdig.accessKey=<ACCESS_KEY> \
--set global.sysdig.region=<SAAS_REGION> \
--set nodeAnalyzer.enabled=false \
--set global.clusterConfig.name=<CLUSTER_NAME> \
--set agent.windows.enabled=true \
--set clusterShield.enabled=true \
--set clusterShield.cluster_shield.log_level=warn \
--set clusterShield.cluster_shield.features.kubernetes_metadata.enabled=true \
sysdig/sysdig-deployKey Helm flags
—set global.sysdig.accessKey=<ACCESS_KEY>
This flag specifies your Sysdig access key.
—set global.clusterConfig.name=<CLUSTER_NAME>
This sets the name of your Kubernetes cluster.
—set agent.windows.enabled=true
This enables the Sysdig Windows agent.
—set clusterShield.enabled=true
Enables the ClusterShield feature for enhanced security.
—set clusterShield.cluster_shield.log_level=warn
Sets the log level to "warn," meaning only warnings and critical issues are logged.
—set clusterShield.cluster_shield.features.kubernetes_metadata.enabled=true
This enables Kubernetes metadata enrichment, providing detailed context for Kubernetes workloads running on Windows nodes.
Writing detection rules for Windows
The Sysdig CNAPP platform offers managed Falco rules tailored for Windows workloads, covering container and host activities. These managed rules are aligned with established security frameworks like MITRE ATT&CK, ensuring a more robust cybersecurity approach. With pre-configured rules available out-of-the-box, Sysdig enables users to quickly implement effective threat detection on Windows systems.
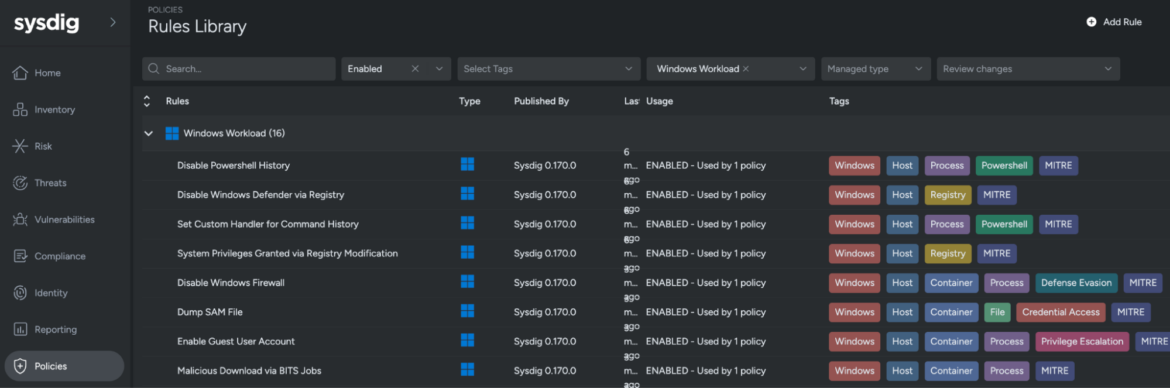
Detection rules based on Falco
DevOps engineering teams are already well-acquainted with Falco, the CNCF graduate project used for real-time threat detection through syscall monitoring. Instead of creating a new solution, leveraging the same technology trusted by the cloud-native community is more efficient. Windows detection rules are written in YAML and follow the same abstractions as the open-source Falco project, streamlining the process for teams. This consistency allows security teams to quickly develop detection rules for both Linux and Windows workloads, avoiding the need to learn yet another proprietary detection logic.
Below is a basic example of a Falco Rule for detecting command shell processes executed inside a pod.
- rule: Windows Shell Spawned Inside Container
desc: Detects when the command shell is spawned inside a container.
condition: >-
process_execute and container_windows and proc.name in
(windows_shell_binaries)
output: >-
Shell Spawned in Container (evt.type=%evt.type evt.args=%evt.args
proc.name=%proc.name proc.pname=%proc.pname gparent=%proc.aname[2]
ggparent=%proc.aname[3] ggparent=%proc.aname[4] container.id=%container.id
container.name=%container.name container.image=%container.image)
priority: critical
tags:
- Windows
- Container
- MITRE_TA0002_execution
source: windowsIn a Falco rule, you can reference a List Resource to specify the Windows shell binaries you want to monitor, enabling you to scope the process names for detection.
- list: windows_shell_binaries
items: [cmd.exe, powershell.exe, putty.exe, git-cmd.exe, pwsh.exe]Once the rule is triggered, you can examine the parent-child relationship through the Process Tree event. This allows you to see which processes were executed, along with their associated command-line arguments, within the Windows container. Additionally, you can gain detailed insights into the specific system call event types involved.
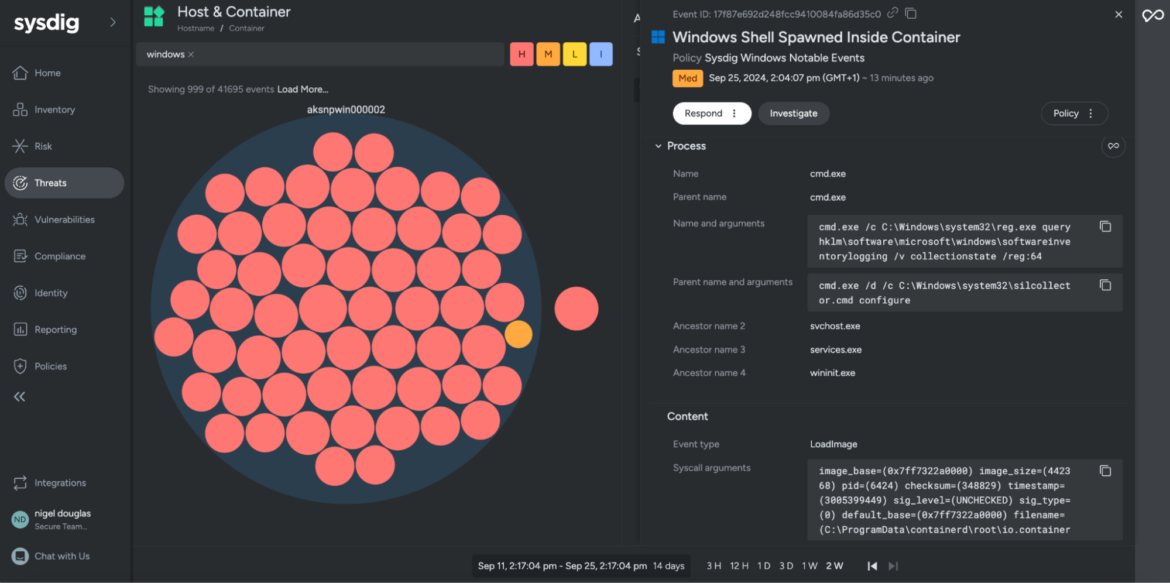
Effective incident response in Kubernetes environments requires DevSecOps engineers to correlate process and container activity with Kubernetes metadata, such as Pod, Node, Deployment, Namespace, and Cluster name. This integrated context enables security teams to respond to incidents on Windows systems without manually piecing together information from a process to the Kubernetes abstractions. This streamlined approach significantly enhances the speed and precision of threat response.
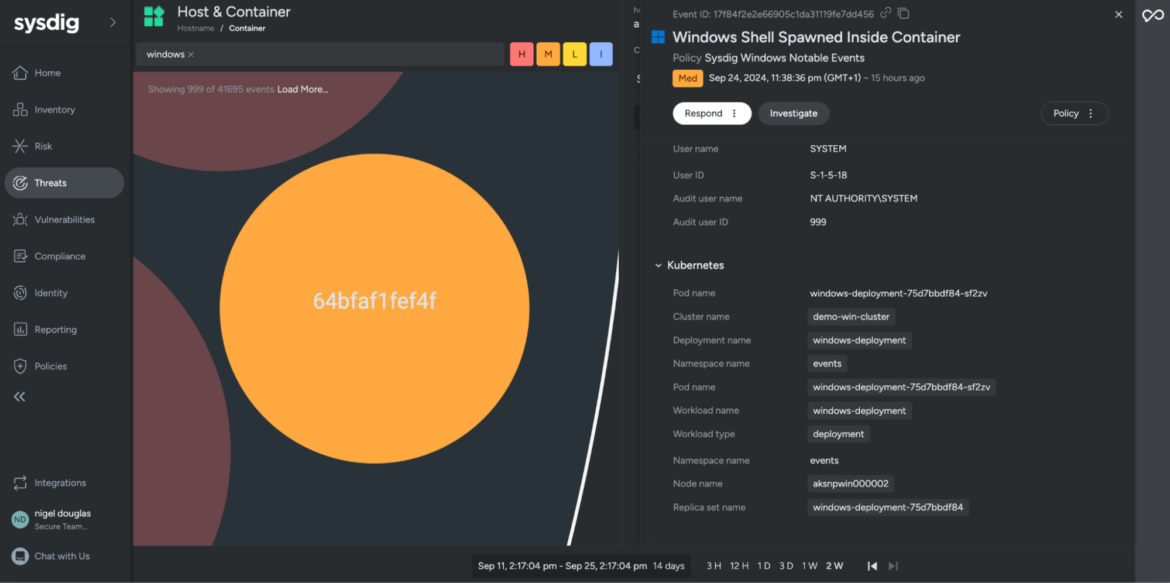
Benefits of Kubernetes Context for Windows Workloads
By running natively in Kubernetes, the Sysdig Windows Agent provides several advantages:
- Enhanced Visibility: The agent captures detailed Kubernetes metadata, including pod and container information, making it easier to understand how your Windows workloads are behaving within the broader Kubernetes environment.
- Unified Security Posture: Whether your workloads are on Linux or Windows, Sysdig applies the same policies and protections, ensuring Detection and Response efforts are consistent.
- Scalability: Sysdig's architecture is designed to scale with your Kubernetes environment, meaning that as you add more nodes and workloads, Sysdig automatically adjusts to provide continuous CDR protection through Runtime Insights.
Conclusion
As organizations move towards hybrid and multi-cloud environments, it becomes essential to have tools that offer cross-platform, cloud-native and on-premise security. The Sysdig Windows Agent extends Sysdig's already robust security capabilities to Windows workloads, particularly in Kubernetes environments. By collecting Kubernetes-specific context and integrating seamlessly with the Sysdig platform, the Windows Agent ensures that all your workloads, Linux or Windows, are protected, compliant, and monitored for potential threats.
For enterprises seeking to modernize their cloud infrastructure while maintaining stringent security standards, the Sysdig Windows Agent represents a critical addition to their existing security toolset. Whether you're running legacy Windows applications or modern microservices, the Sysdig Windows Agent ensures that your Windows workloads are not left vulnerable in an increasingly complex cyber threat landscape. If you're new to the concept of running Windows Containers in Kubernetes, you can check out the official Kubernetes User Guide.


