Is your organization grappling with the relentless pace of ever-changing threats in the cloud? Are you spending hours investigating security events without identifying the root cause of the problem?
The move to the cloud and containers has sped up innovation but also expanded the attack surface that security teams must defend. As organizations grow their cloud infrastructures, they encounter the challenge of sprawl, with hundreds of unchecked and potentially vulnerable applications, services, and identities. Cybercriminals are adapting to this landscape, utilizing advanced techniques to gain access to these environments and extract maximum value. With the global average cost of a data breach reaching a staggering $4.35 million last year, according to IBM, staying ahead of attackers is critical to prevent becoming another statistic in this alarming trend.
Expanding detection and response across the application life cycle
The dynamic attack surface of the cloud has greatly increased the complexity of securing cloud-native applications. Organizations are deploying hundreds or even thousands of containers in production, and managing large volumes of cloud assets and permissions. As a result, security teams and developers need an integrated tool that instantly and continuously provides visibility and shares context across the entire environment. More and more organizations are looking for a cloud-native application protection platform (CNAPP) that consolidates security across the application life cycle, instead of relying on multiple costly solutions that protect different areas.
This is especially important since attackers only require a single entry point into your environment to inflict substantial harm. Once inside, they can move laterally to access sensitive data or carry out cryptojacking attacks. In this battle, the integration of cloud detection and response (CDR) within a comprehensive CNAPP becomes a vital capability. Security teams must possess the ability to swiftly identify various types of threats spanning their entire infrastructure, and respond promptly within a limited timeframe. The scope of threat detection has now expanded to encompass not only workload runtime security, but also cloud services, identities, and the software supply chain. By consolidating CDR and CNAPP, your organization can attain a full understanding of potential threats and proactively address them before they manifest into significant issues.
Most existing cloud security tools fall short
Most existing cloud security tools are slow to identify suspicious behavior and don’t provide sufficient context for security teams to understand how an attack was carried out. This lack of context hinders effective incident response. Once alerted by these tools, organizations often find themselves in a time-consuming and frustrating process of sifting through numerous snapshots, logs, and disparate data sources, trying to piece together the intricate chain of events. This delay prolongs the exposure to threats by hours or even days, allowing them to cause widespread damage while the organization remains in the dark, unaware of the full extent of the breach. Other conventional security tools, like endpoint detection and response (EDR) tools, are not designed to handle the scale or velocity of the cloud and struggle to address cloud-native constructs or show correlation across user activity and workload anomalies.
In evaluating security tools designed for the cloud, there is a debate over whether agent-based or agentless approaches are more effective. The most effective solutions, however, will incorporate both. In the 2023 Gartner® Market Guide for Cloud-Native Application Protection Platforms, Gartner advises prioritizing CNAPPs that “provide a variety of runtime visibility techniques…to provide the most flexibility at deployment.” By leveraging a combination of real-time, agent-based detections and log-based, agentless detections, you can swiftly identify threats across your entire cloud environment and surface the necessary context to respond. Existing cloud security vendors that are unable to offer strong agent-based AND agentless solutions will never provide the complete approach necessary to effectively combat modern threats.
Real-time and end-to-end threat detection
Sysdig is expanding our CDR capabilities to provide end-to-end threat detection throughout the entire cloud fabric. With Sysdig Secure, we are introducing a new agentless deployment of Falco for processing cloud logs to detect threats across cloud, identity, and the software supply chain.
Sysdig’s agentless deployment model supplements our existing agent-based deployment of Falco. We’ve already solved the hard part of cloud security, cloud-native runtime security, with our agent-based workload protection. Combined with our agentless detection capabilities, Sysdig provides 360-degree visibility and correlation across workloads, identities, cloud services, and third-party applications. No matter what entry point an attack targets, our flexible deployment models empower you to protect your cloud and applications effectively.
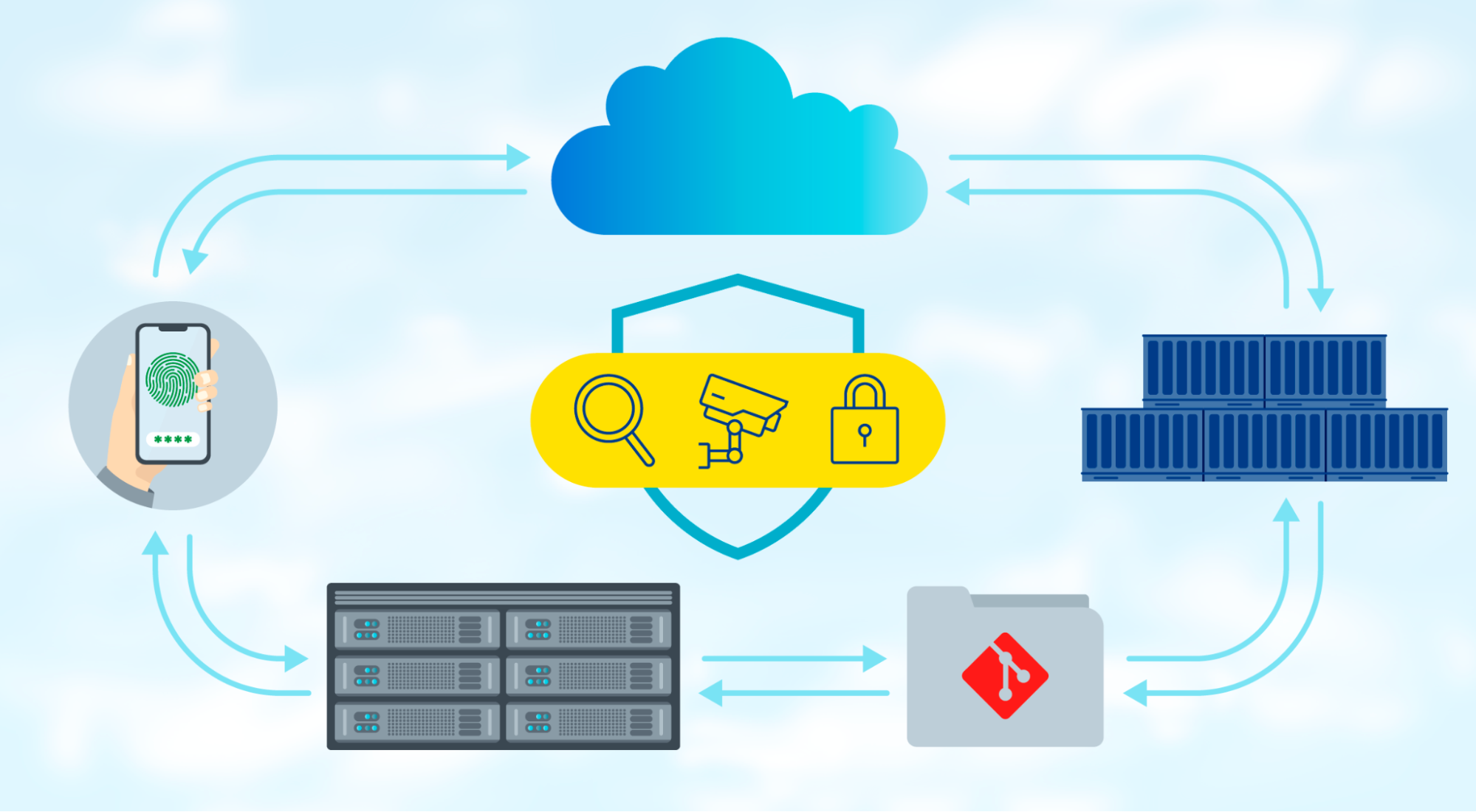
Identity threat detection
Malicious actors have continued to develop techniques for obtaining valid credentials to access sensitive data. Sysdig’s Okta detections enable security teams to protect against common identity attacks, such as multifactor authentication fatigue caused by spamming and account takeover, protecting your valuable data from unauthorized access.
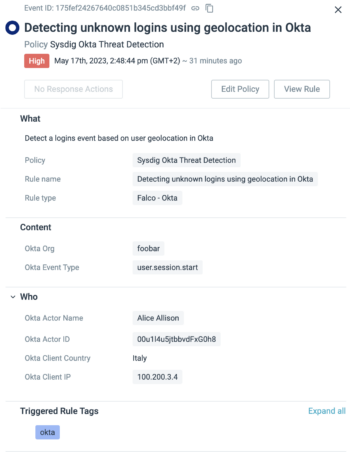
Software supply chain detection
With 61% of all container images pulled from public repositories, threat actors are trying to exploit these repositories as an attack vector. Sysdig’s GitHub detections extend threat detection into the software supply chain, alerting security and DevOps teams on common GitHub security risks, such as when a secret is pushed into a repository or a private repository becomes public.
Enhanced drift control
Sysdig’s Drift Control dynamically blocks executables that were added or modified after a container is deployed into production. By blocking container drift, you can prevent many common runtime attacks that run scripts or malware with embedded executables. Drift Control is a simple runtime security policy that can be quickly applied to the entire environment:
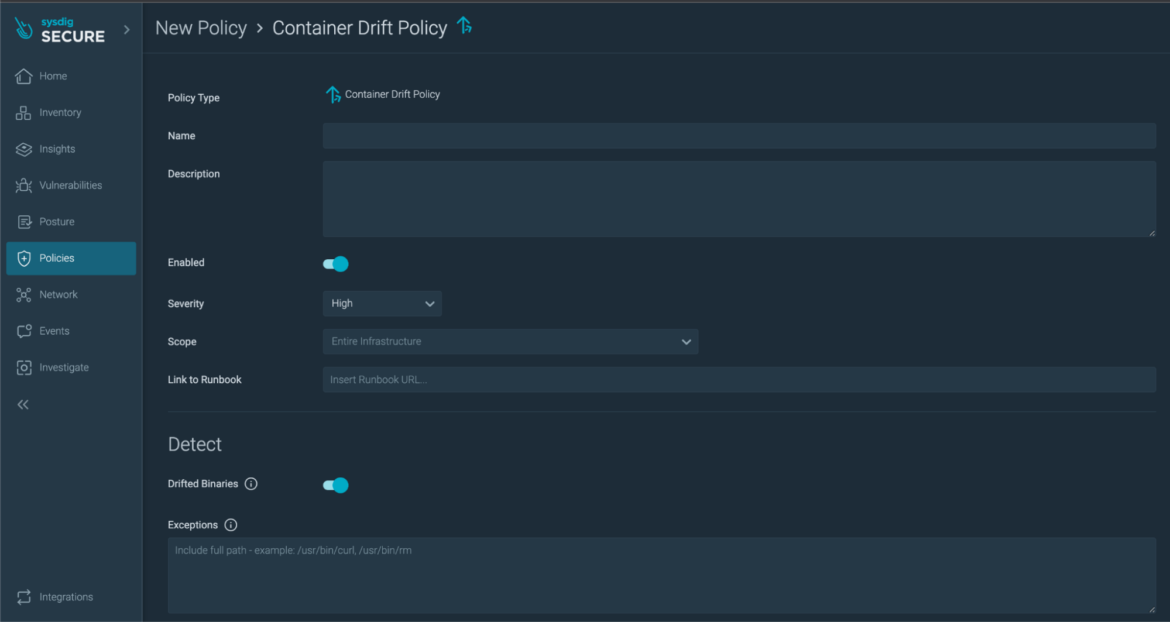
Speeding up incident response with live threat investigation
Sysdig CDR also offers advanced incident response capabilities that empower you to investigate and respond at cloud speed. The longer a malicious actor maintains access to your environment, the greater the potential for extensive damage. Furthermore, the cost associated with a data breach escalates as time elapses without proper response. Immediate response is crucial, but without proper context, understanding the threat and reacting swiftly becomes a challenge. With Sysdig CDR, you gain the insights necessary to take rapid and informed action.
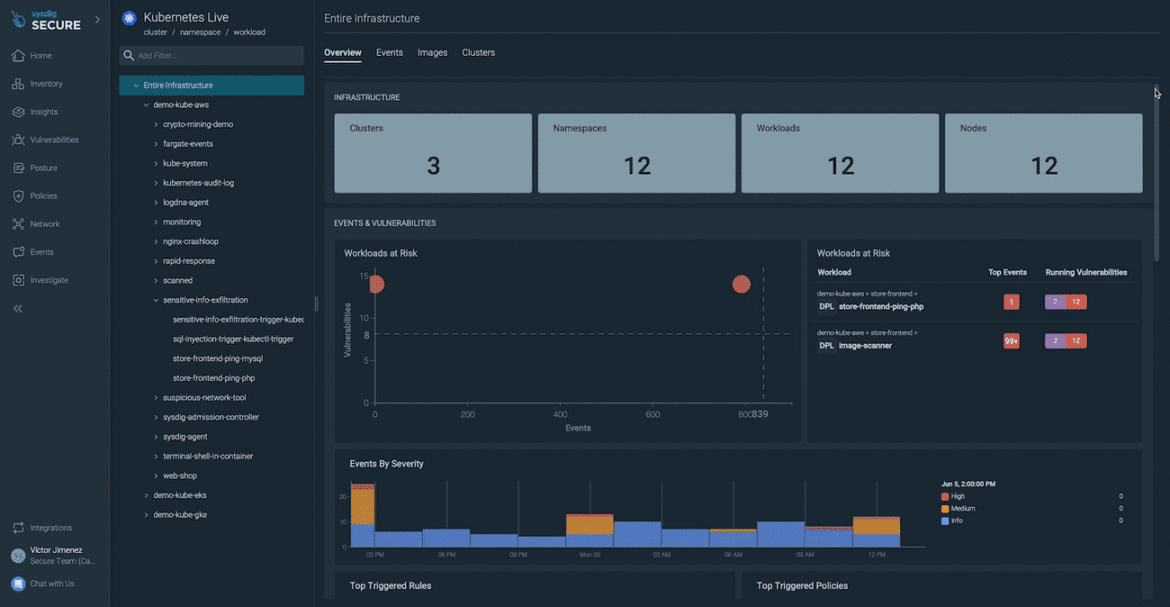
Live mapping
Kubernetes Live brings an EDR-like approach of assembling all relevant real-time events into one view when a breach occurs. This provides teams with a dynamic view of their live infrastructure and workloads, as well as the relationships between them. Equipped with understanding of all the vulnerable workloads, critical security events, and triggered runtime policies in your Kubernetes environment, you can speed incident response with enriched context. Learn more about Kubernetes Live in this blog.
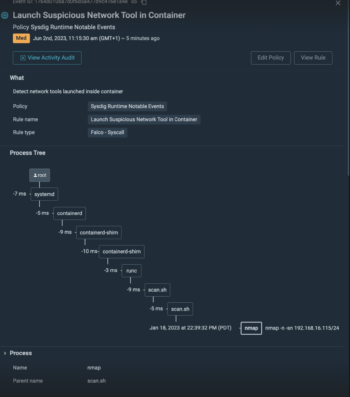
Attack lineage with context
Sysdig Process Tree unveils the attack journey from user to process. This includes the process lineage to show how a process was initiated, as well as key context like container and host information, malicious user details, and impact. With a full understanding of the relationships and dependencies between processes, you can identify which processes are malicious and act on them quickly. Learn more about Process Tree in this blog.
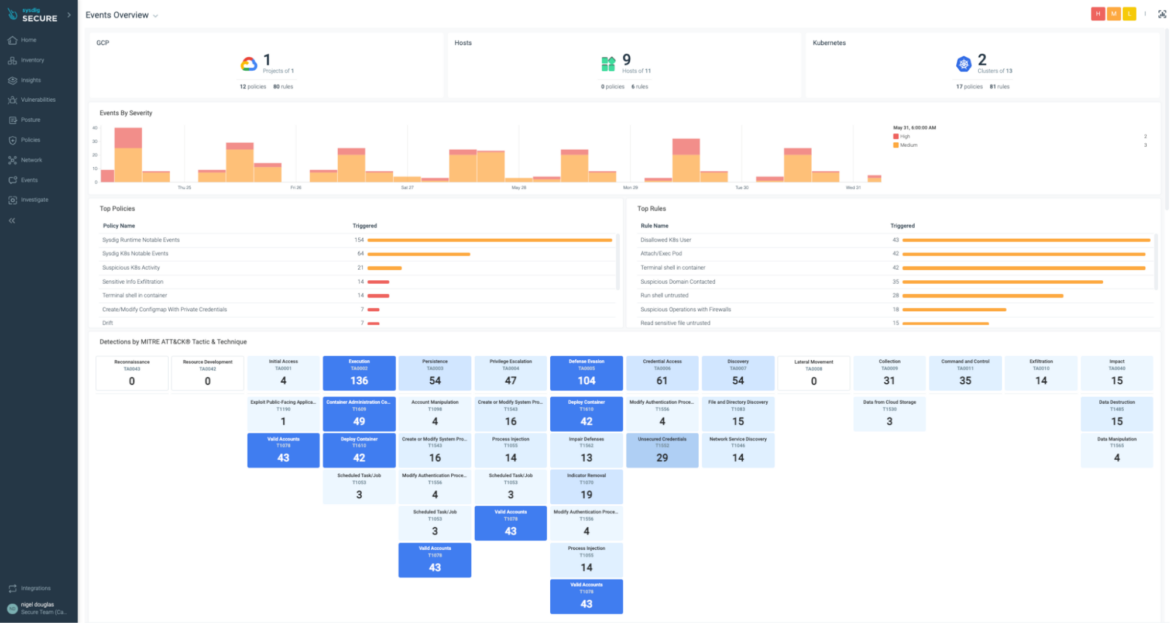
Curated threat dashboards
Sysdig’s threat dashboards spotlight events across clouds, containers, Kubernetes, and hosts, acting as a centralized view of critical security issues. Sysdig also provides dynamic mapping against the MITRE ATT&CK framework for cloud-native environments. Security teams can use this information to understand the full landscape of threats in their environment and prioritize response.
Key Benefits of Sysdig CDR
- Stop cloud breaches with real-time, end-to-end threat detection powered by Falco: Consolidate security with an approach combining Drift Control, Machine Learning, and Falco detections, all curated by Sysdig Threat Research.
- Accelerate cloud threat investigation and incident response in real time: Surface the context you need to understand the possible impact and respond quickly.
Sysdig is the first vendor to deliver the consolidation of CDR and CNAPP, leveraging the power of open source Falco in both agent and agentless deployment models. With Sysdig CDR, you can prevent advanced attacks and contain threats in real time across the cloud fabric.
If you want to learn more, sign up for one of our upcoming webinars or get a demo today.


