
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

The sixth annual Sysdig Cloud-Native Security and Usage Report digs into how Sysdig customers of all sizes and industries are using, securing, and paying for cloud and container environments. We examined the data and found some interesting trends that may help you as you work to develop best practices for securing and monitoring your cloud-native environments.
This year's report has new data on cloud security, container vulnerabilities, and Kubernetes cost optimization. Read on to see how you stack up!
How We Got Our Data
Because our software monitors cloud security, container security, and container usage, we have a unique view of how organizations are using cloud services, Kubernetes, registries, alerts, and applications in cloud-native environments. This real-world, real-time data provides insight into the usage of millions of containers that a subset of our customers are running every day, and billions of unique containers from the past year. The report includes a detailed look at security risks, cloud costs, and trends in container usage.
Let's take a look at some of this year's highlights. Download the full report for more.
Supply chain risk
Our research shows that 87% of container images have high or critical vulnerabilities. The reality is there are too many vulnerabilities to fix, and teams struggle with how to prioritize them. In fact, 85% of critical and high vulnerabilities have a fix available, but are not in use at runtime where they'd be exploitable.

Teams are wasting time and resources on vulnerabilities with no risk to their organization, and leaving high risk vulnerabilities unpatched. By focusing on what is exposed at runtime, teams can focus on the 15% of vulnerabilities that matter the most.
Overly-permissive access
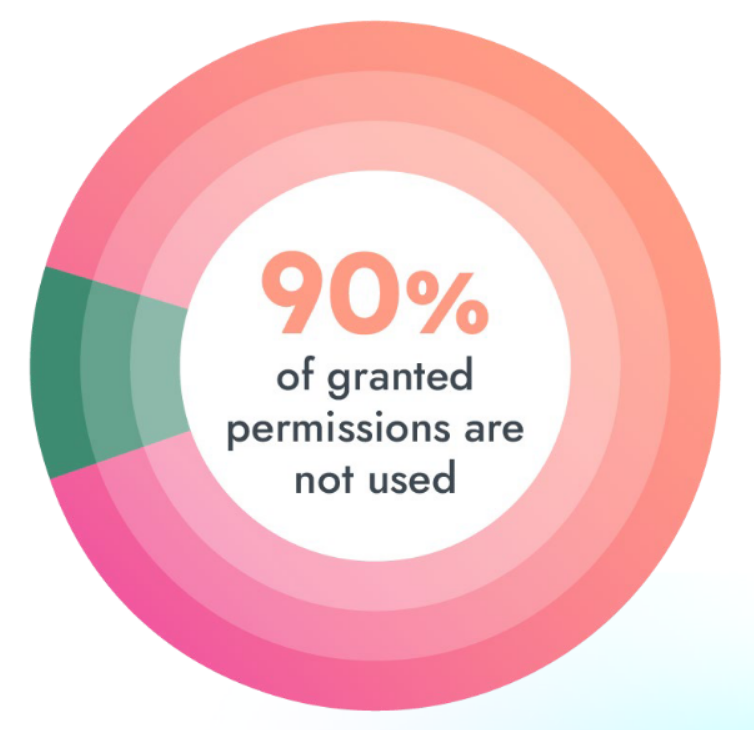
Cloud security best practices and zero trust architecture principles stress that organizations should avoid granting overly-permissive access. Yet, data from the report shows that 90% of permissions are unused. If attackers compromise credentials from identities with privileged access or excessive permissions, they have the keys to the kingdom in your cloud environment.
Cloud cost and unused capacity
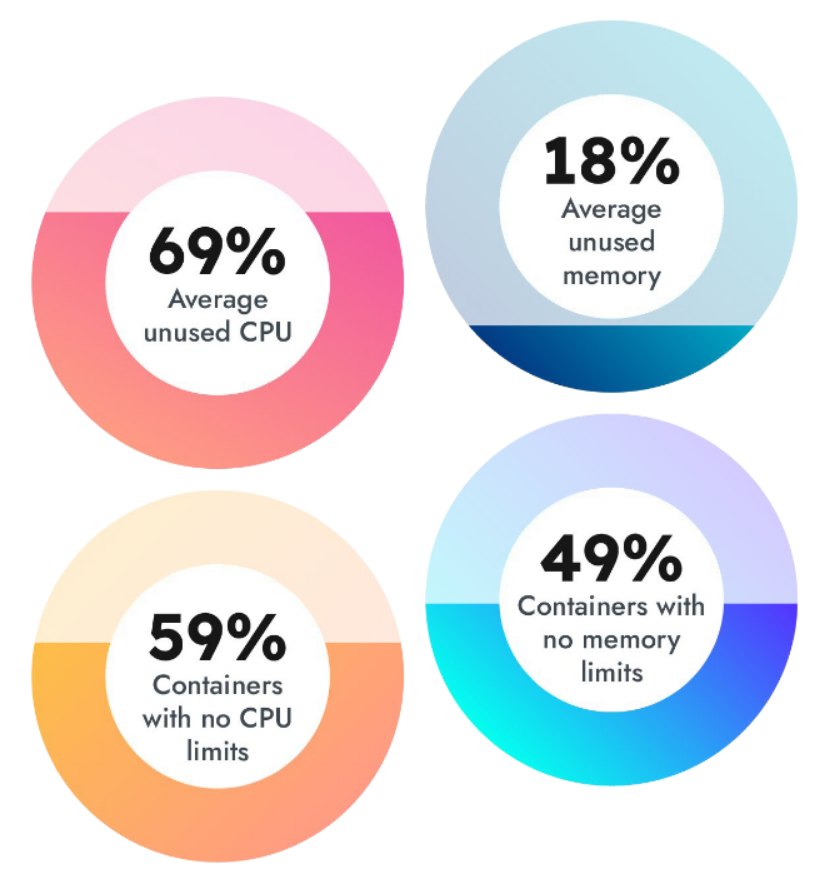
We found that 59% of containers have no CPU limits defined, and 69% of requested CPU resources are unused. Without utilization information for Kubernetes environments, developers are blind to where their cloud resources are over or underallocated. For large deployments, optimizing an environment can save an average of $10 million on cloud consumption bills. On average, organizations of all sizes could be overspending by 40%.
Increasingly short life of containers
This year's data shows that 72% of containers now live less than five minutes! Incident response and forensics teams need to have accurate records in case an event must be investigated after containers are gone. Engineering teams also need similar data for application and infrastructure troubleshooting. With containers lasting such a short period of time, gathering this information is increasingly difficult.
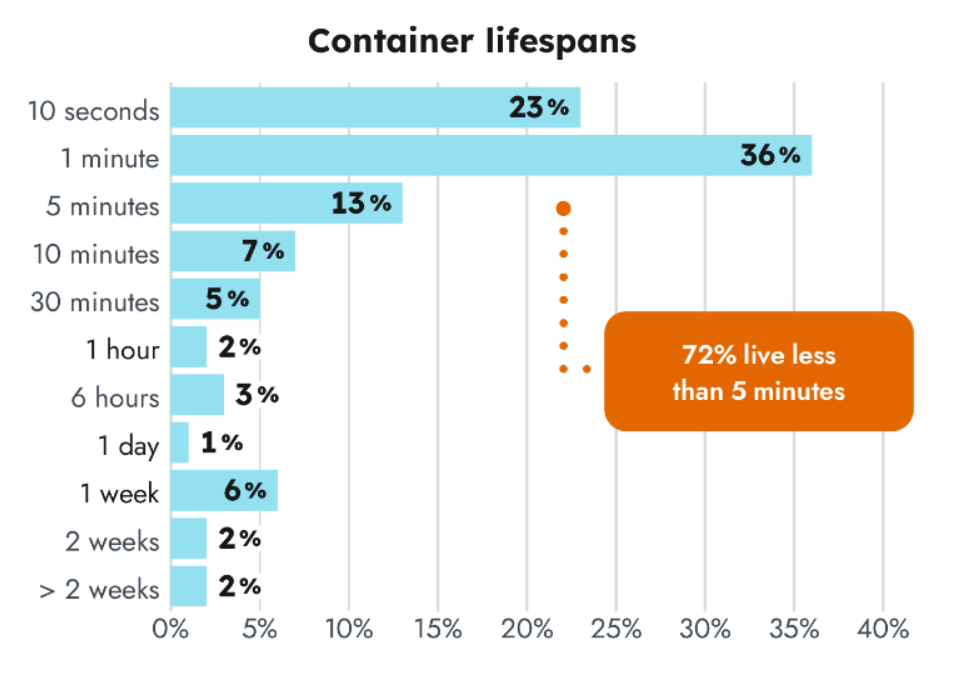
Last year, research showed that 44% of containers lived less than five minutes. This is a 28% increase year-over-year, which speaks to organizations maturing in their use of container orchestration.
Conclusion
Our research demonstrates that although there is awareness of required tools and the benefits of zero trust approaches, cloud security processes still lag behind the fast pace of cloud adoption. From the real-world customer data we examined, there are several security practice areas that require improvement to reduce risk:
- Identity and access management: The large disparity between permissions granted vs. permissions required highlights the urgent need to regularly measure and manage permissions to reduce opportunities for attack.
- Vulnerability management: With a majority of container images running with risky vulnerabilities in production, teams must address image bloat and focus their remediation efforts by prioritizing vulnerabilities based on real runtime risk.
- Detection and response: Privilege escalation and defense evasion attacks are top of the threat list for our customers. To stay ahead of the evolving threat landscape, threat detection rules should be regularly updated to spot nefarious activity.
Beyond security, this year's data demonstrates the opportunity for organizations to reduce cloud costs by addressing unused Kubernetes resources. Time invested in capacity planning can yield a strong return. By implementing proper container resource limits and continuous monitoring, organizations will be able to optimize costs without risking application performance.
Want more? Download the full Sysdig 2023 Container Security and Usage Report now for all the details. You can also find our past reports here.


