Cloud teams are increasingly adopting AWS container services to deliver applications faster at scale. Along with the roll out of cloud native architectures with containers and orchestration, what’s needed to stay on top of the security, performance and health of applications and infrastructure has shifted. At Sysdig, we’ve worked with Amazon to provide tools and integrations that help secure your Cloud Native workloads deployed across all AWS container services. In this blog, we’ll cover how Sysdig Secure DevOps help you embed security, maximize availability, and validate compliance across the container lifecycle on AWS.
Scanning for vulnerabilities pre-deployment on AWS
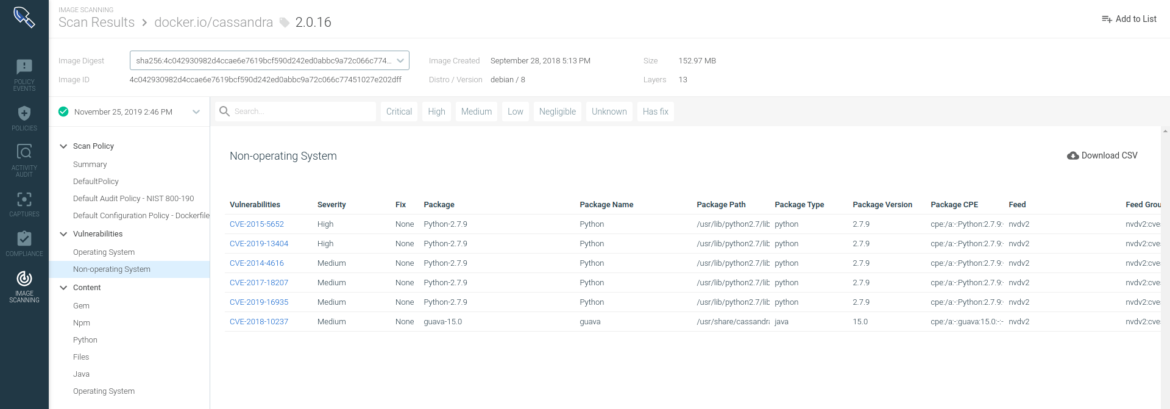
Sysdig Secure allows you to scan for vulnerabilities and misconfigurations before deployment. You will be able to catch vulnerabilities in base images, OS packages and 3rd party libraries like Python packages from PIP or Java JAR files that your developers might be pulling into their application images before they hit production.
When it comes to pre-deployment scanning, there are two typical approaches, and with Sysdig vulnerability management capabilities, you can take both: either perform image scanning from AWS ECR or implement image scanning on your AWS Code Pipelines.
Compliance and audit across AWS container deployments
Different options are available for deploying containers in AWS. You can opt into using ECS, setup Kubernetes on top of EC2 with kops or kubeadm, or you might want to use EKS, the fully managed Kubernetes service from Amazon.
Being able to validate that your deployment is compliant with security best practices like CIS benchmarks for Kubernetes or Docker is one of the first steps. But compliance requirements don’t end there. You must be able to implement compliance at various points:
- During build, mapping container image scanning policies to standards like NIST 800-190, PCI, HIPAA
- During runtime, using policies to continuously detect attack frameworks like MITRE ATt&CK or check compliance after deployment
- And finally, audit any changes in your container environments, which is part of SOC2, PCI, ISO and HIPAA requirements
Sysdig Secure allows you to validate compliance across the entire container lifecycle.
Block runtime threats on ECS, EKS, and Kubernetes on EC2
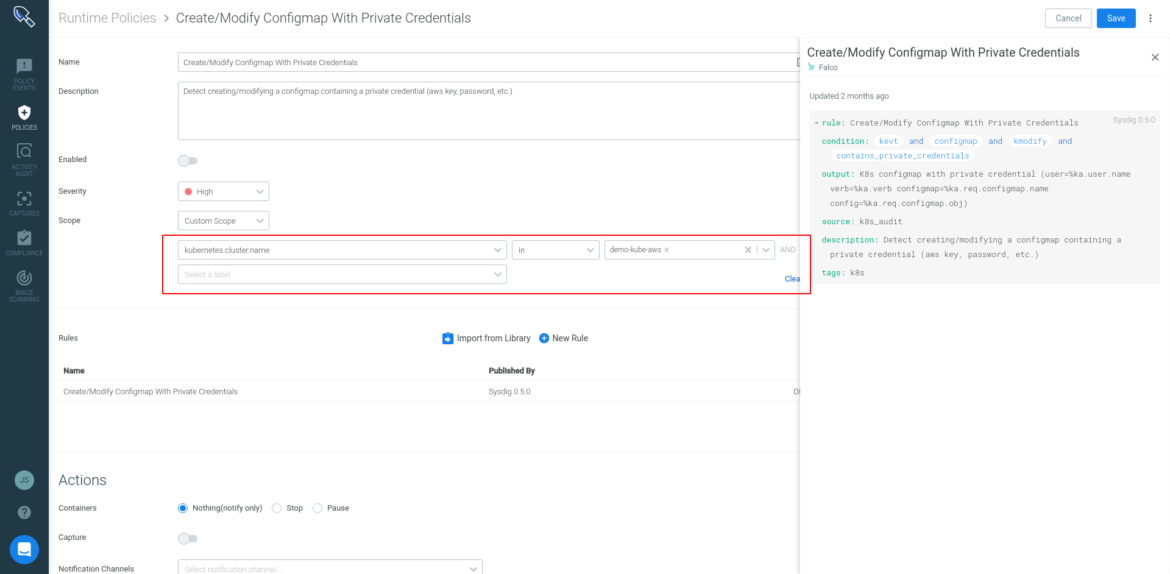
Once in production, it’s important to reduce risk by configuring applications with the minimum privilege and access permissions. At the same time, you need to be able to create and maintain a runtime policy that observes workload behavior and looks for anomalous activity, blocking any threats and attacks not caught in your CI/CD or registry scanning.
Sysdig Secure supports all AWS container services, including ECS and cloud instances on EC2, Kubernetes installed on EC2 and the managed EKS. Sysdig leverages the Falco open source detection engine to monitor anomalous activity on hosts and containers but will also ingest activity at the orchestration layer when using Kubernetes and the EKS managed service.
Read more about ingesting Kubernetes server API events from EKS here.
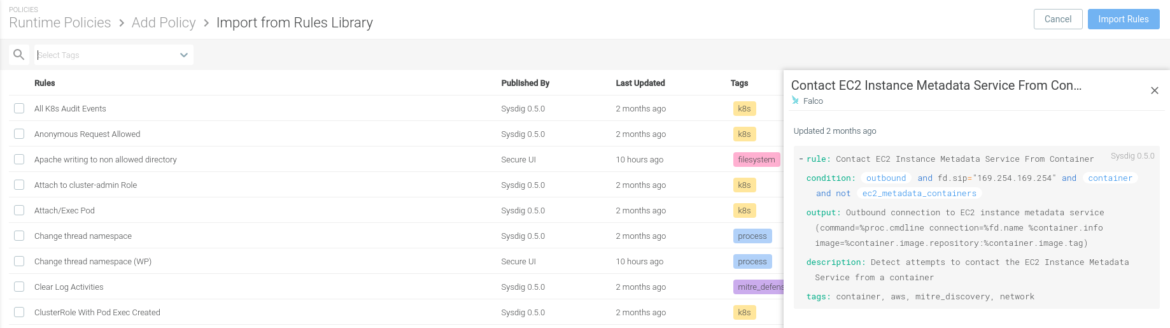
A large collection of out-of-the-box runtime policies available through the Sysdig Secure library allows easily implementing runtime security in the blink of an eye.
Sysdig profiling eases the burden of creating and maintaining your runtime security in large-scale environments, automatically building the policy for you. Sysdig’s approach analyzes and learns container behavior to enhance anomaly detection and block threats before they propagate any further.
Sysdig Secure leverages Kubernetes-native controls like PSP for enforcement. You can read more about it on Pod Security Policies in production with Sysdig’s Kubernetes Policy Advisor and learn about Sysdig runtime security capabilities here.
Monitoring performance, capacity and security on AWS
DevOps teams sit at a crossroads: they need to take care of monitoring but now also for the security of containers and Kubernetes. Unifying monitoring and security visibility, tooling, and workflows can maximize the reliability of your operations.
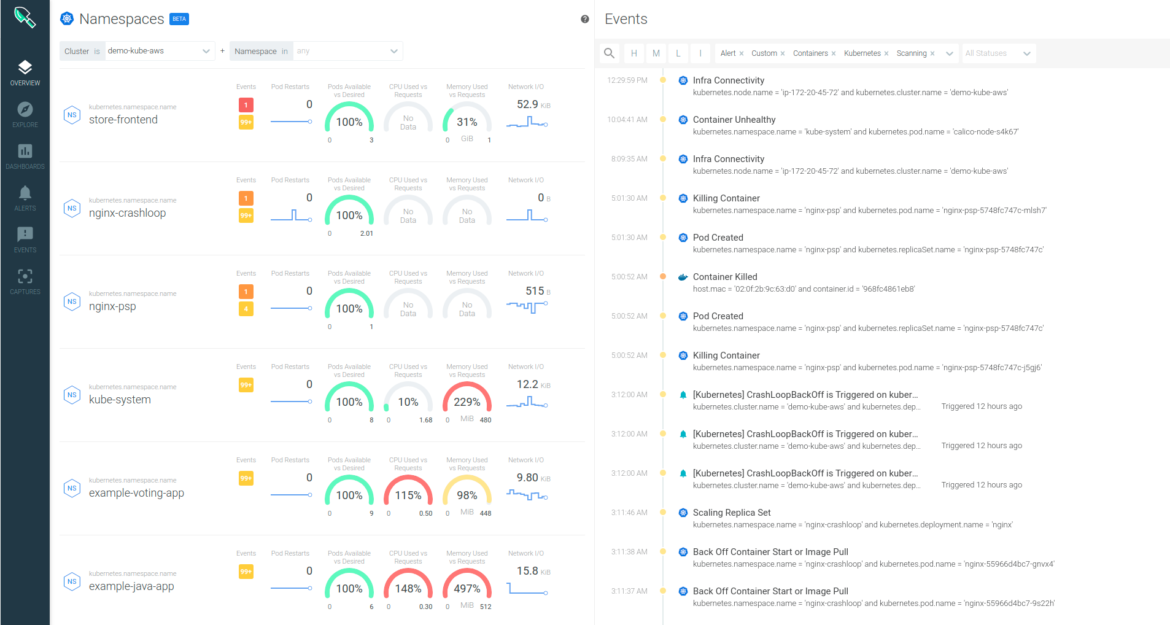
In an environment when you combine different workloads like self-hosted applications on Kubernetes that consume data from hosted AWS services, it is important to have a single source of truth. Sysdig can bring together infrastructure metrics, your application metrics and other metrics from AWS services using CloudWatch, including EC2, ECS, RDS, SQS, DynamoDB or Elasticache and App Mesh.
Read more on Visibility and monitoring App Mesh with Sysdig, Sysdig docs on CloudWatch, and Amazon EKS monitoring and security with Sysdig.
Responding to incidents and forensics on ECS and EKS
When troubleshooting an issue or performing a post-mortem analysis of a security incident, one of the typical challenges is that when a container is destroyed all the relevant information is gone.
In Kubernetes and ECS this happens all the time. Containers can be moved between nodes and services are scaled up and down, deleting container instances. You need to be able to recognize whether the issue comes from malicious activity or a misconfiguration of the app.
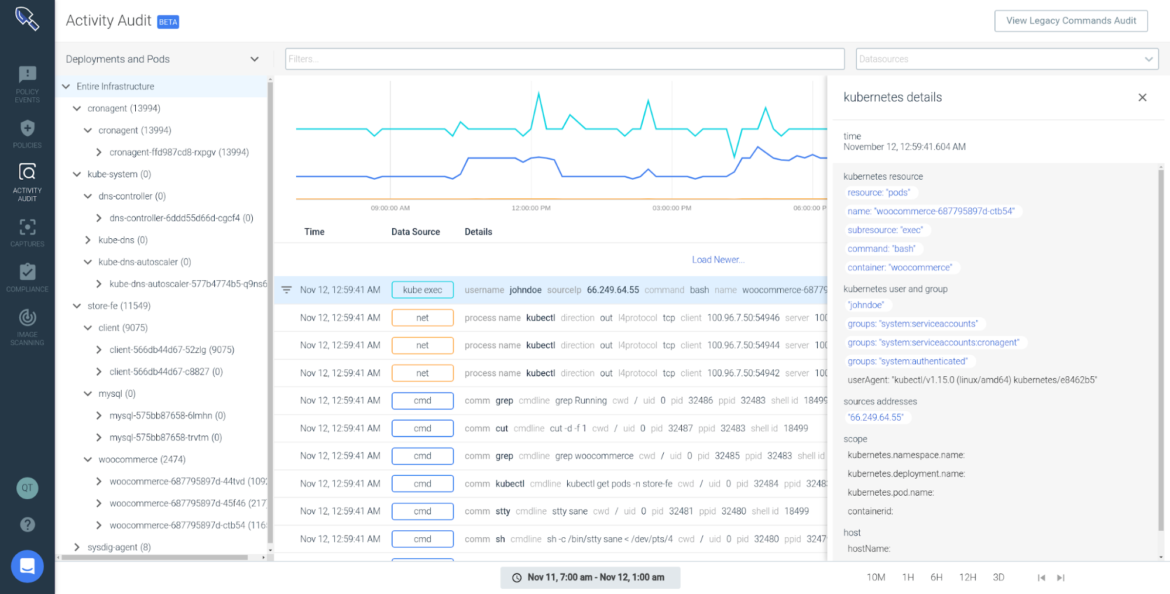
Sysdig’s Activity Audit speeds incident response and enables audit for Kubernetes. Sysdig captures and correlates executed commands, network, and Kubernetes activity so SOC teams can spot what happened. With Sysdig captures, you can also record all container activity at a detailed level, including spawned processes, network connections, file system activity, etc., so you can understand events in detail, and conduct Kubernetes forensics even after the container is long gone.
Read more about this on Incident response in Kubernetes with Sysdig’s Activity Audit.
Sysdig will deliver notifications to your alerting channels, AWS SNS or SIEM, integrating also with AWS Security Hub. This allows you to consolidate security findings across your container environments so you can view and manage security alerts, and automate compliance checks across your AWS account. Both Sysdig Secure and Falco send events to Cloudwatch through Firelens as seen on Multi-cluster security with Falco and AWS Firelens on EKS & ECS.
Conclusions
The Sysdig Secure DevOps Platform allows DevOps and Cloud teams running container workloads on AWS container services to embed security into their workflows, get visibility into availability, monitor their containers, and implement compliance requirements.
All of these integrations are supported by Sysdig as an AWS Advanced Partner. And, if you are looking for solutions in this area, we’ve made it easy for you to sign-up for a trial, purchase and install Sysdig from AWS Marketplace.
We’d love to hear how you’re using AWS services and talk with you about how we can help you confidently run cloud-native workloads in production. If you’re in Las Vegas for AWS re:Invent, stop by and see us at booth #3813 or set up a meeting in advance.