Google Cloud is helping businesses build and deploy apps faster than ever before, but at the same time, cloud and security teams must consider how to implement security best practices to stay ahead of threats and avoid risk. Sysdig collaborates with Google Cloud to equip cloud and security teams with the solutions necessary to be secure without slowing down innovation.
Sysdig unifies cloud security capabilities from prevention to defense with our Cloud Native Application Protection Platform (CNAPP). Live visibility and correlation of signals across cloud workloads, identities, and services help uncover hidden attack paths and threats. This article provides details on what’s available to help you be more secure and how you can tackle the challenges of security for containers, Kubernetes, and cloud services on Google Cloud.
Google Cloud Security & Runtime Insights
Sysdig provides real-time cloud-native security for Google Cloud. This includes securing cloud and container services such as Google Kubernetes Engine (GKE), GKE Autopilot, Anthos, Google Cloud Run, Google Cloud Build, and GCR. What’s more, Sysdig integrates with Google Chronicle and Security Command Center to help you centralize security data and better manage your entire security posture.
In the cloud, every second counts. Security in the cloud is fundamentally different than it was with legacy and on‑premises systems. It requires new knowledge to navigate and new solutions to detect and respond at cloud speed.
At Sysdig, we harness the power of runtime insights to effectively prioritize risks, blending real-time contextual data, including in-use vulnerabilities and permissions, with static assessments, encompassing misconfigurations and known vulnerabilities. Runtime insights empower you to keep pace with the speed and sophistication of cloud attacks and scale your cybersecurity.
Preparing for Cloud & Container Threats
Protecting your cloud infrastructure and workloads from mishaps and attacks is not a one-size-fits-all proposition. There is a wide range of tactics and techniques employed today by threat actors. Beyond malicious activity, you can also face risk from the actions of well-meaning employees who simply don’t know to follow best practices.
Your best defence is to ensure you’ve buttoned down your detection and security practices from development through production. By working with Google Cloud, Sysdig is helping Security teams, Incident and Response teams, Compliance professionals and DevOps teams follow cloud security best practices to meet their organizational goals.
Identifying Active Cloud Risk on GCP
Threat detection for Google Cloud requires visibility into all of your cloud services, GKE, Anthos, containers and more. There is a lot to secure! App delivery requires a number of elements, including hosts, virtual machines, containers, clusters, stored information, and input/output data streams. How can you ensure you are properly securing it all?
The good news is that Google Cloud takes responsibility for the security and maintenance of its cloud services. This goes a long way to ensuring you can operate confidently in the cloud. However, the reality is that you, as a user, also must put the right protections in place.
By pairing the Sysdig cloud security capabilities announced today with our container security features, you’ll be able to more effectively follow security best practices for your Google Cloud accounts, apps, and services.
Cloud Security Posture Management & Compliance
To help you keep up with your use of Google Cloud services, Sysdig posture management enables you to perform static configuration analysis of your cloud infrastructure based on benchmarks like CIS. This helps you see where things are misconfigured. Plus, we provide guided remediation steps within the user interface to help you take action to achieve compliance.
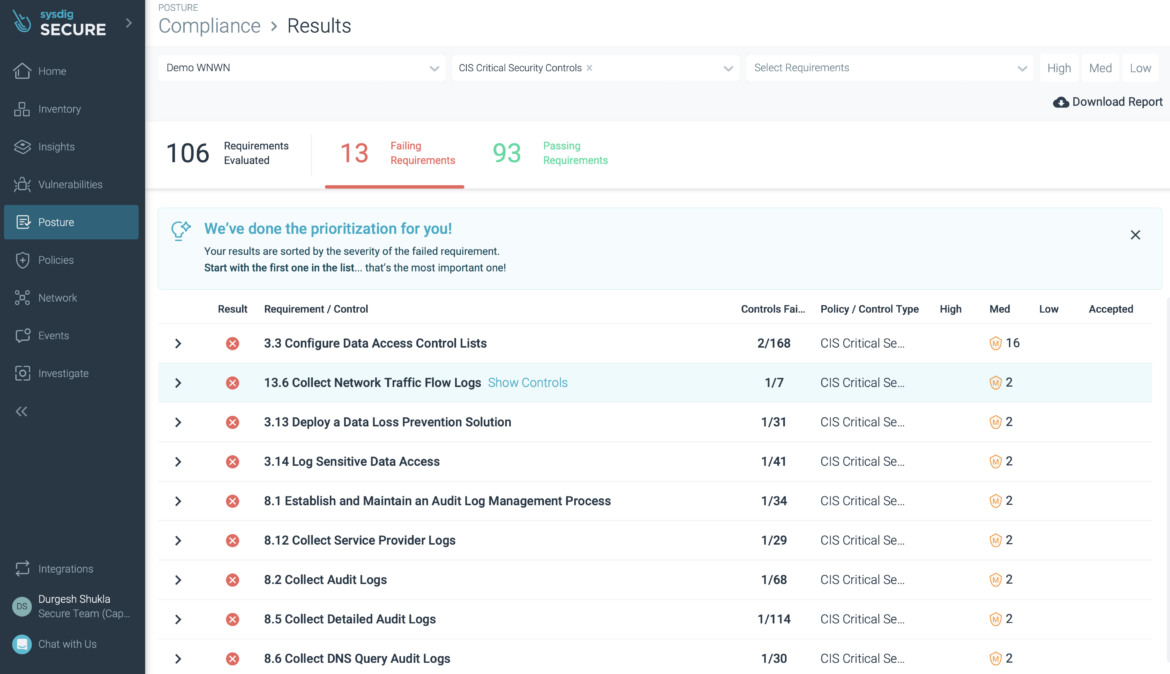
By checking the configuration of your environment, you will know if your IAM policies are secure, see what cloud storage buckets in your account are exposed to the public, and understand things like which VPCs allow ingress traffic, etc.
Cloud Detection & Response with Google Cloud Audit Logs
As your use of Google Cloud services grows, the amount of activity can reach a point where manual analysis isn’t manageable. Failure to react to a threat in a short time can have major consequences.
Google Cloud Audit Logs provide an always-on audit trail for Google Cloud that records both administrative events and user access to your cloud data. Sysdig performs threat detection for Google Cloud by analyzing this log data against a rich set of security rules based on open source Falco. This provides real-time analysis of activity so you can respond to threats faster.
Sysdig provides out-of-the-box rules to help you secure your environment. This includes, for example:
- Command Executed on Unused Region
- Operation by a Non-Corporate Account
- Invitation Sent to Non-Corporate Account
- Super Admin Executing Command
- Suspected Disable of OS Login in a VM Instance
- Shield Disabled for a VM Instance
- Create or Delete Bucket
- Create Cloud Function Not Using Latest Runtime
- Create or Patch DNS Zone without DNSSEC
- Disable Subnet Flow Logs
- Update, Disable, or Delete Sink
- Enable Project-wide SSH keys for a VM Instance
- Enable Connecting to Serial Ports for a VM Instance
- Fast startup: Get up and running in minutes and plug into your DevOps tools (i.e., embed scanning in CI/CD pipelines).
- Easy-to-scale: Monitor and secure a few images or cloud services, and scale up as your footprint grows without worrying about backend data management.
- No infrastructure costs: Avoid paying for in-house hardware and software licenses with perpetual ownership to run security and monitoring.
- Simple maintenance: Remove the overhead of maintenance and support. Sysdig handles rollouts of new SaaS feature updates and patches without disruption.
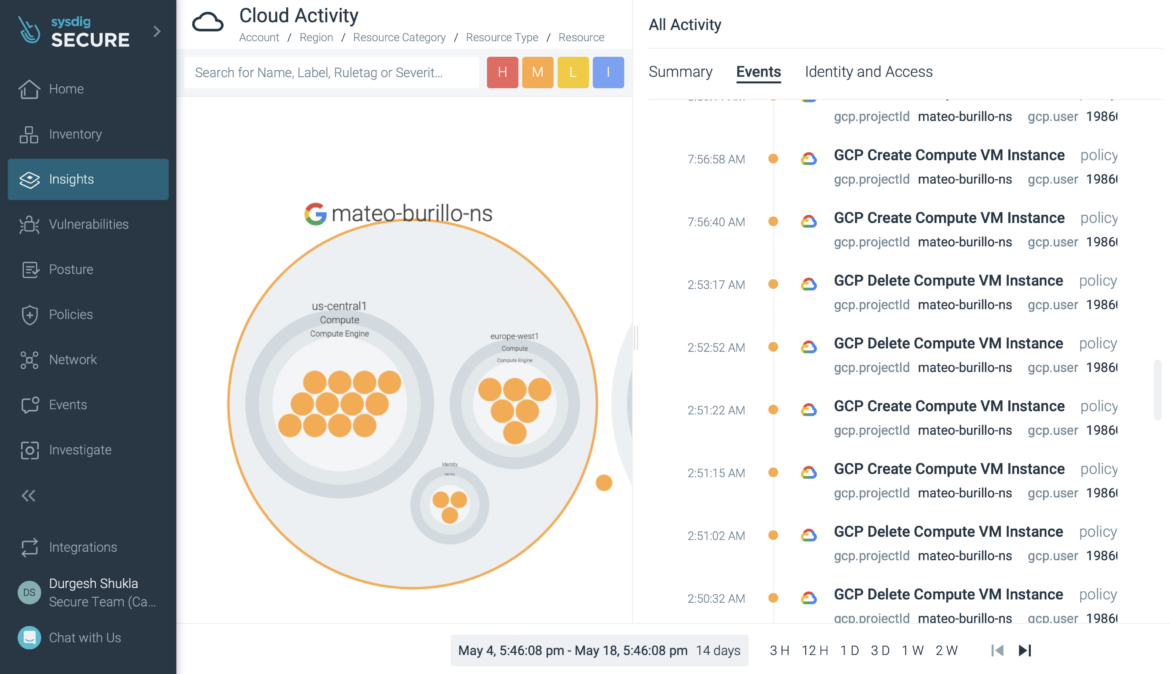
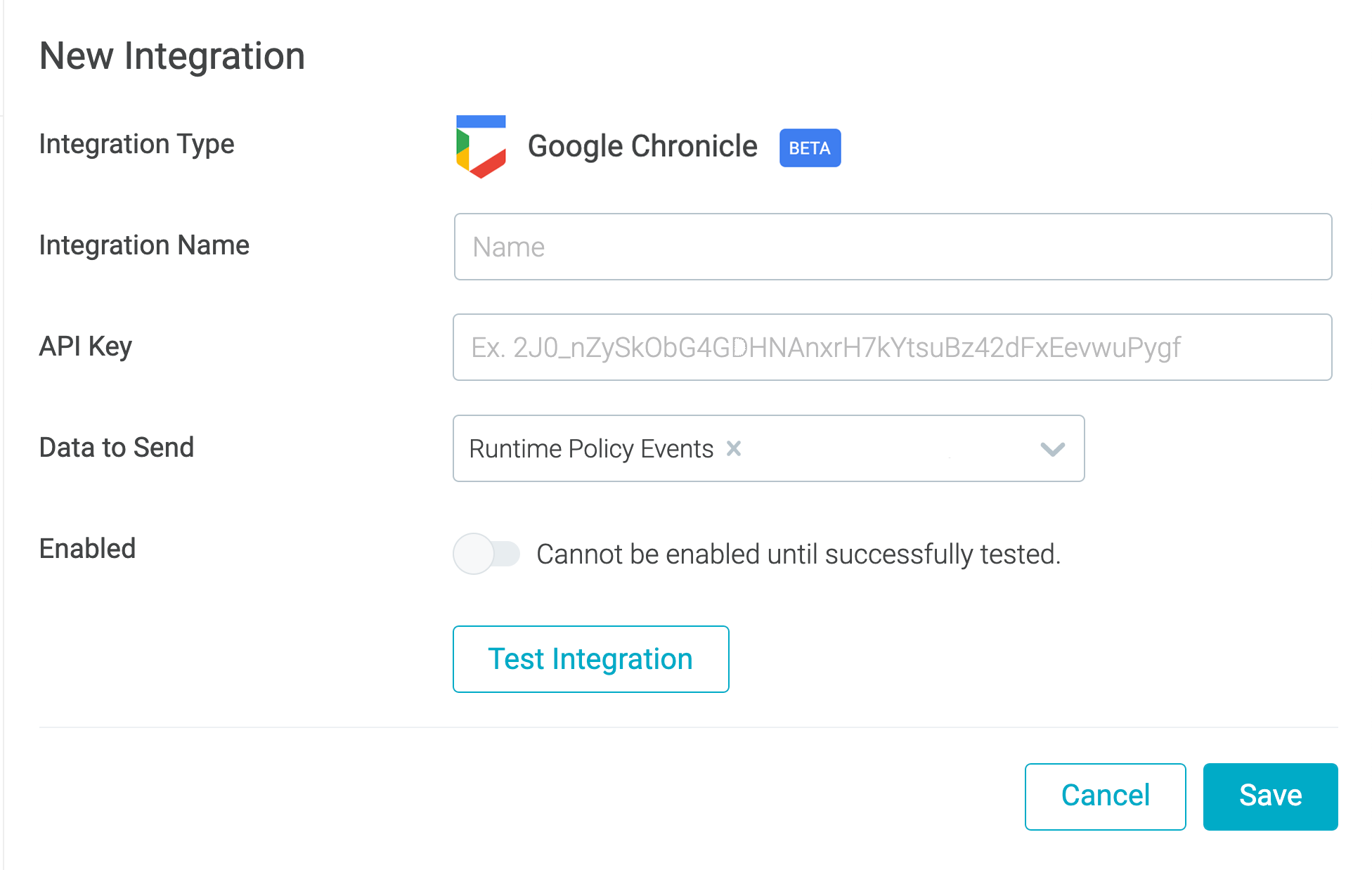
Enabling advanced threat hunting with Google Cloud’s Chronicle
Sysdig supports sending different types of security data to third-party SIEM platforms, data lakes, logging platforms, and SOAR solutions. Sysdig extends this capability to deliver security insights and events to Google Cloud’s security and risk management platform, Security Command Center. Now, you also can leverage this event forwarding capability to send Sysdig-detected security events directly to Google Cloud’s Chronicle security analytics platform.
The Chronicle cloud service enables you to privately retain, analyze, and search massive amounts of security and network telemetry data. Chronicle normalizes, indexes, correlates, and analyzes data to provide instant analysis and context on risky activity.
With this integration, you can extend Chronicle’s capabilities with the unique data available from Sysdig. This includes Kubernetes security, container, and process-level events. Incorporating this event information helps you perform advanced threat hunting and security analytics to reduce mean time to detect (MTTD) and accelerate response for your cloud-native workloads.
Sysdig SaaS on Google Cloud
To meet the demands of dynamic cloud-native environments, visibility and security solutions are increasingly moving to the cloud. Cloud-based software-as-a-service (SaaS) enables enterprises to break free from hardware dependency and instantiate services wherever required. Sysdig SaaS is available on Google Cloud to help users get started quickly and grow without worrying about backend data management.
Sysdig SaaS has many benefits:
The Sysdig CNAPP platform is also available on Google Cloud Marketplace. This means you can purchase and get started right from Google Cloud.
Conclusion
We’re excited to partner with Google Cloud in helping our joint users more effectively secure their cloud services and containers.
We are constantly hard at work deliver visibility, security, and compliance solutions for Google Cloud. This includes exploring things like GenAI to simplify cloud security operations. Keep coming back to see new updates throughout the year (or feel free to sign up for news below).
Having a single view across cloud, workloads, and containers will help you speed the time it takes to detect and respond to attacks. For a deeper look at best practices for Google Cloud security, check out the blog GCP Security Best Practices to Adopt in Production.


