
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

In its mission to simplify building and running cloud-native applications for users, Amazon has announced the GA of AWS App Runner, a new purpose-built container application service.
With security top of mind for most organizations shifting to the cloud, Sysdig has collaborated with AWS to enable threat detection for the new platform.
In this article, we'll describe how App Runner is different from other AWS container services, and show how to Secure App Runner workloads with Sysdig and Falco.
AWS App Runner – secure compute with no infrastructure overhead
With App Runner, there are no servers, container orchestrators, or infrastructure to manage. You simply deliver your source code, container image, or deployment pipeline, and App Runner automatically builds and deploys the container image. App Runner also sets up and manages load balancing, delivers encryption, and scales up or down based on incoming request traffic. This means you can build and run your containerized web applications, mobile backends, and API services in just a few clicks, with no prior AWS expertise or experience required.
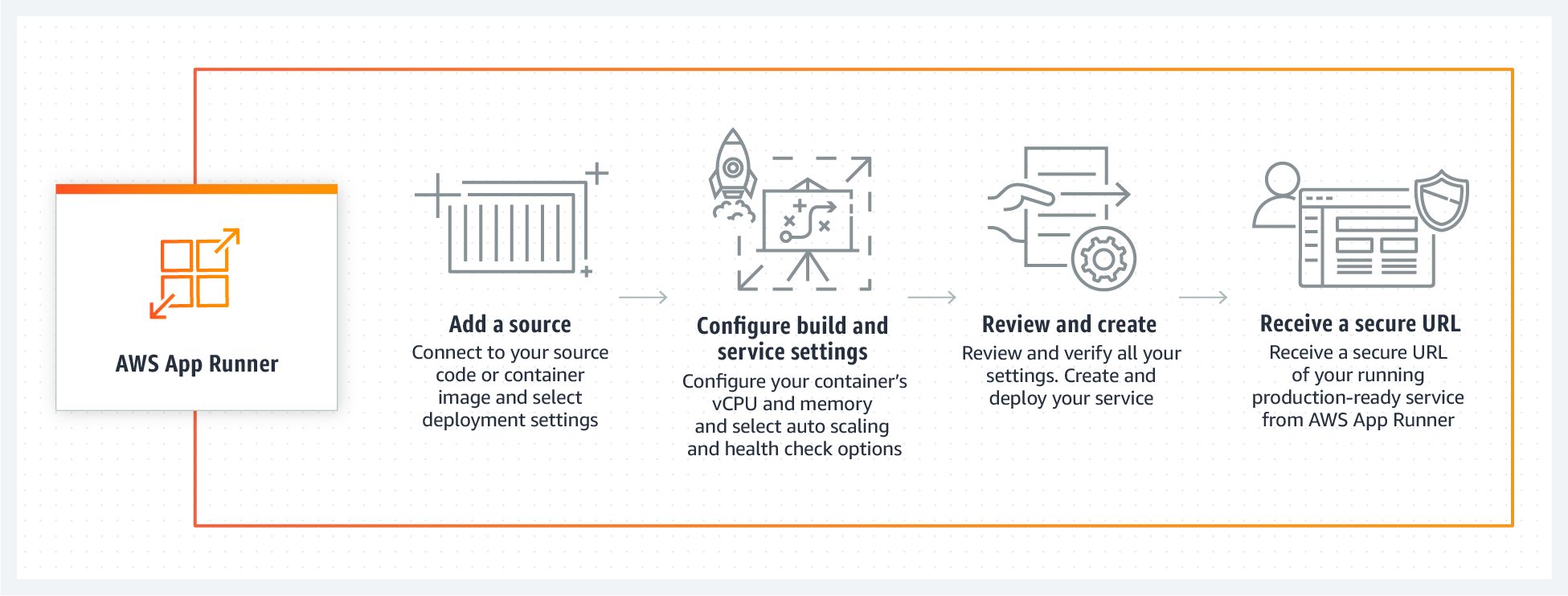
To deploy your new application, App Runner offers the possibility to build from source, pulling from a specified code repository, or to deploy an existing image from a public or private image repository.
In either case, after the usual configuration steps, which include defining runtime and auto-scaling parameters, environment variables, allocated virtual CPU and memory, and more, your new service will be up and running in no time.
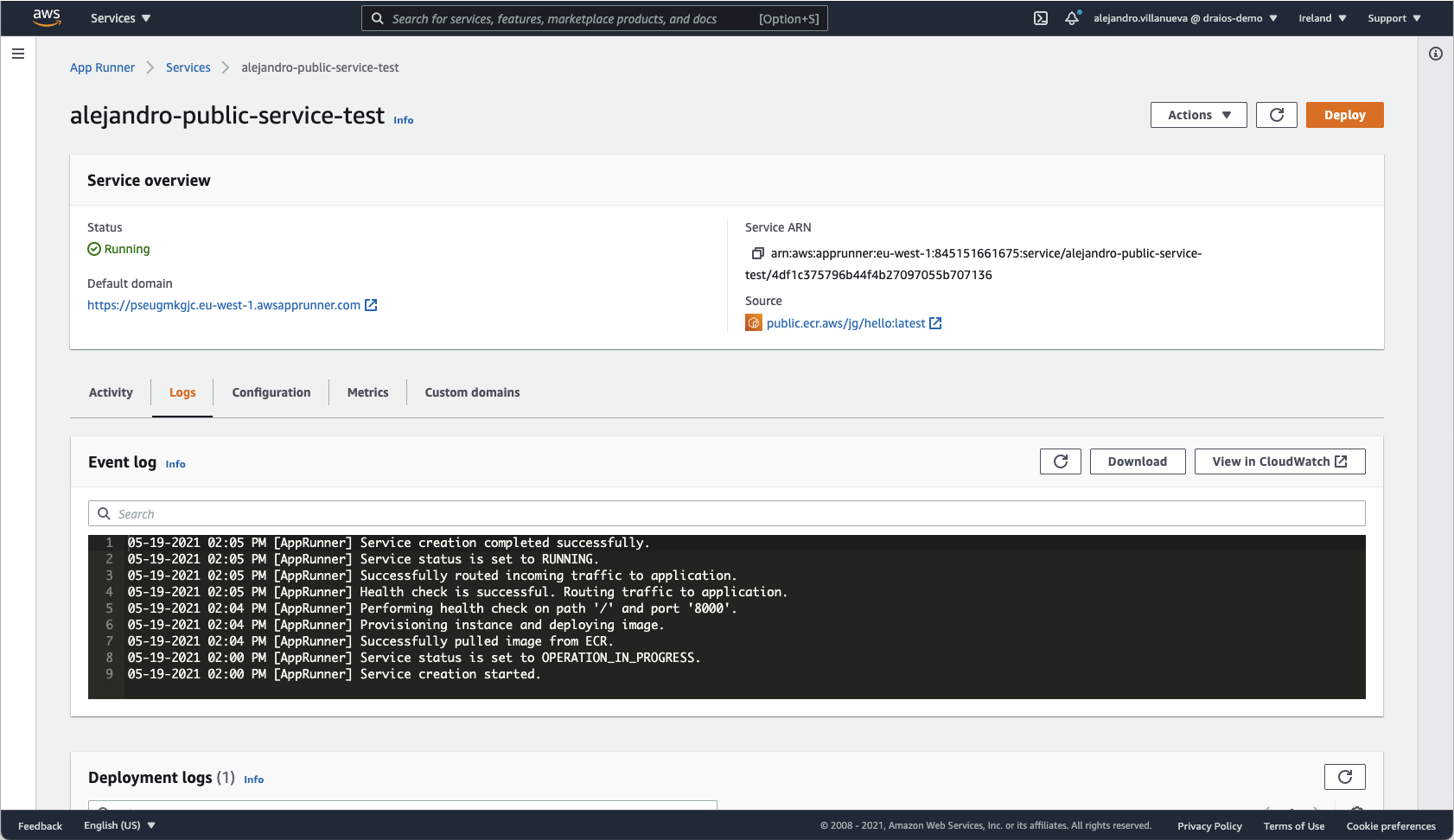
Visibility and Security for AWS App Runner
To secure workloads, visibility into cloud and container activity is needed in order to identify unexpected, unwanted, and malicious events. One of the ways Sysdig provides insight to serve this mission is to tap into AWS CloudTrail logs to look for and alert on anomalies across your in-use cloud services, and to scan the pulled images for known vulnerabilities.
Let's look at an example of how this works with Sysdig Secure. Below, you see an example of a policy triggered due to "App Runner Service Created." This is based on one of the Falco open-source rules built into the out-of-the-box Sysdig Secure runtime policy.
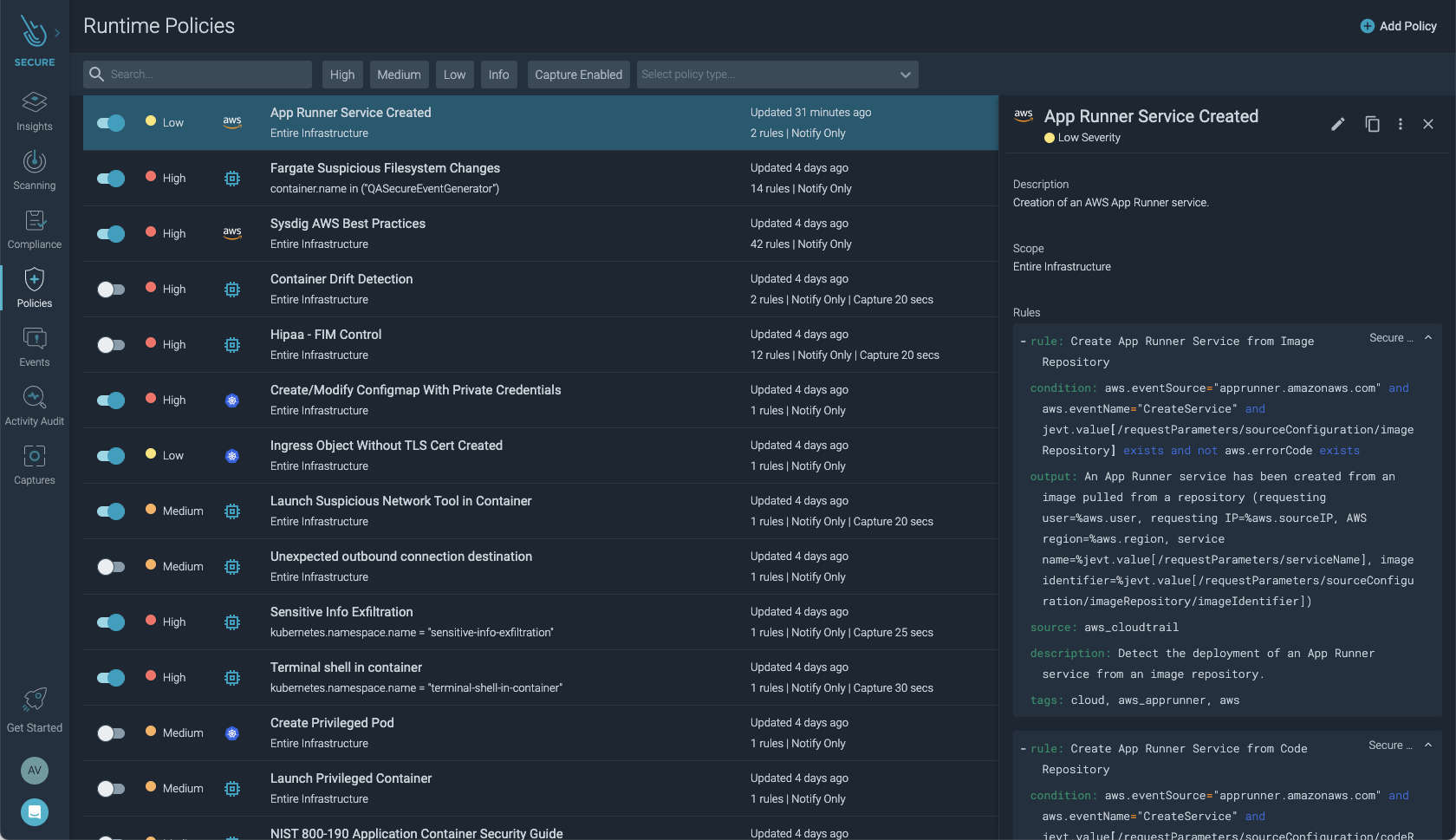
This policy contains rules for detecting that a new App Runner service has been created. In this case, the rule that triggered the policy was Create App Runner Service from Image.
The actual Falco rule looks like this:
- rule: Create App Runner Service from Image Repository
desc: Detect the deployment of an App Runner service from an image repository.
condition:
aws.eventSource="apprunner.amazonaws.com" and
aws.eventName="CreateService" and
jevt.value[/requestParameters/sourceConfiguration/imageRepository] exists and
not aws.errorCode exists
output:
An App Runner service has been created from an image pulled from a repository
(requesting user=%aws.user,
requesting IP=%aws.sourceIP,
AWS region=%aws.region,
service name=%jevt.value[/requestParameters/serviceName],
image identifier=%jevt.value[/requestParameters/sourceConfiguration/imageRepository/imageIdentifier])
priority: NOTICE
tags:
- cloud
- aws
- aws_apprunner
source: aws_cloudtrailDigging deeper into the issue
Let's take a closer look at the information provided in the alert:
aws.accountId 845151661675
aws.eventId ee1a60aa-c013-4643-9597-8334549606d3
aws.region eu-west-1
aws.requestId 5753033d-baf6-44f9-b8d6-903b34f1b863
aws.sourceIP 90.167.195.62
aws.user alejandro.villanueva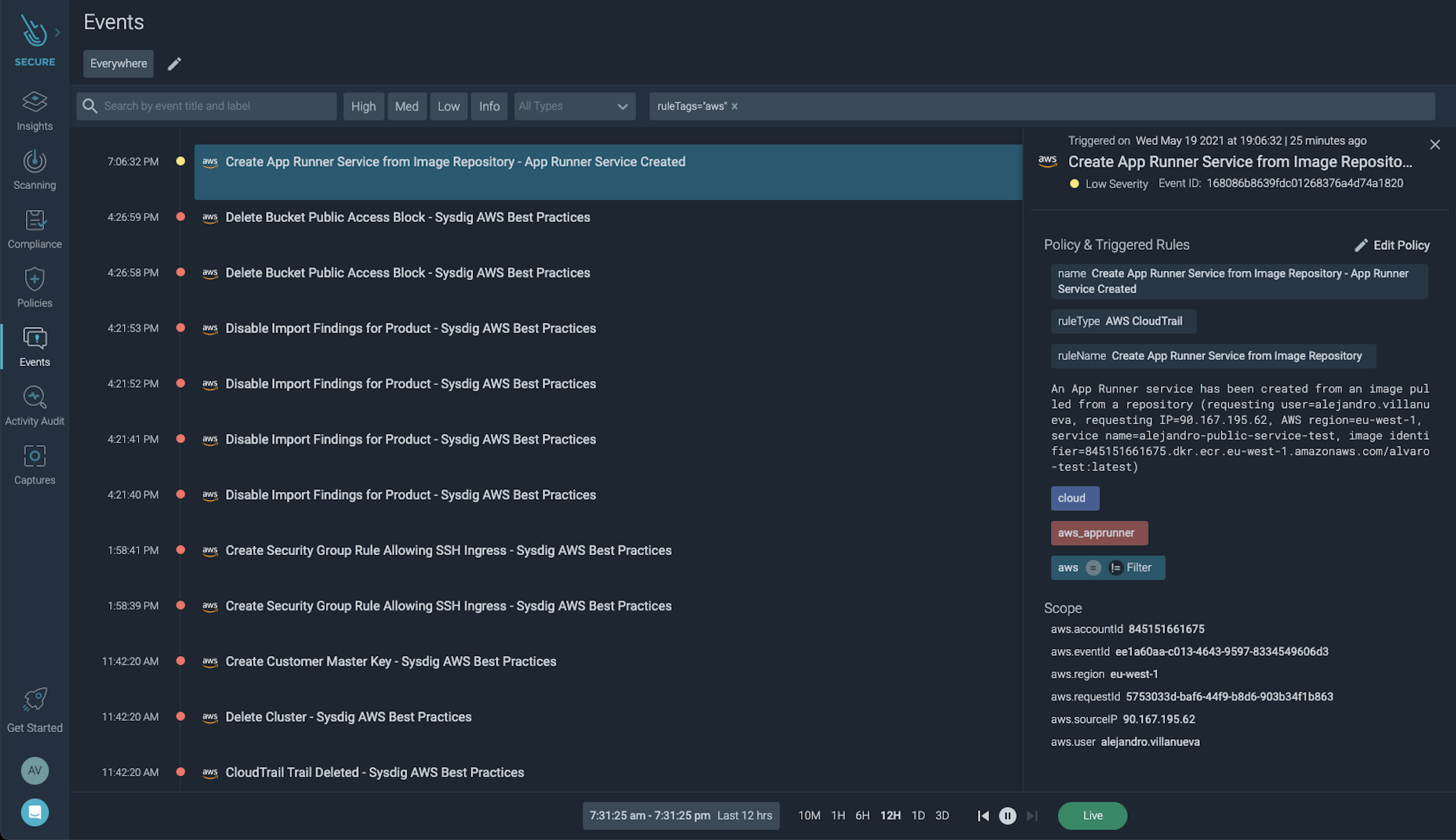
You can see that a new service has been created, in which AWS account it is in, in addition to the user that has created it and from which IP address.
Not only do we get this information, but upon creation of an App Runner service from an image repository, an image scanning is automatically triggered to check for known vulnerabilities.
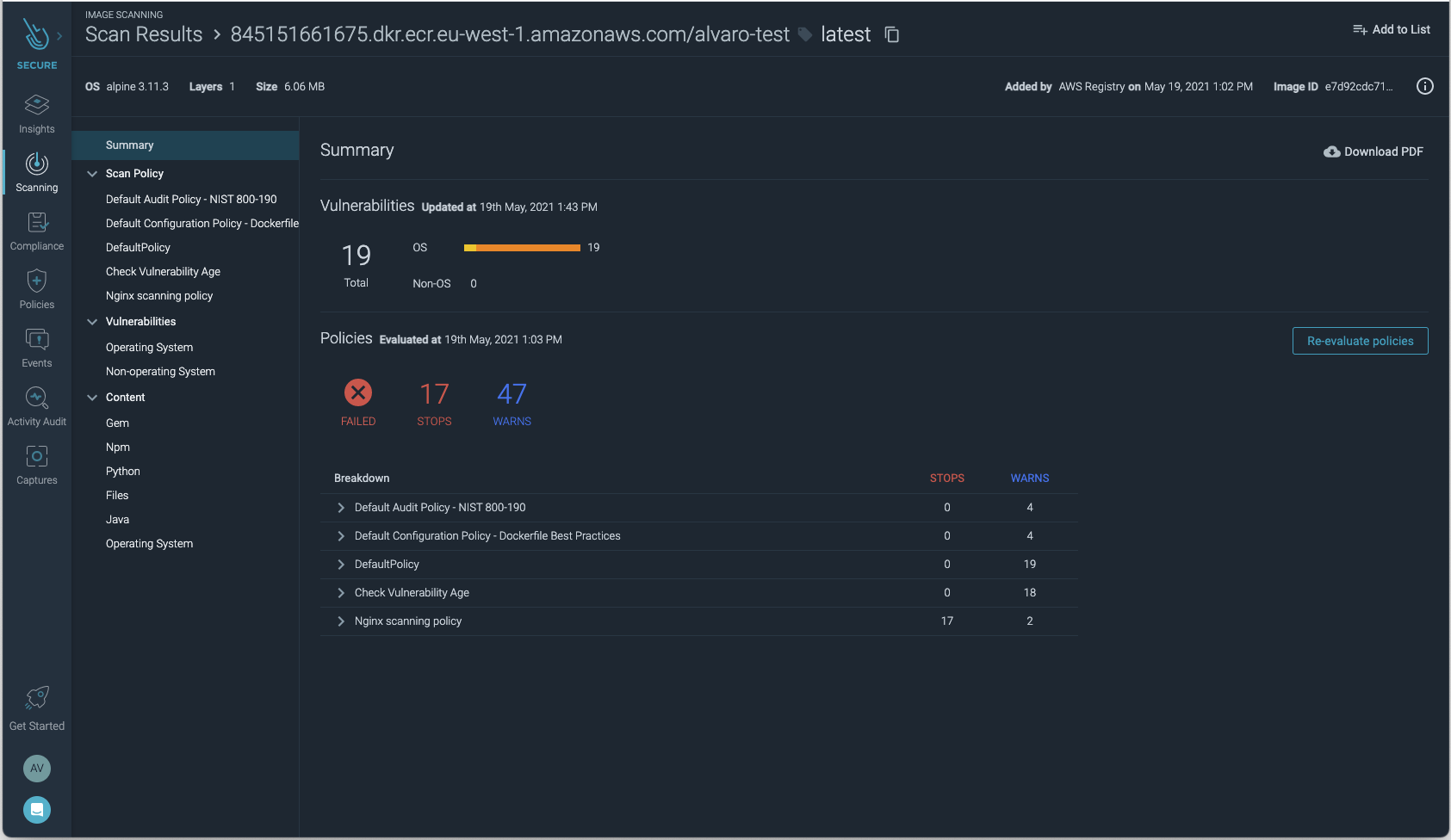
As we can see from the scan results, the deployed image has failed with several OS vulnerabilities. This is an invaluable tool that we can use to audit the security of AWS App Runner services.
Completing the picture with Cloud Activity Insights
The information provided by Sysdig Secure and Falco is already valuable to help investigate the issue and take steps to prevent it in the future. What is often also helpful is to see what other cloud activity was taking place concurrent with the security incident, and to check for configuration issues that might have contributed to the compromise.
As announced recently, Sysdig Secure now incorporates threat detection for cloud infrastructure and also performs checks to identify cloud misconfigurations. You can take advantage of this cloud security posture management (CSPM) information for AWS Cloud to speed up your security investigation.
Cloud Activity Insights in Sysdig Secure display cloud activity events that are in violation of best practices and your established policies. For instance, you can see if at the time of the event noted in the above example, other suspect cloud activities were taking place, such as CloudWatch Delete Alarms. You can also quickly understand if a user has created a security group rule allowing SSH ingress, or if you have had cloud configuration drift, resulting in exposure to risk.
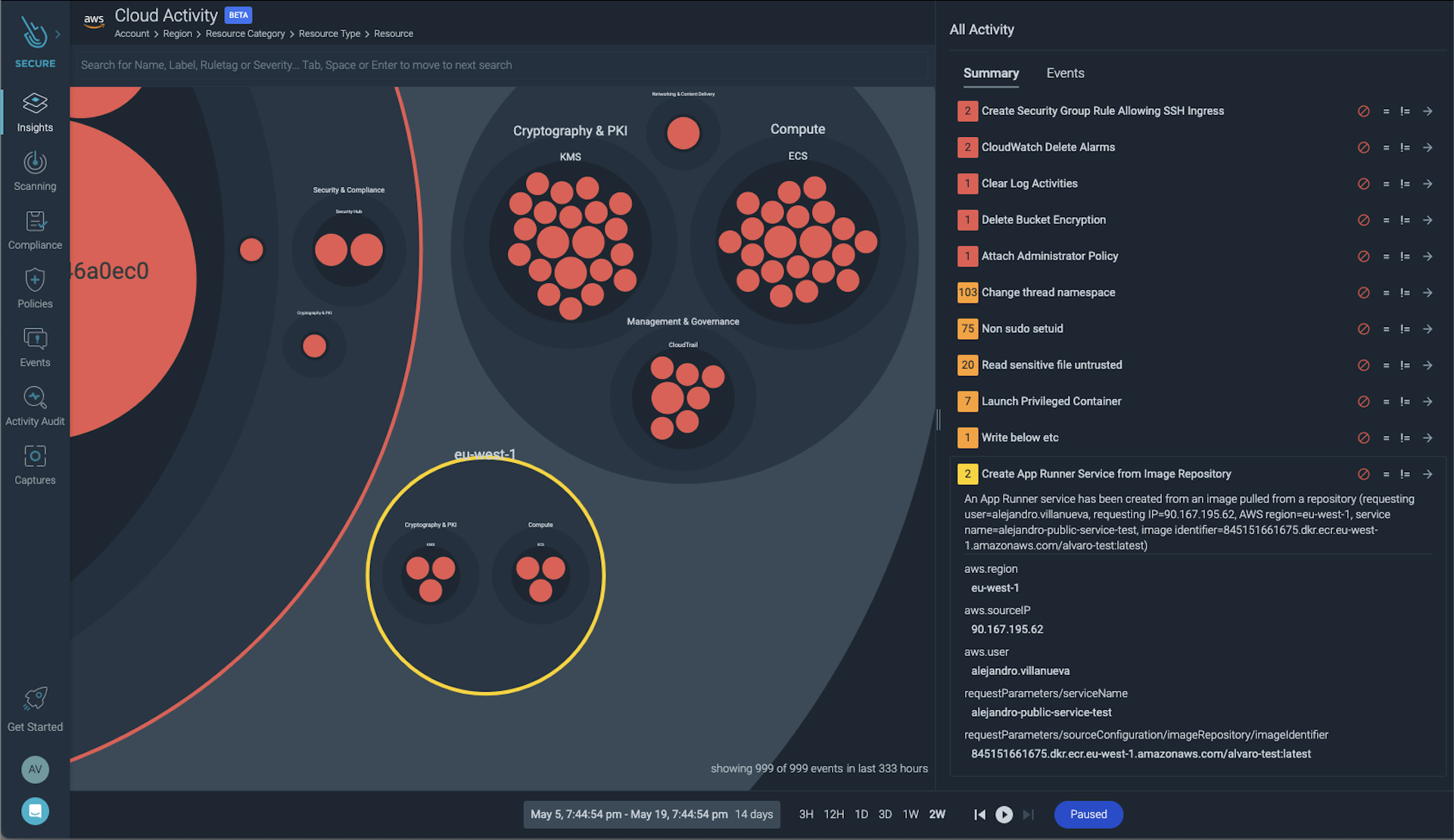
Armed with this information, you now have a very clear picture of the incident and can take action to remedy configuration issues, user permissions, and reduce the likelihood of a repeat offense.
Conclusion
We have seen how getting visibility into App Runner and the surrounding cloud infrastructure, along with automating image scanning, help you be aware of App Runner activity, detect vulnerabilities, and take immediate action to remediate incidents.
App Runner tasks need to be secured just as you would any other cloud asset. Visibility into your container workloads regardless of where they run (e.g., Amazon ECS, Amazon EKS, AWS Fargate, or AWS App Runner) is necessary to detect threats. Augmenting workload insights with cloud insights helps you be even more prepared for incident response and to isolate and prevent issues.
This is what Sysdig Secure is designed to do. It provides the data you need about what happened, with the context of where it happened, and provides details about any surrounding cloud activity. This level of visibility will help you establish controls to protect your applications and infrastructure and quickly identify and diagnose issues like zero-day threats and intrusions to reduce risk for your business.
Want to try these features yourself? Request a 30-day free trial and get started in minutes.


