
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

What's New in Sysdig is back again with the January 2023 edition! I am Dustin Krysak, a Customer Solutions Engineer based in Vancouver, Canada, and I am very excited to update you with the latest feature releases from Sysdig.
This month, Sysdig Secure brings the General Availability of our Host Scanning & CSPM Compliance features. Other changes include Host Vulnerability Reporting, IaC Scanning of Terraform in AWS, and more! Our SDK, CLI, and tools have had several updates and improvements as well.
Sysdig Monitor
- No updates for the month of January.
Please refer to our December Sysdig Monitor Release Notes for current details.
Sysdig Secure
Host Scanning enhancements and General Availability
Vulnerability management for Hosts has received several upgrades and is now considered General Availability.
Newly supported Host OS's
In the development of our Host Scanning feature, many supported OS's were added. In January, we added the following:
- libaba Cloud Linux (a.k.a. Aliyun Linux)
- Google Container-Optimized OS (COS), build 89+
See the complete list of supported Host OSes.
Host vulnerability reporting
Now, it is possible to create scheduled vulnerability reports targeting the Hosts which are scanned with the Sysdig product.
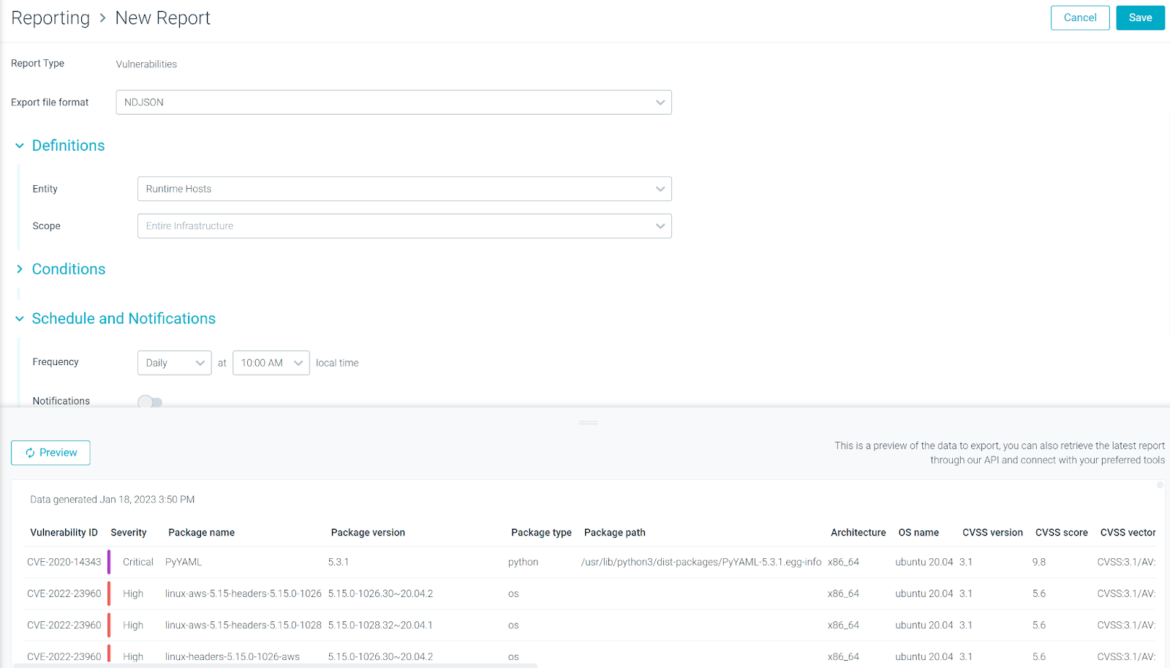
From the Reports function in Sysdig Secure, you can now select if you want to target the Runtime Workloads or Runtime Host. Note that scope labels and report columns will follow the Host Scanning metadata( i.e., HostName or Cloud Provider Region).
CSPM Compliance GA released
Sysdig is pleased to announce the GA release of the new CSPM Compliance, Focus your compliance results on your most important environments and applications!
New features introduced:
- Compliance Page, a new compliance page is introduced, ordered by your Zones!
- CSPM Zones Management
- A default "Entire Infrastructure" zone is created for each customer
- Create your own zone:
- Define scopes for the resources you want to evaluate
- Apply a policy to your zone to add it to the compliance page
- 40+ Risk and Compliance Policies included
To get to know our path from detection to remediation, risk acceptance, zones management, installation, and migration guidelines, please review the documentation.
Note that the new compliance module is not available for OnPrem users. They should continue taking advantage of Unified Compliance.
IaC Scanning now supports Terraform AWS
Sysdig is releasing support for Terraform resources from the AWS Provider. If you have implemented Git IaC Scanning, then pull request checks will now scan AWS resources and report violations of the CIS AWS Foundations Benchmark.
The list of supported resource and source types is now:
- Kubernetes workloads in YAML manifests
- Kubernetes workloads in Kustomize
- Kubernetes workloads in Helm charts
- Kubernetes workloads in Terraform
- AWS cloud resources in Terraform
Other changes in the release include improved Kubernetes resources scanning in Terraform to support additional use cases.
For more information, please check our IaC Security documentation.
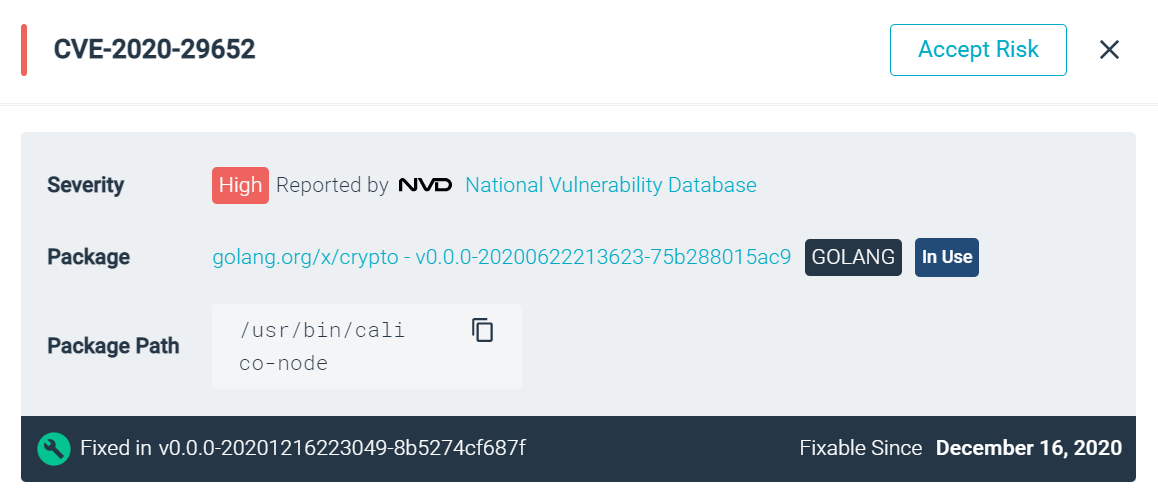
Additional feeds for Golang added to Vulnerability management
Sysdig has added feeds to detect a wider range of Golang-related vulnerabilities. By extracting the packages declared in Golang binaries, we are surfacing vulns in the libraries used to build those binaries. In particular:
Vulnerability Host Scanning for Google COS added
Google COS support has been added to the (preview feature) Host Scanning.
Host Scanning is installed by default when deploying with the Helm chart sysdig-deploy version 1.5.0+.
- Note that Google COS support requires HostScanner container version 0.3.1+.
The new directories added to the default set scanned include:
- Generic binaries (such as docker/containerd and infra tooling)
/bin,/sbin,/usr/bin,/usr/sbin,/usr/share,/usr/local - Libraries (such as default python libs)
/usr/lib,/usr/lib64 - GoogleCOS tooling directories
/var/lib/google,/var/lib/toolbox,/var/lib/cloud
Sysdig Agents
Agent updates
The latest Sysdig Agent release is v12.10.1. Below is a diff of updates since v12.9.1, which we covered in our December update.
Dec. 20, 2022
This hotfix solves the issues discovered in the YAML tab in Advisor in Sysdig Monitor. Clicking the YAML tab works as expected and continues to display YAML configuration for pods.
Dec. 15, 2022
Feature enhancements
Support for Light Mode
A new agent mode, secure_light, has been introduced to provide you with a limited set of secure features. The features that are supported in this mode are:
- Runtime Policies
- Activity Audit (only executed commands)
- Captures
The Sysdig agent running in secure_light mode consumes fewer resources than those running in the secure mode.
For more information, see Secure Light.
Add agent configuration to prevent container operations
A new agent-level configuration, ignore_container_action, has been added to prevent Sysdig agent from taking potentially disruptive container operations, such as kill, pause, and stop, regardless of the policy.
To enable this option, add the following to the dragent.yaml file:
security:
ignore_container_action: trueThis configuration is disabled by default.
When the configuration is enabled and a policy instructs to do a container operation, the agent ignores the policy and creates an Info log message stating that the agent did not take the action because of the configuration.
Also see: Manage Threat Detection Policies | Containers
Improved scope matching
The scope matching for runtime policies has been improved by using equivalent container labels when corresponding Kubernetes labels are temporarily unavailable.
The following settings determine the behavior. The example shows the default values.
Security:
use-container-labels-mapping: true
Container_labels_map:
- "kubernetes.pod.name: container.label.io.kubernetes.pod.name"
- "kubernetes.namespace.name:container.label.io.kubernetes.pod.namespace"IMDSv2 support on AWS Deployments
A new agent-level configuration, imds_version, should be set to 2 on all the deployments that require token-based communication with the AWS metadata service (IMDSv2).
imds_version: 2To continue using the IMDSv1 style AWS metadata requests, leave the configuration unchanged or set it to 1.
imds_version: 1Fix vulnerabilities
- Updated the Go version used for Promscrape to 1.18.7 to resolve CVEs.
- Updated Jackson library to resolve CVE-2022-42003 and CVE-2022-42004.
- Upgraded snakeyaml to 1.32 in sdjagent to address CVE-2022-38752.
Disable checking memory consumption
Disabled the agent watchdog from checking memory consumption when running in Kubernetes, since Kubernetes has its own resource management. If you wish to re-enable the agent watchdog to check memory consumption when running in Kubernetes, set the following config parameter:
Watchdog:
check_memory_for_k8s: trueReport additional labels for Cost Advisor
Modified the default Kubernetes label filters to allow collecting additional labels to identify the instance, region, zone, and the operating system of the nodes. The additional labels help calculating costs associated with your infrastructure.
Identify delegated agents
Added the statsd_dragent_subproc_cointerface_delegated metric to indicate whether the agent is delegated or not.
Improved retrieval of container metadata
Improved fetching container metadata when both Docker and CRI runtimes are available. This reduces problems where runtime policy events have missing container information.
Known issue
The YAML tab in Advisor in Sysdig Monitor that displays pod structure, similar to a kubectl describe operation, might not work as expected. Clicking the YAML tab can lead to an agent restart and, as a result, a temporary loss of metrics.
As a workaround, disable it in the dragent.yaml file as follows:
k8s_command:
enabled: falseDefect fixes
Report all storage classes
The agent now reports all the storage classes instead of just one. Earlier, the agent only sent one storage class from global_kubernetes in the metrics protobuf when multiple storage classes exist in the cluster.
Match group name and user name appropriately in events
Events now reports group.name and user.name correctly. This was caused by an issue where root ID was being resolved as N/A for containers in some cases.
Container terminal shell no longer returns N/A
Implemented container password and group lookup to prevent terminal shell in container returning N/A for the user.name.
Generate command execution records for ARM
Fixed an issue with the activity audit where command execution records were not being generated on ARM processor systems, for top-level processes executed within a container, and with no associated TTY.
Reports labels correctly on pod redeployment
Fixed an issue with promscrape where the agent would report the old pod UID when a pod is redeployed. This led to having all the labels missing from the timeseries scraped from that pod.
Fix JMX monitoring on newer JRE versions
Fixed an issue where JMX monitoring did not work correctly on newer JRE versions due to sdjagent exceptions.
Please refer to our v12.10.1 Release Notes for further details.
Agentless updates
- No updates for the month of January.
Please refer to our December v3.0.5 Release Notes for current details.
SDK, CLI, and Tools
Sysdig CLI
v0.7.14 is still the latest release. The instructions on how to use the tool and the release notes from previous versions are available at the following link:
https://sysdiglabs.github.io/sysdig-platform-cli/
Python SDK
v0.16.4 is still the latest release.
https://github.com/sysdiglabs/sysdig-sdk-python/releases/tag/v0.16.4
Terraform Provider
There is a new release v0.5.47.
Documentation – https://registry.terraform.io/providers/sysdiglabs/sysdig/latest/docs
GitHub link – https://github.com/sysdiglabs/terraform-provider-sysdig/releases/tag/v0.5.47
Terraform modules
- AWS Sysdig Secure for Cloud has been updated to v10.0.3.
- GCP Sysdig Secure for Cloud remains unchanged at v0.9.6.
- Azure Sysdig Secure for Cloud has been updated to v0.9.3.
Note: Please check release notes for potential breaking changes.
Falco VSCode Extension
v0.1.0 is still the latest release.
https://github.com/sysdiglabs/vscode-falco/releases/tag/v0.1.0
Sysdig Cloud Connector
AWS Sysdig Secure for Cloud is unchanged. The current release is still v0.16.26.
AWS Sysdig Secure for Cloud
AWS Sysdig Secure for Cloud remains unchanged at v0.10.3.
Admission Controller
Sysdig Admission Controller has been updated to v3.9.14.
Documentation – https://docs.sysdig.com/en/docs/installation/admission-controller-installation/
Runtime Vulnerability Scanner
The new vuln-runtime-scanner has been updated to v1.2.13.
Documentation – https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/runtime
Sysdig CLI Scanner
Sysdig CLI Scanner remains at v1.3.2.
Documentation – https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/pipeline/
Image Analyzer
Sysdig Node Image Analyzer remains at v0.1.19.
Host Analyzer
Sysdig Host Analyzer remains at v0.1.11.
Documentation – https://docs.sysdig.com/en/docs/installation/node-analyzer-multi-feature-installation/#node-analyzer-multi-feature-installation
Sysdig Secure Online Scan for Github Actions
The latest release is still v3.4.0.
https://github.com/marketplace/actions/sysdig-secure-inline-scan
Sysdig Secure Jenkins Plugin
Sysdig Secure Jenkins Plugin is still v2.2.6.
https://plugins.jenkins.io/sysdig-secure/
Prometheus Integrations
The PromCat team officially released Prometheus Integrations v1.7.0!
Integrations:
- Sec: promcat-jmx-exporter image Critical High vulnerabilities
- Sec: postgresql-exporter image Critical High vulnerabilities
- Fix: Fix issues in the NTP integration
- Fix: Add Logo for Windows integration
- Feat: Add new dashboards for time series measuring to the integrations yaml
- Fix: kubeapi job is using the port label and in some cases doesn't exists
- Fix: Monitoring Integrations – MongoDB install fails
- Fix: Typo in Calico integration
- Fix: Make clear the ksm integration is OSS in docs
- Fix: k8s api-server has a bug in the metric filter
Dashboards and alerts:
- Fix: Linux Host Overview Panels show some values incorrectly
- Feat: Add more Windows alerts using Windows default metrics and process collector metrics
Internal tools and docs:
- Fix: Improve some documentation pages
Sysdig on-premise
5.1.6 Hotfix
Upgrade process
- Supported upgradesfFrom: 4.0.x, 5.0.x
For the full supportability matrix, see the Release Notes on Github. There, you will also find important Install instructions.
- Fixed a privacy setting issue that would revert the admin setting after an update to the values.yaml file.
- Fixed a sidepanel interface bug that would appear under Scan Results.
- Fixed an issue with the metadata service sometimes returns an empty string as a value for some metrics, causing a banner to display saying "A new version of Sysdig is available."
- Fixed an Anchore issue that would show vulnerabilities in packages that should not have been present.
- Updated the Anchore image with latest code and security updates.
Falco rules changelog
Version 0.99.0
Rule changes
- Added the following rules:
- Modify Security Group Rule Allowing Ingress Open to the World
- Connection to IPFS Network Detected
- Improved condition for the following rules:
- Create Security Group Rule Allowing Ingress Open to the World
- Create a Network ACL Entry Allowing Ingress Open to the World
- Detect reconnaissance scripts
- Lastlog Files Cleared
- Launch Remote File Copy Tools in Container
- Put Bucket Lifecycle
- Delete or rename shell history
- Added exception for the following rules:
- Put Bucket Lifecycle
- Update Assume Role Policy
- Updated IoCs Ruleset with new findings
- Reduced false positives for the following rule: Find AWS Credentials
- Default Policy Changes
Added the following rules:- Modify Security Group Rule Allowing Ingress Open to the World
- Connection to IPFS Network Detected
Our Falco team has been busy this month with multiple releases of new features. For more information on what has been released for the entire month of January, please review it here.
New Website Resources
Blogs
- Sysdig, a Leader in Frost Radar, CNAPP 2022
- Top 15 Kubectl plugins for security engineers
- Sysdig Secure and Google Security Command Center Integration – Why, What, How
- Sysdig Monitor Introduces native support for Microsoft Azure Monitor
- Exploiting IAM security misconfiguration and how to detect them
- Our Journey Into Cutting Kubernetes by 40%
- How to Monitor kube-controller-manager
Threat research
Webinars
- Exploring the 2022 State of DevOps Report with Google and Sysdig
- A Hackers Secret to Ethically Cracking the Code in Today's Digital World with Dr. Charlie Miller
Tradeshows
Education
The Sysdig Training team provides curated hands-on labs to learn and practice different topics. The selection of courses for the month of January:
- Learn how to create Kubernetes Network Policies with Sysdig Secure.
- Falco v0.31.0 can now be extended via plugins to detect cloud threats. Learn how to read AWS CloudTrail logs and detect suspicious cloud activity in this lab.


