How to Secure AWS Fargate
Containerization has become one of the pillars of modern cloud-native development, allowing for faster, more flexible, and agile software development. The container ecosystem’s maturation has accelerated in recent years, with various vendors offering a plethora of solutions. As a major cloud provider, AWS has introduced services designed specifically to assist users in running containerized applications more efficiently and effectively. When it comes to tooling and services, AWS users can choose from three major AWS container services: Fargate, Elastic Container Service (ECS), and Elastic Kubernetes Service (EKS).
Continue reading this post to learn how to secure AWS Fargate and its related services, ECS and EKS. We will also discuss some of the best security practices you can implement.
How to Secure AWS Fargate
What you'll learn
-
What AWS Fargate is
-
How the shared responsibility model applies to AWS Fargate
-
Steps you can take to ensure AWS Fargate is secure
What Is AWS Fargate?
AWS Fargate is a pay-as-you-go AWS service that can automatically provision, configure, and scale virtual machine clusters based on the minimum requirements of your containers. It is a serverless compute engine used to launch and run containers without the need to provision or manage the underlying infrastructure.
AWS Fargate works with Amazon Elastic Container Service (ECS) and Amazon Elastic Kubernetes Service (EKS). Customers can use AWS Fargate technology to run containers without having to manage servers or clusters of Amazon EC2 instances. As a result, they do not need to provision, configure, or scale virtual machine clusters to run containers. This is achieved by abstracting the underlying resources.
Some of the salient features of AWS Fargate include:
- AWS Fargate enables you to deploy and manage your applications without worrying about infrastructure by removing the operational overhead of scaling, patching, securing, and managing servers.
- AWS Fargate enables you to monitor your applications through built-in integrations with AWS services such as Amazon CloudWatch Container Insights. You can also use third-party tools to collect metrics and logs.
- AWS Fargate supports the pay-as-you-go pricing model, which means you only pay for what you use. Fargate scales the compute to match your specified resource requirements closely.
- AWS Fargate also helps you improve security through workload isolation. Amazon ECS tasks and EKS pods each have a dedicated runtime environment.
How Secure Is AWS Fargate?
Like any other AWS service, AWS Fargate operates on a shared responsibility model in which customers are responsible for security “in” the cloud, while AWS is responsible for the security “of” the cloud. Given the unique arrangement in AWS Fargate, where AWS oversees infrastructure provisioning, there have been questions about the user’s role in ensuring the security of AWS Fargate within their container applications.
The level of security offered by AWS Fargate will depend on how closely the customer and AWS can adhere to the shared responsibility model. Because of the abstraction benefit, Fargate enables users to give AWS more security responsibilities. Compared to other self-managed instances, AWS Fargate is responsible for more AWS infrastructure resources.
However, keeping user accounts and applications secure continues to be crucial. An attacker can use a Fargate container as a base to move laterally and access additional rights or sensitive information once they have taken control of it. The customer is responsible for averting this scenario by protecting the application code and service configuration.
The AWS Shared Responsibility Model
The diagrams below illustrate how the responsibility of running ECS on EC2 instances varies from running ECS Fargate. AWS is in charge of the physical hardware, underlying services, and ECS control plane in both variations. But it’s crucial to remember that you, the client, are in charge of the underlying virtual machine that houses your container instances on ECS/EC2. The good news is that AWS provides one-click solutions for managing these virtual machines.
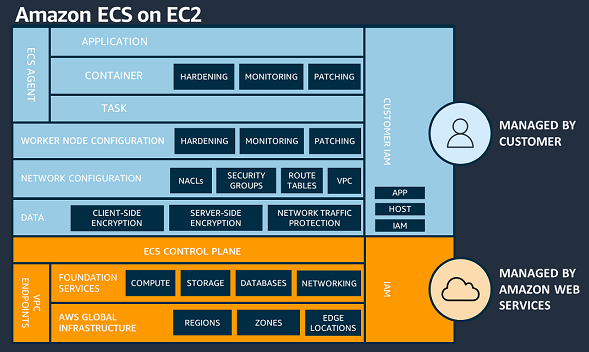
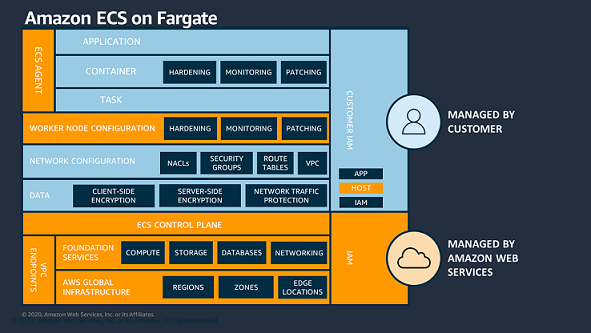
Fargate Security Concerns and Risks
With Fargate, AWS assumes more responsibility for infrastructure security, but there’s still an attack surface to account for. AWS Fargate customers encounter several concerns and risks, including:
- Lack of visibility: The lack of access to the operating system in AWS Fargate makes it very challenging to reach a high level of visibility into what is happening in your container infrastructure. Without deep visibility into the activity of your Fargate workloads, it will be nearly impossible to detect anomalous activities; therefore, it will be nearly impossible to secure the Fargate containers. You cannot secure what you cannot see.
- Misconfigurations in AWS Fargate IAM: IAM roles and access configurations are an integral part of Fargate security, as they delegate permissions to specify which groups or users can access Fargate deployments. Any misconfigurations within the AWS Fargate IAM would allow unauthorized access to sensitive data.
- Lack of container security: Container security is a key part of ensuring that container workloads within Fargate work as intended. Without effective security protecting your containers, you could fall victim to several threats, including container privilege escalations, malware spreading across multiple containers over a network, and access control exploits.
How to Secure AWS Fargate: Best Practices
Automating Container Image Scanning
You can secure AWS Fargate by implementing automated AWS Fargate image scanning to block container threats. Image scanning analyzes the build process and contents of a container image in order to detect security issues, vulnerabilities, or bad practices.
Image scanning can be implemented at various points throughout the container or Kubernetes lifecycle. It provides critical insights that help you ensure security and compliance without compromising the flexibility required to build and run your applications.
Data Encryption
When running AWS Fargate on EKS or ECS, you can encrypt data stored on ephemeral storage with service-managed keys using the industry-standard AES-256 cryptographic algorithm. AWS Fargate customers can take advantage of the 20 GB of ephemeral storage provided for downloading and processing encrypted data. Fargate seamlessly handles data encryption and decryption, so you don’t have to change your applications to access your data. This increases productivity and security. Customers will gain free data encryption while meeting their compliance and security goals.
AWS Fargate Monitoring
Monitoring AWS Fargate gives you 360-degree visibility into your apps and enables you to troubleshoot them faster. CloudWatch, AWS’s default monitoring toolset, includes several features for ECS and Fargate users. For example, CloudWatch Container Insights provides insight into what is going on inside your containers. Using the performance monitoring features available in the Amazon CloudWatch console, you can see a container’s CPU, memory, network, and bytes read/written. The summary of insights on the CloudWatch Container Insights dashboard helps engineering teams debug issues more quickly.
Securing AWS ECS Fargate
There are several best practices you can implement to secure AWS Fargate when working with ECS. For example:
- Use security groups: In AWS ECS Fargate, you can use security groups to control traffic to and from your containers. This will shield the Fargate deployments from unwanted traffic entering the ECS environment.
- Configure IAM: As with any other AWS resource, you can secure AWS ECS Fargate by configuring strong Identity and Access Management (IAM), policies like multi-factor authentication, IAM roles, and security tokens to prevent unauthorized access to your container applications.
Securing AWS EKS Fargate
When using Fargate with EKS, you can configure the best security practices to protect your entire Kubernetes container service by delegating permissions to Fargate via IAM roles, security tokens, and security groups. Additionally, you can configure a secure protocol for contacting Fargate by using security groups to limit traffic to your containers. You can also configure EKS to log and analyze data using AWS CloudTrail and Amazon CloudWatch. This ensures the security of the AWS Fargate resources within your EKS environment.
Conclusion
For businesses looking to simplify container management in the cloud, AWS Fargate reduces your team’s operational burden by offering a serverless experience that abstracts away infrastructure management. As we explained in this post, the customer is responsible for application code security, while AWS oversees the management of the underlying Fargate infrastructure and execution environment. Customers are responsible for actively managing security within AWS Fargate and its associated services, EKS and ECS.
In addition to the security best practices discussed above, Fargate users should utilize a comprehensive security platform for detecting and responding to threats as well as managing their overall cloud security posture.


