AWS CloudTrail
Category
Other Resources
Cloud security with AWS CloudTrail
Detect and respond to cloud threats using AWS CloudTrail logs with Sysdig Secure.
AWS CloudTrail monitors and records account activity across your AWS infrastructure. Sysdig runtime policies, built on Falco, automate monitoring of AWS CloudTrail logs to detect unauthorized access, configuration changes and anomalous activity across your AWS accounts and services.
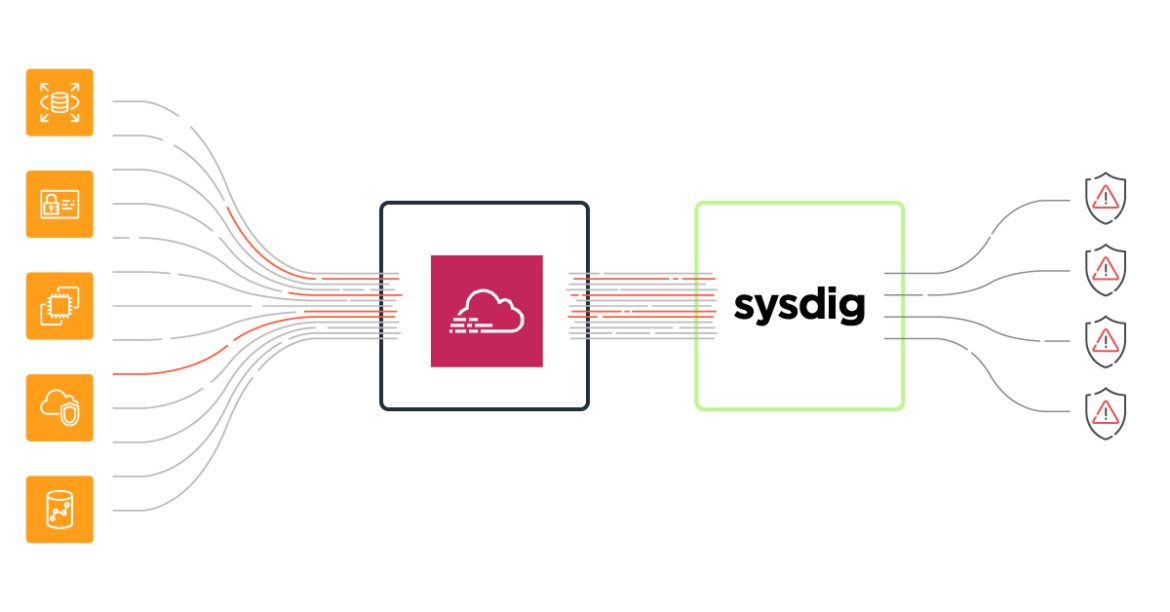
Out-of-the-box CloudTrail rules detect logged events including:
- Login without MFA / deactivate MFA
- Delete bucket encryption
- Create an AWS user
- Create/delete cluster
- Create a public facing load balancer
- CloudTrail logging disabled
- Attach an administrator policy
- Associate an elastic IP address to an AWS network interface
- Allocate a new elastic IP address to AWS account
- Add an AWS user to a group
Read More
Implementing cloud threat detection for AWS with Sysdig Secure and AWS CloudTrail takes just a few minutes. Check out our documentation to learn more.
Other Resources
