
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Welcome to another monthly update on what's new from Sysdig! This month's big announcement is our new support for Prometheus as a managed service. There are several individual features behind this which we cover in more detail below, but here is a summary:
- Sysdig offers remote write and more custom metrics for its managed Prometheus service.
- Sysdig Monitor radically simplifies monitoring integrations based on open source.
Also, Kubernetes 1.22 was released and we shared our review of what to look out for. Go check out our Kubernetes 1.22 – What's new? post if you haven't already.
As always, please go review our own Release Notes for more details on product updates, and ping your local Sysdig contact if you have questions about anything covered in here.
Sysdig Secure
Admission Controller with Kubernetes Audit
This month, we announce the general availability of the Kubernetes Audit functionality as part of the Sysdig Secure Admission Controller.
Background:
Kubernetes admission controllers provide operators the ability to validate and/or mutate incoming API requests. Admission controllers are a core functionality of Kubernetes, and many are enabled by default.
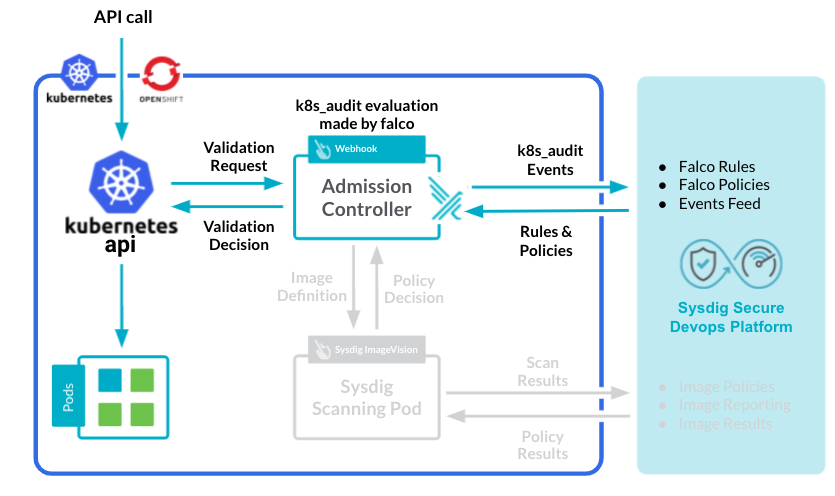
Sysdig Secure has long provided Kubernetes API security by using k8s_audit Falco rules to create policies against Kubernetes audit logs. However, there have been some complications:
- Diverse setup requirements:Many Kubernetes distros are opinionated in a way to collect and access logs, with some using dynamic backends (deprecated in Kubernetes 1.19, but still available in OCP up to 4.3). More vanilla approaches use webhooks, and cloud providers require a bridge to collect logs via their own logging streams.
- Distros diverging from Falco:With OCP 4.4+, there was no clear way to collect and validate audit logs against our Falco rules.
The Solution?
Tap directly in the Kubernetes API request via Admission Controllers and use the existing k8s_audit rules our customers have relied on for so long. See the installation instructions.
Falco Rules
v0.33.0 is the latest version. Below is a diff of changes from v0.20.1, which we covered last month.
Once again, there are a lot of changes and improvements in these versions as we continue to bring you more cloud security rules and improve our container security rules. This includes:
- Additional exception rules for easier filtering, as well as addressing false positives.
- Additional GCP event rules.
Check the Falco Rules Changelog for a full list of changes.
Sysdig Monitor
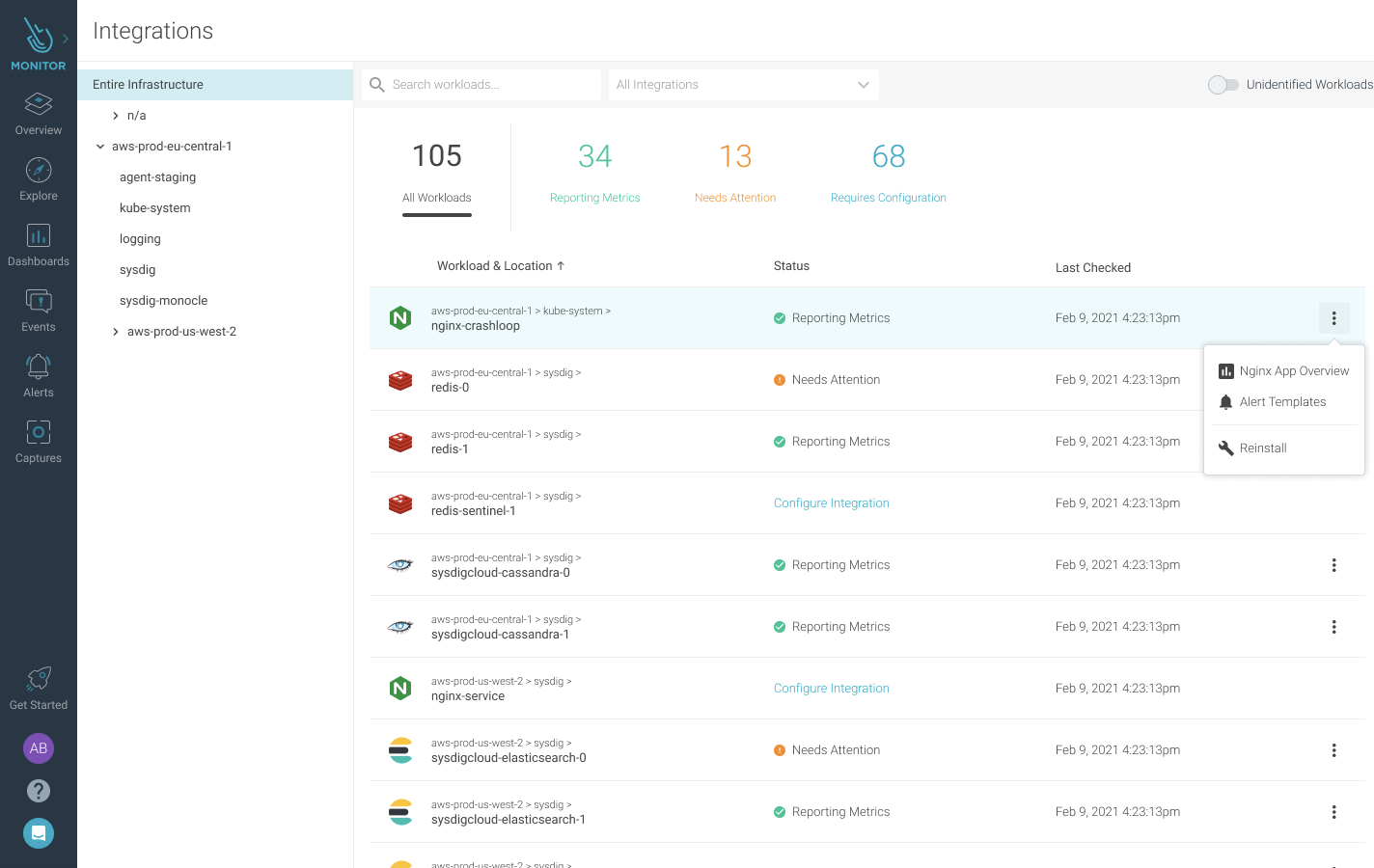
Monitoring Integrations
Sysdig discovers the services running in your environment and gives you visibility into deeper application performance and health telemetry by configuring a managed Monitoring Integration through PromCat. You can easily view which services you can configure an integration for, check the status of existing integrations, and leverage curated content in the alerts library and out-of-the-box dashboards.
Alerts Library
The Alerts Library in Sysdig Monitor gives you a recommended list of alerts to configure based on the services running in your infrastructure. The curated content from Sysdig removes the need to guess which alerts to configure, taking you to full monitoring coverage faster.
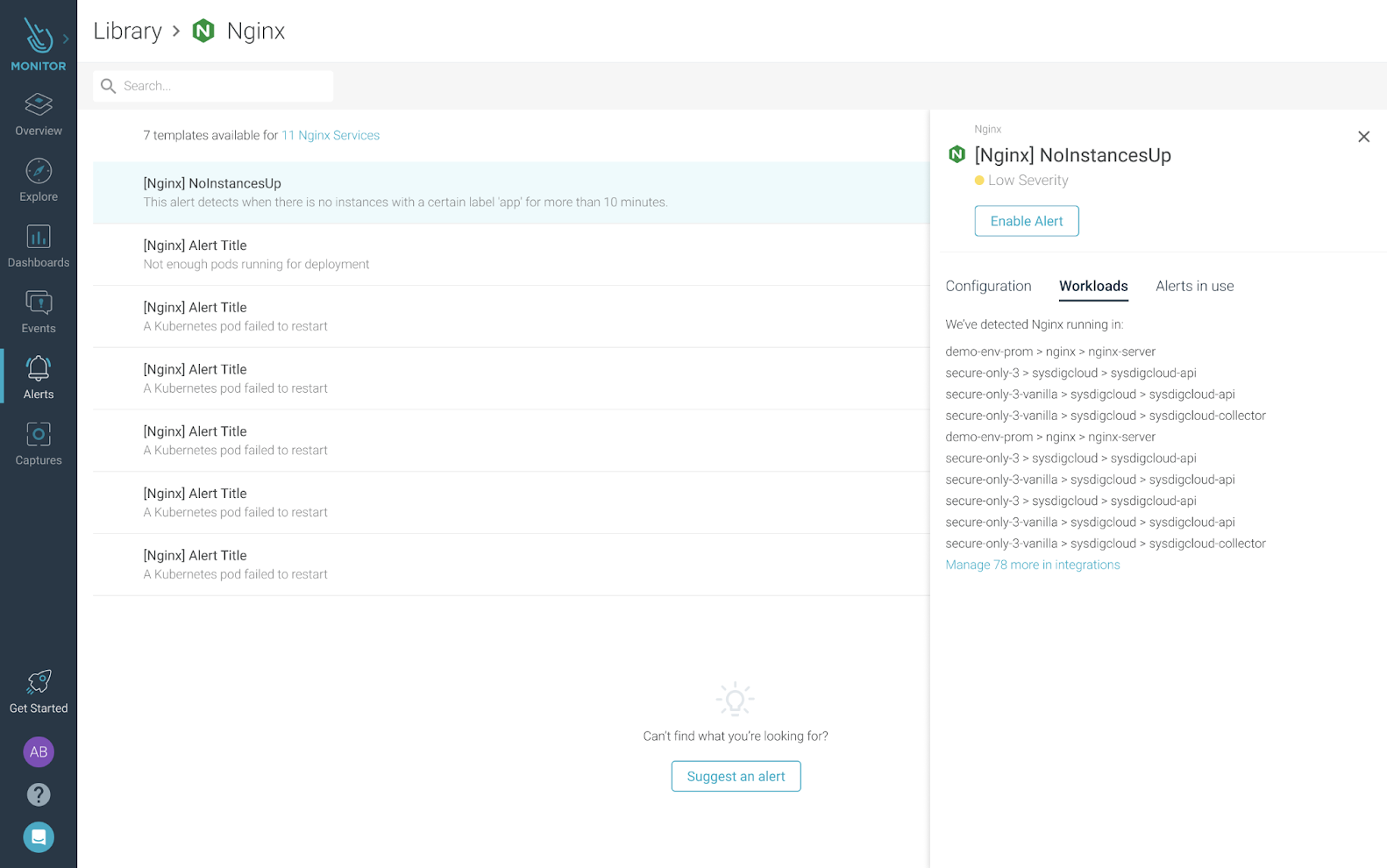
For more information, see Alerts Library.
Enhanced Kubernetes Dashboards
We have introduced several improvements to the out-of-the-box Kubernetes dashboards:
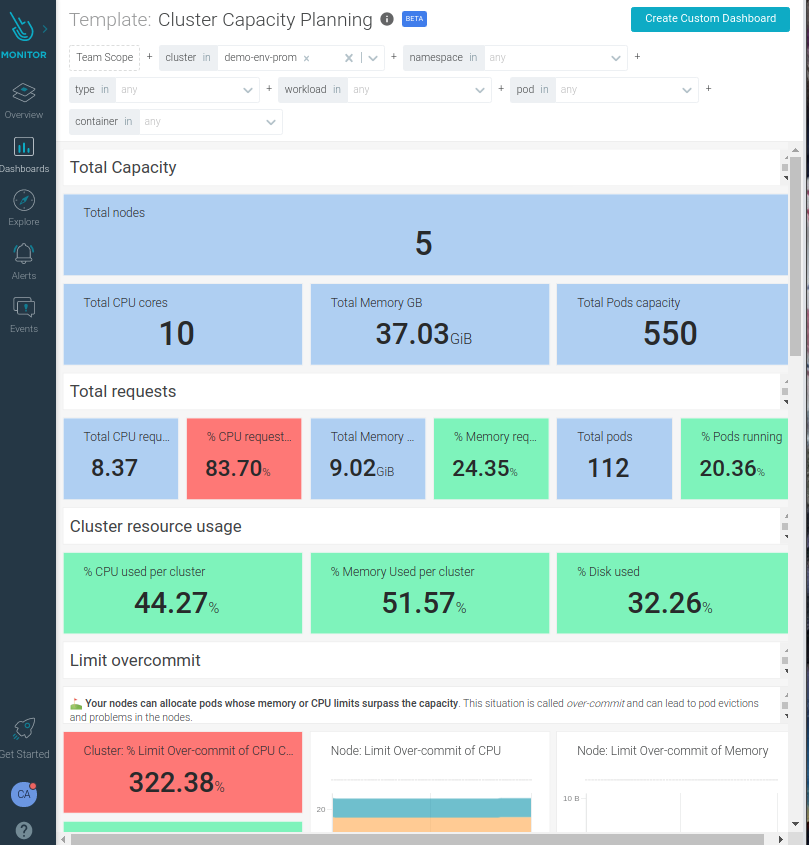
- Workload dashboards are refreshed with relevant status and golden signals.
- Improved UX with panel location and color code.
- Some workflows are simplified to make it easier for beginners in Kubernetes.
- Improved capacity planning capabilities.
- Text boxes are easier to read and locate near the relevant panels.
Customized Session Expiration
Session expiration is the amount of time a user can remain idle before the session is automatically ended or expired. After the session expires, the user must log into the Sysdig application again.
Sysdig now gives you the ability to make a shorter or longer idle session expiration for Sysdig applications. When a user browser is idle for a certain period of time, they will be automatically logged out. For more information, see Configure Customized Session Expiration.
Sysdig Agents
Sysdig Agent
The latest Sysdig Agent release is 11.4.0. Below is a diff of updates since 11.3.0, which we covered in our last update.
Feature Enhancements
- Probe Builder – The probe builder can now be used to build kernel modules for the Sysdig agent. It can run on any host with Docker installed, including (with some preparation) air-gapped hosts. Probe Builder is now enabled and available at https://github.com/draios/probe-builder. See the Readme for more information.
- Promscrape v2 – Promscrape v2 (used when
prom_service_discoveryis enabled for Prometheus) has been changed to discover only Kubernetes pods running on the same node as the agent. This should help reduce the load on the Kubernetes API servers in large clusters. - Added Missing Fields for Unified Workload Metrics – Added Kubernetes metric fields, indicating the availability of daemon sets (
status.numberAvailable,status.numberUnavailable, andstatus.updatedNumberScheduled), as well as replica sets (status.availableReplicas) to support workload-level metrics (SaaS only).
Known Issues
App check-in agent-slim doesn't work due to missing dependencies. This problem will be addressed in an upcoming hotfix release.
Defect Fixes
- Multiple Hosts No Longer Report the Same Pod – Fixed an issue causing multiple hosts to report the same pod if its UUID is the same on both hosts.
- Duplicate StasD Metrics Are Reported Correctly – Fixed an issue related to handling duplicate StatsD metrics corresponding to a container that is reported by a host.
- Stale Markers Are Sent properly for Dropped Targets – Properly generate stale markers for Prometheus metrics when a scrape target is no longer available and when using
promscrape.v1. - Report a Positive Time Delta Value – Fixed a defect that could result in invalid
file.time.in,file.time.out,file.time.other, andfile.time.totalvalues. - Agent No Longer Crashes When App Check or Prometheus Is Enabled – Fixed a defect that could crash the agent when app checks or Prometheus are enabled.
- Secure Captures No Longer Causes Host Shutdown – Prevent agent restarts caused by apparent stalls encountered in the sample handler thread.
Sysdig Serverless Agent
The latest Sysdig Serverless Agent release is 2.0.0, which we covered in our last update.
Sysdig Agent – Helm Chart
The Helm Chart 1.12.8 is the latest version. Below is a diff of updates since v1.12.7, which we covered in our last update.
- Update values.yaml and README.md to reflect no default value for
nodeAnalyzer.apiEndpoint.
https://charts.sysdig.com
Changelog: https://github.com/sysdiglabs/charts/blob/master/charts/sysdig/CHANGELOG.md
Node Analyzer
Version 0.1.13 is still the latest release, which we covered in our last update.
Node image analyzer can be installed as part of the Sysdig Agent install: https://docs.sysdig.com/en/scan-running-images.html
Inline Scanning Engine
v2.4.5 is the latest release. Below is a diff of updates since v2.4.3, which we covered in our last update.
Change
- Bumped ClamAV version to latest (0.103.3).
- Updated base image to get updated security fixes (July 2021).
- Added retry mechanism when pulling images from registries.
- Added a
--write-json PATHoption to permit storing json log to file.
Fixed
- Hotfix: Invalid json output when also using a verbose flag.
- Fixed Malware scan fails when an image has not read permissions on files.
- Fixed a failure in getting images for registries that don't support tag listing.
See also: Integrate with CI/CD Tools.
Admission Controller
v3.4.1 is the latest release. Below is a diff of updates since v3.4.0, which we covered in our last update.
- Support postfix via regex in namespace matcher.
https://docs.sysdig.com/en/admission-controller.html
SDK, CLI and Tools
Sysdig CLI
v0.7.12 is still the latest release, which we covered in our last update.
https://github.com/sysdiglabs/sysdig-platform-cli/releases/tag/v0.7.12
https://sysdiglabs.github.io/sysdig-platform-cli/
Python SDK
v0.16.2 is still the latest release, which we covered in our last update.
https://github.com/sysdiglabs/sysdig-sdk-python/releases/tag/v0.16.2
Terraform Provider
v0.5.16 is the latest release. Below is a diff of updates since v0.5.15, which we covered in our last update.
- Added support for Falco exceptions. More info here.
Falco VS Code Extension
v0.1.0 is still the latest release.
https://github.com/sysdiglabs/vscode-falco/releases/tag/v0.1.0
Sysdig Cloud Connector
v0.8.1 of the Sysdig Cloud Connector was released, we covered v0.7.13 last month.
Here are some highlights of the diff between these versions:
New Features
- Supporting GCP Audit Logs
Bug Fixes
- Show the username who assumed the role instead of the assumed role.
- Fixed a typo on config settings when registering on GCP.
- Fixed GCP registry when the project is an empty string.
aws.userwhen identity is provided via SAML or Web.
Check the full list of changes to get the full details.
Sysdig Secure Inline Scan for Github Actions
v3.2.0 is the latest release. Below is a diff of updates since v3.0.2, which we covered in our last update.
- Changed the way the inline-scanner is executed to allow running with Rootless docker.
- If multiple images are scanned, create multiple run checks.
- Added a debug output when debug is enabled for actions.
- Bumped octokit to v5 and dependency versions.
https://github.com/marketplace/actions/sysdig-secure-inline-scan
Sysdig Secure Jenkins Plugin
v2.1.11 is the latest release. Below is a diff of updates since v2.1.9, which we covered in our last update.
- Honor the environment variables injected with InjectEnv plugin for Freestyle jobs.
- Include publish and fix date for vulnerabilities in security report, when available and provided by the backend.
- New option,
runAsUser, to execute the inline scanner as the specific UID. - New option,
inlineScanExtraParams, to add additional parameters to the inline scanner. - Honor the environment variables set at the step level (
withEnv) or at the stage level (environment) for pipelines.
https://plugins.jenkins.io/sysdig-secure
New Website Resources
Blogs
- Sysdig and Apolicy: Automating cloud and Kubernetes security with IaC security and auto-remediation
- THREAT ALERT: Crypto miner attack – Sysrv-Hello Botnet targeting WordPress pods
- Send your metrics to a Prometheus Remote Write endpoint without Prometheus – OpenTelemetry
- AWS GDPR compliance with Sysdig Secure
- Sysdig offers remote write and more custom metrics for its managed Prometheus service
- Having your Pi, and eating it with Prometheus remote write!
- No pain… More gain! Sysdig Monitor radically simplifies monitoring integrations based on open source
- Securing AWS IAM with Sysdig Secure
- Sysdig supports Respect in Security to remove harassment from the industry
- Kubernetes 1.22 – What's new?
- How to mitigate CVE-2021-33909 Sequoia with Falco – Linux filesystem privilege escalation vulnerability
- What is the MITRE ATT&CK Framework for Cloud? | 10 TTPs You should know of
Webinars
- Improve Your Capacity Planning for Kubernetes
- Simplifying the Prometheus Experience
- Modernize and Secure DevOps with Confidence
- Improve Cloud Threat Detection and Response using the MITRE ATT&CK Framework


