
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

What's New in Sysdig is back again with the November 2022 edition! I am Matt Shirilla, an Enterprise Sales Engineer based in Texas, and I am very excited to update you with the latest feature releases from Sysdig.
For Sysdig Monitor, this month brings new filtering for AWS Cloudwatch Metric Streams and a new Lambda Extension for AWS Lambda Telemetry API , plus the release of new Advisories. For Sysdig Secure, we have several usability improvements and new Falco rules from our Threat Research Team.
Sysdig Monitor
New Advisories
The following new Advisories have been introduced:
- Cluster pod capacity: Cluster is reaching pod capacity, when this happens new pods cannot be scheduled.
- Replicas unavailable: A workload has unavailable replicas, which can affect app availability.
- Cluster CPU overcommitment: Cluster is overcommitting CPU, which may affect availability.
- Cluster memory overcommitment: Cluster is overcommitting memory, which may affect availability.
Filtering AWS Cloudwatch Metric Streams
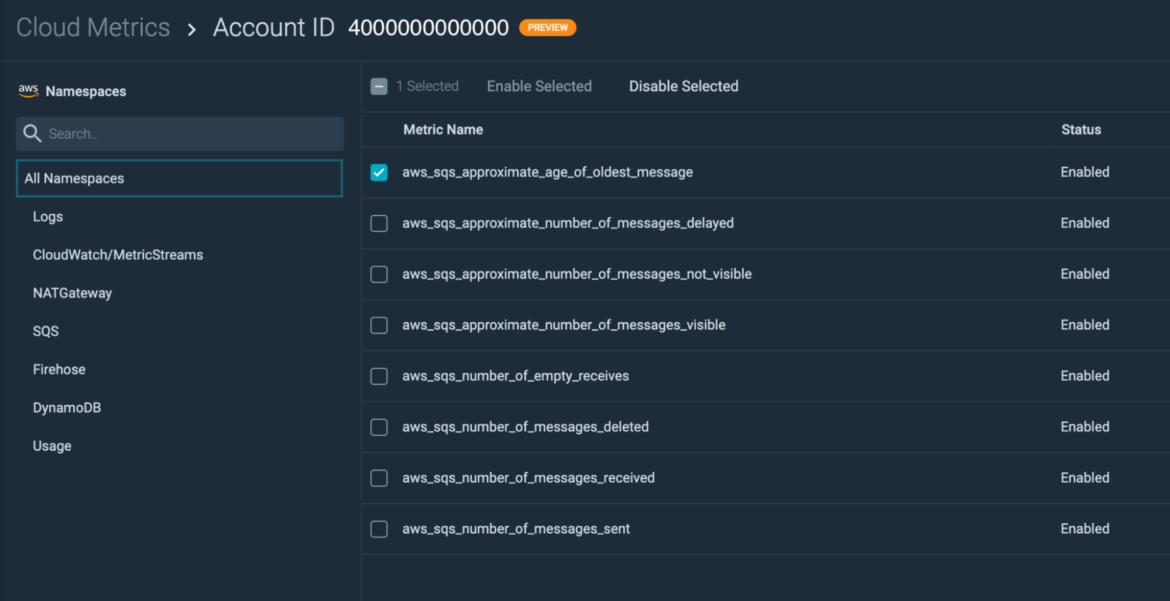
Sysdig now provides you the ability to filter (drop) metrics that are coming from AWS CloudWatch Metric Streams via Kinesis Firehose. This provides our AWS users full control over what metrics coming from Streams are ingested and stored by Sysdig Monitor. With CloudWatch Steams Metrics Filtering, you can now choose to only ingest and store the metrics that are important for you, on a per-service basis, thereby reducing the data storage cost. You can include or exclude specific metrics from individual AWS namespaces as they are ingested.
- The ability for customers to filter (e.g., drop) metrics that are coming from AWS CloudWatch Streams via Kinesis Firehose, providing our AWS customers full control over what metrics coming from Streams are ingested and stored by Sysdig Monitor.
- AWS currently does not offer the ability to filter CloudWatch Streams metrics that are pushed to an endpoint like Sysdig Monitor; it's all or nothing. With CloudWatch Steams Metrics Filtering, customers can now choose to only ingest and store the metrics that are important for them, on a per-service basis.
- Yes, this has been enabled for all users in all AWS regions. Once a customer enables an AWS CloudWatch Streams account, they'll be able to access filtering.
- You can find AWS CloudWatch Metrics Filtering under Monitor -> Integrations -> Data Sources -> Cloud Metrics -> -> Manage Metrics
- CloudWatch Streams Metrics Filtering is just the tip of the iceberg for bringing more metric-level control into the Monitor UI. Stay tuned for more information on what's coming up next with metrics management.
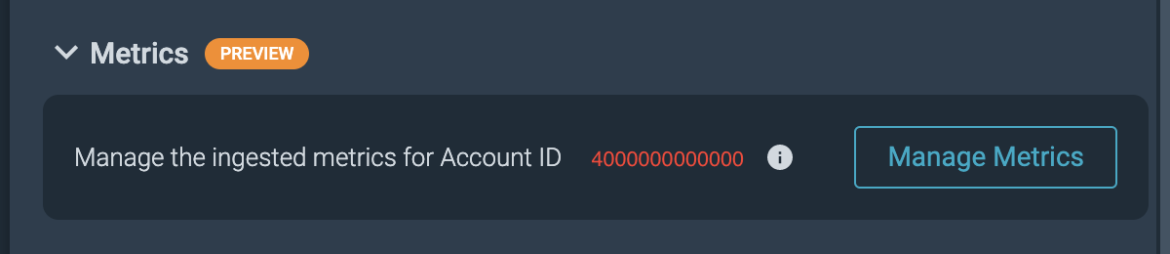
For more information, see Filter Metrics from CloudWatch Metric Stream.
No-data support for Metric and Event Alerts
We are now giving users the option to configure how our alerting system behaves when a metric stops reporting data (for the configured segment / scope / duration).
Sysdig Monitor Lambda Extension for AWS Lambda Telemetry API
The Cloud Monitoring team is excited to announce preview availability of the new Sysdig Monitor Lambda Extension for AWS Lambda Telemetry API! This new Lambda extension allows Sysdig Monitor users to consume metrics directly from Lambda events as functions are executed, bypassing the need to route Lambda metrics through another platform, such as AWS CloudWatch.
The new Lambda extension generates metrics based on real-time Lambda events and pushes those metrics to Sysdig Monitor.
The normal way Lambda customers receive function metrics is by connecting Lambda to AWS CloudWatch. With the Sysdig Monitor Lambda Extension for AWS Lambda Telemetry API, customers can consume the most critical function execution metrics with an up to 85% reduction in metrics ingestion latency.
Read more about the new Sysdig Monitor Lambda Extension here.
Dashboard enhancements
- Minimum interval for PromQL Queries: You can now define a minimum interval for PromQL Queries, which is handy when working with scarce metrics. For more information, see Define Minimum Interval for PromQL Queries.
- Bulk delete dashboards: Dashboard Manager now gives you the ability to bulk delete dashboards. See Dashboard Manager.
Alert enhancements
When a metric stops reporting data, you now have the option to ignore or notify on the notification channel associated with the alert threshold.
Notification channels
Sysdig now allows you to refine which sections are used when sending Slack notifications. See Customize Notifications.
Monitoring integrations
Integrations
- Added the following integrations:
- OpenShift 4 Scheduler
- OpenShift 4 Controller Manager
- OpenShift 4 API Server
- OpenShift 4 Kubelet
- Azure Virtual Machines
- Azure Virtual Machine Scale Sets
- Enable OpenShift CoreDNS job
- Add support for OpenShift in Fluentd integration
- Update the postgresql-exporter and elasticsearch-exporter images with critical vulnerability fixes
Dashboards and Alerts
- Added openshift-api scopes in OpenShift v4 API Server Dashboard
- Added the minimum interval option in AWS MetricsStream dashboard templates
Sysdig Secure
Usability improvements for secure events
Link events to network activity, tuner, view rule
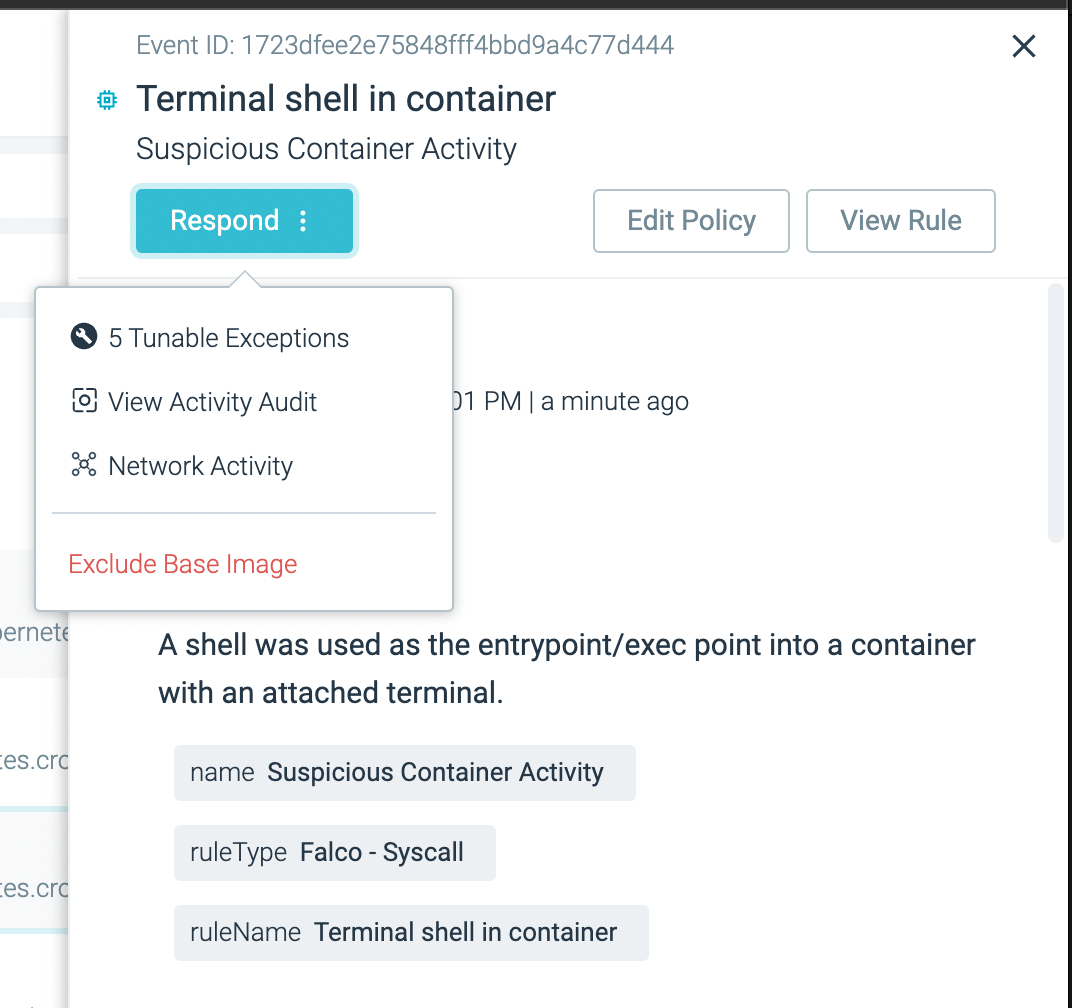
To help security investigators distinguish false positives from real issues, it can be helpful to review the associated network activity. We are adding a link to Sysdig's Network Topology visualization directly into relevant event details, under the Respond button.
Similarly, where applicable, the Runtime Policy Tuning feature will show up under the Respond button. The user can go through the flow to add exceptions and reduce false positives.
Finally, we've added the ability to view the rule definition from the event details panel. You can see the event details and the rule definition side-by-side.
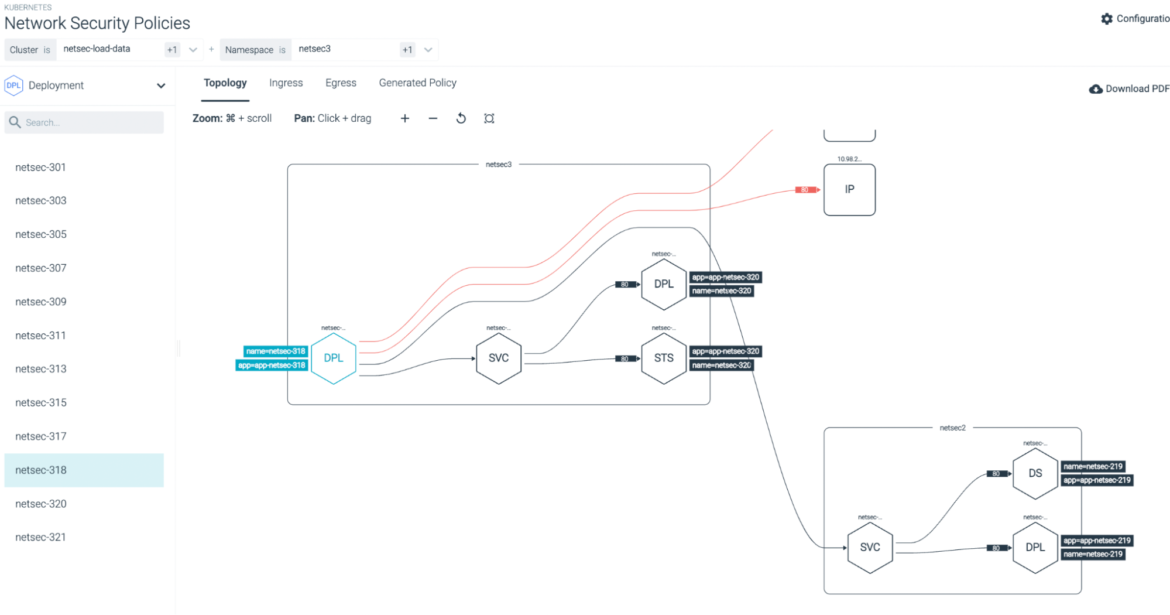
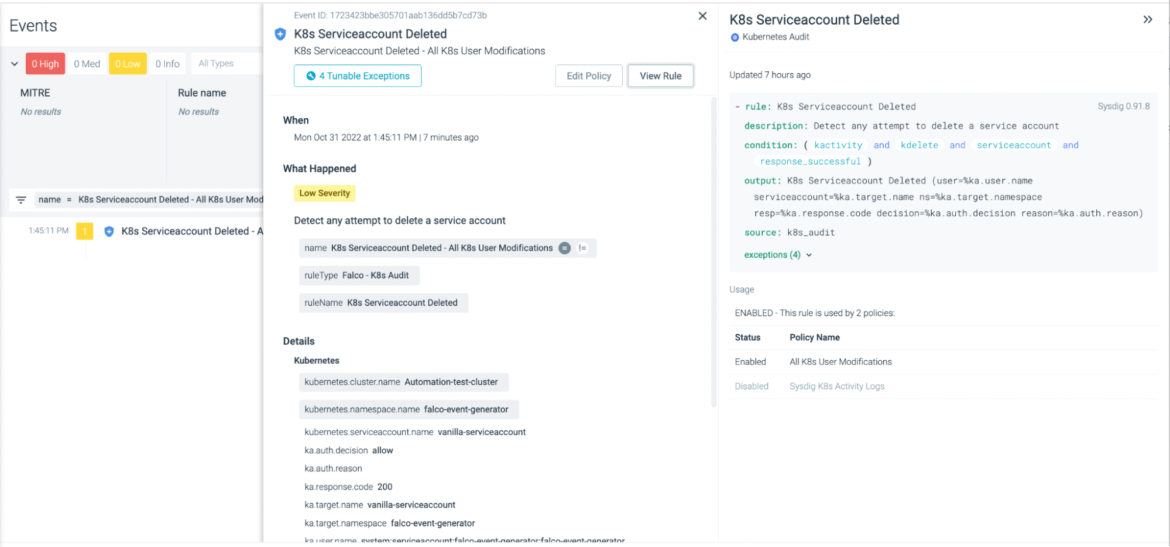
See the documentation for details.
Rule names added to event notifications
The notifications for runtime events have been enhanced to include a rule name. For email, Slack, and Microsoft Teams, the rule name will be a link to the rule definition.
New secure Event Forwarder integration: Google Security Command Center
A new integration has been released for Sysdig Secure's Event Forwarder functionality:
Google Security Command Center or SCC is a centralized vulnerability and threat reporting service that helps you strengthen your security posture and provide asset inventory and discovery.
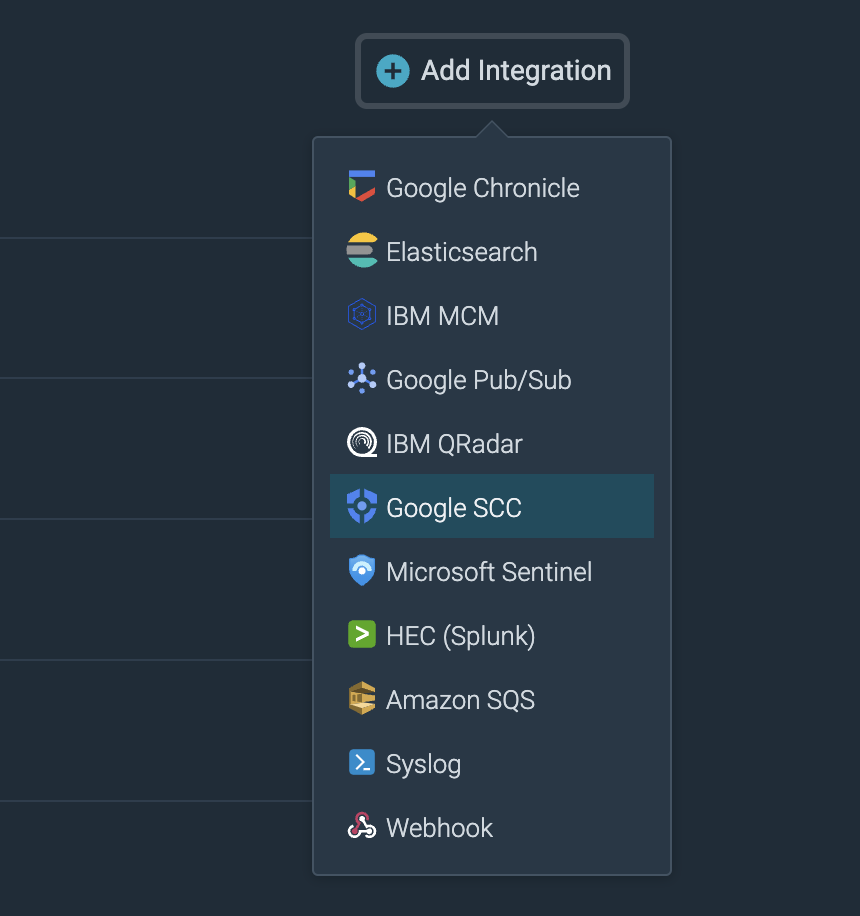
Falco rules
The Sysdig Threat Research Team has released one new rule this week for Secure.
Redirect STDOUT/STDIN to Network Connection in Host:
- This rule detects copying of STDIN/STDOUT file descriptors that are redirected to a new network connection. This rule is similar to the one we have been using for containers, but it's applied to hosts. It's used to detect reverse shells which are deployed by attackers to open a non-interactive shell in the compromised host/container and run arbitrary commands.
Lastlog Files Cleared:
- This rule came from commands seen in honeypot, and detects a deletion of lastlogs records by using the "lastlog" command or editing the lastlogs files. This technique is used by attackers to hide their presence or remove their traces.
Sysdig Agents
Agent updates
The latest Sysdig Agent release is v12.9.1. Below is a diff of updates since v12.9.0, which we covered in our October update.
Defect fixes
- Fix Legacy Proxy Connection Between Agent and Collector: The legacy mode of the proxy connection between the agent and the collector works as expected. You can continue to configure if need be.
- Fix Enriching Prometheus Metrics with Labels Periodically: Solved an issue where most labels would be dropped from Prometheus metrics every five minutes. This issue affects the Kubelet jobs associated with Prometheus Integrations, as well as the custom job configuration declared by the user.
- Fixed the following vulnerabilities:
- CVE-2022-42003
- CVE-2022-42004
- CVE-2022-40674
- CVE-2022-3515
Please refer to our v12.9.1 Release Notes for further details.
SDK, CLI and tools
Sysdig CLI
v0.7.14 is still the latest release. The instructions on how to use the tool and the release notes from previous versions are available at the following link:
https://sysdiglabs.github.io/sysdig-platform-cli/
Python SDK
v0.16.4 is still the latest release.
https://github.com/sysdiglabs/sysdig-sdk-python/releases/tag/v0.16.4
Terraform Provider
There is a new release v0.5.4.
- Fix: Falco rule, modify to not require condition when appending rule (#200)
- Feature: monitor alerts, support for alertV2 (#194)
- CI: add a target to install/uninstall the provider locally (#191)
Documentation – https://registry.terraform.io/providers/sysdiglabs/sysdig/latest/docs
GitHub link – https://github.com/sysdiglabs/terraform-provider-sysdig/releases/tag/v0.5.41
Terraform modules
- AWS Sysdig Secure for Cloud has been updated to v0.10.1
- GCP Sysdig Secure for Cloud remains unchanged at v0.9.4
- Azure Sysdig Secure for Cloud has been updated to v0.9.3
Note: Please check release notes for potential breaking changes
Falco vs. Code Extension
v0.1.0 is still the latest release.
https://github.com/sysdiglabs/vscode-falco/releases/tag/v0.1.0
Sysdig Cloud Connector
AWS Sysdig Secure for Cloud is unchanged. The current release is still v0.16.23.
AWS Sysdig Secure for Cloud
AWS Sysdig Secure for Cloud remains unchanged at v0.10.1.
Admission Controller
Sysdig Admission Controller has been updated to v3.9.12.
Documentation – https://docs.sysdig.com/en/docs/installation/admission-controller-installation/
Runtime Vulnerability Scanner
The new vuln-runtime-scanner has been updated to v1.2.13.
Documentation – https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/runtime
Sysdig CLI Scanner
Sysdig CLI Scanner remains at v1.2.10.
Documentation – https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/pipeline/
Image Analyzer
Sysdig Node Image Analyzer remains at v0.1.19.
Host Analyzer
Sysdig Host Analyzer remains at v0.1.11.
Documentation – https://docs.sysdig.com/en/docs/installation/node-analyzer-multi-feature-installation/#node-analyzer-multi-feature-installation
Sysdig Secure Online Scan for Github Actions
The latest release is still v3.4.0.
https://github.com/marketplace/actions/sysdig-secure-inline-scan
Sysdig Secure Jenkins Plugin
Sysdig Secure Jenkins Plugin is still v2.2.5.
https://plugins.jenkins.io/sysdig-secure/
Prometheus Integrations
The PromCat team officially released Prometheus Integrations v1.2.0!
Integrations:
- Feat: New integration. Azure Virtual Machine Scale Sets
- Sec: postgresql-exporter image Critical High vulnerabilities
- Sec: Updated elasticsearch-exporter image Critical High vulnerabilities
- Fix: Kube-scheduler and controller-manager jobs not available
- Fix: Kube-scheduler and controller-manager ports switched
- Fix: Added better details to HAProxy Ingress integration Prerequisites
Dashboards and alerts:- Feat: Added the minimum interval option in AWS MetricsStream dashboard templates
- Fix: Apply correct functions (rate vs, average) in Kubernetes dashboards
- Fix: Some Kubernetes Jobs panels have wrong PromQLs
- Fix: Scope not being applied in panel in pod rightsizing dashboard
Sysdig on-premise
Sysdig has released 5.1.4 Hotfix in November 2022
Secure
- Removed the Legacy Benchmarks button from the Secure UI. This feature is soon to be deprecated in on-premise deployments.
- Added the Shared with Team permission in Group Mappings to the ServiceManager role.
Defect fixes
- Fixed an issue when a scanned image would not correctly report a vulnerability detected the in kernel-headers package.
- Fixed a Secure scanning issue when an image was scanned by multiple sources (e.g.m Inline Scanner and Node Analyzer) and the UI would redirect the user to the incorrect source.
- Fixed a Team Scope issue in Secure when the agent.tag.accountid scope was configured and users could not see Host scanning results.
- Updated the Secure Only on-premise setting for the aggregation interval set to 60 seconds, helping reduce the number of "stream resetting" log warnings in the Sysdig backend.
The full release notes can be found here: Sysdig Docs or Github .
New website resources
Blogs
- CSPM – Least privilege principle in practice
- Detecting Cryptomining Attacks "in the Wild"
- Understanding Kubernetes Limits and Requests
- AWS recognizes Sysdig as an Amazon Linux 2022 Service Ready Partner
- How to Monitor Kubernetes API Server
- The Real Cost of Cryptomining: Adversarial Analysis of TeamTNT
- How to secure Helm
- Strengthen Cybersecurity with Shift-left and Shield-right Practices
- Announcing AWS Lambda Telemetry API Support for Sysdig Monitor
- Three multi-tenant isolation boundaries of Kubernetes
- How to deal with ransomware on Azure
- Does cloud log management shield you from threats? CloudTrail vs CloudWatch
- Using Sysdig Secure to Detect and Prioritize Mitigation of CVE 2022-3602 & CVE 2022-3786: OpenSSL 3.0.7
- How to monitor etcd
- Tales from the Kernel Parameter Side
- Responding to the Dropbox Breach with a Falco GitHub Plugin
- 5 Steps to Stop the Latest OpenSSL Vulnerabilities: CVE-2022-3602, CVE-2022-3786
- How the Critical OpenSSL Vulnerability may affect Popular Container Images
- The four Golden Signals of Kubernetes monitoring
- Sysdig Digs Deeper: Sysdig Ranked in the Top 100 Companies by Employees
- Container Image Scanning on Jenkins with Sysdig
- Should you put all your trust in the tools?
- Sysdig TRT uncovers massive cryptomining operation leveraging GitHub Actions
Webinars
- Getting Started With Sysdig's Enterprise Prometheus Service
- Kubernetes Security Best Practices: Image Builds and Container Execution
- Becoming a Cloud Security Ninja: Sharpen your Cloud Threat Detection Sword with Machine Learning
- Cloud Attacks Are Here: Threat Actors Like Containers Too!
Tradeshows
Education


