Welcome to the October edition of What’s New in Sysdig in 2022! I’m Tushar Kapadi, Sr. Solution Architect based out of the San Francisco Bay Area. I joined Sysdig a little over a year ago and it has been an exciting journey to say the least! I have worn many hats in my career, from Practice Manager to Software Developer and everything in between. I am excited to share some updates to What’s New in Sysdig for this month!
October has, as usual, been a busy month, and Sysdig announced many new features. In Sysdig Monitor, we announced the release of four new Advisories and Yaml config support for Advisor. In Sysdig Secure, we released Severity filtering in Insights, Pod and Node activity view in Insight and four new Falco rules added to the Rules Library. Each of these are discussed in detail below.
Platform
On-the-fly Group Mapping
On-the-fly mapping of group attributes coming from the identity provider/active directory to Sysdig Teams and Roles for the user. When a user logs in, Sysdig reads the group attribute and adds the user to the appropriate teams with the role(s) specified in the mapping.
For more information, see Group Mapping
Sysdig Monitor
4 new Advisories
There are 4 new Advisories added to the list:
- Cluster pod capacity – cluster is reaching pod capacity, when this happens new pods cannot be scheduled.
- Replicas unavailable – a workload has unavailable replicas which can affect app availability
- Cluster CPU overcommitment – cluster is overcommitting CPU which may affect availability
- Cluster memory overcommitment – cluster is overcommitting memory which may affect availability
For more information, see Advisor
YAML Configuration support for Advisor
Advisor can display the YAML configuration for pods, which is the equivalent of running kubectl get pod <pod> -o yaml. This is useful to see the applied configuration of a pod in a raw format, as well as metadata and status.
For more information, see YAML Configuration
Define Minimum Interval for PromQL Queries
When working with PromQL queries you can use the $__interval variable and Sysdig will apply the most appropriate sampling corresponding to the time range you have selected. Sometimes you might have some metrics that report data with a coarser granularity and you want to apply an interval that is higher than the proposed
For example, if you have a metric that reports data every 3m, and you have selected the 1h preset in the time navigation, the $__interval will be replaced with a time duration of 10s. This will result in time charts with isolated data points instead of lines.
For more information, see Define Minimum Interval
Configurable Slack Notification Sections
We are giving end users the ability to customize sections used when sending Slack notifications. We came up with an awesome design that lets users easily visualize the final notification while they configure sections.
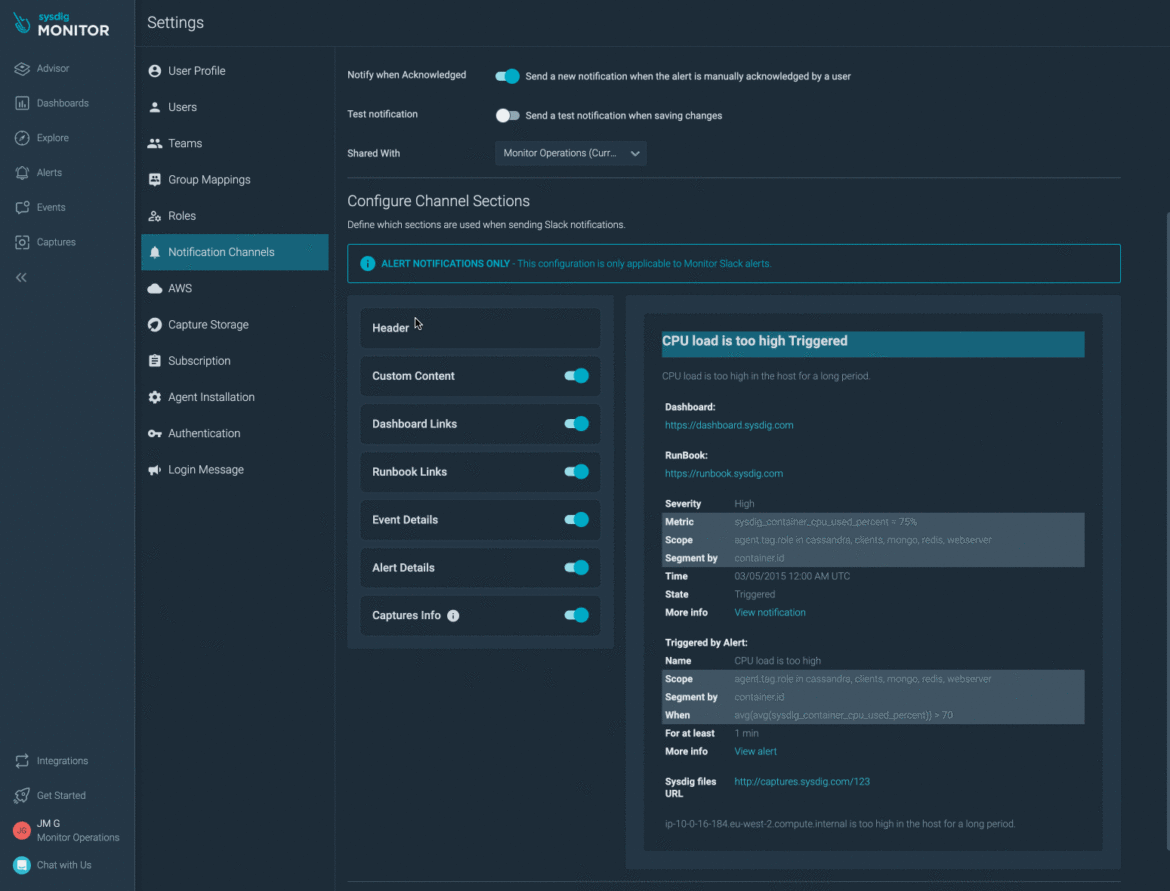
For more information, Slack Notifications
Sysdig Secure
Insights – Severity Filtering
Events shown on the Insights page can now be filtered by severity. The will load the first 999 events of the selected severities over the previous two weeks, and subsequent event loading will continue based on the filter.
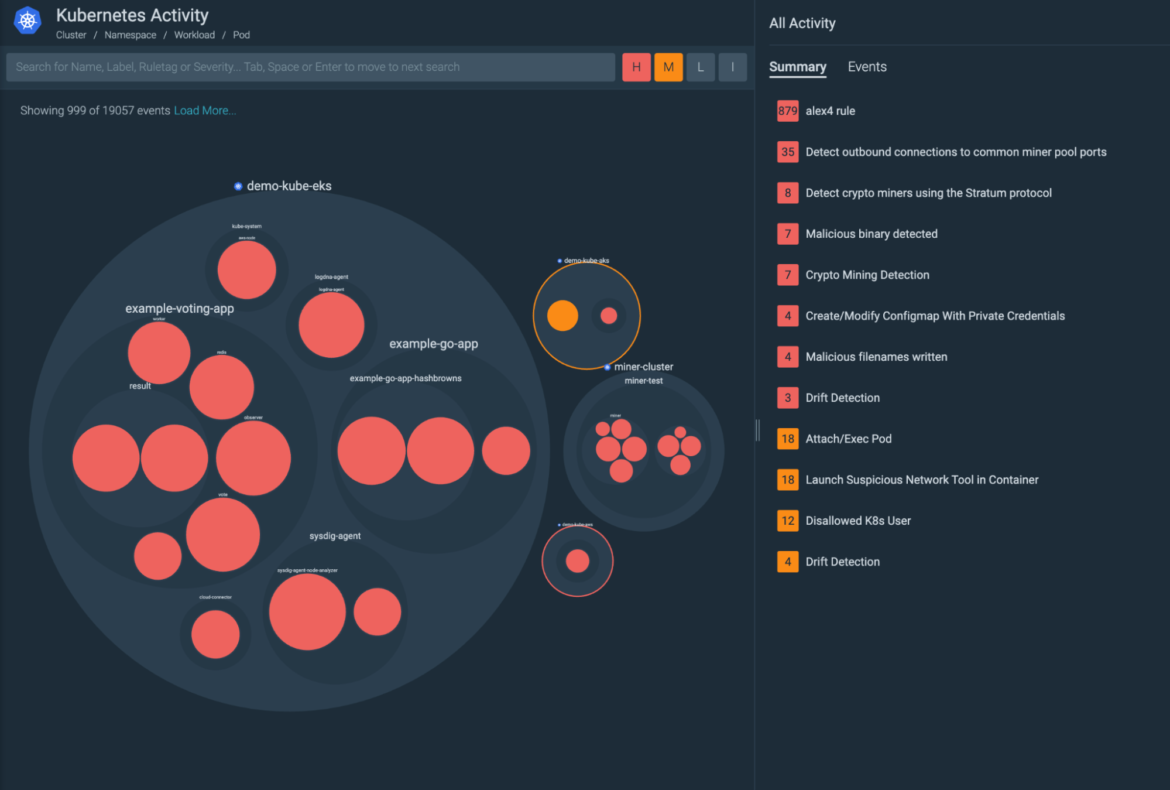
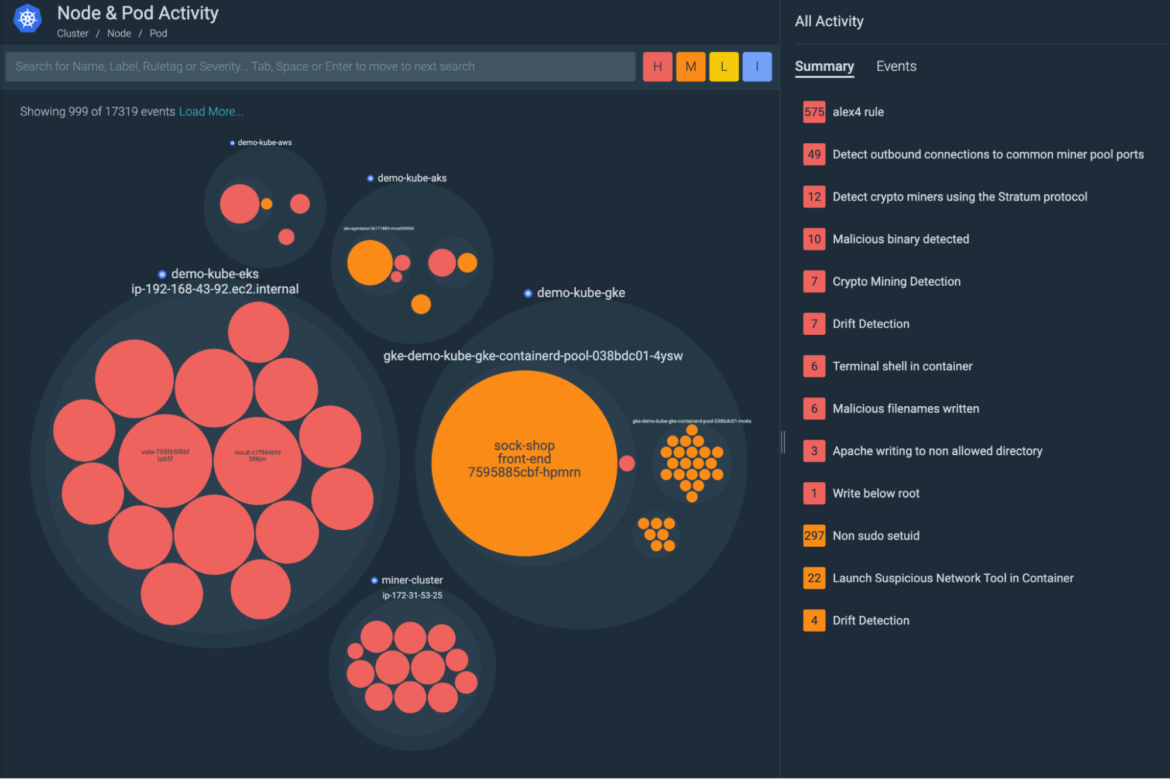
Insights – Node & Pod Activity View
This new view focuses on the physical boundaries of nodes in a cluster and will be able to show activity happening outside of the Kubernetes logical boundaries, while at the same time showing the Kubernetes context.
Highlighting New Rules in Managed Policies
New rules created by the Sysdig Threat Research Team will be added to Managed Policies. A new icon will show policies that have been updated with new rules in the last seven days, and will highlight the rule that was added.

Falco Rules
v0.90.0 is the latest version. Here there are some highlights of the changes from v0.85.0, which we covered in September:
Added the following rules:
- Diamorphine Rootkit Activity
- This rule detects Diamorphine activities which is a loadable kernel module (LKM) rootkit for Linux kernels. It’s used and designed to obtain higher privileges on processes and hide malicious activities. This tool has been used in recents real-world attacks monitored in the wild.
- Dump memory for credentials
- This technique was seen in malwares and consists of searching in maps or mem files (stored inside of processes folders) to find credentials in plaintext. The condition is raced when a process like grep, find or cat tries to open files in maps or mem folders (usually stored in paths like /proc/proc_number/) and for sure can be an indicator of compromise.
- Kill known malicious process
- Attackers try to kill known malicious processes in order to gain complete control of the machine or remove executions started by previous infections/attacks. These commands are usually executed during the first phases of attack. The process list is constantly updated when new malicious process names will be found.
- Unexpected Connection from legitimate Process/Port
- This rule detects a process (or its parent) generating unexpected network connections. The use case started from a recent malware (VIRTUALPITA) targeting VMware VSphere where the ksmd process exploited to open a port and get remote code execution, file transfer or service management. At the moment the rule detects only this specific use case but we are going to update the detection use cases that use this technique will be found. Customers can only add their own process if they want to monitor specific processes in their environment.
Further details and the full changelog can be found on Sysdig documentation.
Sysdig Agents
Agent Updates
The latest Sysdig Agent release is v12.9.0. Below is a diff of updates since v12.8.1, which we covered in our September update.
Feature Enhancements
- Add new KSM Metrics
- Send Node Resource Metrics
- Upgrade Vulnerable Go Packages in Promscrape V1
- Retry CRI API Calls After Failed Async Attempts
- Add Error Traces when Open SSL Connection Fails
- Report Taint Information for Kubernetes Nodes
Known Issues
- The s390x architecture image is not available for v12.9.0; therefore, this version of the agent cannot be installed in zLinux. Note that using the
latesttag for agent images on zLinux will not work until the next agent version is released.
Defect Fixes
- Restarting Agent No Longer Causes Kernel Panic
- Support Arbitrary Java Command Names
- Captures Are No Longer Corrupted in Few Hosts
- Report Containers as Expected
- Upgrade
psycopg2Module - Build Kernel Modules on RHEL6
- Stop Reporting Unschedulable Pods
- Initialize Agent on Latest Kernels
- Disable the Policy Scope Cache
- Update kube-bench and kubectl Binaries
- Show Correct Output Message in the Launch Sensitive Mount Container Rule
- Show Required Secure Event Output Fields in Custom Rules
Please refer to our v12.9.0 Release Notes for further details.
SDK, CLI, and Tools
Sysdig CLI
v0.7.14 is still the latest release. The instructions on how to use the tool and the release notes from previous versions are available at the following link:
https://sysdiglabs.github.io/sysdig-platform-cli/
Python SDK
v0.16.4 is still the latest release.
https://github.com/sysdiglabs/sysdig-sdk-python/releases/tag/v0.16.4
Terraform Provider
v0.5.40 is still the latest release.
Documentation – https://registry.terraform.io/providers/sysdiglabs/sysdig/latest/docs
Github link – https://github.com/sysdiglabs/terraform-provider-sysdig/releases/tag/v0.5.40
Terraform Modules
- AWS Sysdig Secure for Cloud has been updated to v0.1.0
- GCP Sysdig Secure for Cloud has been updated to v0.9.4
- Azure Sysdig Secure for Cloud has been updated to v0.9.2
Note: Please check release notes for potential breaking changes
Falco vs. Code Extension
v0.1.0 is still the latest release.
https://github.com/sysdiglabs/vscode-falco/releases/tag/v0.1.0
Sysdig Cloud Connector
AWS Sysdig Secure for Cloud has a new release! v0.16.19 includes new features and some minor fixes.
Features include:
- New registry scanner for Elastic Container Registry
- Toggle feature for brute force detection
- GuardDuty Ingestor
Check the full list of changes to get the full details.
AWS Sysdig Secure for Cloud
AWS Sysdig Secure for Cloud has been updated to v0.10.1.
Features include:
- Required use of Terraform 1.3 starting with v0.10.0
- Work-in-progress support for ECR scanning
Check the full list of changes for details.
Admission Controller
Sysdig Admission Controller has been updated to v3.9.8.
Documentation – https://docs.sysdig.com/en/docs/installation/admission-controller-installation/
Runtime Vulnerability Scanner
The new vuln-runtime-scanner has been updated to v1.2.13.
Documentation – https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/runtime
Sysdig CLI Scanner
Sysdig CLI Scanner has been released to v1.2.10.
Documentation – https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/pipeline/
Image Analyzer
Sysdig Node Image Analyzer is still set to v0.1.19.
Host Analyzer
Sysdig Host Analyzer has been updated to v0.1.11.
Documentation – https://docs.sysdig.com/en/docs/installation/node-analyzer-multi-feature-installation/#node-analyzer-multi-feature-installation
Sysdig Secure Inline Scan for Github Actions
The latest release is still v3.4.0.
https://github.com/marketplace/actions/sysdig-secure-inline-scan
Sysdig Secure Jenkins Plugin
Sysdig Secure Jenkins Plugin is still v2.2.5.
https://plugins.jenkins.io/sysdig-secure/
Prometheus Integrations
The PromCat team officially released Prometheus Integrations v1.0.0!
Integrations:
- Feat: Add description text to integration jobs
- Feat: Add support in Fluentd for OpenShift
- Feat: Create Troubleshooting text for Istio and Istio-envoy integrations
- Feat: New integrations – OpenShift Control Plane
- Fix: Edit AWS MetricStreams panels to show solid line on gap always
- Fix: kafka-service in wizard should be a textToList so the customer can enter more than one Kafka service
Dashboards and alerts:
- Fix: Change query in the Nginx Ingress Template
- Fix: Typo in dashboard template for Kubernetes Controller Manager
Promcat.io and Promotion
- Fix: AWS RDS LongCPUThrottling wrong value in Alerts
Sysdig On-Premise
Sysdig has released 5.1.3 Hot Fix September 2022
Bugs fixed
- Fixed an Elasticsearch issue occurred during upgrades that could result in pods ending in a CrashLoopBackOff state. This fix will overall improve Elasticsearch resiliency for users
The full release notes can be found here: Sysdig Docs or Github .
New Website Resources
Blogs
- Building honeypots with vcluster and Falco: Episode I
- Kubernetes ErrImagePull and ImagePullBackOff in detail
- Extract maximum value from your Microsoft Sentinel SIEM with Sysdig Secure
- How to detect MFA spamming with Falco
- Preventing DoS attacks in Kubernetes using Falco and Calico
- Image scanning for GitLab CI/CD
- How to monitor Istio with Sysdig
- How to monitor Istio, the Kubernetes service mesh
- Cost Advisor: Optimize and Rightsize your Kubernetes Costs
- Detecting and mitigating CVE-2022-42889 a.k.a. Text4shell
Webinars
- Oct 20 – Is Your SecOps Ready for Cloud and Containers?
- Oct 25 – Not your Parent’s Cloud Security: Real-time Cloud Threat Detection for GCP
- Nov 1st – Getting Started With Sysdig’s Enterprise Prometheus Service
- Nov 29 – ThreatQuotient and Sysdig Webinar
Tradeshows
Education


