As container adoption in AWS takes off, ECR scanning is the first step towards delivering continuous security and compliance. You need to ensure you are scanning your images pulled from AWS ECR for both vulnerabilities and misconfigurations so that you can avoid pushing applications running on AWS that are exploitable.
Sysdig Secure embeds security and compliance across all stages of the Kubernetes lifecycle. Leveraging 15+ threat feeds, Sysdig Secure provides a single workflow to detect vulnerabilities and security or compliance-related misconfigurations.
Understanding Image Scanning
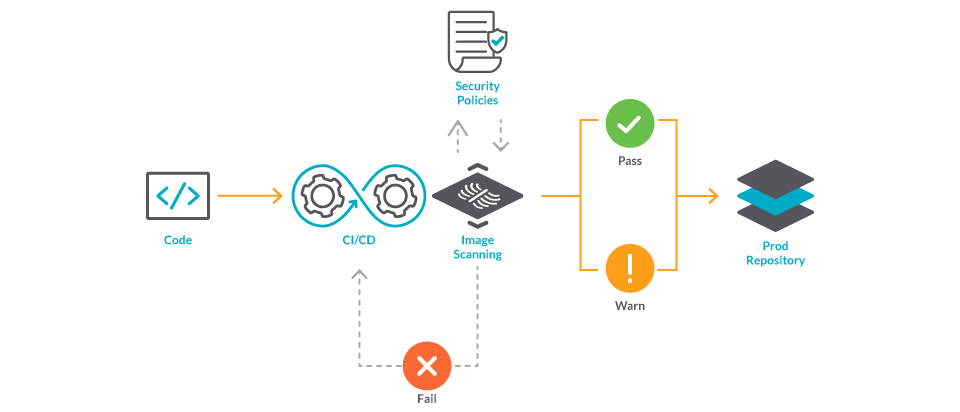
Image scanning refers to the process of analyzing the contents and the build process of a container image in order to detect security issues, vulnerabilities, or bad practices. There are several ways to leverage image scanning depending on the use case:
- Integrate scanning into development lifecycle: As your teams build applications, Sysdig prevents vulnerable images from being pushed through your CI/CD pipelines (Jenkins, Bamboo, Gitlab, or AWS CodePipeline) and identifies new vulnerabilities in production. Sysdig Secure is part of the Sysdig Secure DevOps Platform, which lets you confidently run cloud-native workloads in production. This is primarily requested by development teams.
- You can also launch inline scanning manually: Read more in the official documentation or have a look at some examples. This is mostly used by security operators. It is also possible to trigger backend scanning manually for images hosted in ECR or any V2 registry by using the “Scan Image” button (this is the old fashioned way and it is not recommended anymore).
- If you are using AWS ECR, you can get automatic image scanning on push so that any image is secured from the very first step, when it is being inserted. This is the way we are going to explain in this article.
If you would like to know more about image scanning, we strongly recommend following the best practices.
AWS ECR scanning with Sysdig Secure

Amazon Elastic Container Registry (ECR) is a fully-managed Docker container registry that makes it easy for developers to store, manage, and deploy Docker container images. Amazon ECR is integrated with AWS container services like ECS and EKS, simplifying your development to production workflow.
Sysdig Secure provides additional ECR scanning capabilities on top of ECR default image scanning based Clair, such as scanning for non-OS vulnerabilities (3rd party libraries), misconfigurations, and compliance checks.
You only need to deploy Sysdig Secure for Cloud on your AWS account, either by using Cloud Formation Templates or Terraform, and it will provide ECR scanning integration out-of-the-box without needing to add any address or credential manually. You can read more about ECR integration in the official documentation.
After the installation, you can check that your services have been correctly installed by reviewing this checklist on how to know that your services are working.
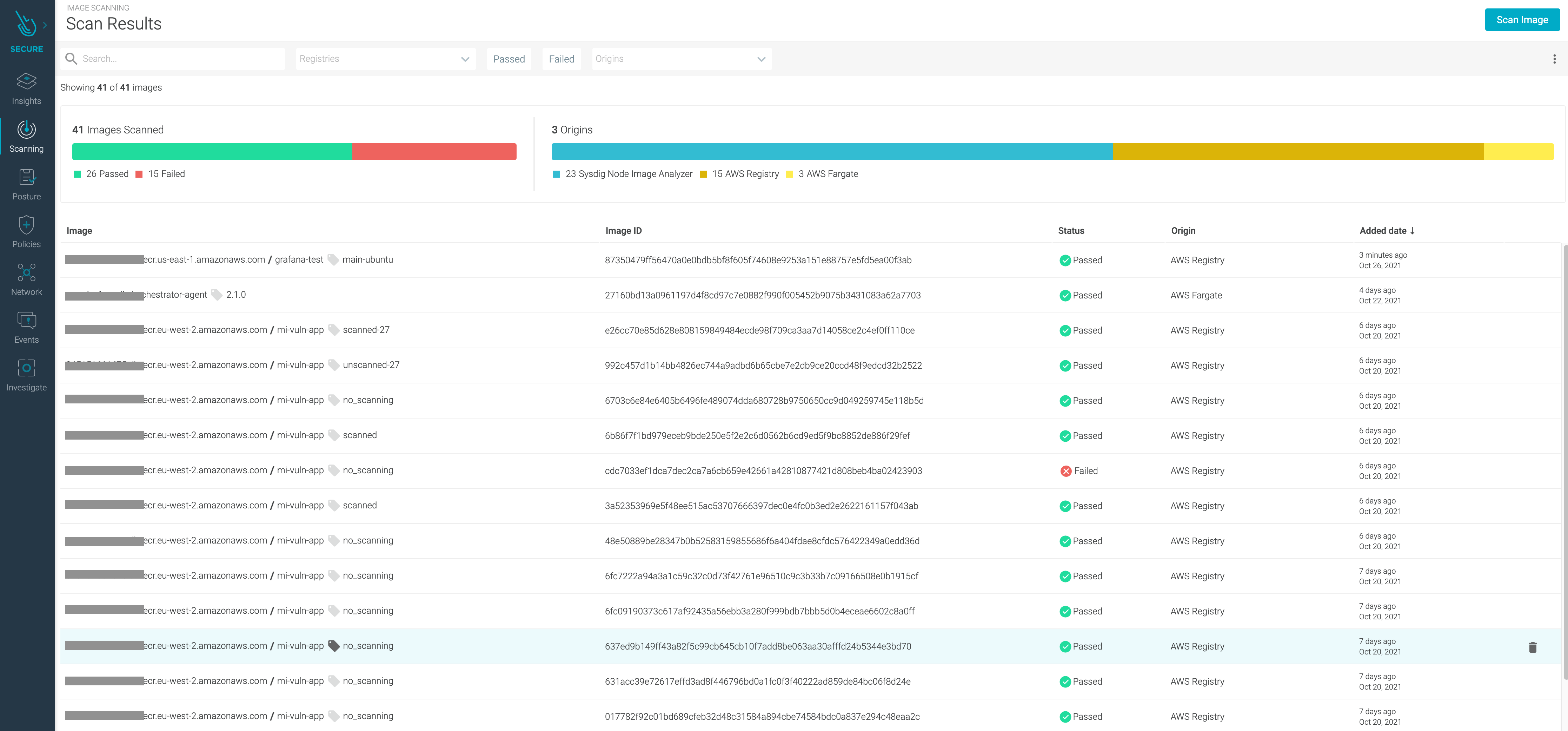
Next time an image is pushed into any of your ECR registries, it will be scanned automatically, providing visibility into:
- Official OS package vulnerabilities
- Configuration checks:
- Exposing SSH in a Dockerfile.
- Users running as root
- Vulnerabilities in 3rd party libraries:
- Javascript NPM modules.
- Python PiP.
- Ruby GEM.
- Java JAR archives.
- Secrets, credentials like tokens, certificates, and other sensitive data
- Known vulnerabilities & available updates.
- Metadata: Size of an image among others.
- Compliance checks for several frameworks:
These artifacts are then stored and evaluated against custom scanning policies that can be specified to a particular registry, repository, or image tag. These policies help detect vulnerabilities, misconfiguration, or compliance issues within your images and generate pass/fail results directly in the UI.
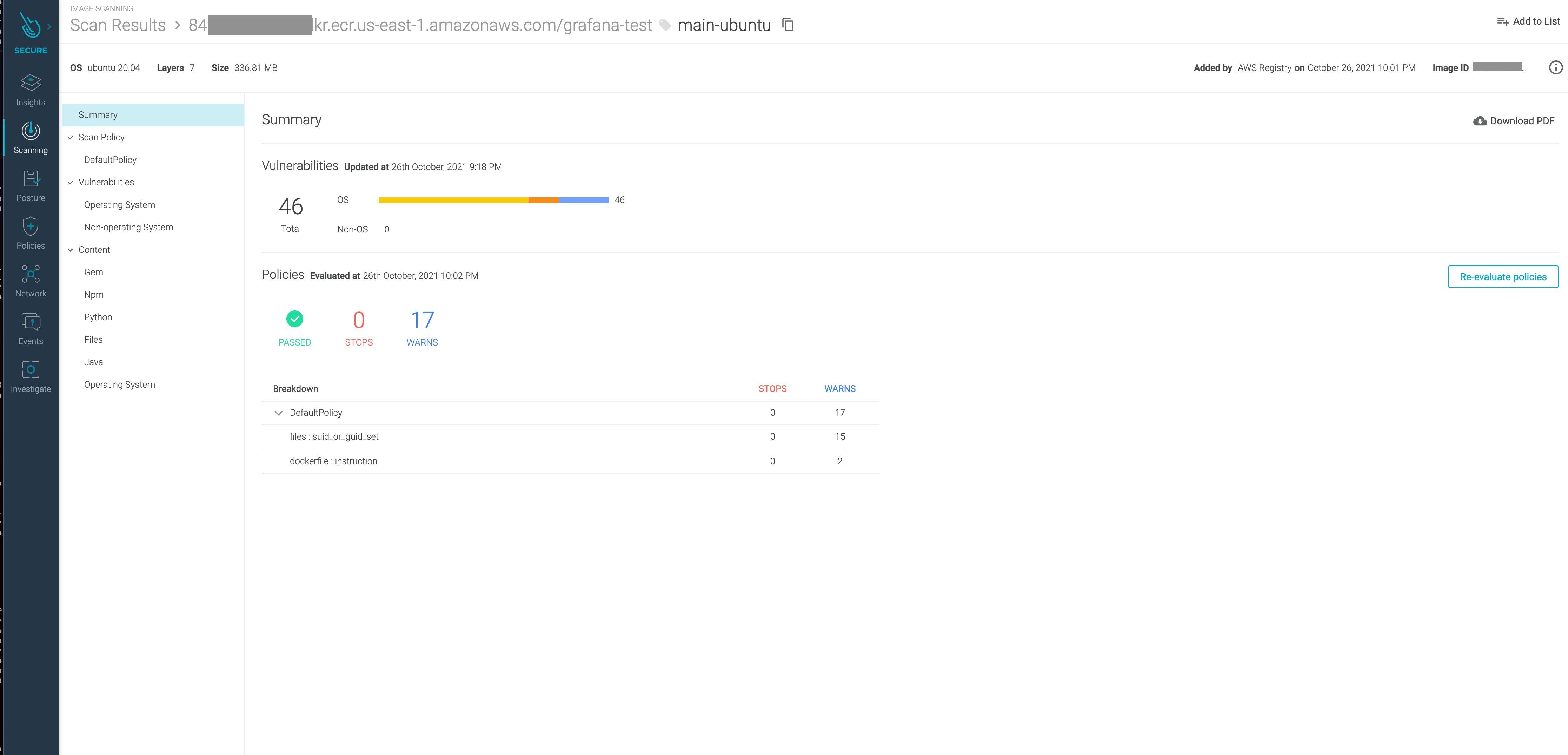
The report provides any OS/non-OS vulnerabilities discovered in detail. For each vulnerability discovered, Sysdig Secure shows the package version that it found in the image (which is affected by that vulnerability), and it also shows the version number that includes the fix for that issue.
To remove the vulnerability, you’ll need to rebuild the container image to include a version of that package that has a fix available.
For example, the affected package might be in the base image itself. In this case, it is best to update the base images directly. In other cases, the package might be installed on top of the base image by a command in the Dockerfile. For example, it’s common to see package manager commands like apt or yum specified in the Dockerfile. If these specify the version of the affected package, you’ll need to edit the Dockerfile.
Now that we have discussed ECR scanning, let us talk about ECR vulnerability reporting and ECR vulnerability alerting.
AWS ECR vulnerability reporting and alerting
Application security teams often need to ensure they address any high severity CVE with a fix within 30 days.
With Sysdig Secure, you can help bring traditional patch management processes to containers. Teams can set up policies for vulnerability reporting both in ECR and/or running in a particular AWS cluster or region. You can then query for specific vulnerabilities by advanced conditions like CVE ID, severity, fix, age or any other criteria.
For example, if new CVE has been announced, you may want to report on images in ECR that are vulnerable because of it:
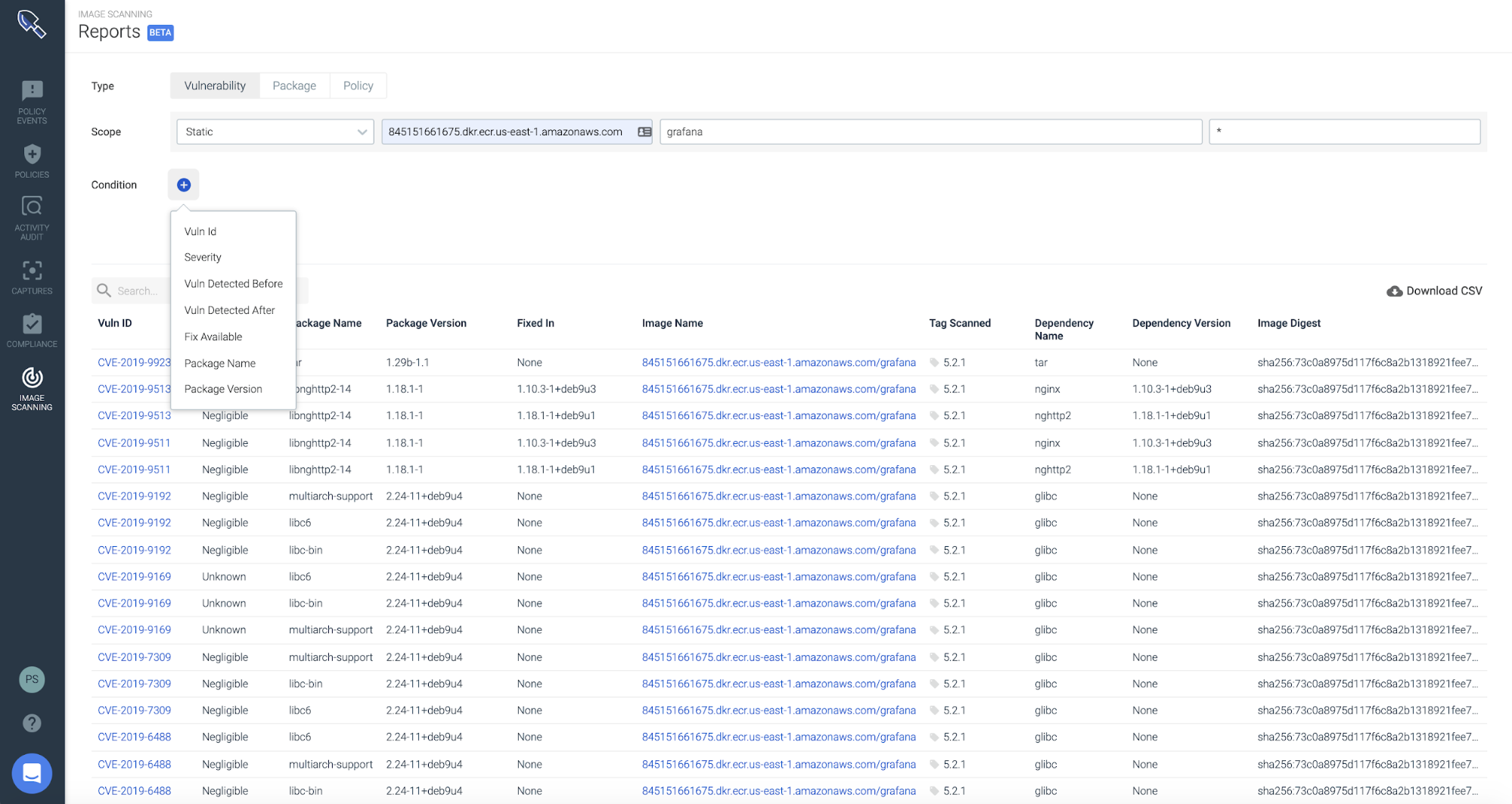
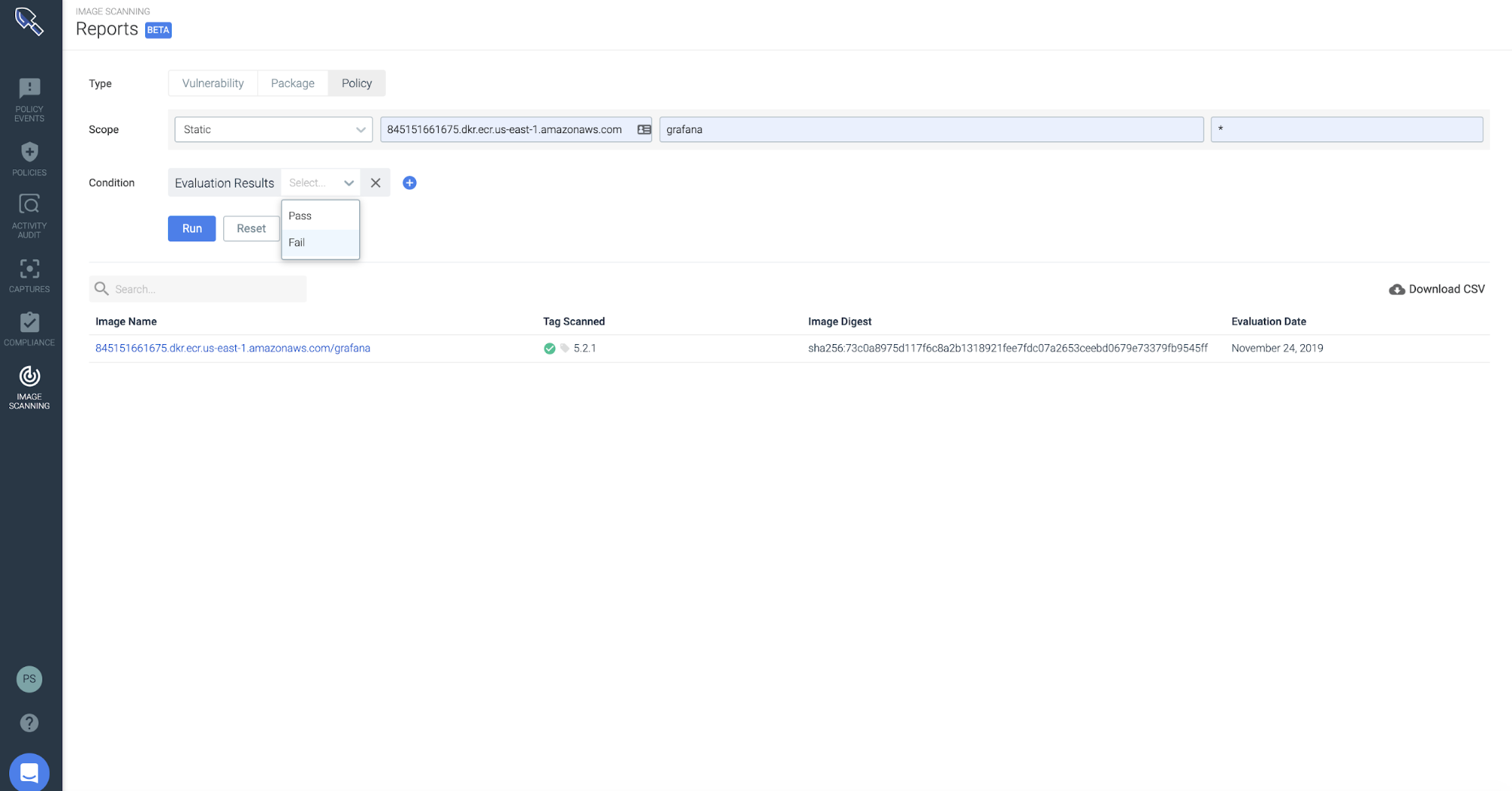
After scanning the images currently in ECR, the next question typically is what were the image scanning results for all the builds in the past for that service? Vulnerability management teams need reports on all the scans that have happened against a specific repo over time in ECR.
With Sysdig Secure, you can query by policy and apply a specific scope that answers your question with less than 3 clicks:
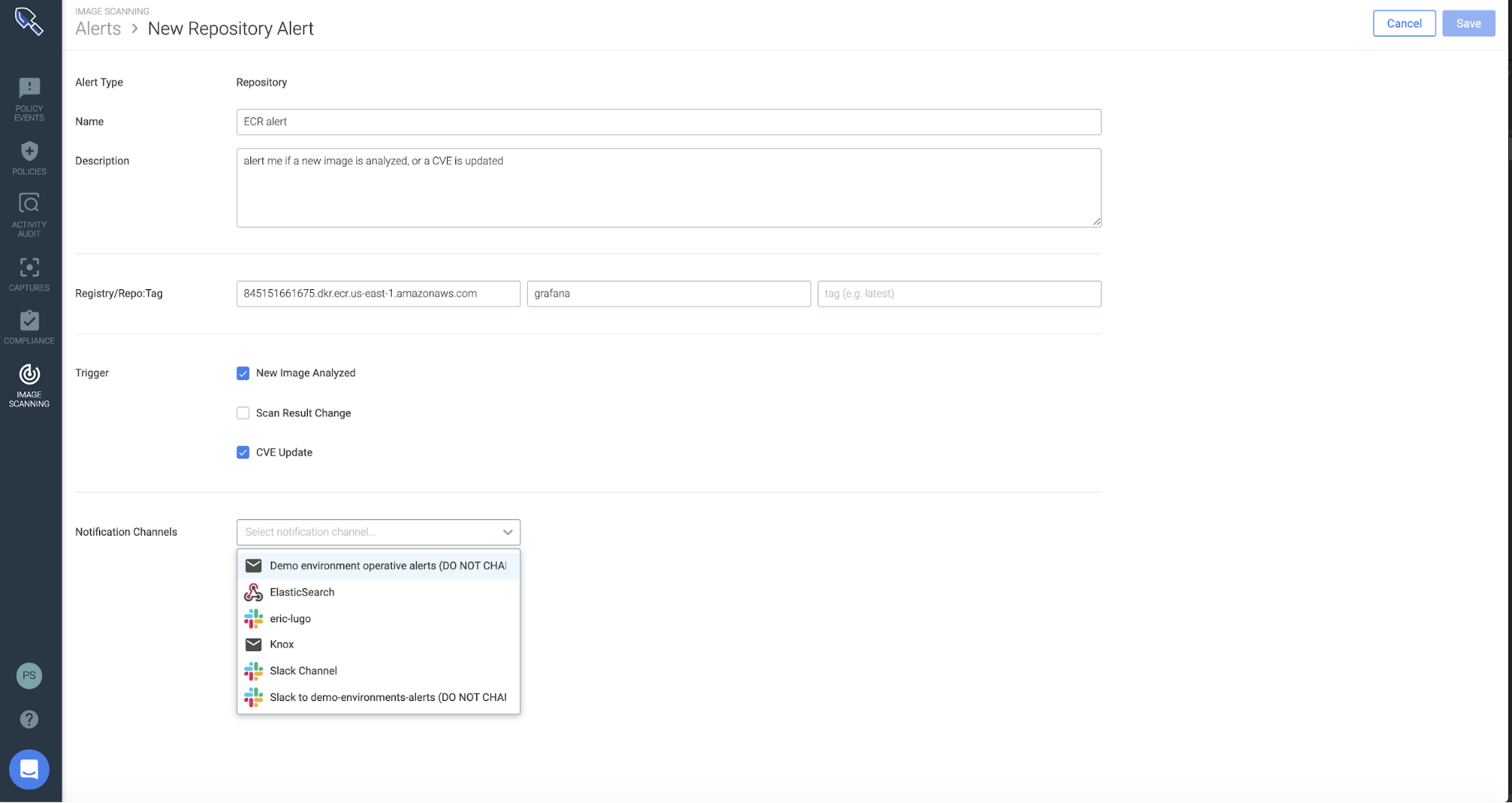
Finally, it is easy to set up vulnerability alerting for ECR. You can set alerts for your team if a new image is analyzed in ECR or a CVE gets an updated score. You can create downstream notifications via Slack, AWS SNS, etc. or create your own custom webhooks to take specific actions.
Conclusion
Hopefully you see how easy it is to get up and running with both AWS Elastic Container Registry and Sysdig Secure. You can also dig deeper into Sysdig’s container and Kubernetes image scanning capabilities or read more about how Sysdig extends security services across various AWS container services (EKS, ECS)
Or go to www.sysdig.com and contact us for a custom demo!


