Sysdig maintainers are thrilled to announce the latest release of our beloved OSS tool for analyzing and/or recording the activity of processes and containers on a Linux system.
You can find the full CHANGELOG in the GitHub repository, but here are some highlighted features:
- Plugin Support
- Colors for outputs
- Podman Support
- New flag
proc.is_exe_writableadded to filtering options - New syscalls:
mprotect,execveat,copy_file_range,clone3
Note: The 0.29.1 has been released with a bug fix shortly after we started to write this post.
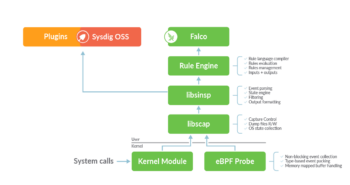
Plugins
This release brings a big new feature. Following the latest releases of Falco, Sysdig OSS is now able to use Plugins.
The same plugins used by Falco can now be also used for extending the inputs of Sysdig OSS. Plugins help to add new event sources that can be evaluated using filtering expressions/Falco rules and the ability to define new fields that can extract information from events.
Installation
First of all, if you haven’t installed Sysdig OSS yet, here are the instructions to start using it in your favorite Linux OS.
Once installed, download the plugin you need from the plugin registry or elsewhere and install it in /usr/share/sysdig/plugins following these steps:
mkdir -p /usr/share/sysdig/plugins cd /tmp wget https://download.falco.org/plugins/stable/dummy-0.2.0-x86_64.tar.gz tar xvzf dummy-0.2.0-x86_64.tar.gz mv libdummy.so /usr/share/sysdig/plugins/
To verify the plugin is correctly deployed, you can run the following command:
$ sysdig -Il Plugin search paths are: /usr/share/sysdig/plugins/ 1 Plugins Loaded: Name: dummy Description: Reference plugin for educational purposes Contact: github.com/falcosecurity/plugins Version: 0.2.0 ... output ommited ...
Configuration file
To enable plugins, you can either use a Falco plugin configuration file or pass arguments to your command line.
Here’s an example of a config file for the dummy plugin to generate 10 synthetic events to briefly test our plugin framework:
plugins:
- name: dummy
library_path: /usr/share/sysdig/plugins/libdummy.so
init_config:
jitter: 10
open_params: ''{"start":1, "maxEvents": 10}''
load_plugins: [dummy]
To use this configuration file, just use the option --plugin-config-file followed by the filename you have created containing the configuration.
$ sysdig --plugin-config-file dummy-config.yaml
1 2022-04-01 13:00:09 [dummy] {"sample": "2"}
2 2022-04-01 13:00:10 [dummy] {"sample": "6"}
3 2022-04-01 13:00:10 [dummy] {"sample": "11"}
... output omitted ...
For more details about how to use and configure plugins, see the plugin section in Falco docs.
Command line configuration
As an alternative, you can use the options -H and/or -I in the command line to configure a plugin as follows:
$ sysdig -H dummy:'{"jitter":50}' -I dummy:'{"start":1,"maxEvents":10}'
These two new options are now available for that purpose:
-Hto manually register a: plugin_nameplugin (a path is also supported!), passing the specifiedinit_configas a JSON string-Ito set the: plugin_nameplugin as input plugin, passing to itopen_paramsas a JSON string
See --help for more details about the usage.
When no plugin is manually registered, any found plugin in system directories is automatically registered.
You need to set both arguments -H and -I when you manually register a plugin.
A quick and final test with the dummy plugin would resemble this output:
$ sysdig -I dummy:'{ "init_config": 1, "maxEvents": 3}'
1 2022-04-01 13:00:15 [dummy] {"sample": "5"}
2 2022-04-01 13:00:15 [dummy] {"sample": "8"}
3 2022-04-01 13:00:15 [dummy] {"sample": "9"}
Example
Let’s now try a more useful example, the docker plugin.
First, install it:
mkdir -p /usr/share/sysding/plugins/ cd /tmp wget https://github.com/Issif/docker-plugin/releases/download/v0.1.0/docker-plugin_0.1.0_linux_amd64.tar.gz tar xvzf docker-plugin_0.1.0_linux_amd64.tar.gz cp libdocker.so /usr/share/sysding/plugins/
Run Sysdig with a similar syntax to this one:
$ sysdig -H docker:'{"flushinterval": 10}' -I docker:'{}'
In a different terminal, start a docker container:
$ docker run -ti docker.io/alpine sh
We mentioned that Sysdig OSS natively supports Podman containers. However, this plugin in particular has been developed to interact with Docker events.
You should obtain an output similar to:
1 2022-03-30 19:25:32 [docker] {"status":"create","id":"e2ede0ab2e274e98203baf2cbde76ce576452462611cb62b02b799916fc4aede","from":"alpine","Type":"container","Action":"create","Actor":{"ID":"e2ede0ab2e274e98203baf2cbde76ce576452462611cb62b02b799916fc4aede","Attributes":{"image":"alpine","name":"stoic_goldberg"}},"scope":"local","time":1648661132,"timeNano":1648661132044628389}
2 2022-03-30 19:25:32 [docker] {"status":"attach","id":"e2ede0ab2e274e98203baf2cbde76ce576452462611cb62b02b799916fc4aede","from":"alpine","Type":"container","Action":"attach","Actor":{"ID":"e2ede0ab2e274e98203baf2cbde76ce576452462611cb62b02b799916fc4aede","Attributes":{"image":"alpine","name":"stoic_goldberg"}},"scope":"local","time":1648661132,"timeNano":1648661132046127121}
3 2022-03-30 19:25:32 [docker] {"Type":"network","Action":"connect","Actor":{"ID":"a46db2080f7217fd5ff95064227d7f46a160c7217e9b43a566d8778792bc6ab2","Attributes":{"container":"e2ede0ab2e274e98203baf2cbde76ce576452462611cb62b02b799916fc4aede","name":"bridge","type":"bridge"}},"scope":"local","time":1648661132,"timeNano":1648661132157630105}
4 2022-03-30 19:25:32 [docker] {"status":"start","id":"e2ede0ab2e274e98203baf2cbde76ce576452462611cb62b02b799916fc4aede","from":"alpine","Type":"container","Action":"start","Actor":{"ID":"e2ede0ab2e274e98203baf2cbde76ce576452462611cb62b02b799916fc4aede","Attributes":{"image":"alpine","name":"stoic_goldberg"}},"scope":"local","time":1648661132,"timeNano":1648661132462006264}
5 2022-03-30 19:25:32 [docker] {"status":"resize","id":"e2ede0ab2e274e98203baf2cbde76ce576452462611cb62b02b799916fc4aede","from":"alpine","Type":"container","Action":"resize","Actor":{"ID":"e2ede0ab2e274e98203baf2cbde76ce576452462611cb62b02b799916fc4aede","Attributes":{"height":"37","image":"alpine","name":"stoic_goldberg","width":"294"}},"scope":"local","time":1648661132,"timeNano":1648661132464329983}
We can also format the output to suit our needs:
sysdig -H docker:'{"flushinterval": 10}' -I docker:'{}' \
-p 'time=%evt.time status=%docker.status
from=%docker.from type=%docker.type
action=%docker.action name=%docker.attributes.name'
time=19:27:34.310497000 status=create from=alpine type=container action=create name=zen_ellis
time=19:27:34.312382000 status=attach from=alpine type=container action=attach name=zen_ellis
time=19:27:34.433546000 status= from= type=network action=connect name=bridge
time=19:27:34.736048000 status=start from=alpine type=container action=start name=zen_ellis
time=19:27:34.736200000 status=resize from=alpine type=container action=resize name=zen_ellis
Or even write/read data captures:
sysdig -H docker:'{"flushinterval": 10}' -I docker:'{}' \
-w /tmp/docker.scap
sysdig -H docker:'{}' -I docker:'{}' \
-r /tmp/docker.scap \
-p 'time=%evt.time status=%docker.status
from=%docker.from type=%docker.type
action=%docker.action name=%docker.attributes.name'
time=19:30:19.100057000 status=die from=alpine type=container action=die name=zen_ellis
time=19:30:19.233340000 status= from= type=network action=disconnect name=bridge
time=19:30:20.358480000 status=create from=alpine type=container action=create name=practical_carver
time=19:30:20.358486000 status=attach from=alpine type=container action=attach name=practical_carver
time=19:30:20.470413000 status= from= type=network action=connect name=bridge
time=19:30:20.755902000 status=start from=alpine type=container action=start name=practical_carver
time=19:30:20.755915000 status=resize from=alpine type=container action=resize name=practical_carver
Conclusion
Thanks to plugins, Sysdig OSS now allows you to analyze a diverse number of event sources in the same way Falco does to protect your infrastructure, either on-premise or in the Cloud.
Falco is setting the path for a whole new ecosystem where a varied number of tools are leveraging Falco’s core functionality to achieve one common goal: to detect threats sooner and more efficiently.
Learn more about Sysdig’s Open Source Journey here.
Is your project not yet analyzed by Sysdig OSS or Falco? Propose a plugin for it! Follow our resources for helping you:


