
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

"What's New in Sysdig" is back with the March and April 2023 edition! Happy International Women's Day! Happy St. Patrick's Day! Ramadan Mubarak! Happy Easter! And we hope you had an excellent Kubecon in Amsterdam! We are Gonzalo Rocamador, Enterprise Sales Engineer based in Spain, and Parthi Sriivasan, Sr. Customer Solution Architect, and we are excited to share with you the latest feature releases from Sysdig.
This month, Sysdig Secure's Container Registry scanning functionality became generally available for all users. This functionality provides an added layer of security between the pipeline and runtime scanning stages. On Sysdig Monitor, we introduced a feature to automatically translate Metrics alerts in form-based query to PromQL. This allows you to choose between the convenience of form and the flexibility of PromQL.
We are excited to announce the availability of the Sysdig 6.0 on-premises release. This release brings several product offerings that are available on the Sysdig SaaS platform for the Monitor & Secure product.
In March, we expanded the Sysdig platform coverage to new environments by adding support for GCP metrics on Sysdig Monitor. Also, we extended our new security posture module to cover Openshift platforms. Further, we introduced a new inventory feature as a tech preview. This feature provides a consolidated view of all resources across Infrastructure as a Code, containers, cloud, and hosts, along with their security posture and configuration.
Stay tuned for more updates from Sysdig and let's get started!
Sysdig Monitor
GCP Metrics are Now Natively Supported by Sysdig Monitor
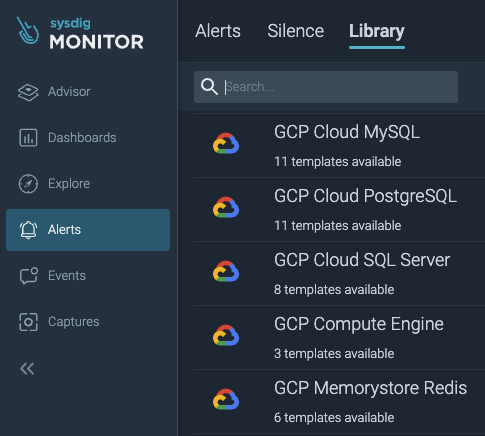
We are happy to announce the general availability of GCP metrics support in Sysdig Monitor. Just connect your Google Cloud account, enable the integration, and benefit from out-of-the-box GCP monitoring.
Initial support includes integrations for GCP MySQL, PostgreSQL, SQL Server, Compute Engine, and Memorystore for Redis. Customers can leverage out-of-the-box dashboards and alerts for these services. Additionally, metrics are collected for all GCP services – so, if there's not a set of dashboards/alerts for a service, it's simple to create them.
More information is available in the documentation and in our recent blog post: https://sysdig.com/blog/native-support-gcp-monitor/
How customers are using this:
Thanks to its multi-cloud integration model, Sysdig customers can easily monitor AWS, Azure, and GCP workloads and services from a single pane of glass.
Customers can now correlate their own applications, services, and Prometheus metrics with Kubernetes and cloud context, without any extra effort.
Forget about taking care of exporters or any other service to pull your GCP metrics. Everything is handled by Sysdig Monitor. The same way Sysdig Monitor works with third-party applications and services, it offers a completely smooth experience for GCP integration.
Translate Metrics Alerts to PromQL
Metric alerts configured in form-based query can now be automatically translated to PromQL. This allows users to choose between the convenience of form and the flexibility of PromQL. Translation to PromQL also allows users to define more complex and composite queries that are not possible with Form. For more information, see Translate to PromQL.
Monitoring Integrations
Added the following integrations:
- k8s-cAdvisor
- Microsoft IIS
- Microsoft SQL Server Exporter
- KNative (integration with jobs only)
- Added the following:
- Zone label to the GCP integrations
- Security updates to the UBI image of exporters
- New ports and certificate path to the Etcd default job
IBM Cloud Integrations
The IBM cloud Integrations add new easy-to-use dashboards, focused on relevant metrics, and support specific alerts for these integrations.
- IBM Cloud PostgreSQL
- IBM Cloud MongoDB
Dashboards and Alerts
Introduced the following improvements and changes to dashboards & alerts:
- Improved the CoreDNS integration dashboard and alerts with latency metrics
- Deprecated the Linux Memory Usage dashboard
- Moved the Linux Host Integration dashboard to the Host Infrastructure category
- Improved the Memory Usage dashboard for Linux VMs
- Removed the _AWS CloudWatch: DynamoDB Overview By Operation dashboard
For more information, see Integration Library.
Sysdig Secure
Container Registry Scanning is Generally Available
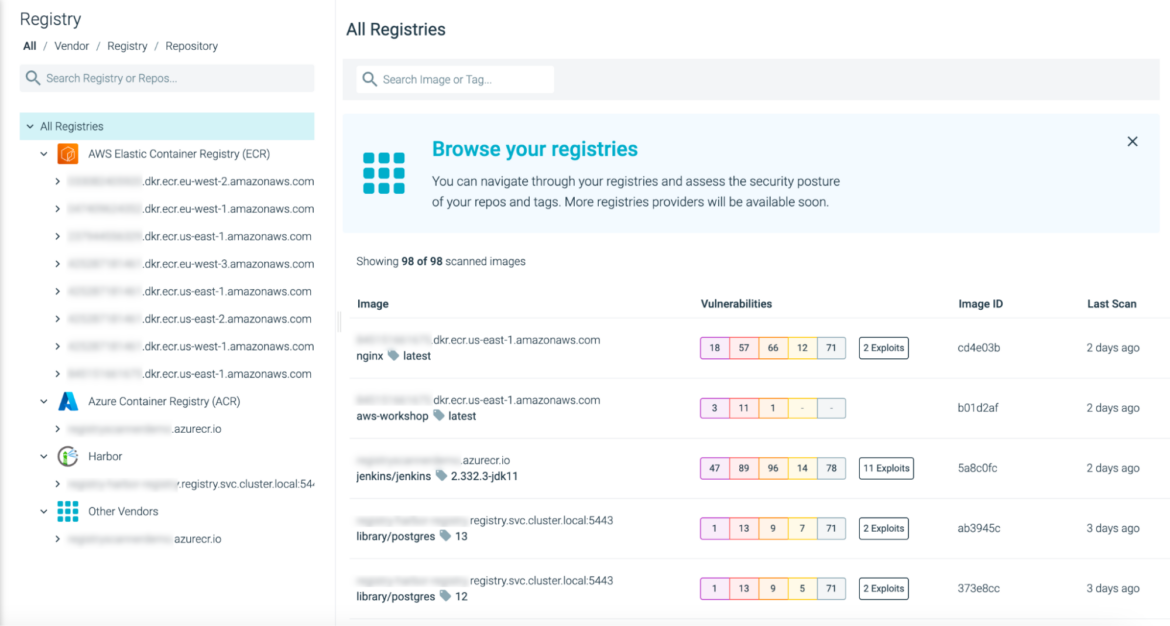
Sysdig Secure is excited to announce the general availability of the Image Registry Scanning functionality as part of our Vulnerability Management suite.
How customers are using this:
- Registries are a fundamental stage in the life cycle of container images. This feature provides an added layer of security between the pipeline and runtime stages, allowing you to gain complete visibility into potential vulnerabilities before deploying to production.
- Container registries accumulate large amounts of images from developers and sometimes from third-party vendors. Some of these images are obsolete or no longer suitable for runtime, and registry scanning provides the necessary security layer to avoid degradation of the security posture.
- Once the container registry is instrumented and analyzed, users can generate registry reports to extract, forward, and post-process the vulnerability information.
Supported vendors:
- AWS Elastic Container Registry (ECR) – Single Registry and Organizational
- JFrog Artifactory – SaaS and On-Premises
- Azure Container Registry (ACR) – Single Registry
- IBM Container Registry (ICR)
- Quay.io – SaaS
- Harbor
Risk Scores Explanation Enhanced in CIEM
Understand a breakdown of your CIEM Risk Scores with Overview explanations.
How customers are using this:
- Within the Posture tab, you'll find different Identity and Access resources with Risk Scores.
- Select an entity from the list in the table and a drawer appears providing a detailed breakdown of the entity's risk score. This includes the specific attributes and permissions that have contributed to it. Learn more about how risk scores are calculated.
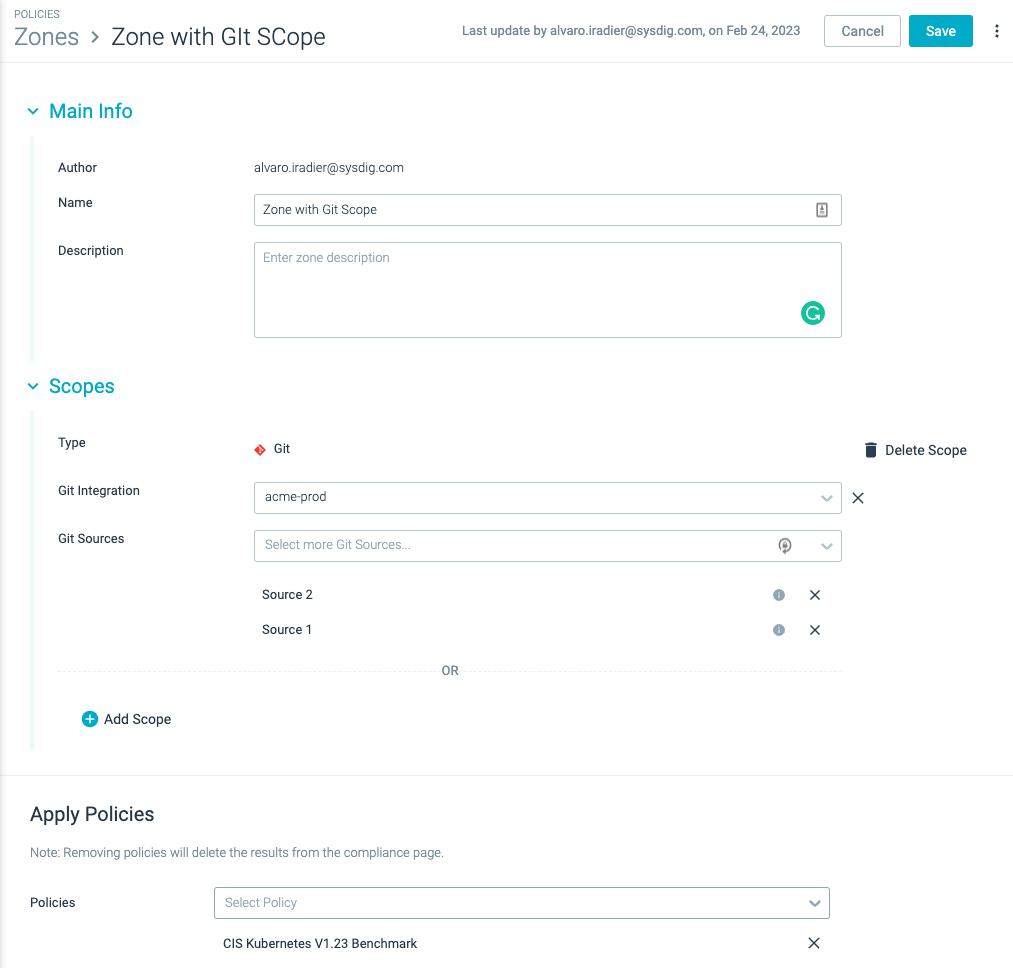
Git Scope for Zones
We have extended the flexibility of Zones for Posture to also support Git integrations and IaC (Infrastructure as Code) scanning.
How customers are using this:
With the introduction of Git scope for zones, users can include the new Git scope types as part of the zone definition and configure the policies that apply for that zone.
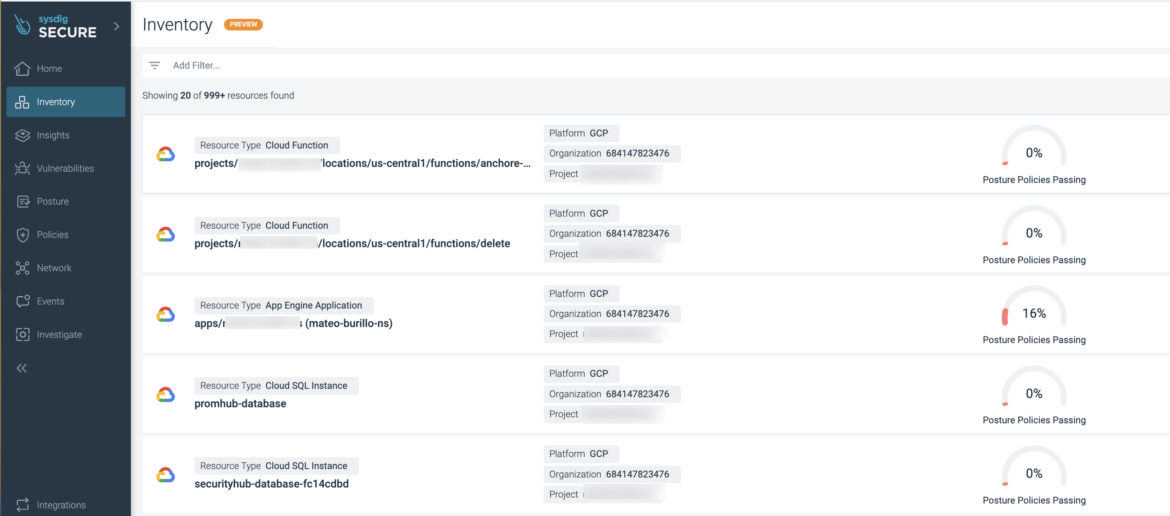
Inventory Released as Tech Preview
We are happy to announce that Inventory is available to all customers as a new top-level menu item.
How customers are using this:
Sysdig users can gain visibility into resources across the cloud (GCP, Azure, and AWS) and Kubernetes environments from a single view. With the current release of Inventory, Sysdig users can achieve goals such as:
- View all resources across their cloud environment(s)
- Protect all resources and mitigate blind spots
- Know all current resources in their infrastructure that share properties
- Know which resources belong to a business unit
- Review posture violations for a resource and take action (remediate or handle risk)
Support for CIS Security Control v8
The CIS critical Security Controls (CIS Controls) are a prioritized set of Safeguards to mitigate the most prevalent cyber-attacks against systems and networks. They are mapped to and referenced by multiple legal, regulatory, and policy frameworks. CIS Controls v8 (latest) has been enhanced to keep up with modern systems and software. Movement to cloud-based computing, virtualization, mobility, outsourcing, Work-from-Home, and changing attacker tactics prompted the update and supports enterprise security as they move to both fully cloud and hybrid environments.
This policy, with 1,316 controls classified into 18 requirement groups, is now available as part of Sysdig's posture offering.
Support for OWASP Kubernetes Top 10
The OWASP Kubernetes Top 10 is aimed at helping security practitioners, system administrators, and software developers prioritize risks around the Kubernetes ecosystem. The Top 10 is a prioritized list of these risks. This policy, containing 344 controls classified into 10 requirements, is now available in Secure.
More information about this policy can be found in OWASP Kubernetes Top 10.
Updated CIS AWS Foundations Benchmark to v1.5.0
We are happy to announce the update of the existing CIS Amazon Web Service Foundations Benchmark policy to its latest version at the time (v1.5.0). This new version includes a new resource type (EFS File System) for greater coverage, as well as new controls for the Amazon Elastic File System (EFS) and Amazon Relational Database Service (RDS) services. The total number of controls in this new update has been raised up to 79.
Helm Chart 1.5.80+ and Cli-Scanner 1.3.6 Released
- RELEASE suffix in Java packages leading to false negatives resolved
Specific Java packages containing a .RELEASE suffix were not correctly matched against their existing vulnerabilities, for example:
https://mvnrepository.com/artifact/org.springframework.boot/spring-boot-starter-web/1.2.2.RELEASE
was not correctly parsed and matched against the relevant vulnerabilities. This case is particularly common for spring-boot libraries.
This fix will remove false negatives, for example, uncover real vulnerabilities that were present in those packages but not previously listed. - IMPROVEMENTS display full path for jar-in-jar libraries:
When a jar library is found inside another jar container, Sysdig will display the absolute and relative path inside the jar, using the colon as separator:
Before: /SpringHelloWorld-0.0.1.jar
After: /SpringHelloWorld-0.0.1.jar:BOOT-INF/lib/spring-core-5.3.16.jar
See Vulnerabilities|Pipeline for details on downloading and running the cli-scanner.
Legacy Inline Scanner v 2.4.21 Released
- Updated anchore to 0.8.1-57 (March 2023)
- Support OCI manifest list: parse and scan images built with attestation storage
- Vulns fixes for the following High severity CVEs:
- CVE-2022-41723
- CVE-2022-47629
- CVE-2023-24329
- CVE-2023-25577
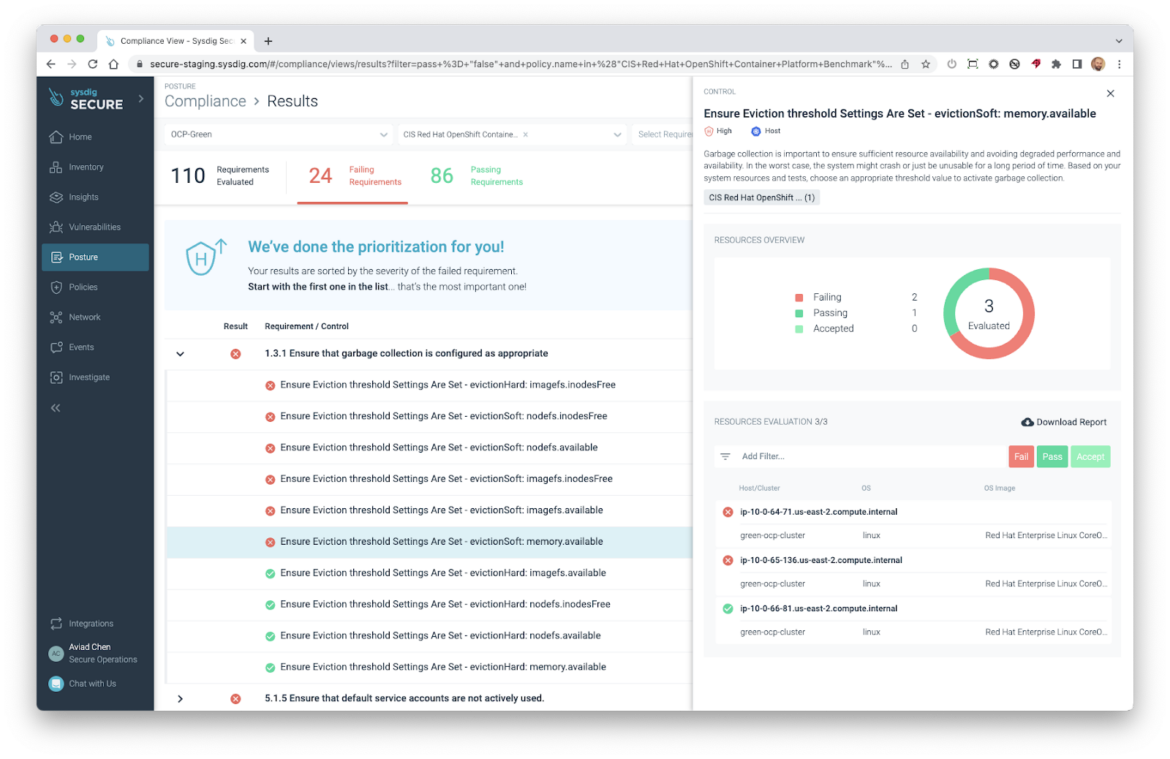
Posture now supports Red Hat OpenShift Container Platform (OCP4)
Sysdig is pleased to announce the support for the OpenShift platform. The CIS Red Hat OpenShift Container Platform Benchmark policy is now available, with 181 controls (145 are exclusive to OpenShift), using a new Cluster resource type which is of paramount importance in OCP4 due to the nature of the platform.
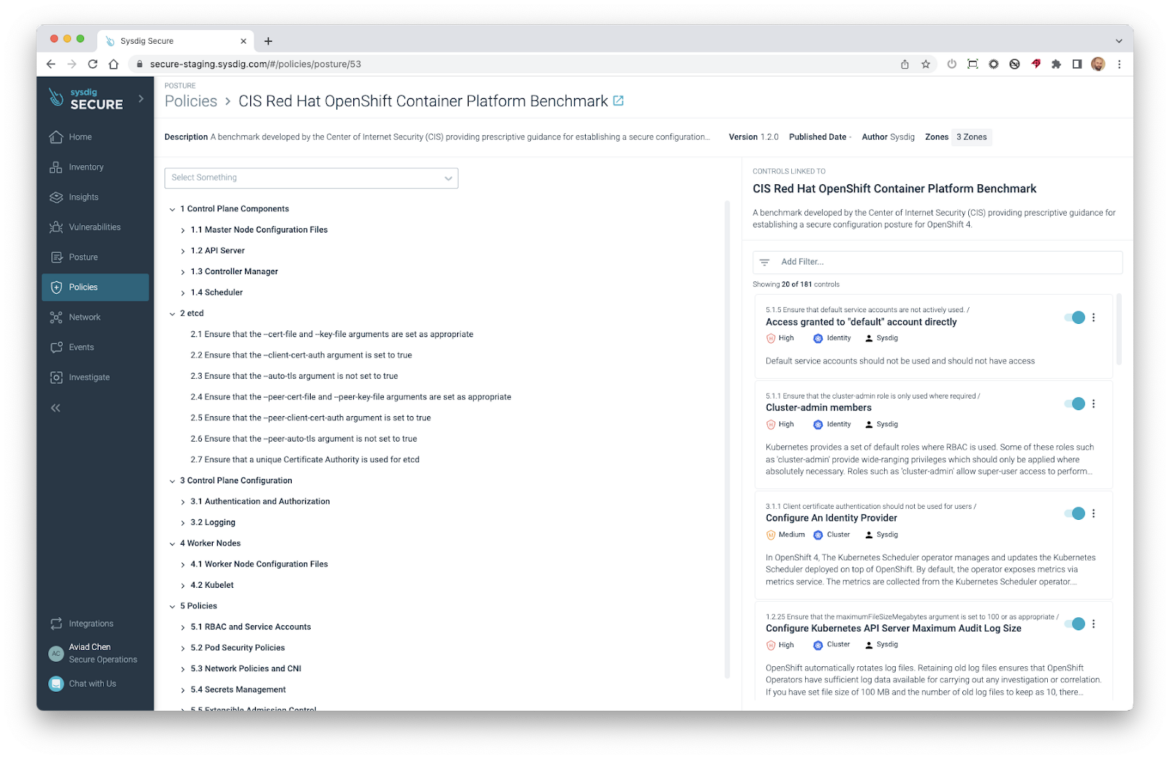
Improved Search of Posture Controls
Our ~1,000 Posture Controls are now easier to find, by their Name, Description, Severity, Type, and Target platform or distribution, anywhere you are looking for them:
- Filtering for controls in the Control library
- Filtering in the Policies library, including while editing your custom policy We also added enhanced visibility of control targets by showing the supported platform and distributions on each control.
Support for Posture on OCP, IKS, and MKE
We have added Posture support for new Kubernetes distributions:
- Support for Red Hat OpenShift Container Platform 4 (OCP4):
- CIS Red Hat OpenShift Container Platform Benchmark policy
- Support for IBM Cloud Kubernetes Service (IKS):
- Sysdig IBM Cloud Kubernetes Service (IKS) Benchmark policy
- Support for Mirantis Kubernetes Engine (MKE):
- Sysdig Mirantis Kubernetes Engine (MKE) Benchmark policy
New Out-of-the-Box Security Posture Policies Released
- CIS Kubernetes V1.24 Benchmark
A new Posture policy has been released following the CIS Kubernetes V1.24 Benchmark. This policy provides prescriptive guidance for establishing a secure configuration posture for Kubernetes 1.24, and includes 13 new controls.
- CIS Critical Security Controls v8
The CIS Critical Security Controls (CIS Controls) are a prioritized set of Safeguards to mitigate the most prevalent cyber-attacks against systems and networks. They are mapped to and referenced by multiple legal, regulatory, and policy frameworks. CIS Controls v8 (latest) has been enhanced to keep up with modern systems and software. Movement to cloud-based computing, virtualization, mobility, outsourcing, work-from-home, and changing attacker tactics prompted the update and supports an enterprise's security as they move to both fully cloud and hybrid environments.
This policy, with 1,316 controls classified into 18 requirement groups, is now available as part of Sysdig's posture offering.
- OWASP Kubernetes Top 10
The OWASP Kubernetes Top 10 is aimed at helping security practitioners, system administrators, and software developers prioritize risks around the Kubernetes ecosystem. The Top 10 is a prioritized list of these risks. This policy, containing 344 controls classified into 10 requirements, is now available in Secure.
- CIS Amazon Web Services Foundations Benchmark v1.5.0 (latest)
We are happy to announce the update of the existing CIS Amazon Web Services Foundations Benchmark policy to its latest version at the time (v1.5.0). This new version includes a new resource type (EFS File System) for greater coverage, as well as new controls for the Amazon Elastic File System (EFS) and Amazon Relational Database Service (RDS) services. The total number of controls in this new update has been raised up to 79.
The New CSPM Experience is Now Available in All IBM Cloud Production Environments
Sysdig is pleased to announce the GA release of the new CSPM Compliance in all IBM cloud production environments, Focus your compliance results on your most important environments and applications!
New features introduced:
- A new compliance page is introduced, ordered by your Zones!
- CSPM Zones Management
- Define scopes for the resources you want to evaluate
- Apply a policy to your zone to add it to the compliance page
- 50+ Risk and Compliance Policies included
To get to know our path from detection to remediation, risk acceptance, zones management, installation, and migration guidelines, please review the documentation.
New Page for Privacy Settings
A new page has been added in Administration|Settings to adjust Privacy settings for Sysdig Secure.
New Filter and Grouping for Threat Detection Policies
This release enhances the Threat Detection policies by showing the policies in a grouped manner and the ability to filter by policy type.
Additionally, badges on the list now alert when rules have been added or updated in managed policies.
New Filter and Grouping for Rules Library
This release enhances the Threat Detection rules library by showing the rules in a grouped manner, as well as adding the ability to view only custom rules.
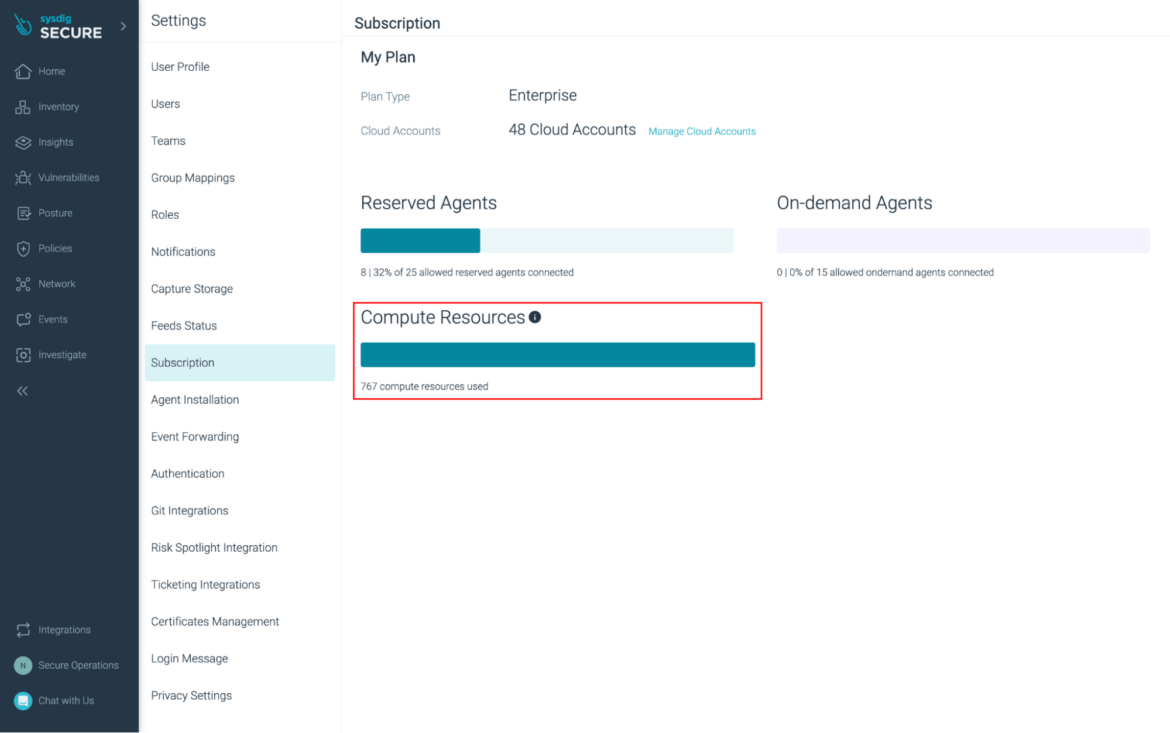
Cloud Account Compute Resource Usage Reporting
In this release, we have added Compute Resource usage reporting to the subscription page.
Sysdig Agents
Agent Updates
The latest Sysdig Agent release is v12.13.0. Below is a diff of updates since v12.11.0, which we covered in our February update.
Feature enhancements
Kernel Support
Supports kernel version v6.2.0 and above.
Version Upgrade for Library Benchmark
Library Benchmark has been updated from version 1.5.0 to 1.7.1.
Collect PodDisruptionBudget Metrics
Added support for collecting Kubernetes PodDisruptionBudget metrics.
Send Start and Ready Time for Pods
Added support for sending start time and ready time for a pod when configured. For more information, see Customize KSM Collection.
Optimize collecting runtime rules
The Falco rules optimizer has been enabled by default. This performs optimizations on the collection of runtime rules in conjunction with system call events to help reduce agent CPU usage.
Defect Fixes
Agent No Longer Fails When Customer ID Is Unspecified
Fixed a problem where an agent, which is stuck in a restart loop due to lack of configured customer ID, would fail to recognize when the configuration was subsequently updated to provide a customer ID.
Agent Retrieves JMX Metrics as Expected
Sysdig agent no longer generates heap dumps while fetching JMX metrics.
Podman containers running as unprivileged systemd services are detected correctly
Container image metadata is reported correctly with Podman 4.x
The following vulnerabilities have been fixed:
CVE-2022-40897 and CVE-2022-41723
Fix proxy connection
Fixed an issue where proxy connection could fail if used in conjunction with agent console.
Agentless Updates
v4.0.0 is still the latest release.
SDK, CLI, and Tools
Sysdig CLI
v0.7.14 is still the latest release. The instructions on how to use the tool and the release notes from previous versions are available at the following link:
https://sysdiglabs.github.io/sysdig-platform-cli/
Python SDK
v0.16.4 is still the latest release.
https://github.com/sysdiglabs/sysdig-sdk-python/releases/tag/v0.16.4
Terraform Provider
There is a new release v0.7.4.
Documentation: https://registry.terraform.io/providers/sysdiglabs/sysdig/latest/docs
GitHub link: https://github.com/sysdiglabs/terraform-provider-sysdig/releases/tag/v0.7.4
Terraform modules
- AWS Sysdig Secure for Cloud has been updated to v0.10.8.
- GCP Sysdig Secure for Cloud remains unchanged at v0.9.9.
- Azure Sysdig Secure for Cloud has been updated to v0.9.5.
Note: Please check release notes for potential breaking changes.
Falco VSCode Extension
v0.1.0 is still the latest release.
https://github.com/sysdiglabs/vscode-falco/releases/tag/v0.1.0
Sysdig Cloud Connector
AWS Sysdig Secure for Cloud has been updated to v0.16.34.
Admission Controller
Sysdig Admission Controller remains unchanged at v3.9.16.
Documentation: https://docs.sysdig.com/en/docs/installation/admission-controller-installation/
Runtime Vulnerability Scanner
The new vuln-runtime-scanner has been updated to v1.4.10.
Documentation: https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/runtime
Sysdig CLI Scanner
Sysdig CLI Scanner has been updated to v1.3.8.
Documentation: https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/pipeline/
Sysdig Secure Online Scan for GitHub Actions
The latest release has been updated to v3.5.0.
https://github.com/marketplace/actions/sysdig-secure-inline-scan
Sysdig Secure Jenkins Plugin
Sysdig Secure Jenkins Plugin has been updated to v2.2.9.
https://plugins.jenkins.io/sysdig-secure/
Prometheus Integrations
Integrations:
- Fix: Add new zone label to GCP integrations
- Feat: New integration – Microsoft IIS
- Feat: New integration – Microsoft SQL Server Exporter
- Sec: Security updates on exporters UBI images (2023-02)
- Sec: Update helm chart with new image version
- Doc: Correct TS consumption for Istio integration in our documentation
- OSS: Create a PR in the Windows exporter official repo with a list of fixes
Dashboards and alerts:
- Fix: Linux Host Integration should be listed in the Host Infrastructure category
- Feat: Improve Memory Usage dashboard for Linux VMs and maybe join with Host Resource Usage
- Fix: Missing parenthesis in PromQL expression in GCP PostgreSQL
- Fix: Update Time series dashboard with new metric name
- Fix: Kubernetes Alert for nodes down lack comparison with zero
- Fix: Remove the dashboard "_AWS CloudWatch: DynamoDB Overview By Operation"
- Fix: Windows dashboards scope to include job label
- Refactor: Convert existing AWS CloudWatch templates to Prometheus format
Sysdig On-premise
New release for Sysdig On-premises with version 6.0
Upgrade Process
This release only supports fresh installations of the Sysdig platform into your cloud or on-premises environment.
For the full supportability matrix, see the Release Notes. This repository also includes the on-prem Installation instructions.
Monitor
Sysdig has migrated to a Prometheus-native data store and is now available on on-premises deployments. This release adds several product offerings that are available on the Sysdig SaaS platform for the Monitor product. The following features are now available in the fresh installation of the 6.0.0 on-premises release.
Advisor
Dashboards
Explore
Alerts
Integrations
AWS Cloudwatch Metrics
- The AWS CloudWatch API metrics will be available in Prometheus format. For more information, see AWS CloudWatch API Metrics.
Notification Channels
Two new notification channels have been added:
Secure
Insights
Sysdig Secure has introduced a powerful visualization tool for threat detection, investigation, and risk prioritization to help identify compliance anomalies and ongoing threats to your environment. With Insights, all findings generated by Sysdig across both workload and cloud environments are aggregated into a visual platform that streamlines threat detection and forensic analysis. For more information, see Insights.
Compliance
New report types have been added to Unified Compliance:
- GCP
- Azure
- Kubernetes
- Docker
- Linux
Threat Detection Policies and Rules
Threat detection policies now have three "flavors," following the same model in our SaaS platform.
- Default/Managed Policies
- Managed Ruleset Policies
- Custom Policies
For information on the full description of these policy types, see in our Threat Detection Policies.
Integrations
Platform
Custom Roles
A custom role is an admin-defined role which allows Sysdig administrators to bundle a set of permissions and allocate it to one or more users or teams. This feature has been available in SaaS and is now released for our on-premises users. For more information, see Custom Roles.
Group Mappings
Group mappings allow you to connect groups from your identity provider (IdP) to the roles and teams associated with your Sysdig account.
Login Message
You can now configure a custom login message to help maintain security standards based on your organization.
Platform Audit
Sysdig provides both a UI and a set of APIs for auditing and reporting on the use of the Sysdig platform itself. By default, the UI is disabled to help minimize the required resources of running on-premises. The API is enabled by default. For more information, see Sysdig Platform Audit.
Privacy Settings
You can choose to opt in or out of sharing usage data with Sysdig.
Falco Rules Changelog
- Added the following rules:
Kernel startup modules changedModify Timestamp attribute in FileLaunch Code Compiler Tool in ContainerPut Bucket ACL for AllUsersCreate Hardlink Over Sensitive FilesAzure Storage Account CreatedAzure Storage Account DeletedGCP Create ProjectGCP Create Compute VM InstanceGCP Enable APICreate BucketDelete BucketDetect release_agent File Container EscapesJava Process Class File DownloadLaunch Excessively Capable ContainerUnprivileged Delegation of Page Faults Handling to a Userspace Processucket
- Reduced false positives for the following rules:
Launch Package Management Process in ContainerPTRACE anti-debug attemptLinux Kernel Module Injection DetectedLaunch Privileged ContainerReconnaissance attempt to find SUID binariesSuspicious Operations with FirewallsLinux Kernel Module Injection DetectedPTRACE attached to processRead sensitive file untrustedThe docker client is executed in a containerLaunch Privileged ContainerWrite below rootSchedule Cron JobsSuspicious Cron ModificationLaunch Remote File Copy Tools in ContainerLaunch Suspicious Network Tool on HostSystem procs activityModify Shell Configuration FileWrite below etcLaunch Sensitive Mount ContainerMount Launched in Privileged ContainerPTRACE attached to processClear Log ActivitiesLaunch Package Management Process in ContainerContainer Run as Root UserLaunch Remote File Copy Tools in ContainerLaunch Root User ContainerSet Setuid or Setgid bitSuspicious Cron ModificationDisallowed K8s UserThe docker client is executed in a containerLaunch Package Management Process in ContainerClear Log ActivitiesLaunch Package Management Process in ContainerWrite below etcRead sensitive file untrustedPTRACE attached to processLaunch Excessively Capable ContainereBPF Program Loaded into KernelRead sensitive file untrustedNon sudo setuidWrite below rootRead sensitive file untrustedWrite below rpm databaseLaunch Sensitive Mount ContainerLaunch Root User in ContainerNon sudo setuidWrite below etcRedirect STDOUT/STDIN to Network Connection in ContainerRead ssh informationClear Log ActivitiesModify Shell Configuration FileSystem ClusterRole Modified/Deleted- Improved condition for the following rules:
Put Bucket LifecycleExecution of binary using ld-linuxMount Launched in Privileged ContainerTampering with Security Software in ContainerLaunch Ingress Remote File Copy Tools in ContainerModify Timestamp attribute in File
- Updated k8s image registry domains.
- Updated the MITRE, GCP MITRE, and AWS MITRE tags.
- Improved the
falco_privileged_imageslist. - Updated IoCs Ruleset with new findings.
- Added Falco rules versioning support.
- Added an exception for the
OpenSSL File Read or Writeand for theoutbound Connection to C2 Serversrule rule.
- Improved condition for the following rules:
Our Falco team has been busy the last couple of months with multiple releases of new features. For more information on what has been released for the entire month of March and April, please review here.
New Website Resources
Blogs
- How to Monitor Your Windows Infrastructure
- Sysdig Validated as AWS CloudOps Competency Launch Partner
- Kubernetes 1.27 – What's new?
- Troubleshooting Application Issues with Extended Labels
- Why the Wiz/SentinelOne Partnership Validates the Sysdig Approach
- AWS recognizes Sysdig as an Amazon Linux 2023 Service Ready Partner
- ChatGPT as your Falco Consultant
- Aligning Falco's Cloudtrail Rules with MITRE ATT&CK
- MITRE ATT&CK and D3FEND for Cloud and Containers
- Millions wasted on Kubernetes resources
- Easily Monitor Google Cloud with Sysdig's Managed Prometheus
- DISA STIG compliance for Docker and Kubernetes with Sysdig Secure
- Kubernetes CPU Requests & Limits VS Autoscaling
- Why CNAPP Needs Runtime Insights to Shift Left and Shield Right
- SANS Cloud-Native Application Protection Platforms (CNAPP) Buyers Guide
- Terraform Security Best Practices
- Guidelines: How to reduce the noise of Falco rules in Sysdig Secure
- Migrating from Prometheus, Grafana, and Alert Manager to Sysdig Monitor
- Kubernetes CreateContainerConfigError and CreateContainerError
- Why Companies Still Struggle with Least Privilege in the Cloud
- Prometheus Exporters in Sysdig Monitor
- Monitoring with Custom Metrics
- Prometheus and Kubernetes Metrics Ingestion
Threat Research
- Proxyjacking has Entered the Chat
- How to Detect SCARLETEEL with Sysdig Secure
- CSI Container: Can you DFIR it?
- OWASP Kubernetes Top 10 – A Risk Assessment
- SCARLETEEL: Operation leveraging Terraform, Kubernetes, and AWS for data theft
- Bypassing Network Detection with Graftcp
- Chaos Malware Quietly Evolves Persistence and Evasion Techniques
Webinars
- Prioritize Cloud Risk and Accelerate Remediation with Sysdig and AWS – APAC
- Prioritize Cloud Risk and Accelerate Remediation with Sysdig and AWS
- Dig Deeper! Prioritize Cloud Vulnerabilities and Reduce Container Spending
- Crack the Exam Code to Become a Certified K8s Security Specialist in 2023
Tradeshows
- April 4, AWS Summit Paris 2023, Paris, France
- April 5 – 7, FIC Europe 2023, Lille, France
- April 17 – 21, KubeCon Europe 2023, Amsterdam, Netherlands
- April 24 – 27, RSA Conference 2023, San Francisco CA
- April 25, Sysdig 'Dig Day' with AWS Copenhagen
Education
The Sysdig Training team provides curated, hands-on labs to learn and practice different topics. The selection of courses for the month of March:


