“What’s New in Sysdig” is back with the August 2023 edition! My name is Jonathon Cerda, based in Dallas, Texas, and the Sysdig team is excited to share our latest feature releases with you.
Sysdig Announces Revolutionary Generative AI Defense for Cloud Security! Sysdig Sage is a generative AI assistant built on a unique AI architecture specifically designed for cloud security. Sysdig Sage goes beyond typical AI chatbots to employ multi step reasoning and multidomain correlation to quickly discover, prioritize, and remediate risks specific to the cloud. It also leverages the power of Sysdig runtime insights to reveal hidden connections between risks and security events that would otherwise go undetected. You can find more information on this here.
Stay tuned for more updates from Sysdig, and let’s get started!
Sysdig Secure
Agentless Threat Detection for GitHub (CA)
Your GitHub organizations can be now secured with Sysdig agentless CDR, which extends its capabilities adding the first Git provider to the list of supported sources. By installing the Sysdig app on GitHub, it will be possible to enable our Falco-powered threat detection capabilities. Read how to do that in our documentation. You will also find policies and rules provided and maintained constantly by our Threat Research Team, along with the possibility to create your own custom ones.
Agentless Threat Detection for Okta (Preview)
Sysdig agentless CDR extends its coverage by adding support for Okta, the first Identity provider in the list of supported sources. You can now connect Okta organizations to Sysdig and use the power of Falco rules to detect threats in your environment. Along with the customizability of Falco rules, Sysdig provides managed policies and rules that are constantly being updated.
Control Access to Zones and Posture Policies
Sysdig is introducing two new permission items under Sysdig Secure → Policies:
- Zones (Read, Edit)
- Posture Policies (Read, Edit)
These permission items enable administrators to control who can edit access to Zones and Posture Policies, including APIs.
Existing roles are updated with the following permissions:
- Default Roles: Team Manager, Advanced User:
- Zones → Edit, Posture Policies → Edit
- All Existing Custom Roles and Default Roles: Service Manager, Standard User, View Only:
- Zones → Read, Posture Policies → Read
Runtime Rule Tuner Updated
When applying exceptions to tune rules and turn down noisy event notifications, the interface has been simplified and improved.
- Exception information now presented in easy-to-understand name/value pairs
- Values can be freely edited
- Explicit “Apply” button added for each exception, making the choices conscious and avoiding security blindspots
- If you are using Terraform to manage exceptions, you can now view the suggested exception as a Terraform snippet and copy/paste it into your Terraform file
- Impacted policies and any already-applied exceptions are displayed to help you make more informed decisions
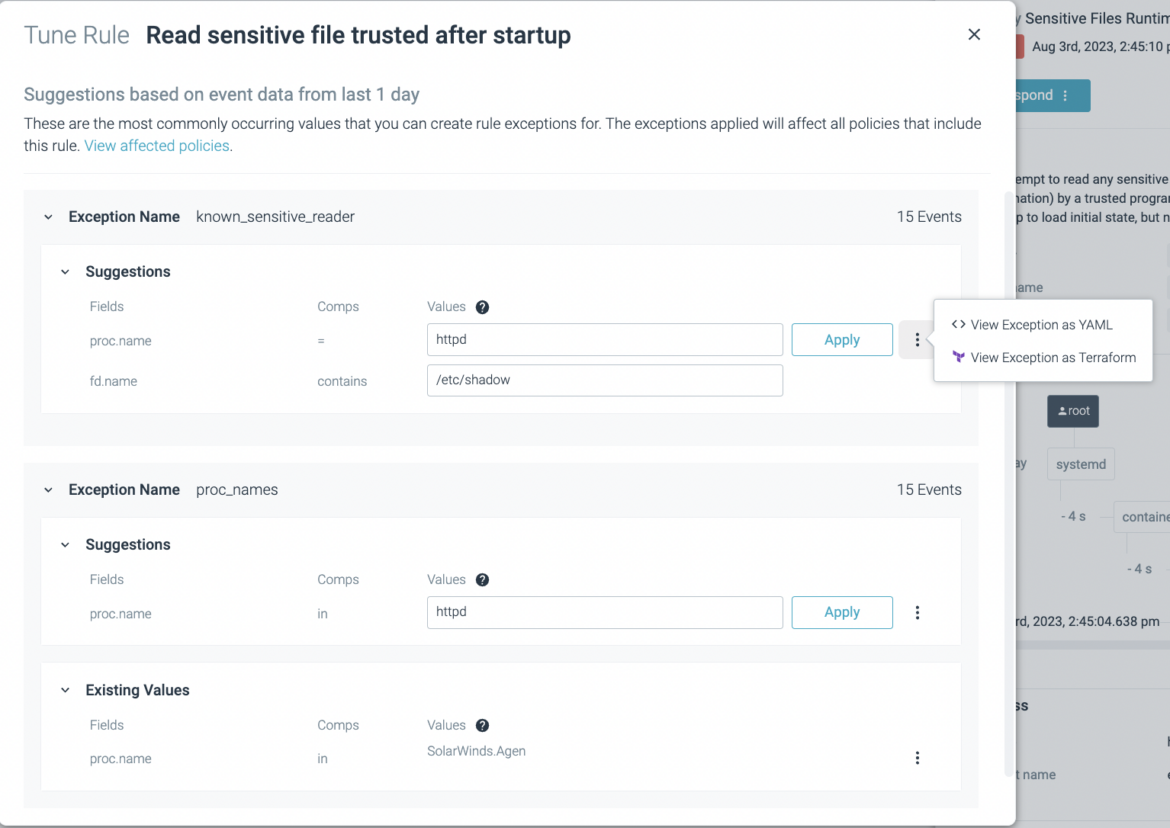
See how to use the improved feature in the Events feed. You can also access it from Insights.
Sysdig Monitor
Cost Advisor reaches GA, packed with new features
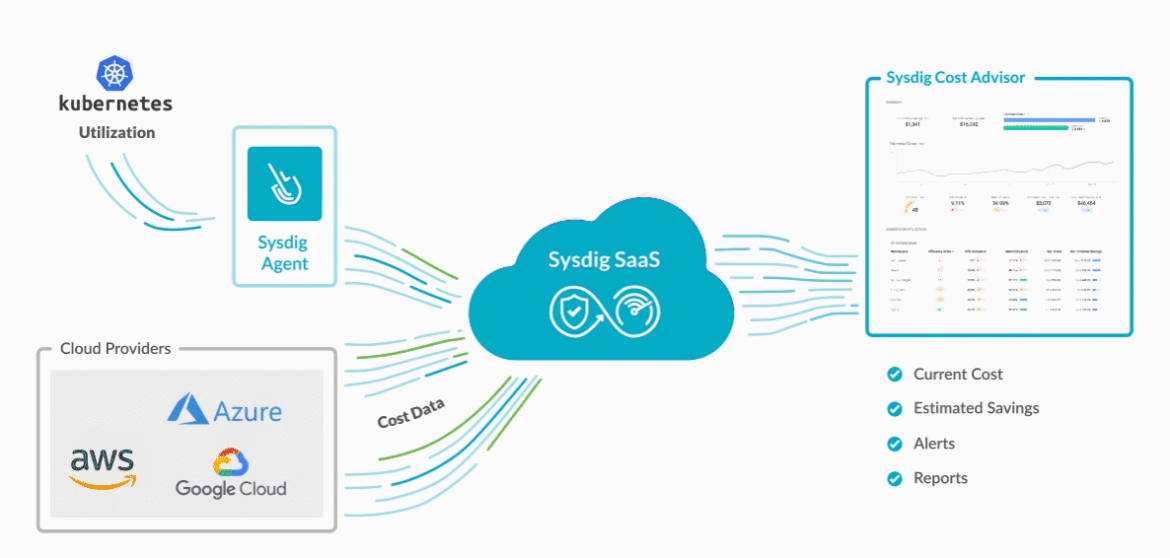
We’re excited to announce a significant milestone in Sysdig’s journey towards helping teams get visibility into, and optimize Kubernetes Costs. Cost Advisor is now generally available and we’ve made significant improvements.
- Private Billing, currently available for AWS, reconciles costs with your specific AWS billing agreements. Usage of reserved and spot instances, as well as savings plans and other discounts will be used to calculate costs. This integration will be useful for customers that want more accurate costs instead of relying on public on-demand pricing.
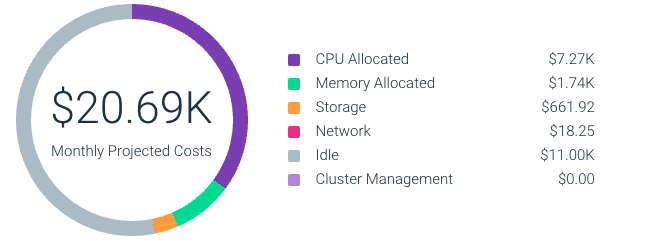
- We’ve added support for storage, load balancer, and idle costs. This paints a fuller picture of your Kubernetes costs where workloads are leveraging persistent volumes and load balancers, and idle costs gives platform teams insights into the cost of used cluster capacity – a great indicator as to whether a cluster can be reshaped or scaled down.
- Cost Explorer empowers users to explore costs in detail with granular segmentation. This helps users understand, for example, what is the cost of a workload that is running across multiple clusters.
- Cost Reports streamlines cost reporting processes with the ability to set up period report generation that can be exported to 3rd party systems, and Slack and email notifications help create a culture of cost discipline.
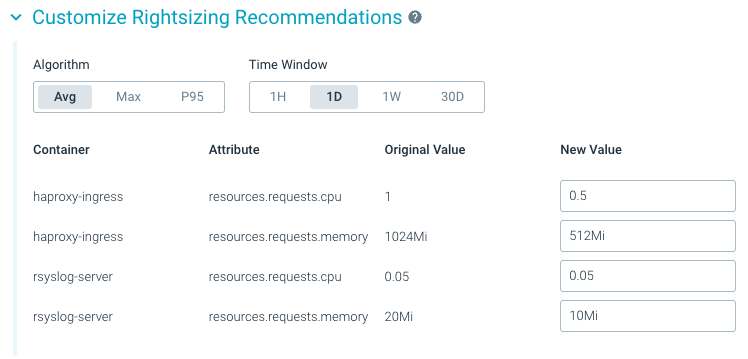
- We’ve made improvements to workload rightsizing to give users more control over the recommendations provided. Depending on whether a workload is production / HA grade, or a staging / dev setup, when rightsizing a workload users can choose between more conservative or aggressive recommendations.
New Alerting Capabilities
Sysdig has recently introduced a new feature that enables users to manually resolve triggering alerts. This enhancement allows users to exercise direct control over the alert resolution process. In addition, Sysdig Monitor now includes the automatic deactivation of orphaned alert occurrences. Orphaned alert occurrences refer to alerts triggered by entities that no longer report data. This automatic deactivation process ensures that alert occurrences originate only from entities that are actively providing data to Sysdig Monitor. For example, it prevents situations where alerts are triggered by a database that was decommissioned months ago, eliminating potential confusion.
Furthermore, Sysdig Monitor now incorporates the Alert Resolution Delay for PromQL Alerts. This feature is designed to curtail noisy alert resolutions by imposing a requirement that an alert condition must remain resolved for a user-defined duration before being marked as officially resolved. This aspect adds a layer of precision to the resolution process, leading to a more efficient alert management workflow.
Metrics Usage
Metrics Usage has been updated with two new features (Total Time Series Count panel, Per-metric Time Series Churn Over Time & Label Exploration).
Monitoring Integrations
- Added support for Istio 1.16.
- Added an option in Windows Installer to change the Prometheus agent port.
- Added time charts for CPU and Memory usage in the Cluster Capacity Planning Dashboard.
Sysdig Agents
12.16.0 August 08, 2023
Feature enhancements
Supports Control Group v2
Control groups v2 (cgroups v2) are now supported in the Sysdig Agent. In particular, the v1 freezer subsystem is not mounted when using cgroups v2, which causes potential compatibility issues.
Collects node labels
Sysdig Agent can by default collect the node-role.kubernetes.io/* labels set on nodes.
Known issues
Container Limits to Drift Control
- For kernel versions below v5.13, Drift Control can monitor up to 128 containers per node.
- For kernel versions v5.13 or above, modify the container limit using one of the following methods:
- Open the
sysctl -n fs.fanotify.max_user_groupsfile and set the new value by usingsysctl -w fs.fanotify.max_user_groups=<new_limit>. - Open the
cat /proc/sys/fs/fanotify/max_user_groupsfile and runecho <new_limit> > /proc/sys/fs/fanotify/max_user_groups.
Replace<new_limit>with your choice of container limit.
- Open the
Defect fixes
Removed compliance manager support
Compliance manager functionality has been removed from Sysdig Agent. The feature was not supported anymore and yet it appeared in a security audit as having a vulnerability. For these reasons, this functionality has been dismissed.
Ignores non-running pods for scraping
The Prometheus k8s-pods job configuration has been modified to drop scrapes from non-running pods.
Enables FIPS mode
The agent can now enable FIPS-compliant (Federal Information Processing Standards) mode even if the whole system isn’t in FIPS-compliant mode.
Resends unacknowledged policy events
Sysdig Agent attempts at resending unacknowledged policy events when the collector disconnects.
Adds missing health metrics in secure modes
An additional metric is collected in the secure and secure_light modes. The protobuf output for secure and secure_light mode now includes an aggrSamplingRatio aggregation field, weighted to the negotiated metrics interval.
SDK, CLI, and Tools
Sysdig CLI
v0.7.14 is still the latest release. The instructions on how to use the tool and the release notes from previous versions are available at the following link:
https://sysdiglabs.github.io/sysdig-platform-cli/
Python SDK
The Python SDK remains at v0.16.6.
Terraform Provider
We have just released the 1.12.0 version of terraform provider. This release includes:
- Add form based prometheus alert type
- Add change alert type
- Add resource for silence rule
- Add new notification channel types
- Add missing arguments to (legacy) webhook notification channels
- Add missing arguments to monitor slack notification channels
- Allow usage of alerts v2 on IBM
- Hotfix cspm policy creation
https://docs.sysdig.com/en/docs/developer-tools/terraform-provider
Terraform Modules
- AWS Sysdig Secure for Cloud remains unchanged at v10.0.9
- GCP Sysdig Secure for Cloud remains unchanged at v0.9.10
- Azure Sysdig Secure for Cloud changed to v0.9.7
- Support use of Reader role in Trust Relationship module (#91)
- feat: Support using Reader CSPM role
- linting fixes
- Support use of Reader role in Trust Relationship module (#91)
Falco VSCode Extension
v0.1.0 is still the latest release.
https://github.com/sysdiglabs/vscode-falco/releases/tag/v0.1.0
Sysdig Cloud Connector
New Cloud Connector changes to (v0.16.47) under helm chart 0.8.2:
Admission Controller
New Admission Controller release (3.9.25) under helm chart 0.11.3.
Sysdig CLI Scanner
Sysdig CLI Scanner changed to v1.5.1.
When you run cli-scanner with the --json-scan-result parameter, the severities in JSON keys are not capitalized anymore. For example:
"vulnTotalBySeverity": {
"Critical": 2,
"High": 65,
"Low": 24,
"Medium": 107,
"Negligible": 417
},Code language: Perl (perl)…has been changed to:
"vulnTotalBySeverity": {
"critical": 2,
"high": 65,
"low": 24,
"medium": 107,
"negligible": 417
},Code language: Perl (perl)This change impacts the following JSON objects:
vulnTotalBySeverityfixableVulnTotalBySeverity
https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/pipeline/
Sysdig Secure Inline Scan Action
The latest release remains unchanged at v3.5.0.
https://github.com/marketplace/actions/sysdig-secure-inline-scan
Sysdig Secure Jenkins Plugin
The Sysdig Secure Jenkins Plugin remains at version v2.3.0.
https://plugins.jenkins.io/sysdig-secure/
Prometheus Integrations
Prometheus Integrations remains at 1.16.0:
https://github.com/draios/prometheus-integrations/releases/tag/v1.16.0
Integrations:
- Fix: Preserve
istio_buildandpilot_proxy_convergence_time_bucketmetrics on IstioD job - Feat: Add support for Istio 1.16
- Docs: Fix k8s-PVC integration prerequisites
- Feat: Add in Windows Installer an option to change the Prometheus agent port
- Fix: Some control plane integrations have wrong label used for aggregation
- Feat: Tweak PromQL filters in order to avoid great amount of TS in the subqueries
- Test: Create a test to check the Prometheus jobs files are correct
Sysdig On-premise
On-prem release v6.4 is the latest release!
Upgrade process
Supported upgrades from: 5.0.x, 5.1.x, 6.x
For the full supportability matrix, see the Release Notes. This repository also includes the on-prem Installation instructions.
Platform fixes
- Fixed an issue with fresh installations and upgrades with FIPS mode enabled on backend hosts.
- Fixed an intermittent issue accessing the Sysdig UI when using a newly created team.
- Fixed an init container issue for the sysdigcloud-feeds-db deployment that would use the wrong mount point.
Falco Threat Detection Rules Changelog
Several versions of the rules have been released in the last months. Below are the release notes for the most recent rules changes.
https://docs.sysdig.com/en/docs/release-notes/falco-rules-changelog/
- Reduced false positives for the
Launch Root User Containerrule. - Added the following rules:
AWS ECS Create Task DefinitionAWS RDS Master Password UpdateAWS IAM Credential Report Request
- Updated the IoCs Ruleset with new findings.
- Improved the
network_tool_binarieslist. - Added support for
accept4 syscall.
Default policy changes
Added the following rules:
AWS ECS Create Task DefinitionAWS RDS Master Password UpdateAWS IAM Credential Report Request- Improve condition for
Azure RDP Access Is Allowed from The Internetrule - Improve condition for
Azure SSH Access Is Allowed from The Internetrule
Default policy changes
Remove the AWS IAM Credential Report Request rule from policy.
- Reduced false positives for the following rules:
Write below rootSet Setuid or Setgid bitPossible Backdoor using BPFNon sudo setuidLaunch Sensitive Mount Container
- Updated the IoCs Ruleset with new findings
- Improve output for the
Fileless Malware Detected (memfd)rule
Default policy changes
Removed Packet socket created in containercode> from the Sysdig Runtime Notable Events policy.
- Reduced false positives for the following rules:
Execution from /tmpLaunch Privileged ContainerPacket socket created in container
- Updated the IoCs Ruleset with new findings
- Reduced false positives for the following rules:
Packet socket created in containerChange thread namespaceAWS SSM Agent File Write
Default policy changes
Downgraded AWS rules.
Open Source
Falco
Falco 0.35.1 is now available.
https://github.com/falcosecurity/falco/releases/tag/0.35.1
New Website Resources
Blogs
LABRAT: Stealthy Cryptojacking and Proxyjacking Campaign Targeting GitLab
Prioritize Vulnerabilities Faster with Checkmarx and Sysdig
Boost Detection and Response with Cybereason and Sysdig
Google’s Vertex AI Platform Gets Freejacked
2023 Global Cloud Threat Report: Cloud Attacks are Lightning Fast
Webinars
Aug. 7th – Rise Together: Empowering Women at Work
Aug. 17th – Beyond the Neon Lights: Top Takeaways from Black Hat USA
Aug. 25th – Threat Hunting in the Cloud Solutions Forum 2023
Sysdig Education
Sysdig Sage: https://www.youtube.com/watch?v=LoPaplPV4KA
Kraken Discovery Lab: VULNERABILITY MANAGEMENT HANDS-ON WORKSHOP on Aug. 30th!
Intro to Secure (video) – https://www.youtube.com/watch?v=jJv4_HTxwVI
Intro to Monitor (video) – https://www.youtube.com/watch?v=SyD_4sNadAQ
Vulnerability Management Landing Page (video) – https://www.youtube.com/watch?v=1_uPQnVKZAI
Sysdig Live – https://www.youtube.com/watch?v=bo1D-jQssw8
Process Trees – https://www.youtube.com/watch?v=wqf_ZY_cqwQ


