On May 11, several Italian institutional websites, including the Italian Senate, the Ministry of Defense, and the National Institute of Health, were taken offline and unreachable for a few hours. This was day one of a multiday cyber attack, which targeted other Italian websites as well as other countries. The pro-Russian hacker groups Killnet and Legion claimed the attacks through their Telegram channels, killnet_channel and legion_russia, and used the Mirai malware to perform their DDoS (distributed denial-of-service) attacks to Italian websites.
If confirmed, this would be the first claimed attack against Italy from pro-Russian cyber groups since the beginning of the war in Ukraine.
The Sysdig Threat Research Team has been collecting and monitoring data about the Mirai group and similar Mirai malwares for some time. In the last 90 days, we monitored more than 1000 attacks from different types of malwares based on Mirai.
In this article, we cover what happened through the declarations of the parties involved. We will also provide context to the Mirai botnet and explain how it is possible to detect Mirai activities through Falco, the CNCF runtime security tool.
The threat actor Killnet
Killnet has been operating as a threat actor since the beginning of 2022. The Killnet telegram channel was created on Jan. 23, 2022, and the Legion channel was launched four months later, on April 28. Based on communications on the Killnet channel, it seems that Legion is a subgroup of Killnet.
Before targeting Italy, over the past few months, they have targeted government and private companies in other countries, including the United States, Estonia, Latvia, Germany, Poland, Czech Republic, and Ukraine. The websites they are targeting make it clear that their targets include countries that oppose Russia.
We can retrieve other information about Killnet from an interview with their founder, published on April 22. Known as killmilk, they said, “Killnet originally appeared as a service on the dark web.” With the conflict in Ukraine starting, they decided to stop the commercial use of their botnet to support the fight against Ukraine and NATO countries, without actually stealing “money even from their enemies.” During the interview he also mentioned that their targets are “only those who are the conductor of evil and aggression, and we do not touch the civilian population.”
According to Killnet, the botnet they use for their attacks is composed for the vast majority of foreign devices (only 6% of Russian machines), and they are financed by enthusiasts and patriots who “have nothing to do with the authorities.”
Talking about findings, on March 3, Killnet published some cryptocurrency addresses asking for financial support in their official channel, as shown below.
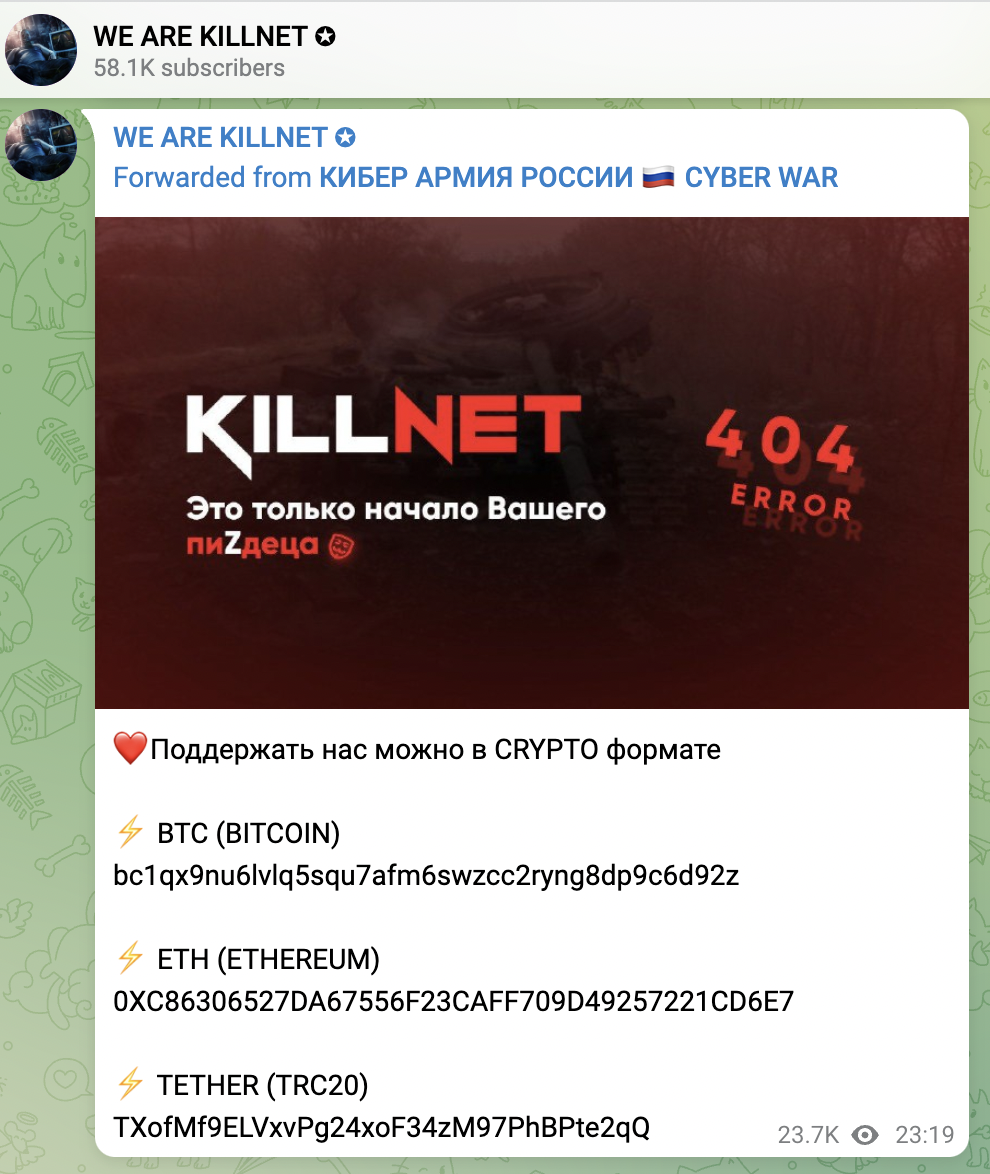
Checking for those addresses, it is possible to verify the amount of money they received (at the time of this writing):
- BTC: $25,757.16 → https://www.blockchain.com/btc/address/bc1qx9nu6lvlq5squ7afm6swzcc2ryng8dp9c6d92z
- ETH: $604.17 → https://www.blockchain.com/eth/address/0xc86306527da67556f23caff709d49257221cd6e7
- TETHER: $10,317 → https://usdt.tokenview.com/en/address/TXofMf9ELVxvPg24xoF34zM97PhBPte2qQ
The main modus operandi of Killnet, Legion, and similar groups is to create a botnet of hundreds of thousands machines infected with the famous Mirai malware and to use it to perpetrate DDoS attacks.
What is the Mirai Botnet?
The Mirai malware is responsible for many large-scale DDoS attacks since 2016. The main target of this malware is Internet of Things (IoT) devices, because a few years ago, their default configurations were not sufficiently secure and most of the IoT devices exposed on the internet had their default configuration.
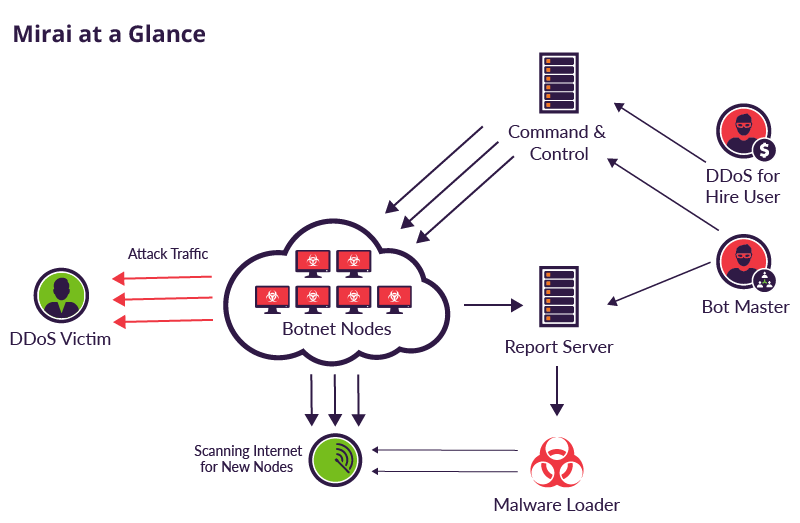
Since 2016, the botnet of IoT devices infected with Mirai has hit several popular websites in several countries, including GitHub, Twitter, Reddit, Netflix, and Airbnb, which has cost hundreds of millions of dollars.
Since the Mirai group published their malware source code on Hack Forums, many cyber criminals downloaded it and reused the same techniques to create other malwares. Some of them aim to target specific zero day vulnerabilities, others target embedded processors or hijack cryptocurrency mining operations, as we talked about recently in our blog.
Well-prepared cyber groups can customize the Mirai malware in order to keep it updated with the most recent vulnerabilities.
What happened? Killnet attacks in detail
Killnet’s attacks succeeded in making the websites of some Italian institutions unreachable. Also, they targeted the Eurovision voting system and the websites of some German and Polish companies, although those attacks were mitigated.
Let’s try to summarize the events that have happened so far.
- May 11, 2022
- 16:49 CET – Legion posted a list of Italian websites hit by their DDoS attack
- 17:57 CET – Legion posted a list of Polish and German websites that were going to be the next target
- May 12, 2022
- 3:42 CET – Legion posted another list of Italian websites that went unreachable
- 11:30 CET – Killnet informed that they did “military cyber exercises,” and that they “will go on the offensive” as soon as the training finishes
- May 14, 2022
- 22:48 CET – Legion incited their supporters to perform a DDoS attack towards the Eurovision voting system
- May 15, 2022
- 7:51 CET – The Italian State Police informed the public in a tweet that they thwarted a cyber attack against Eurovision
- 22:48 CET – Killnet posted a video where they declared cyber war on 10 countries
- May 16 2022
- 1:29 CET – Killnet claimed a DDoS attack against the website of the Italian State Police
- May 17 2022
- 4:06 CET – Killnet claimed another DDoS attack against the Italian State Polic website
Let’s see in detail what happened using information collected from the threat group official telegram chats.
- May 11 at 16:49 CET – It all started when Legion posted a list of Italian websites that were verified to be unreachable. The translated title of their message is ‘Squad “Mirai” Beat and beats only commander Mirai Attack on Italy.’
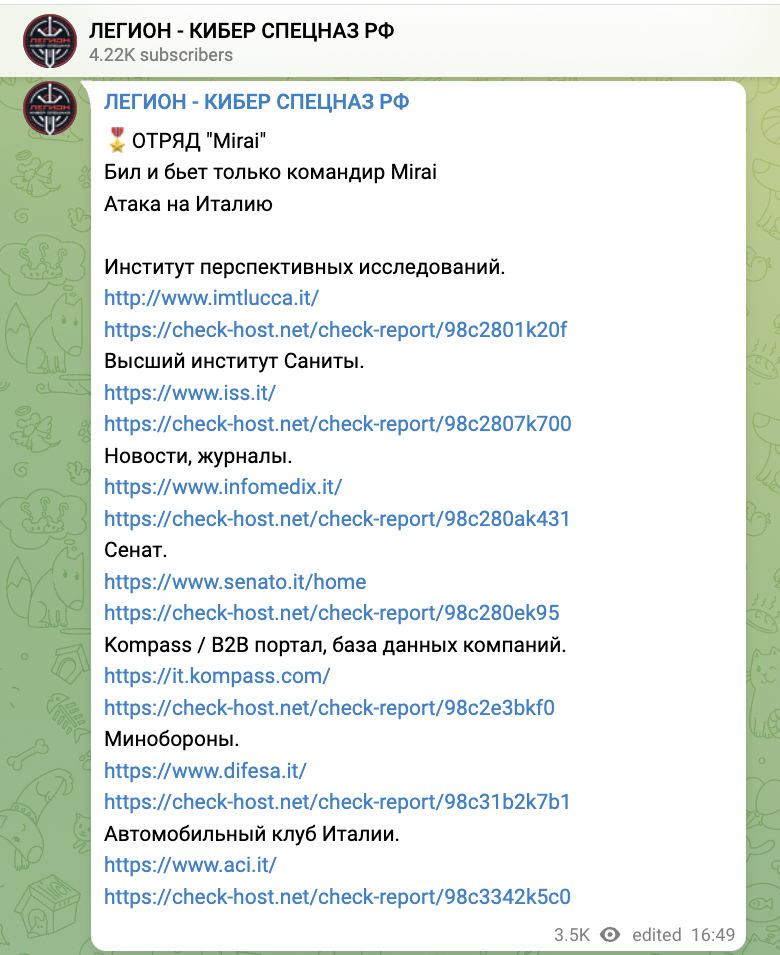
A few minutes later, Killnet posted the following message warning about next activities:

- May 11 at 17:57 CET – Legion posted another message with a list of Polish and German websites that were going to be the next target of another cyber group called Jacky. The message title is ‘Squad “Jacky” Hitting these sites. Anyone who wants to help.’

- May 11 at about 20:00 CET – All hit Italian targets were restored.
- May 12 at 2:35 CET – Killnet confirmed that the attack to the previously listed websites was performed by Legion, which seems to be a subgroup of Killnet.
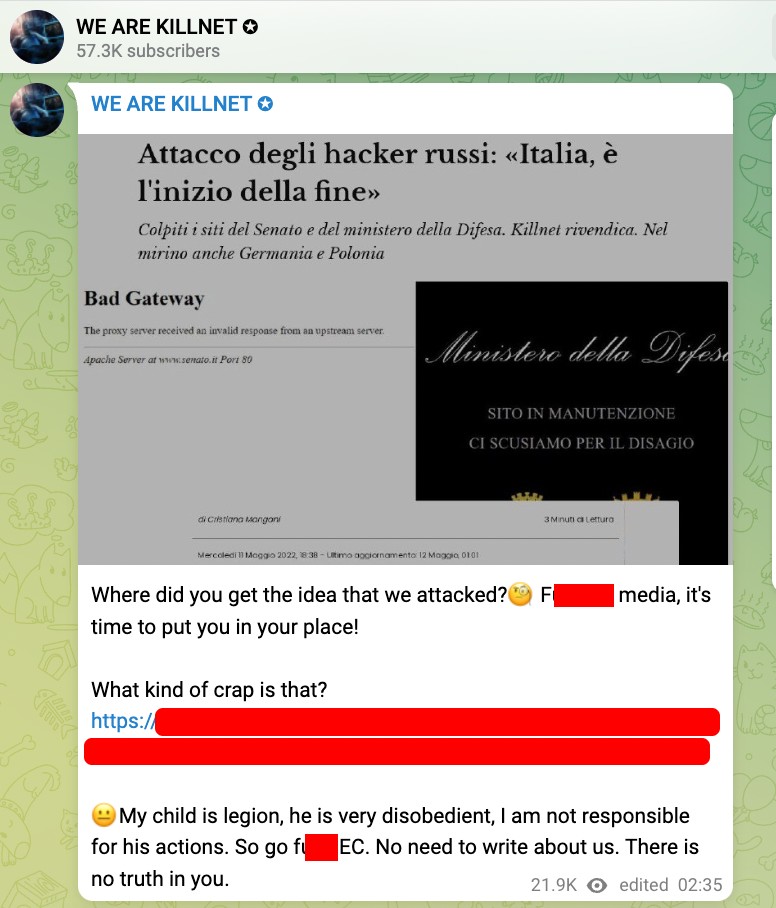
- May 12 at 3:42 CET – Legion posted another short list of Italian websites that went unreachable, including the Senate website. This message was titled ‘Demonstrative Attack on the network infrastructure of Italy from the commander of the detachment “MIRAI.”’
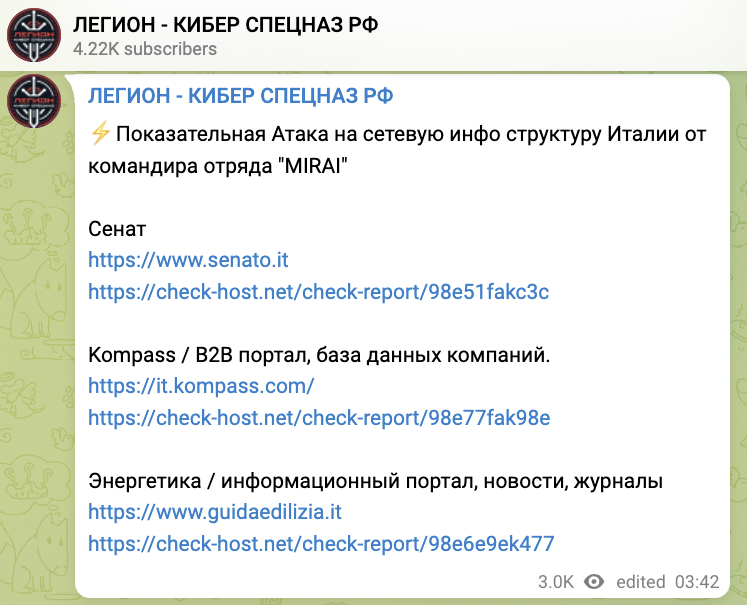
- May 12 at 11:30 CET – Killnet claimed some attacks, too. Actually, Killnet specified that they did not attack, but it was a “military cyber exercises,” and that they “will go on the offensive” against Italy and Spain as soon as the training finishes.
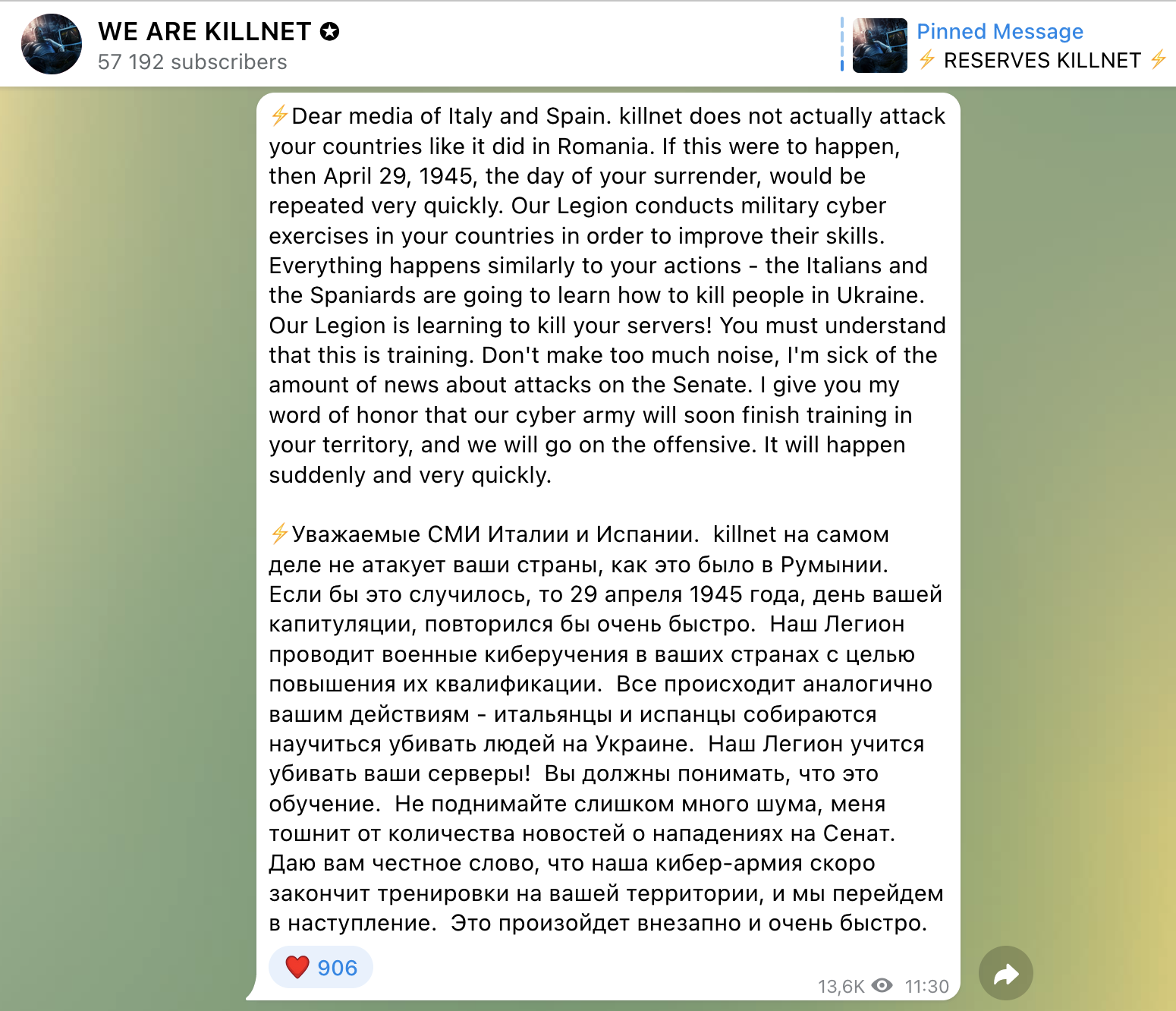
- May 14 at 22:48 CET – Legion incited their supporters to perform a DDoS attack towards the Eurovision voting system, giving some advice about how to proceed.
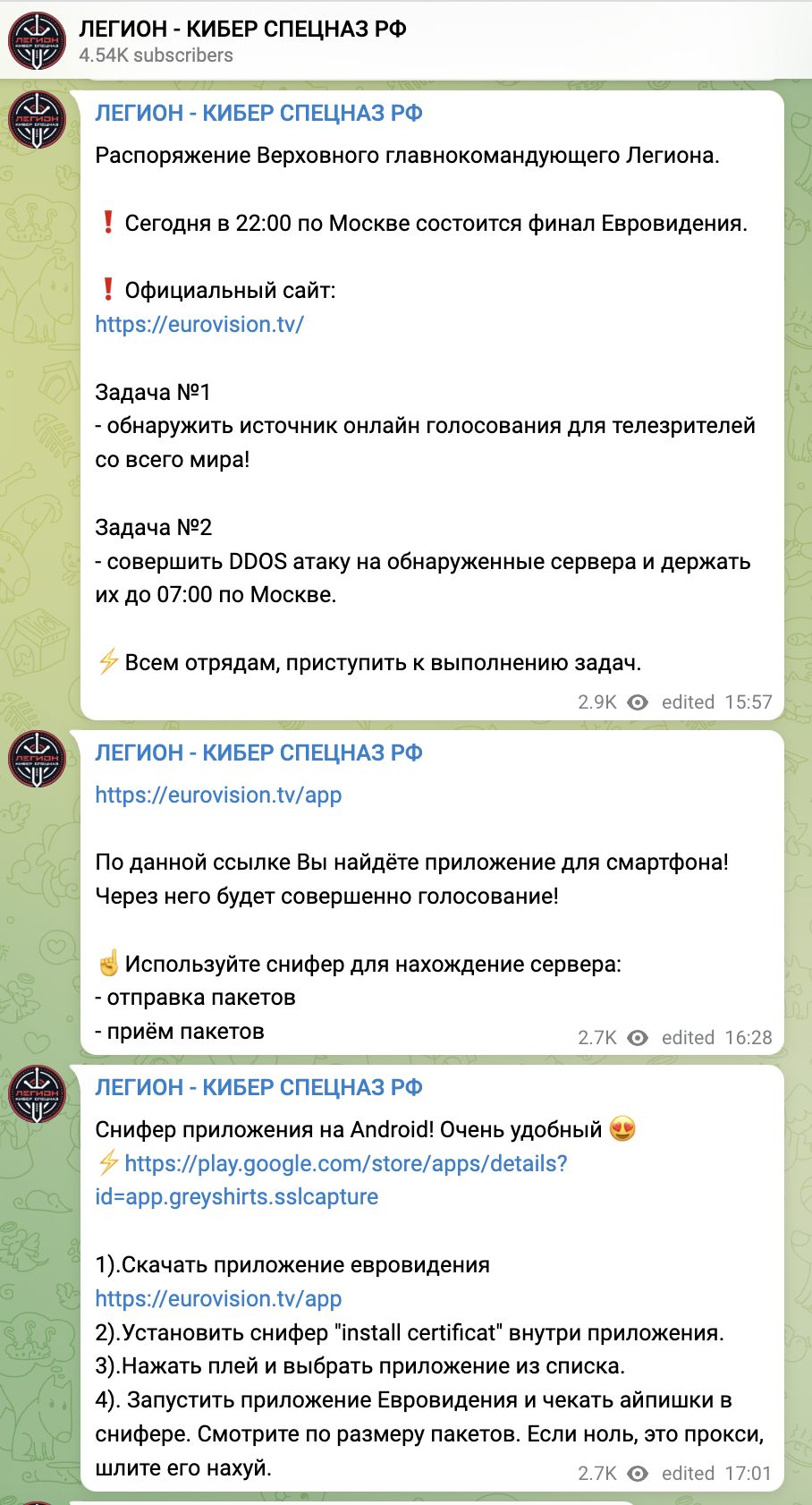
- May 15 at 7:51 CET – The Italian State Police released a tweet that they thwarted a cyber attack against Eurovision.
- May 15 at 22:48 CET – Killnet posted a video where they declared cyber war on 10 countries: US, UK, Germany, Italy, Latvia, Romania, Lithuania, Estonia, Poland, and Ukraine.

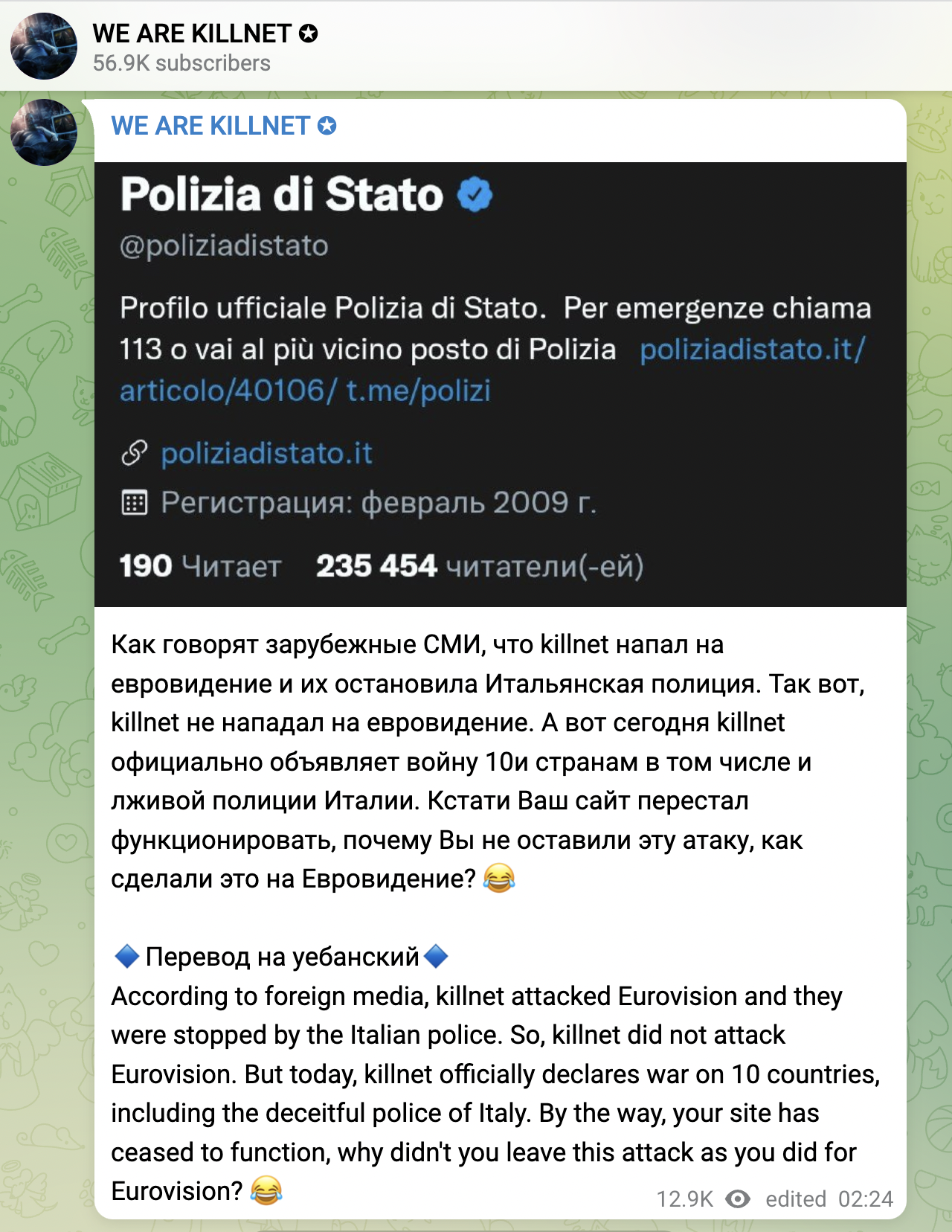
- May 16 at 1:29 CET – Killnet were ironic about the previous tweet and posted an image of what seems to be the website of the Italian State Police being hit by a DDoS attack.
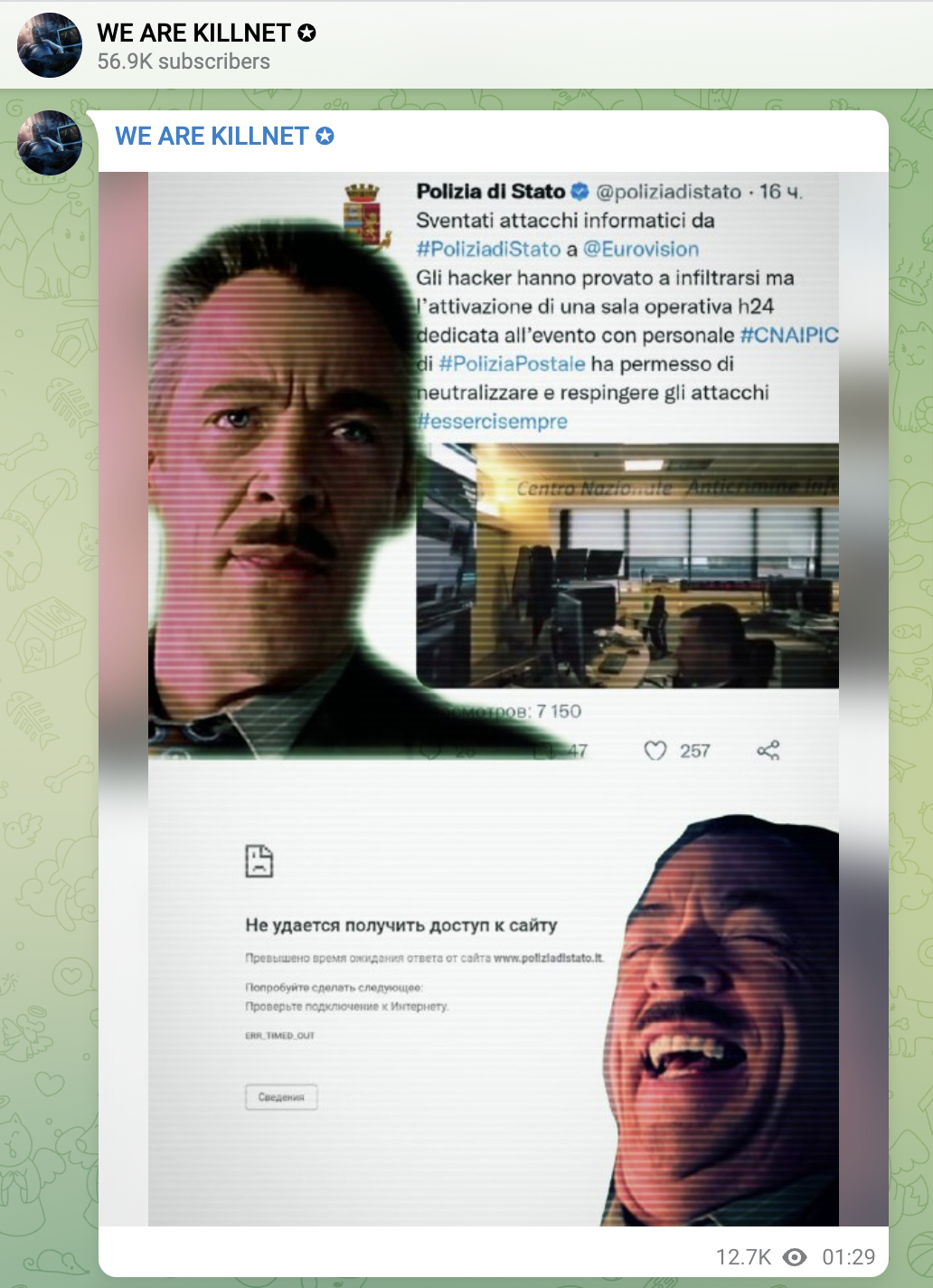
After one hour, as shown below, Killnet announced that they did not attack the Eurovision website and confirmed their war declaration, including the Italian State Police among the targets.
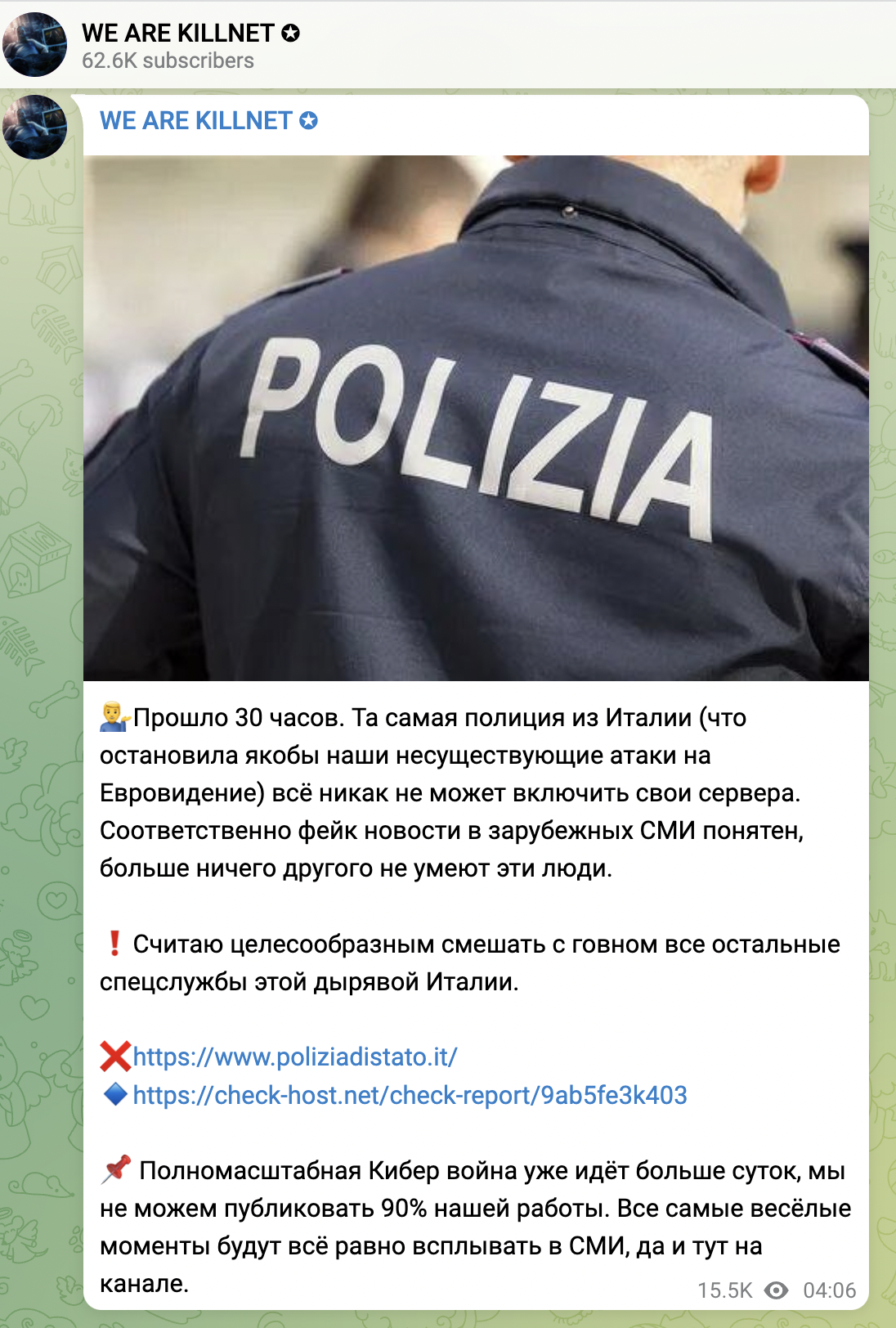
- May 17 at 4:06 CET – Killnet claimed another DDoS attack against the website of the Italian State Police. They added that ‘A full-scale Cyber War has been going on for more than a day, we cannot publish 90% of our work. All the funniest moments will still pop up in the media, and here on the channel.’
What we found about Mirai
The Sysdig Threat Research Team collected and monitored data about the Mirai group and similar Mirai malware for some time. During the last year, Mirai has always been active when we see it. In particular, in the last 90 days, we monitored more than 1,000 attacks from different types of malwares based on Mirai.
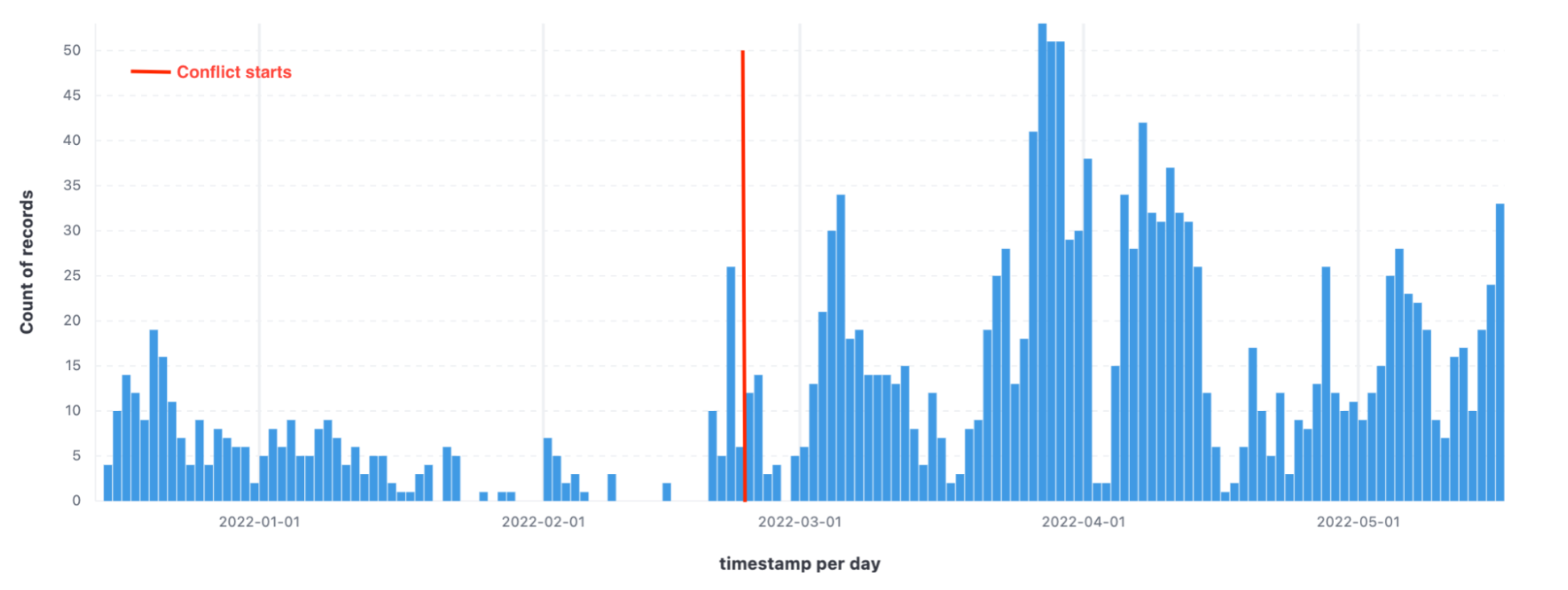
From the data collected, we can see a spike in Mirai attacks from the end of February till now. As we know, the conflict in Ukraine started on Feb. 24, as marked in the screen above. The correlation between these two events is likely and supported by a lot of information on DDoS attacks performed during these months.
Using the data collected, The Sysdig Threat Research team designed new detection rules to address the malicious behaviors related to malwares to provide better detection using Falco.
Detecting Mirai using Falco
The following rules have proven to be useful in detecting the activities of similar Mirai malwares:
- rule: Execution from /tmp
desc: This rule detects file execution from the /tmp directory, a
common tactic for threat actors to stash their
readable+writable+executable files.
condition: spawned_process and ((proc.exe startswith "/tmp/" or
(proc.cwd startswith "/tmp/" and proc.exe startswith "./" )) or
(proc.cwd startswith "/tmp/" and proc.args contains "./"))
output: "File execution detected from /tmp
(proc.cmdline=%proc.cmdline)"
priority: WARNING
tags: [mitre_execution]
- macro: curl_download
condition: proc.name = curl and
(proc.cmdline contains " -o " or
proc.cmdline contains " --output " or
proc.cmdline contains " -O " or
proc.cmdline contains " --remote-name ")
- rule: Launch Ingress Remote File Copy Tools in Container
desc: Detect ingress remote file copy tools launched in container
condition: >
spawned_process and
container and
(proc.name = wget or curl_download) and
not user_known_ingress_remote_file_copy_activities
output: >
Ingress remote file copy tool launched in container
(user=%user.name user_loginuid=%user.loginuid command=%proc.cmdline
parent_process=%proc.pname container_id=%container.id
container_name=%container.name
image=%container.image.repository:%container.image.tag)
priority: NOTICE
tags: [network, process, mitre_command_and_control]
- rule: Write below root
desc: an attempt to write to any file directly below / or /root
condition: |
root_dir and evt.dir = < and open_write and proc_name_exists and
not exe_running_docker_save and not zap_writing_state and not
maven_writing_groovy and not kubectl_writing_state and not
cassandra_writing_state and not calico_writing_state and not
rancher_writing_root and not runc_writing_exec_fifo and not
user_known_write_root_conditions and not
user_known_write_below_root_activities
output: File below / or /root opened for writing (user=%user.name
user_loginuid=%user.loginuid command=%proc.cmdline parent=%proc.pname
file=%fd.name program=%proc.name container_id=%container.id
image=%container.image.repository)
priority: ERROR
tags:
- mitre_persistence
Reference for “Write below root” where the full definition can be found: https://github.com/falcosecurity/falco/blob/master/rules/falco_rules.yaml#L1332
To avoid false positives, you can add exceptions in the condition to better adapt to your environment.
Conclusion
The kinds of cyber attacks that we’ve seen recently are not new techniques. What is new is the fact that these attacks were brought about by the political context of the current war between Russia and Ukraine.
The fact that those attacks managed to disrupt the network services of institutional servers implies that the Italian government and other institutions are not adequately prepared for these attacks, which can become increasingly impactful if we don’t manage to reinforce our web infrastructures.
However, we are far from calling it a cyber war. It’s not necessary to overstate the terms we use to describe those events. Instead, it’s important to create awareness of cyber-security through consistent and truthful information. Indeed, the communication part should not be underestimated.
Misinformation contributes to weakening our infrastructures from future attacks. Transparent communication of the incidents from the parties involved would help increase the general awareness about cyber attacks, and that is fundamental to preventing them.


