Cloud Detection and Response (CDR)
Securing the Cloud with End‑to‑End Detection
Traditional security measures struggle to effectively protect the dynamic and distributed nature of modern applications. Threats can now exploit vulnerabilities across various layers of cloud infrastructure, making it crucial to adopt a unified approach to security and threat detection.
Detect and Respond to Attacks at Cloud Speed
Adopt a unified, proactive approach to defending against evolving cloud threats through a consolidated cloud-native application protection platform (CNAPP) with Sysdig.
-
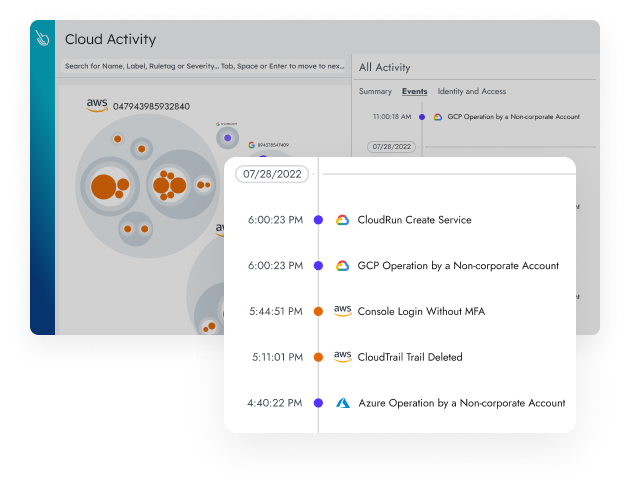
Real-Time Detection
Stop attacks up to 10 times faster.
-
End-to-End Coverage
Consolidate security across containers, cloud services, Linux/Windows servers, identities, and third-party apps.
-
Attack Path Visualization
Layer real-time detections on attack path analysis to reveal active lateral movement and visualize the attack’s reach.
End-to-End Detection
Go beyond mere system call detection in hosts and containers with comprehensive detection capabilities spanning the entire stack. Minimize risk at scale by employing horizontally distributed rule evaluation through Falco.
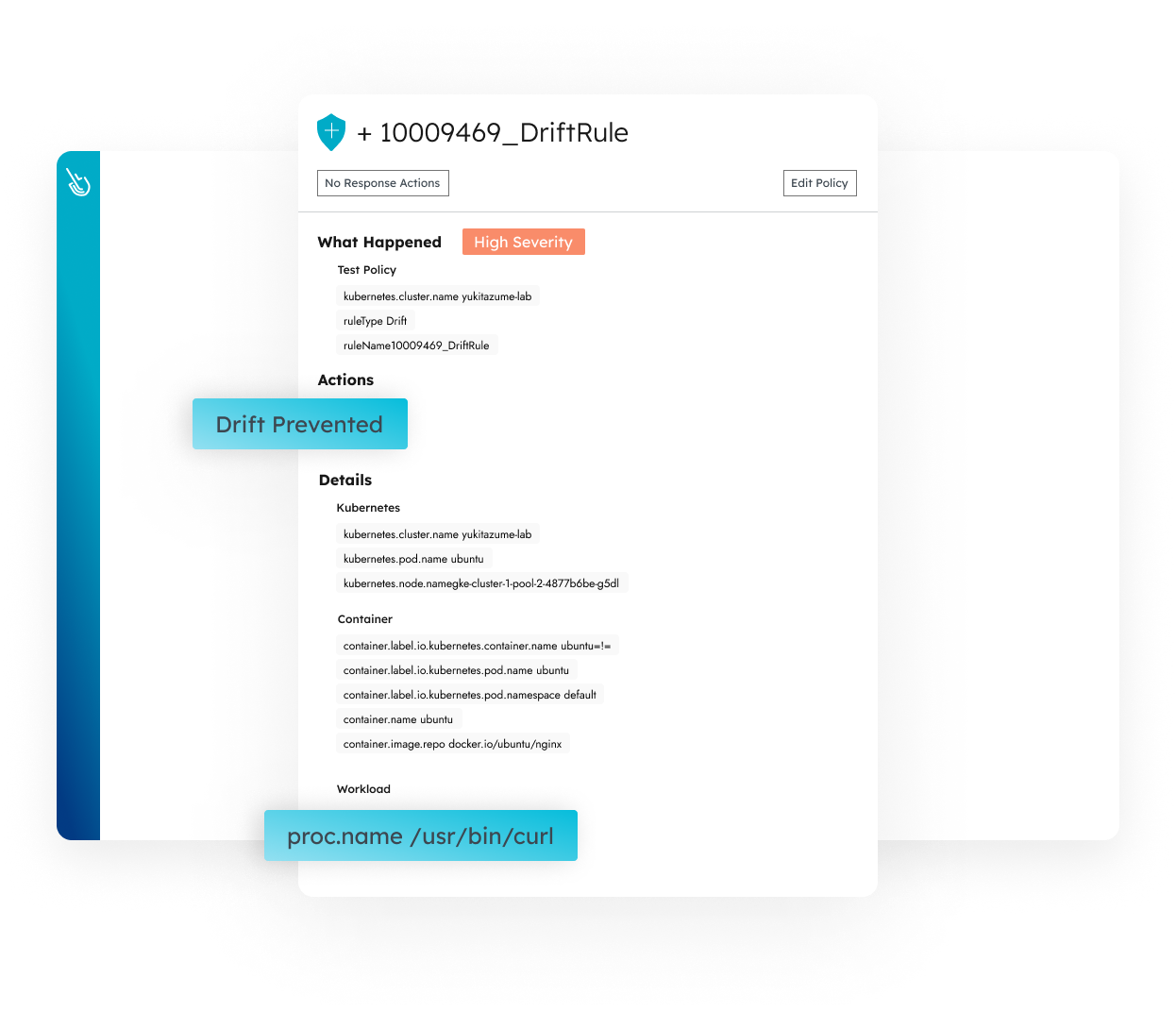
Container Drift Prevention
Block executables that were not in the original container. Stop malware, malicious users, and risky legacy practices by enforcing cloud-native immutability principles.
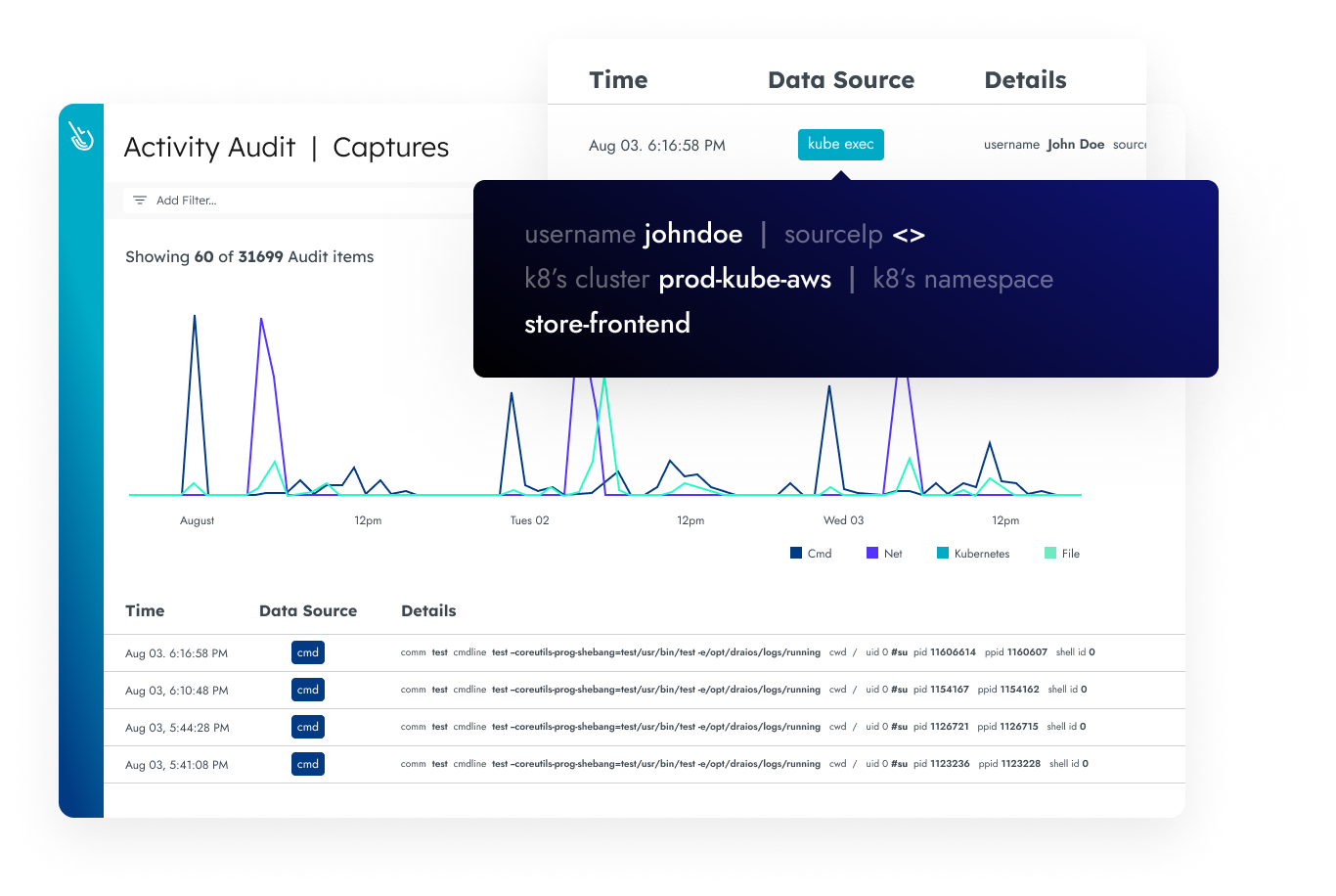
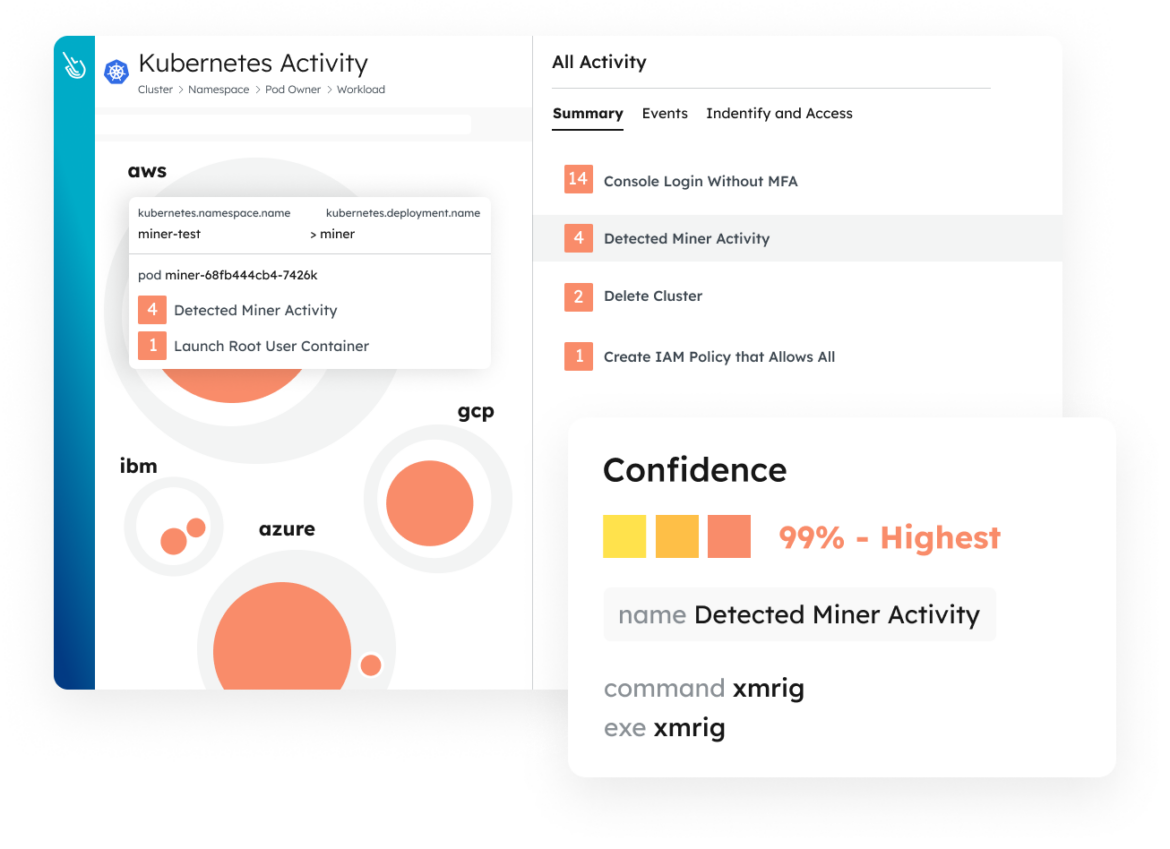
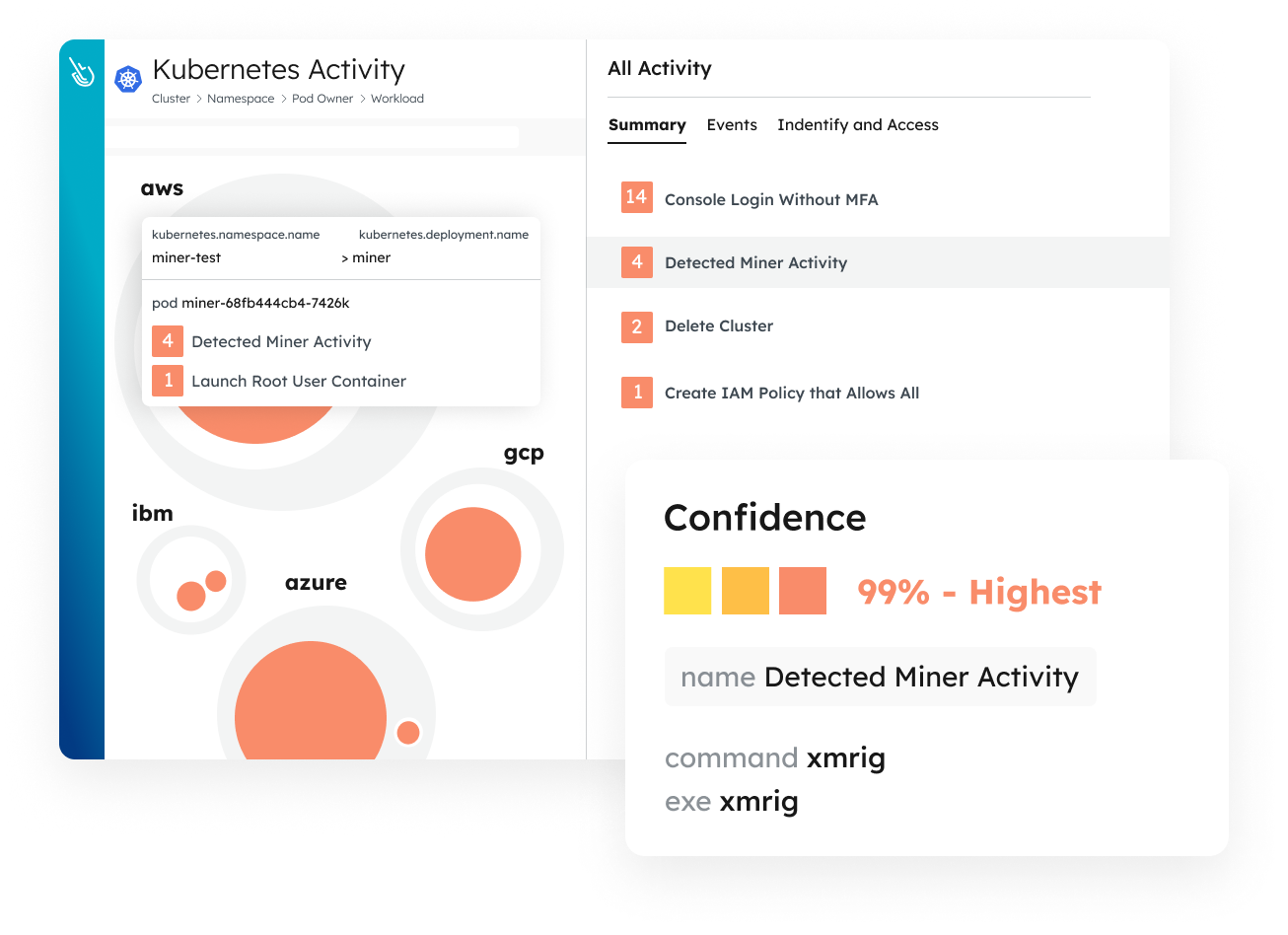
Live Threat Investigation and Incident Response
Accelerate investigation and response with rich context correlated across multiple domains. Capture detailed user and system activity including commands, network connections, file activity, and process lineage. Enrich events using container, host, Kubernetes, or cloud metadata.
Detection and Response Are Fundamental to CNAPP
Security teams need an integrated tool that provides continuous visibility into their entire environment. Sysdig’s cloud-native application protection platform (CNAPP) uses runtime insights to stop attacks across the application life cycle.
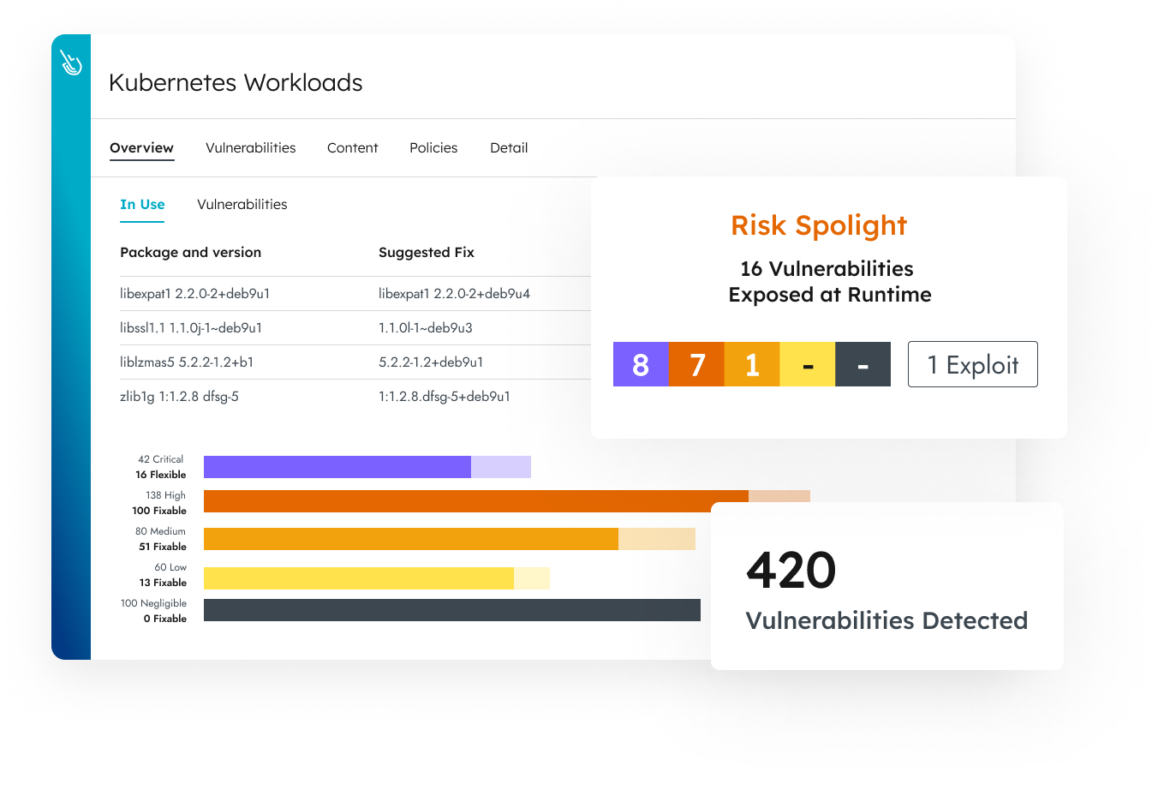
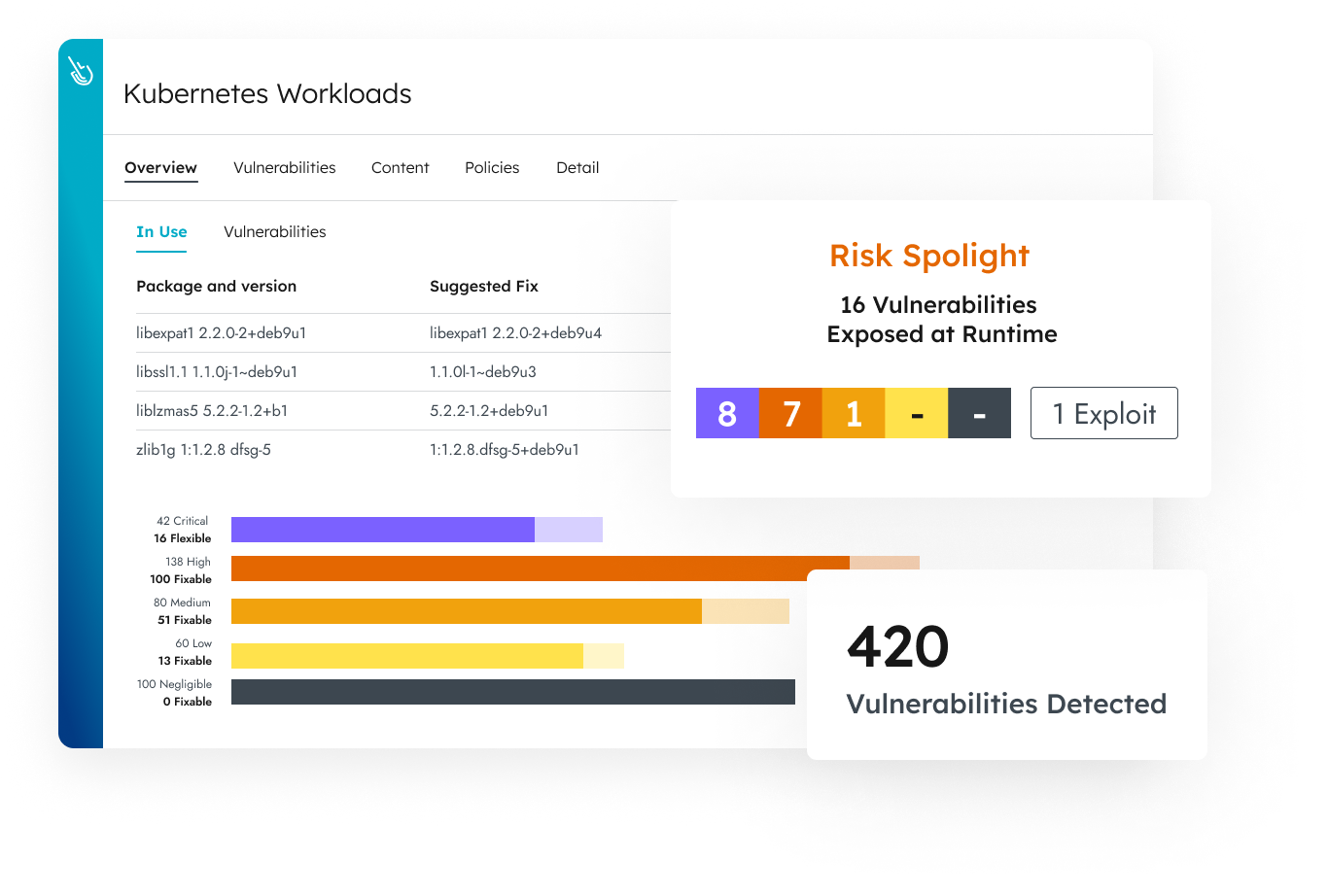
Vulnerability Management
Reduce vulnerabilities by up to 95% and boost developer productivity with actionable runtime insights through visibility into critical in-use packages.
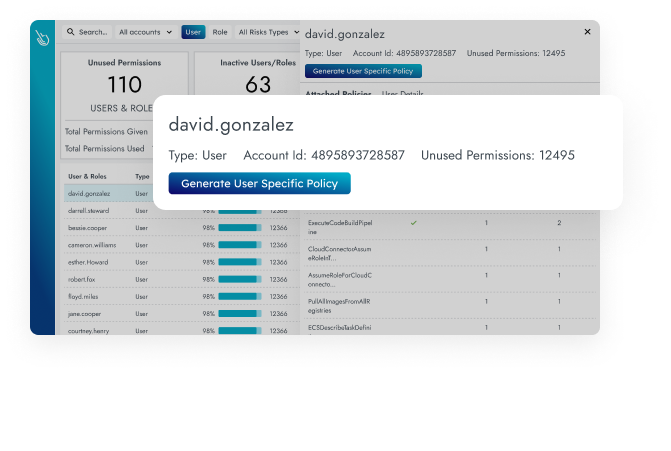
Entitlement Management
Close permissions gaps in less than two minutes by focusing on what is in use. Grant least-privilege access with a single click.
Posture Management
Instantly detect posture drift and eliminate blind spots. Build guardrails to keep your infrastructure safe from human error.
Detection and Response
Stop attacks up to 10x faster. Detect threats in real time anywhere in the cloud fabric with an end-to-end approach.
Built on the Open Source Solution for Threat Detection
Falco is the open source runtime security solution for real-time detection of threats and anomalies across containers, Kubernetes, and cloud services.
Through deep visibility of your entire cloud-native infrastructure, Falco enables cloud-native application protection platforms (CNAPP) with end-to-end detection and powers Sysdig’s prioritization based on in-use packages.
Related Content
Take the Next Step!
See how you can secure every second in the cloud.