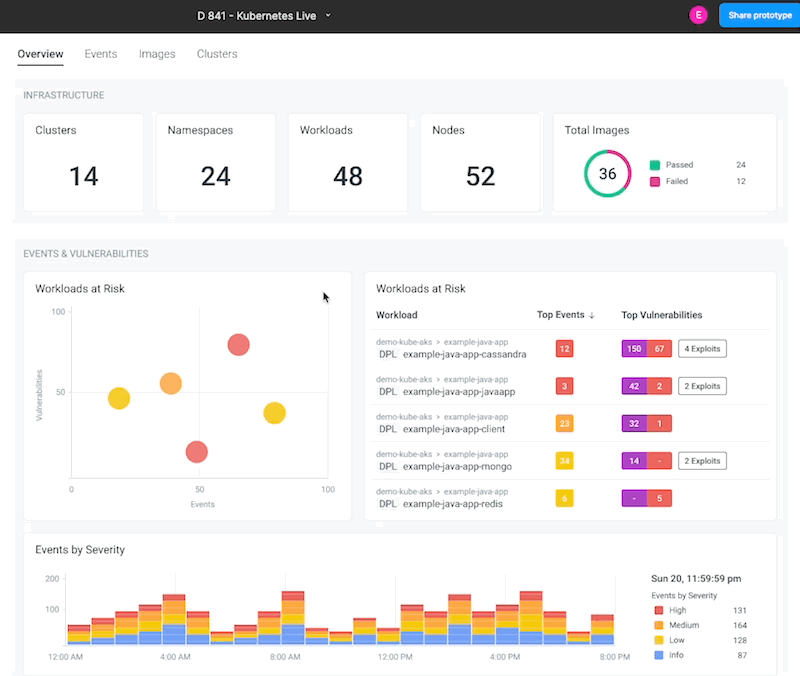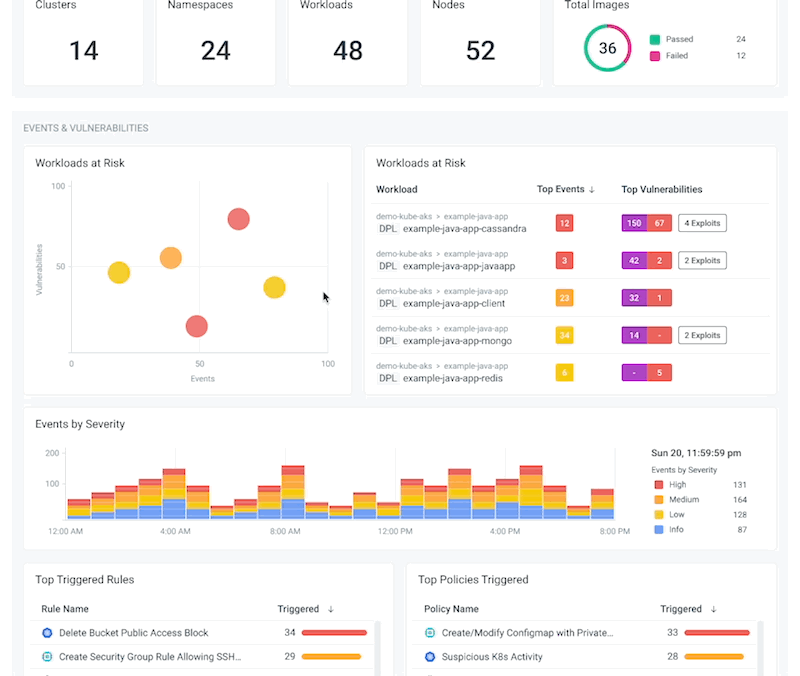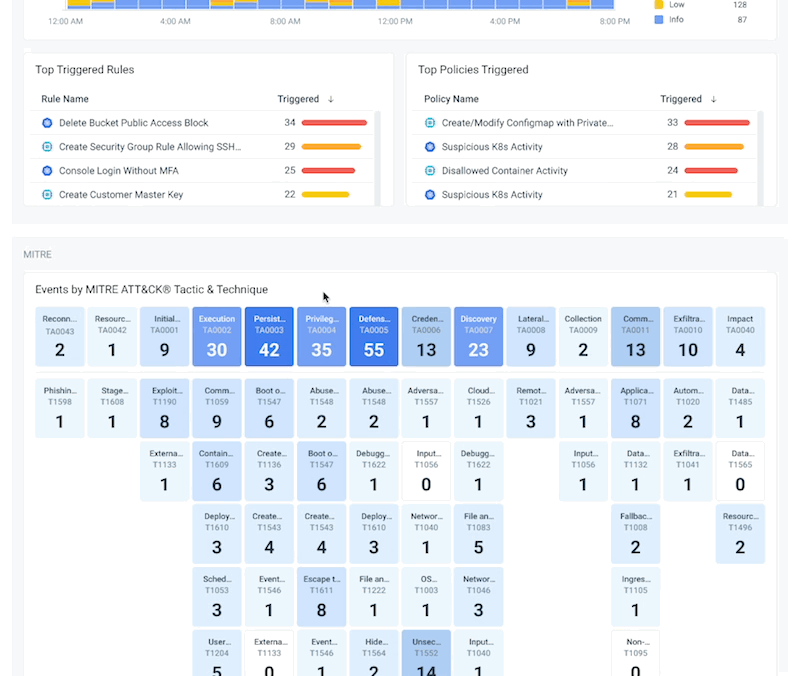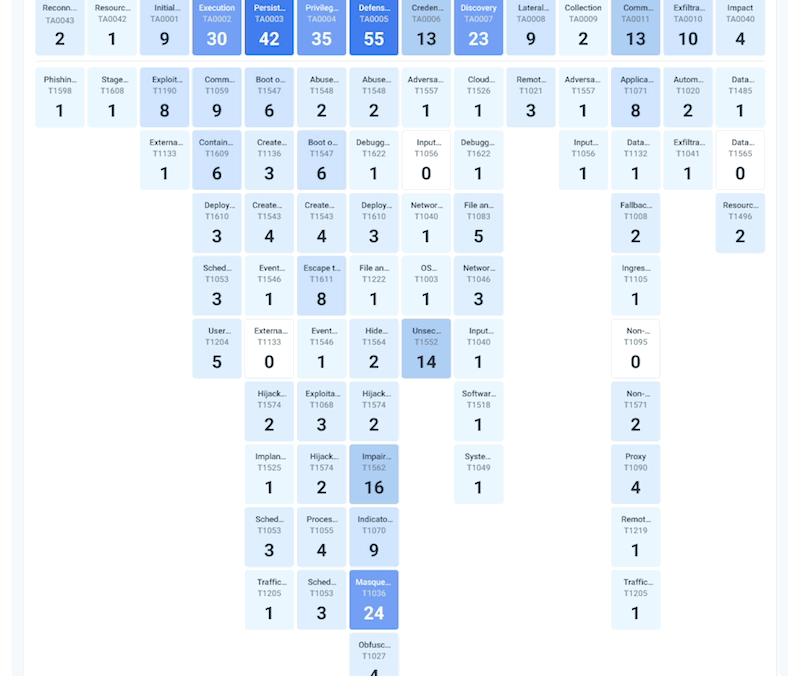
Securely Run Containers and Kubernetes
Manage vulnerabilities, configurations, and compliance risks. Detect and respond to threats in containers and Kubernetes
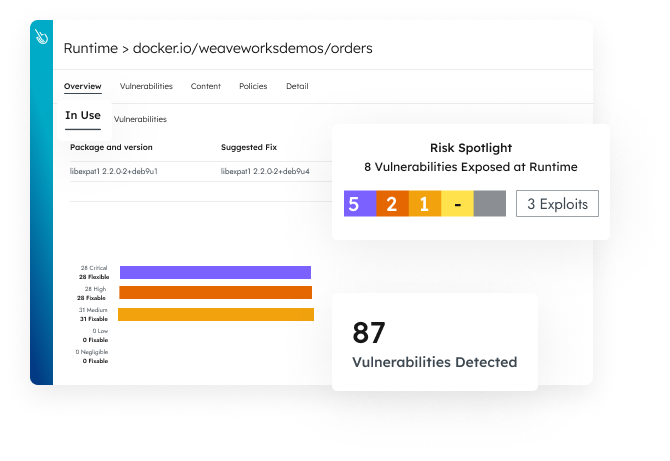
Container Security
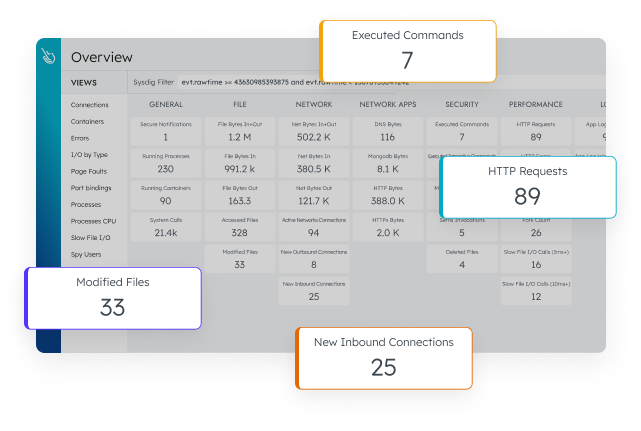
Reduce risk with image scanning integrated into CI/CD pipelines and runtime. Secure runtime with out-of-the-box managed policies based on Falco and ML. Know what happened and why with an audit trail.
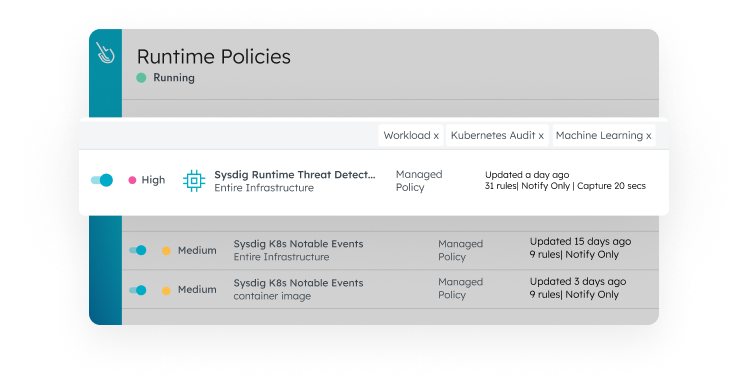
Kubernetes Security
Block risky images and fix configuration and permissions. Detect malicious Kubernetes API activity. Apply consistent policies with OPA.
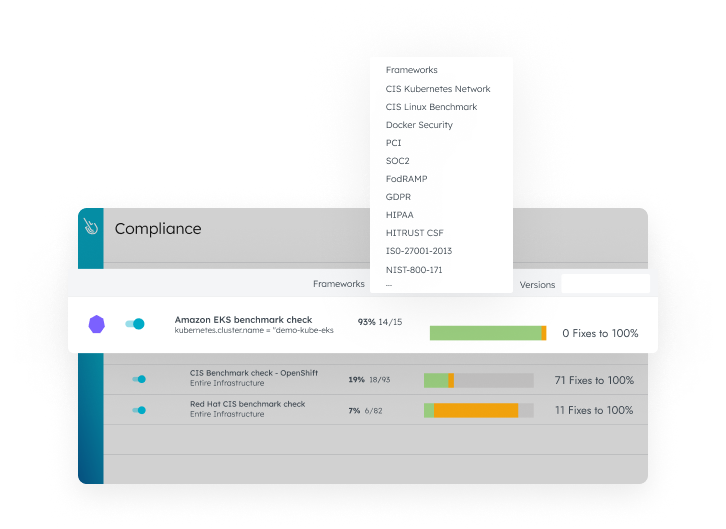
Compliance
Validate CIS Benchmarks and compliance (PCI, NIST, SOC2) for container and Kubernetes environments. Automate compliance and governance with OPA policies.
From shift left to shield right, security at cloud speed
SaaS-First Platform Integrated Into Your DevOps Workflow
Take the Next Step!
See how you can secure every second in the cloud.