Welcome to another monthly update on what’s new from Sysdig. Our team continues to work hard to bring great new features to all of our customers, automatically and for free!
First and foremost, Merry Christmas, God bless you with prosperity and happiness, Feliz Navidad, Joyeux Noël, Frohe Weihnachten, 聖誕快樂, عيد ميلاد مجيد, Buon Natale, Prettige Kerstdagen, メリー クリスマス, Счастливого Рождества! Hanukkah Sameach and general holiday greetings to all! Whatever you may or may not be celebrating, we wish you a joyous holiday season from all of us at Sysdig. I know that, for many, this will extend into the new year, so Happy New Year as well! If you are working or on call through the holiday period, I hope your alerts are calm, your applications remain healthy, and no security incidents occur! I can imagine that the vast majority of us are really looking forward to the new year!!!
This month, our team has been heavily focused on getting ready for the festive period. Many of our customers have a change-freeze over Christmas and New Years (many of our retail related customers start this from just before Black Friday), so we’ve been spending time focusing on many of the backend tasks that don’t represent visible changes. As I’m sure you’re all aware, this is just as important as new shiny features! So this month, we have no new features to shout about directly in Monitor or Secure, but we do have a number of other updates for you in our other components.
As always, please go check out our own Release Notes for more details on product updates, and ping your local Sysdig contact if you have any questions about anything covered here.
Finally, don’t miss the What’s new in Kubernetes 1.20? blog, which is a great recap of our favorite features or changes to watch out for. If you have any concerns about the Docker deprecation notice, there’s a great explanation on the Kubernetes website.
Sysdig Secure
Falco rules update
The latest rules in the Sysdig UI are now v0.10.3, and the following are changes from v0.10.2, which was covered last month:
- Ensure that
falco_rules_local.yamlis evaluated against all of the default files. - Ensure that the logs clearly show which files are being evaluated.
- Add new rule
Container Run as Root Userto policyInadvised Container Activity. - Add
crioandmultusto listuser_known_change_thread_namespace_binaries.
You can use this container image to push these updates to your environment.
Sysdig agents
Sysdig Agent
The latest Sysdig Agent release is 10.8.0. Below is a diff of updates since 10.6.0 which we covered last month.
New Features & Enhancements
- Policies and Baselines V1 Messages Are Deprecated: Sysdig agent no longer supports the old backend message types that were originally deprecated in on-prem release 2.4.0 (August 2019).
- Load Falco Rules on a Separate Thread: Partially load Falco rules in the background to avoid interrupting event processing.
- Workflow for Unacknowledged Metrics: The agent is restarted if a metrics acknowledgment hasn’t been received from the Sysdig backend components in eight minutes. This can happen if networking issues cause the agent to believe it has an active connection when the backend has closed the connection.
- Run Single Agent RPM Per Host: Prevents multiple agent services from being launched on the same RHEL-based hosts.
- Improved handling of network errors.
Fixes
- OpenShift Hardening Guide Correctly Detects Master and Worker Nodes: Running the OpenShift Hardening Guide functionality of the Kubernetes Benchmark will now correctly detect master vs. worker nodes, and run the appropriate Benchmark tests.
- Agent No Longer Terminates Non-Agent Processes: In some rare situations when process creation in the Agent’s JMX module failed due to issues caused by resource limits, it could inadvertently stop unrelated processes running on the host. This problem has been fixed.
- Filtering Long Container Labels: Filtering long container labels works as expected with no parsing failures or undesirable agent restarts.
- Reports Correct Value for the
kubernetes.pod.restart.rateMetric: Fixed an issue that could causekubernetes.pod.restart.ratemetric to be incorrect. - Scraping Prometheus Metrics While Multiple Process Listening to Port 9090 Concurrently: Fixed a problem that caused scraping Prometheus metrics to fail when another process was listening to the TCP port 9090 on a host interface.
- StatsD Metrics Reports Correct Value: Fixed a problem that caused Statsd metrics to be double the expected value.
- Agent v0.92.1RC Fails to Create Process List: A failure during the
/proctree search byscap_proc_add_from_proc()will be suppressed to returnSCAP_SUCCESS. Processing will continue and the gap will be filled in the process table later when the first event for the particular process arrives. - Environment Variable Hash Reports Correct Value: Fixed an issue that could cause the environment variable hash, associated with the exported processes in audit tap, to have an incorrect value.
- Undesired JMX Availability Check: Fixed an issue that could cause
sdjagentprocess in the agent to consume a high CPU. The process no longer performs JMX checks for availability every second, which had been causing high CPU consumption.
Helm chart
The Helm Chart 1.11.1 has been released. Te following is a diff of changes since 1.10.4, which we covered last month.
Changes
- Node Image Analyzer is now deployed by default (
nodeImageAnalyzer.deployset to true by default). - Explain all Node Image Analyzer settings in
values.yamlandREADME, and link to the official Sysdig docs. - Use the latest image from Agent (10.8.0).
- Use the latest image from Node Image Analyzer (0.1.7).
- Change
check_certificatetossl_verify_certificatein NIA settings to sync with NIA configmap.
Node image analyzer
Version 0.1.7 was released and includes a minor fix that caused image analysis errors on some OpenShift clusters configured in FIPS mode.
Node image analyzer can be installed as part of the Sysdig Agent install.
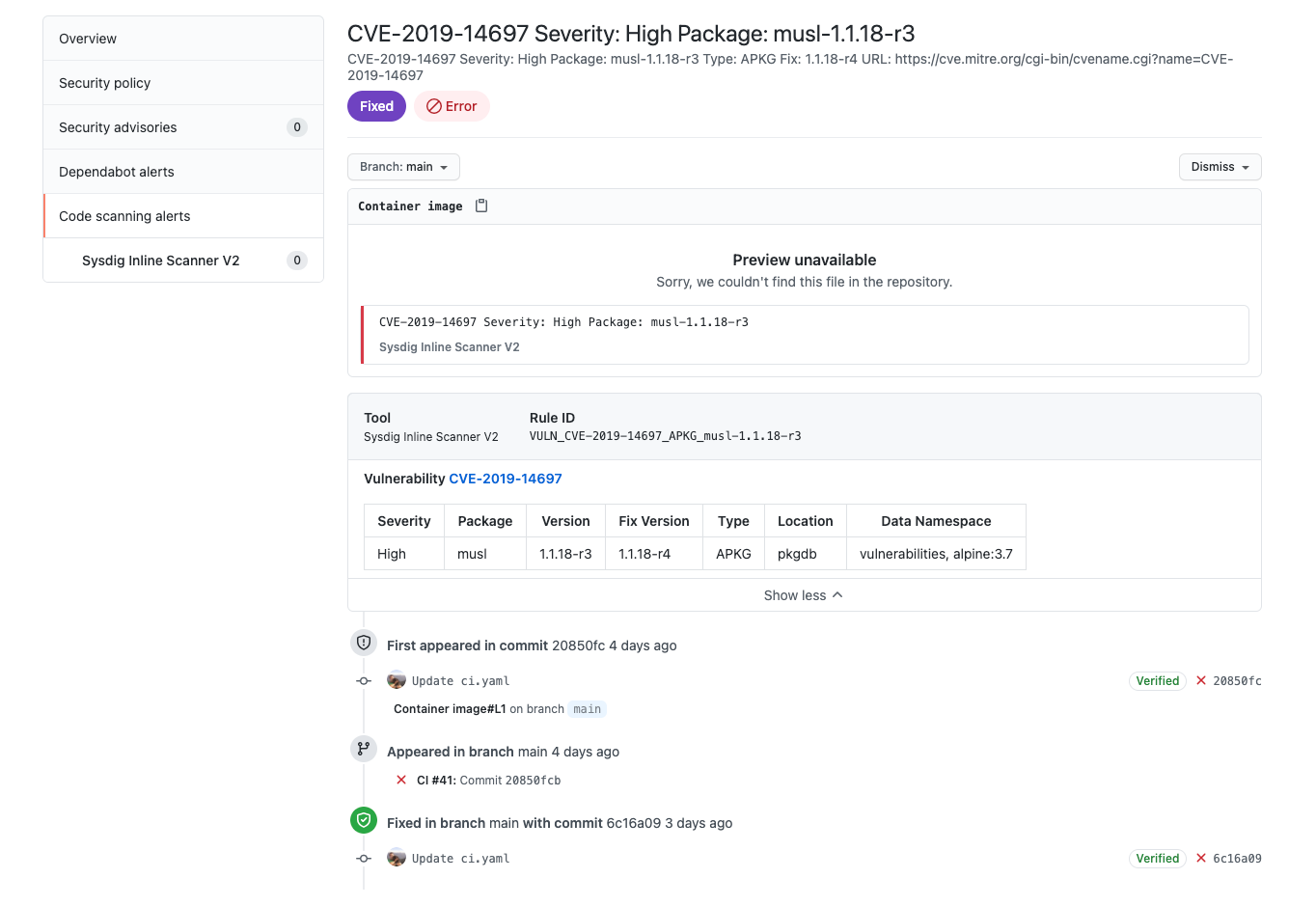
Inline scanning engine
Version 2.2 is the latest version. Below is a diff of changes since v2.0, which was the latest last month:
New
- The vulnerability report information has been added to the container output, pairing with the image details and policy evaluation.
- When scanning an image using the digest pullstring, it will be stored using the truncated digest as a tag.
- Ability to analyze scratch-based images.
Fixed
- Fixed a permissions issue when running the container with a user other than root.
- Fixed a bug retrieving the PDF output for previously scanned images.
- Addressed several vulnerabilities found in the inline scanner container.
See also: Integrate with CI/CD Tools.
SDK, CLI and Tools
Sysdig CLI
v0.7.0 was released and includes the following diff updates from v0.6.6.
Features
- Split policy event feed endpoint in old and new
- For more information: https://sysdiglabs.github.io/sysdig-platform-cli/usage/policy/events.html
Documentation fixes
- Remove description from site in the docs
- Events documentation:
https://sysdiglabs.github.io/sysdig-platform-cli/usage/event/
https://sysdiglabs.github.io/sysdig-platform-cli/usage/event_v1/
Python SDK
v0.14.7 was released. The following is a diff of updates since v0.14.4, which we covered last month.
Features
- Allow to retrieve runtime policy events by ID.
- Add the type parameter to the create_alert docs.
- Add
get_image_scanning_resultsmethod to SdScanningClient.
Bug Fixes
- Return the correct policyID and policyName in
get_image_scanning_results.
Terraform provider
v0.5.6 has been released. Below are the diff changes from v0.5.4, which we covered last month:
- Update docs with falco rule priority changes
- Change falco rule priority to info
- Update note warning message
Falco VS code extension
v0.1.0 is still the latest release.
Sysdig cloud connector
v0.4.0 of the Sysdig cloud connector was released. The following is a diff of updates since v0.3.0, which we covered last month:
- Added support for GCP AuditLog.
- Publish events on Secure Event Feed.
- Skip PSP simulations when retrieving from Sysdig Secure.
- Fix scheduling times on pull-based ingestors.
Sysdig Secure inline scan for Github Actions
v3 was released this month, and includes the following features:
- Action v3 uses the new secure-inline-scan 2.x with better performance and more input options. See the Inline Scanner 2.2 release notes.
- Create a check run on analysis, and add annotations with the failing gates and found vulnerabilities.
- Add SARIF report output to allow integration with Github Code scanning.
PromCat resources
As a reminder, Promcat.io is a curated set of Prometheus exporters that Sysdig will provide full support for to our customers. It is publicly available so everyone can still make use of it, although we will only be able to offer official support to our customers.
The following new Prometheus exporters have been added to the website:
- Added Rancher.
- Added AWS RDS.
We also made the following enhancements:
- Changed ETCD Integration. No federation needed.
- Improvements in dashboards, and integration of Kubernetes control plane.
- Improved scope variables in PostgreSQL Sysdig Dashboards.
Deprecation notices
None to announce this month!
Sysdig training updates
We continue to provide up-to-date and cutting edge training featuring our products and surrounding technologies. The latest featured contents are:
- Learn how to define your Security infrastructure as code: A new Use Case video (seven minute watch) has been published, demoing how to setup and configure a Secure GitOps workflow with Terraform, GitHub Actions, and Sysdig Secure.
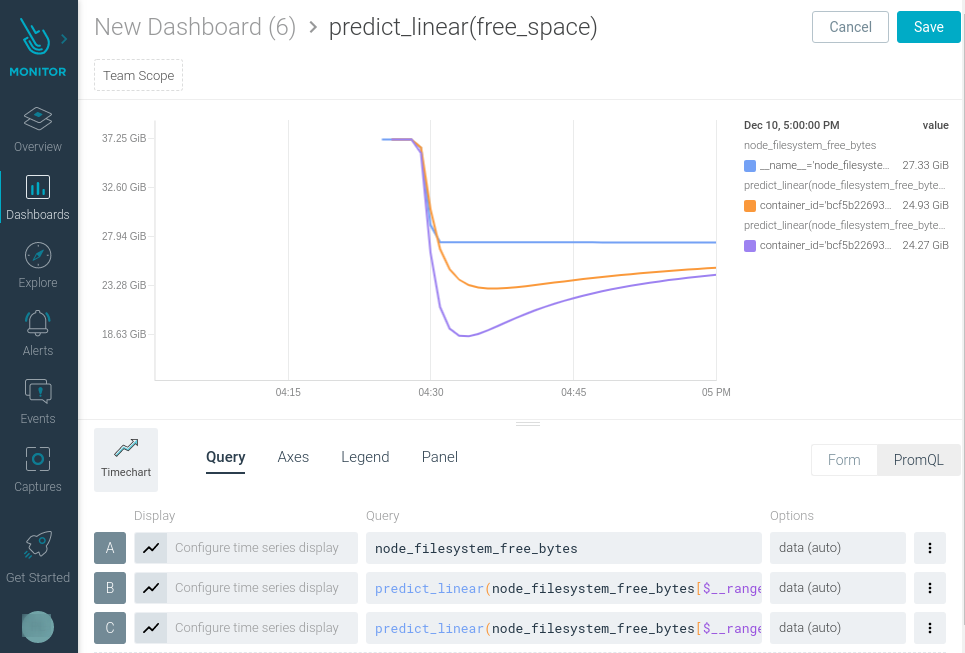
- Extend Sysdig with Prometheus: Two new interactive learning labs have been released.
- Learn how to use
predict_linear()to visualize and predict your free disk space. - Learn how to configure a
blackbox_exporterwith Sysdig to monitor your service availability and meet SLAs. The two labs can be completed in less than 10 minutes!
- Learn how to use
New website resources
Blogs
- Cooking the perfect holiday ham with IoT, Prometheus, and you
- How to monitor an Oracle database with Prometheus
- Preventing malicious use of Weave Scope
- Your team is running containers, but are they secure?
- Security, compliance, and visibility for Amazon EKS-D
- What’s new in Kubernetes 1.20?
- Zoom into Kinsing
- Securing Kubernetes clusters with Sysdig and Red Hat Advanced Cluster Management
- Open Source is Taking Over Security
Webinars
- Seeing is Securing Containers on AWS Fargate
- Zero Trust Network Security for Containers and Kubernetes
- AWS Re:Invent activity


