Welcome to the September edition of What’s New in Sysdig in 2022! I’m Ayu Shah, Principal Sales Engineer based out of San Francisco Bay Area. I joined Sysdig a little over six months ago and it has been an exciting journey to say the least! I have worn many hats in my career, from Software Engineering to Sales and everything in between. I am excited to share some updates to What’s New in Sysdig for this month!
September has, as usual, been a busy month, and Sysdig announced many new features. In Sysdig Monitor, we announced the release of Google Chat Channel Integration, Stacked Bar Time Chart and Case sensitive filtering. In Sysdig Secure, we released Custom OPA based Policies for CSPM, 2 new Falco rules and Insights for Hosts and Containers, among other things. Each of these are discussed in detail below.
Sysdig Monitor
Google Chat Channel Integration
A new Google Chat channel integration is available to all Sysdig Monitor SaaS customers. It allows you to send alerts to Google Chat using webhook integration.
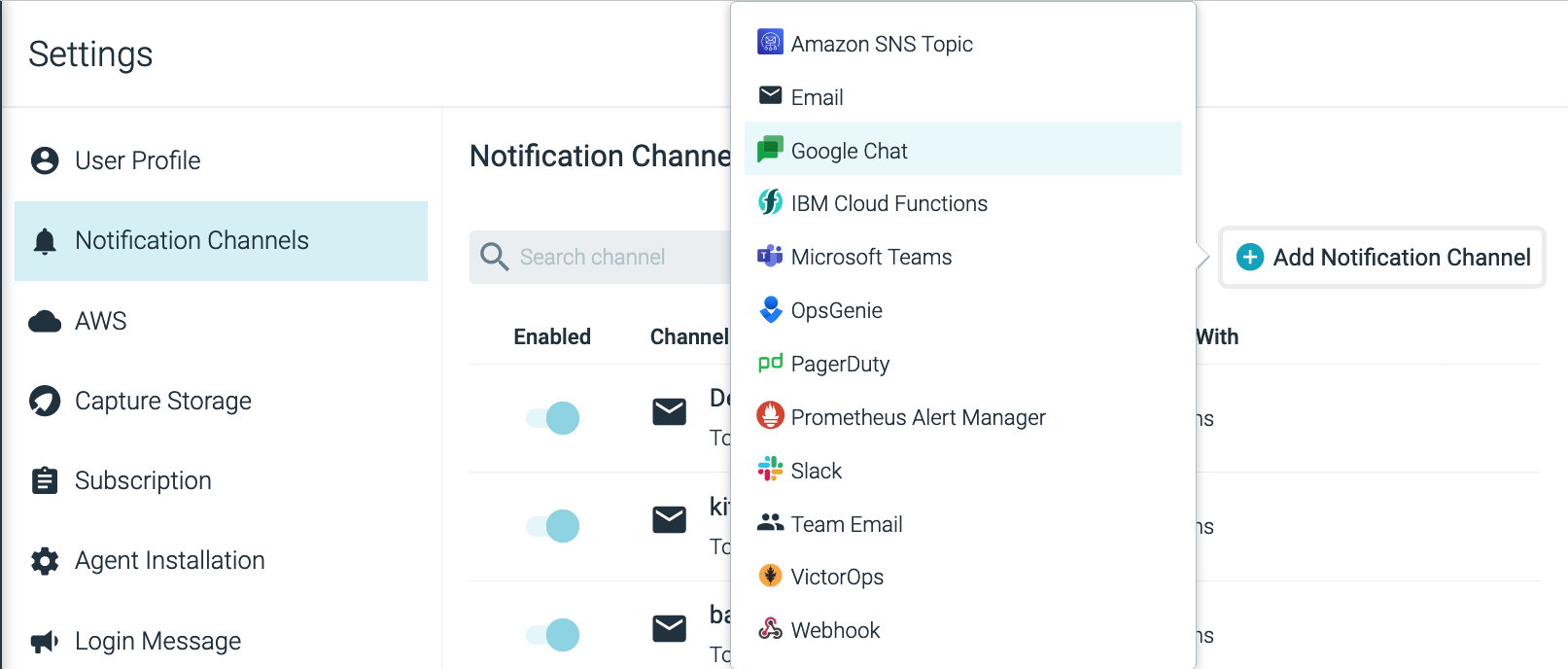
For more information, see Configure a Google Chat Channel.
Stacked Bar Time Chart
We’ve released a new display option to display Time Charts as bars. This is suitable when viewing sporadic metrics, or a metric occasionally drops to 0.
Case sensitive filtering
From now on, Sysdig will align with Prometheus on time series filtering, meaning that label names in filter expressions will be case sensitive.
For more information, see the September Release Notes.
Sysdig Secure
CSPM Policies – Custom OPA based Policies (Preview)
This is a technical preview release, and the feature is open for all customers. This feature includes:
- Clone an existing policy and edit its metadata
- Create, Edit & Delete a custom policy
- Create, Edit & Delete requirements in a custom policy
- Link & Unlink available controls to policy requirements
You can read more about the feature in Sysdig’s documentation.
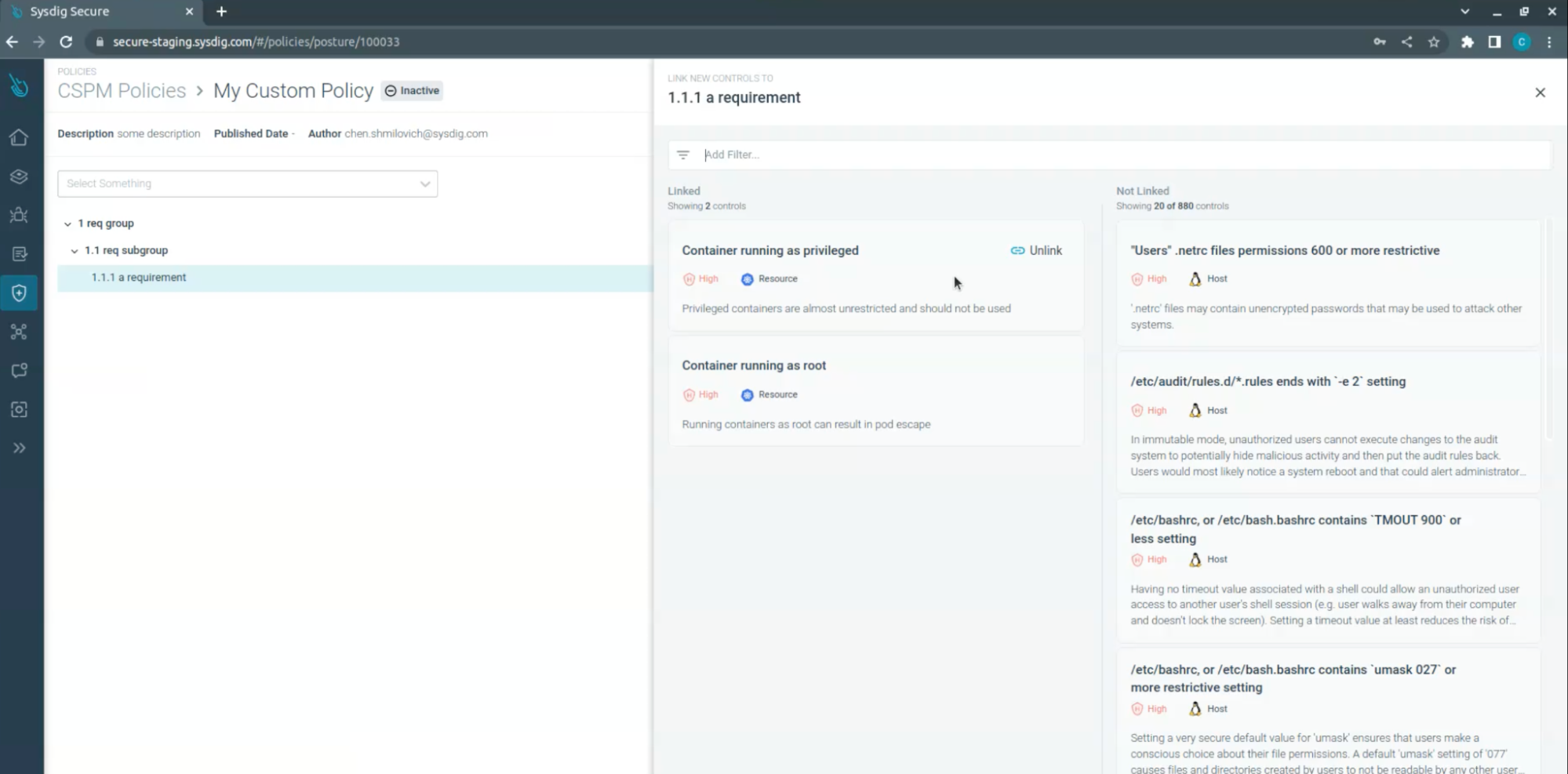
New Falco Rules
The Sysdig Threat Research Team has released two new rules this week for Secure.
Scripting Language Execution below dev
Scripts, such as shell or Python, are often used by attackers once on a compromised system. One way to hide these scripts is to place them in an uncommon directory where administrators may not check. The /dev directory is an example of these uncommon directories. If a script is found in the /dev directory, it should be investigated.
Policy: Sysdig Runtime Notable Events
False Positive Chance: Low
Suspicious Kernel Parameter Modification
Once an attacker is on a system, they may need to modify it in order to advance their goals. This could include disabling certain security features or prepping a system to be more efficient for more tasks such as cryptomining. If kernel parameters are changed during runtime, they should be checked to make sure they are legitimate.
Policy: Sysdig Runtime Notable Events
False Positive Chance: Medium
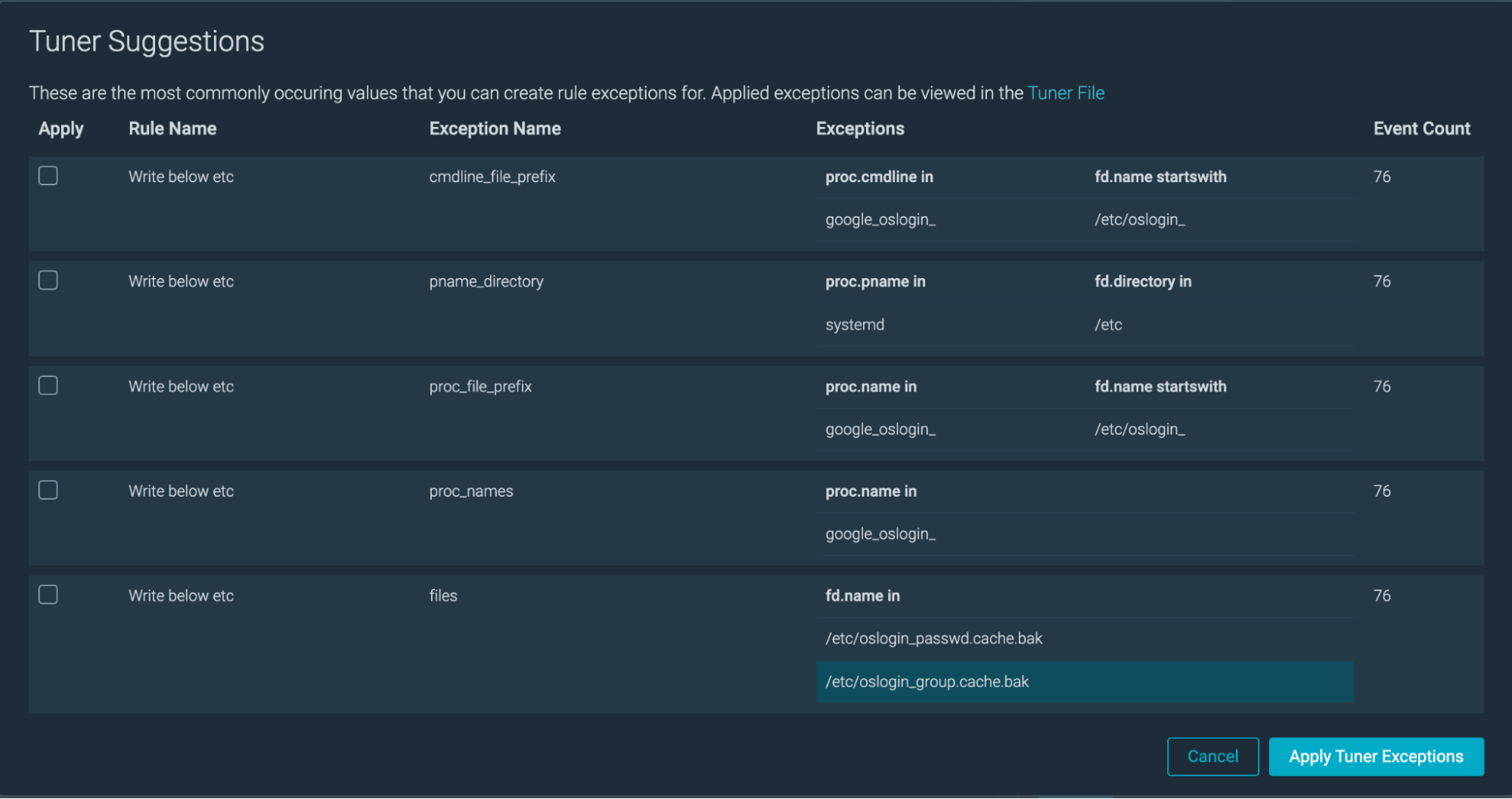
Insights for Host & Containers
We have released “Host & Containers” views for insights. Customers who are running non K8s environments can now get similar sights at the Host and Container level. This feature also gives customers the ability to create exceptions from those workloads using the insights tuner.
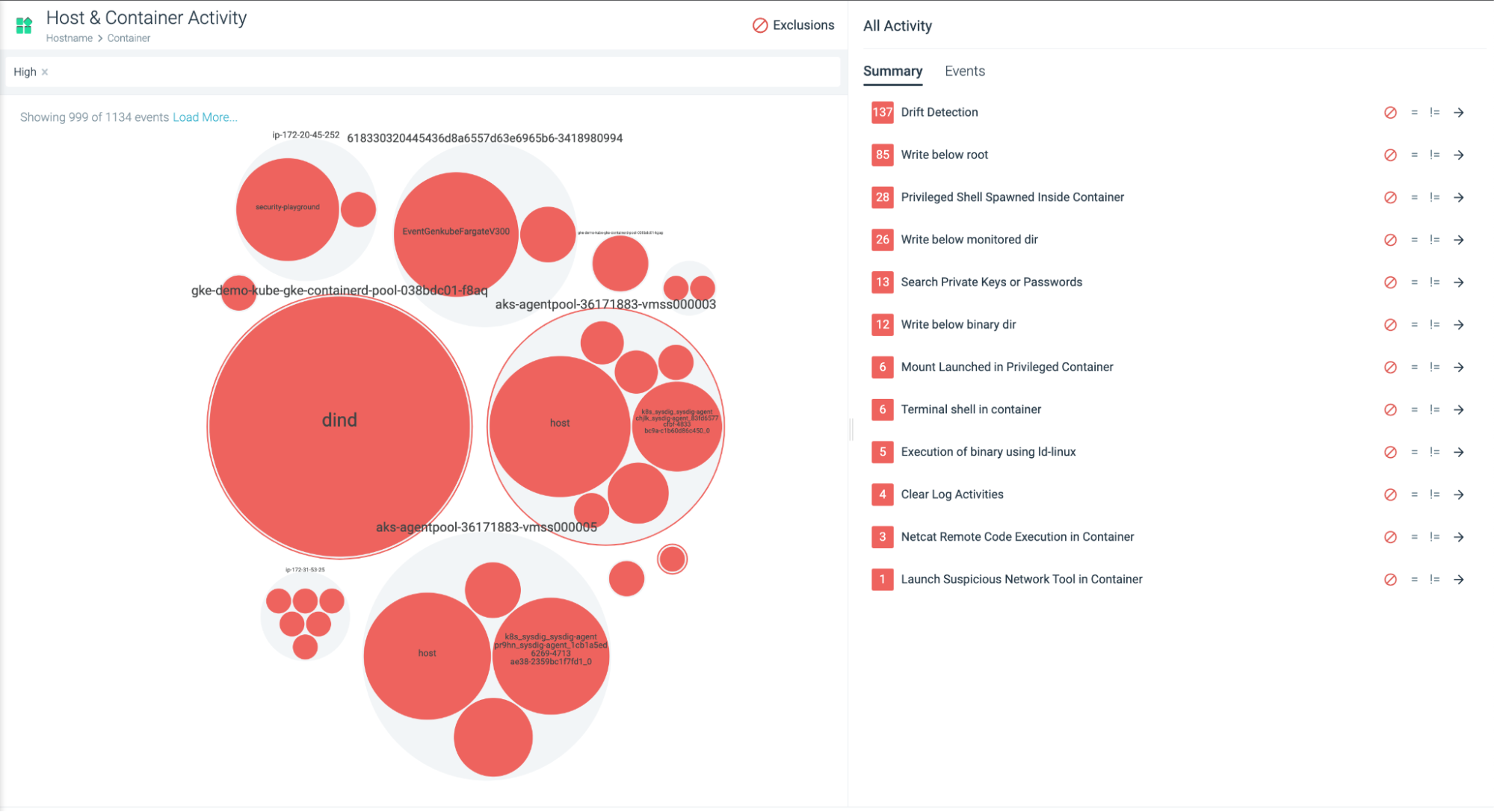
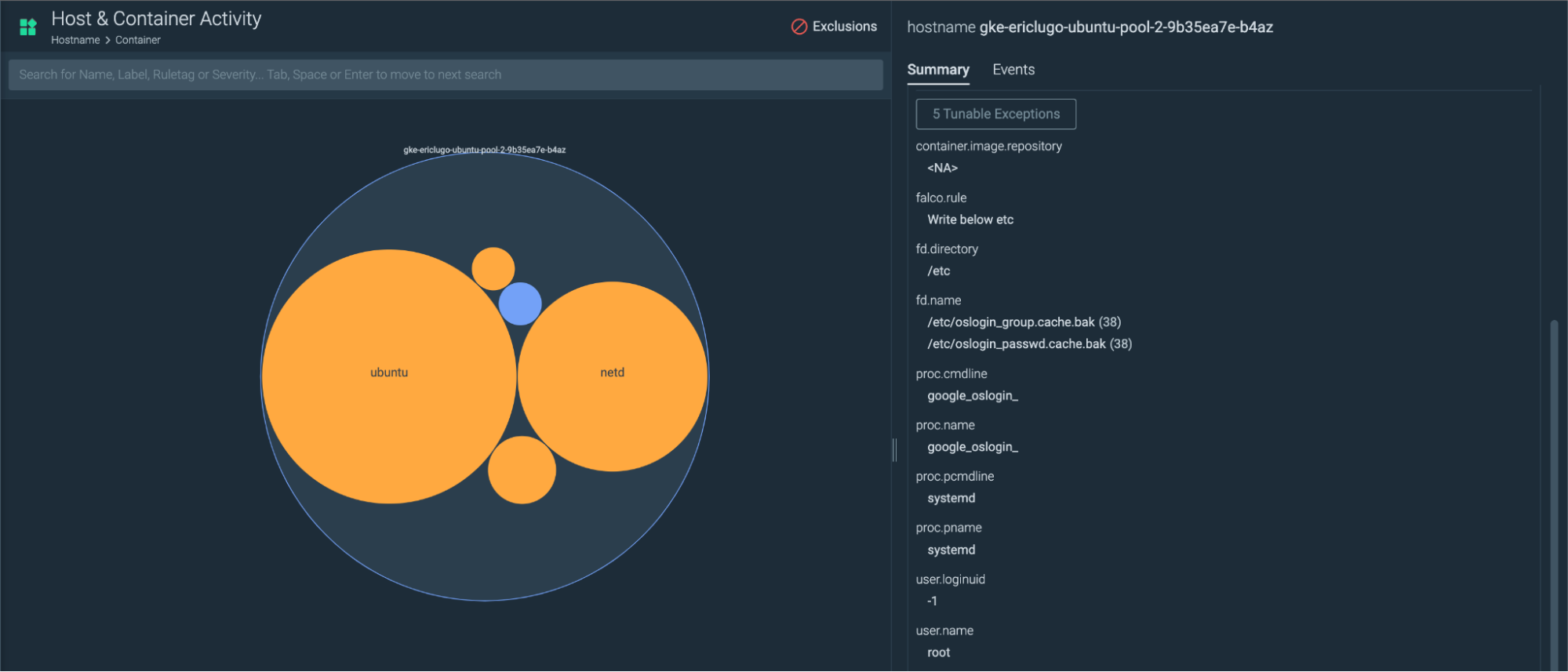
SAML Single Logout
SAML single logout feature is now available on all SaaS (non-IBM) regions. Furthermore, we have added support for single logout integration with Okta.
Disable a Rule within a Policy
Customers can now disable (and re-enable) individual rules within threat detection policies. This allows:
- Using a subset of rules within a managed policy or managed ruleset without giving up the ability to receive new rule updates.
- Temporarily disabling a noisy rule until the cause is investigated or an appropriate exception is put in place.
Actionable Compliance – Control Library (Preview)
Sysdig is pleased to announce the Preview release of CSPM Control Library in Actionable Compliance. This is a technical preview release and the feature is open for all customers. This feature includes:
- Visibility of all available controls
- Filter for specific controls by control attributes
Read more about the feature here.
Falco Rules
v0.85.0 is the latest version. Here there are some highlights of the changes from v0.80.2, which we covered in August:
Added the following rules:
- Scripting Language Execution below dev
- Suspicious Kernel Parameter Modification
Further details and the full changelog can be found on Sysdig documentation.
Sysdig Agents
Agent Updates
The latest Sysdig Agent release is v12.8.1.. Below is a diff of updates since v12.8.0, which we covered in our August update.
Defect Fixes
- Fix Vulnerabilities in Promscrape V1
- Upgraded the Prometheus version and resolved vulnerabilities in promscrape v1.
- Remove Symbolic Link to /etc in the Agent Container
- Read information on users and groups from /host/etc/passwd and /host/etc/group when agent is running as a container.
- Show Falco Events as Expected
- Fixed a problem when the Falco output string for a rule is cut on the first absent or empty field
Please refer to our v12.8.1 Release Notes for further details.
SDK, CLI, and Tools
Sysdig CLI
v0.7.14 is still the latest release (Download Link). The instructions on how to use the tool and the release notes from previous versions are available at the following link:
Python SDK
v0.16.4 is still the latest release.
Terraform Provider
v0.5.40 is still the latest release.
Documentation – https://registry.terraform.io/providers/sysdiglabs/sysdig/latest/docs
Github link – https://github.com/sysdiglabs/terraform-provider-sysdig/releases/tag/v0.5.40
Terraform Modules
- AWS Sysdig Secure for Cloud has been updated to v0.9.7
- GCP Sysdig Secure for Cloud has been updated to v0.9.3
- Azure Sysdig Secure for Cloud has been updated to v0.9.2
Note: Please check release notes for potential breaking changes
Falco vs. Code Extension
v0.1.0 is still the latest release.
Sysdig Cloud Connector
AWS Sysdig Secure for Cloud has a new release! v0.16.13 includes new features and some minor fixes.
Features include:
- GuardDuty Ingestor
Check the full list of changes to get the full details.
Admission Controller
Sysdig Admission Controller has been updated to v3.9.7.
Documentation – https://docs.sysdig.com/en/docs/installation/admission-controller-installation/
Runtime Vulnerability Scanner
The new vuln-runtime-scanner has been released to GA state with v1.2.8.
Documentation – https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/runtime
Sysdig CLI Scanner
Sysdig CLI Scanner has been released to v1.2.8.
Documentation – https://docs.sysdig.com/en/docs/sysdig-secure/vulnerabilities/pipeline/
Image Analyzer
Sysdig Image Analyzer has been updated to v0.1.19.
Host Analyzer
Sysdig Host Analyzer is still set to v0.1.10.
Documentation – https://docs.sysdig.com/en/docs/installation/node-analyzer-multi-feature-installation/#node-analyzer-multi-feature-installation
Sysdig Secure Inline Scan for Github Actions
The latest release is still v3.4.0.
Sysdig Secure Jenkins Plugin
Sysdig Secure Jenkins Plugin has been updated to v2.2.5. It now supports the new Sysdig scanning engine. The legacy engine is still supported but will be deprecated soon.
Prometheus Integrations
Integrations:
- Fix: Improved OpenShift HAProxy configuration to use ClusterRole.
- Fix: Improved documentation with the official integrations names.
- Fix: Fixed documentation page for Application Integrations.
- Fix: In Istio agent configuration, removed metrics filtering in envoy job. This was preventing other custom metrics merged into the Envoy sidecar from being sent.
Dashboards and alerts:
- Fix: Typo in metric for ALB and ELB AWS Metrics Stream services.
- Fix: Improved RDS text for PostgreSQL.
- Fix: Improved calculation of used vs request/limits in Kubernetes Capacity Planning dashboard.
- Fix: Improved promQL in kubernetes dashboards to avoid artifacts happening on ephemeral containers.
- Fix: Deleted duplicate dashboard templates.
- Refactor: Updated Kubelet metrics (Kubernetes >1.19) in dashboard templates:
- kubelet_running_container_count –> kubelet_running_containers.
- kubelet_running_pod_count –> kubelet_running_pods.
- Fix: Removed duplicated dashboard templates.
Promcat.io
- Fix: Improved OpenShift HAProxy configuration to use ClusterRole
Sysdig On-Premise
The 5.1.0 On-Premise minor release is now official. Here are some highlights for this minor release:
- Added support for Kubernetes versions 1.22 and 1.23.
- Added a pre-flight check to verify the kubectl and K8s versions of the cluster with the context provided by the customer.
- API documentation for Sysdig Secure is now enabled by default.
- Feature Enhancement: Falco Exceptions – Create Exception Objects to a Default Rule.
- Various bug fixes.
The full release notes can be found here: Sysdig Docs or Github .
New Website Resources
Blogs
- Sysdig 2022 Threat Report: Cloud-native threats are increasing and maturing
- How to meet 24 Google Cloud Platform (GCP) security best practices using open source
- Image Scanning with GitHub Actions
- How to monitor OpenShift with Sysdig Monitor
- Understanding Kubernetes Evicted Pods
- Threat news: TeamTNT targeting misconfigured kubelet
- Container Image Scanning for Azure Pipelines with Sysdig
- Fixing potential security issues in your Infrastructure as Code at the source with Sysdig
- KSPM and How to improve your Kubernetes Security Posture
- Prioritize Alerts and Findings with Sysdig Secure
- IBM LinuxONE and Sysdig: Building cyber resilient systems in hybrid cloud environments
- How Onna Technologies uses Snyk & Sysdig to secure the SDLC while saving time and money
- AWS Security Groups Guide
- The Quiet Victories and False Promises of Machine Learning in Security
- 26 AWS Security Best Practices to Adopt in Production
- Turbocharge your Azure security and compliance posture with Sysdig
- What is Kubernetes CrashLoopBackOff? And how to fix it
- Introducing Managed Policies for Sysdig Secure
- Sysdig launches Partner Technical Accreditation Program
- SBOM 101 – All the questions you were afraid to ask Software Bill of Materials
Webinars
- August 24 – 5 Easy Ways to Secure Images & Prioritize Risk from Source to Run On AWS
- Sept. 06 – How Does Your Kubernetes Environment Stack Up?
- Sept. 13 – How to Improve Security for Cloud-Native App Platform in 3 Easy Steps for Azure
- Sept. 15 – Becoming a Cloud Security Ninja: Sharpen your Cloud Threat Detection Sword with Machine Learning
- Sept. 20 – 5 Best Practices to Prevent, Detect, and Respond to Threats Lurking Within Your Azure Cloud Workloads
- Sept. 22 – Becoming a Cloud Security Ninja: Slice Through Alerts and Prioritize What Matters
- Sept. 27 – The Ultimate Strategy to Achieve PCI Compliance and Stay That Way on Azure
- Sept. 28 – CrashLoopBackoff + Four Other K8s Troubleshooting Tips Everyone Should Know (EMEA)
- Sept. 29 – Becoming a Cloud Security Ninja: Slice Your SIEM Costs by Pre-Processing Cloud Logs
- Oct. 4 – 5 Steps to Secure Containers and Prioritize Risk on GKE and Anthos
- Oct. 18 – How to Detect and Respond to Threats Lurking in your GKE Workloads
- Oct. 20 – Is Your SecOps Ready for Cloud and Containers?
- Oct. 25 – Not your Parent’s Cloud Security: Real-time Cloud Threat Detection for GCP
Tradeshows
- Sept. 26-28, Infosec World, Florida, USA
- Oct. 6 – Virtual
- Oct. 10-12, ISC2, Las Vegas NV
- Oct. 11-13, Google Next, San Francisco CA
- Oct. 13-14 – Virtual
- Oct. 24-28, Kubecon NA 2022, Detroit MI
- Nov. 28 – Dec. 2, AWS Reinvent, Las Vegas NV
Education


