Server Threat Detection
Securing Servers in the Cloud Requires a Cloud Centric Approach
Modern threats can exploit a Linux or Windows server as an entry point to compromise an organization’s entire cloud infrastructure. Detecting and responding with cloud speed is critical, but relying on traditional endpoint solutions creates blind spots.
Traditional EDR Isn’t Built for Cloud
Traditional EDR solutions struggle to detect and offer actionable context to understand cloud-native attacks. Sysdig is purpose-built for securing cloud-native services by offering multi-domain correlation to combat advanced cloud attacks that can move from servers to cloud, or from cloud-native services to servers.
Narrow Detection and Configurability
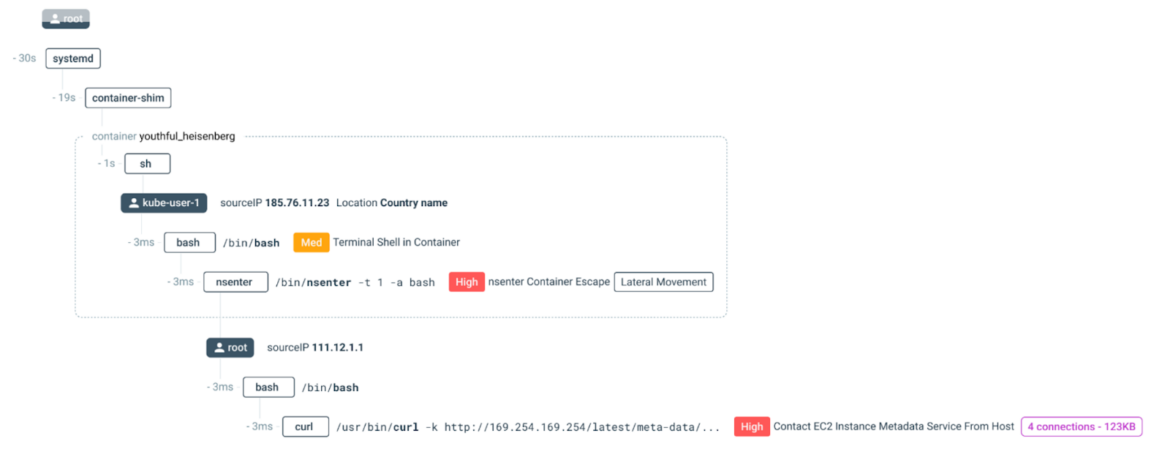
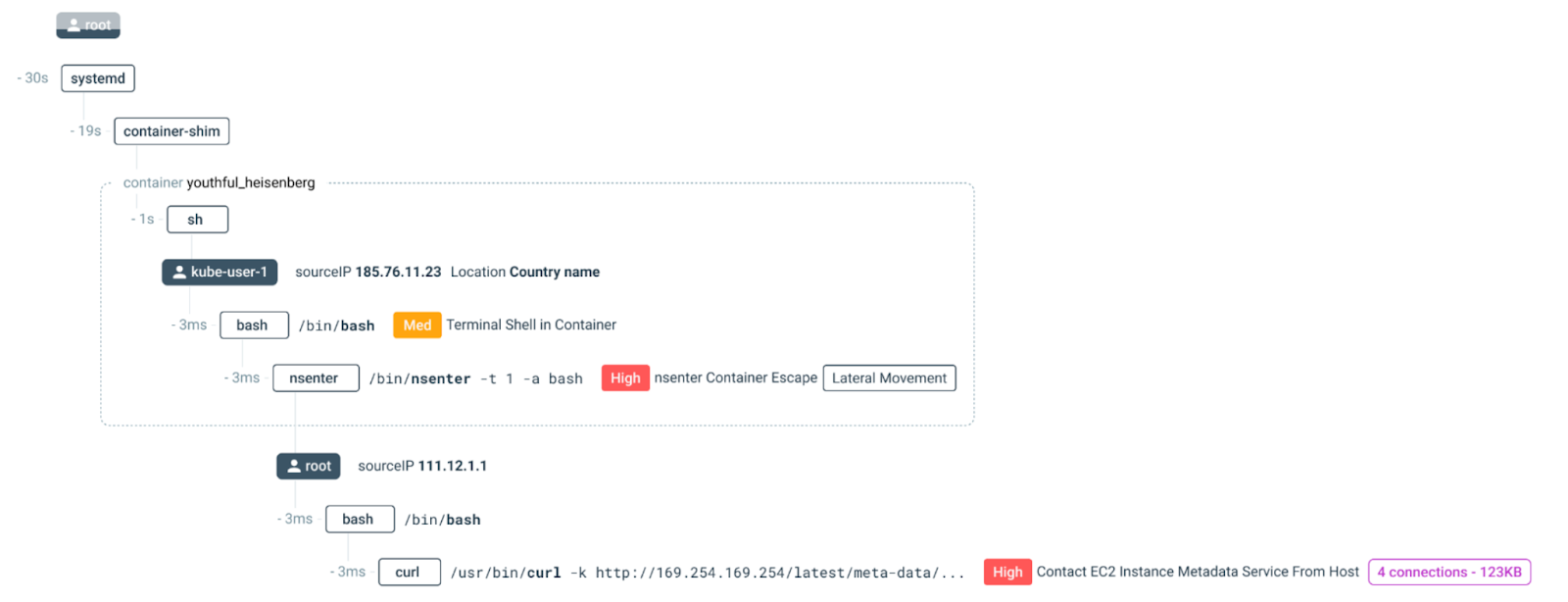
EDR tools employ a rigid black box approach and struggle to detect post-exploitation activity in the cloud (e.g., lateral movement).
Fragmented Investigation
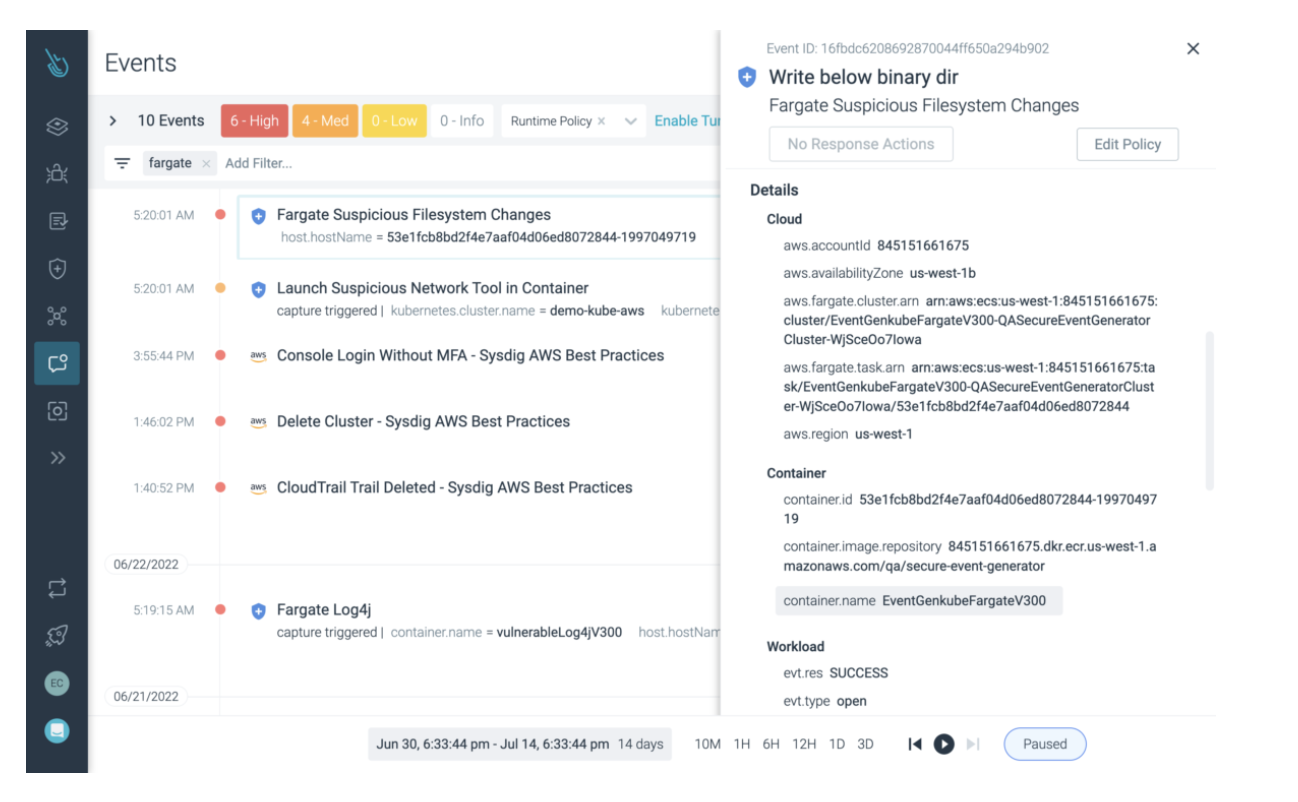
EDR tools fail to correlate insights across hosts, containers, and cloud resources, requiring security teams to manually stitch events.
Limited Response
EDR tools lack actionable attack path analysis and offer inadequate response capabilities.
Real-Time Detection and Configurability
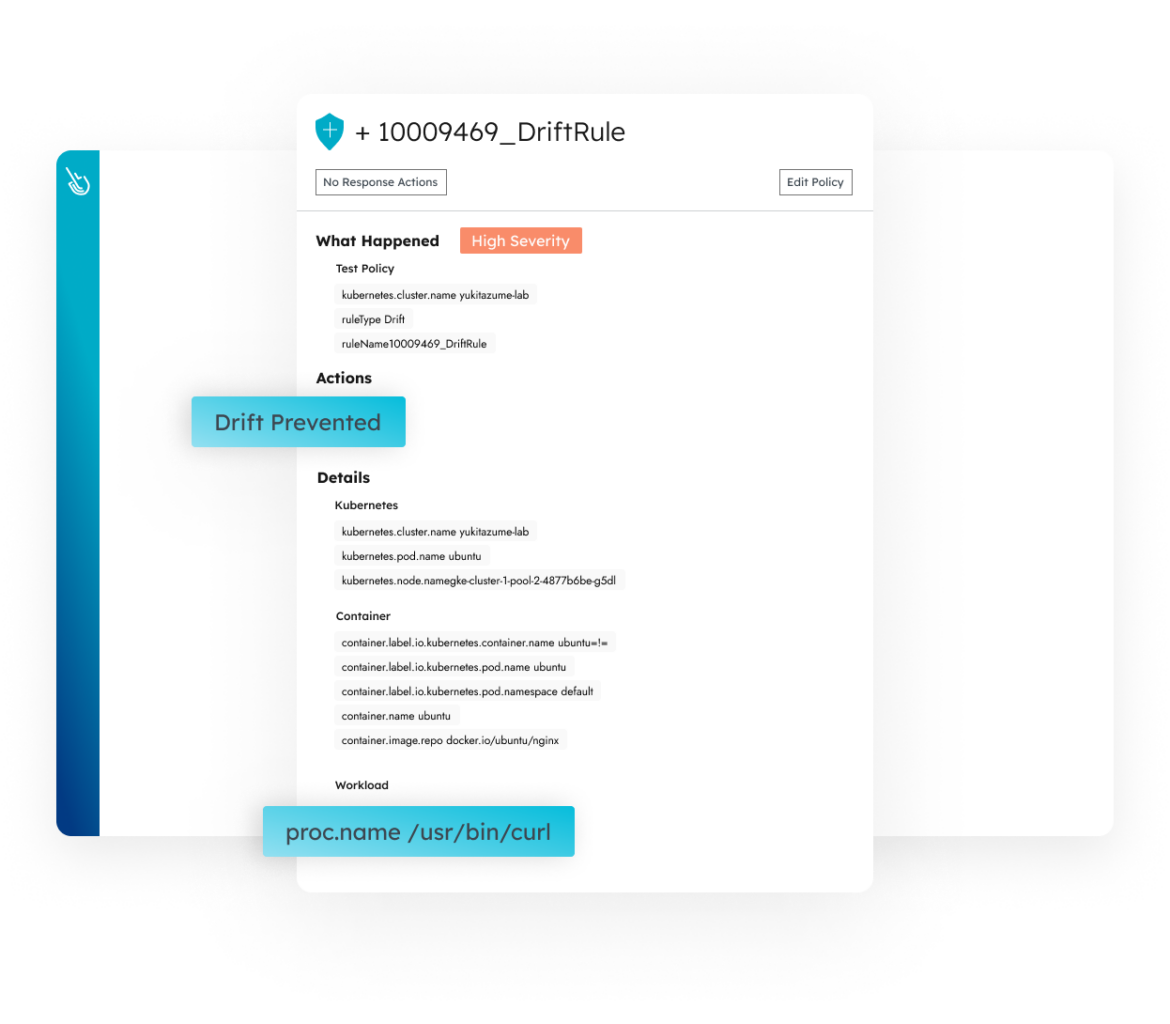
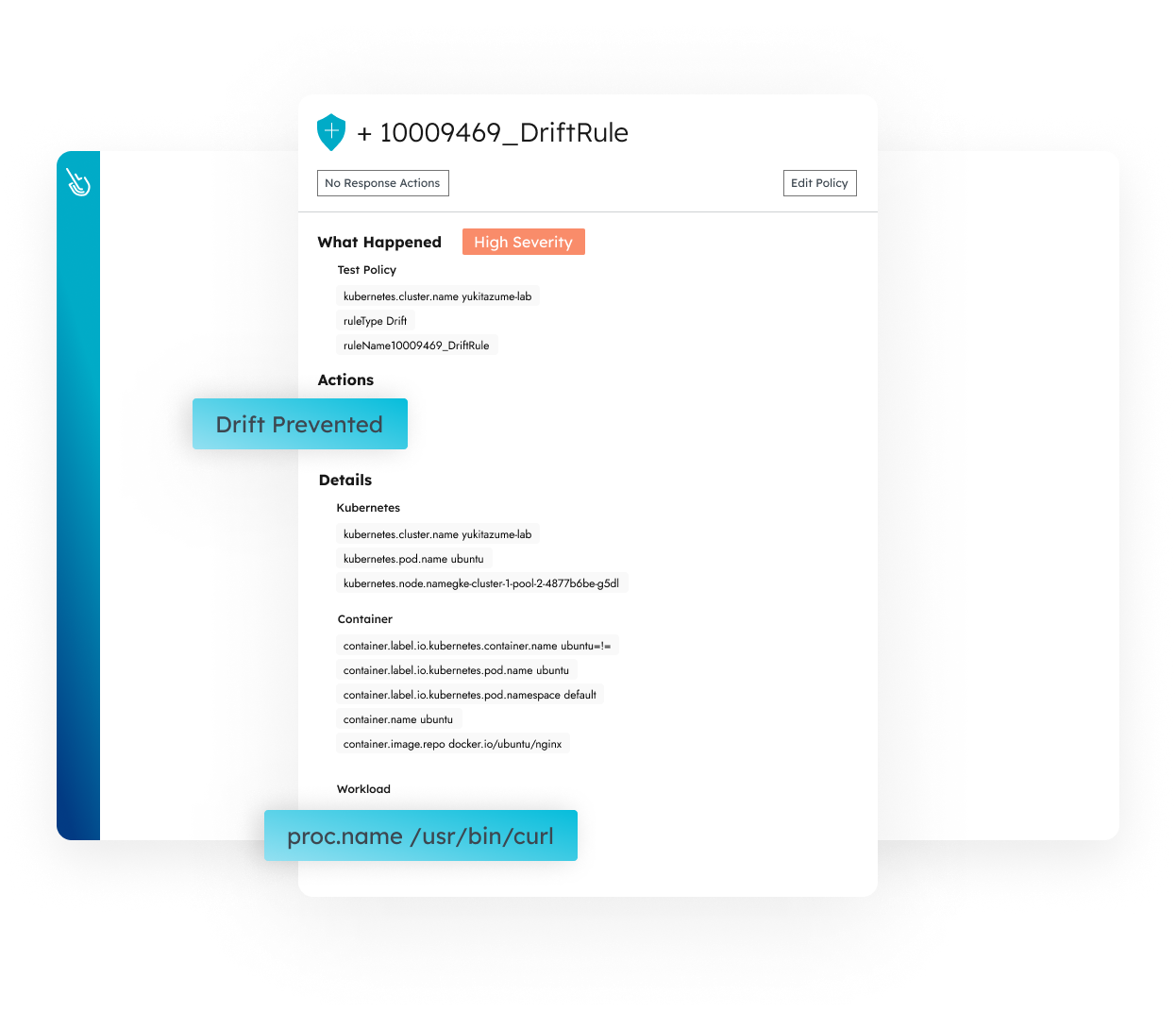
Ditch the black box approach with customizable and transparent detection across Linux and Windows servers. Leverage the configurability of Falco for more accurate, faster detection across multiple domains (servers, containers, cloud services, and more).
Contextualized Investigation
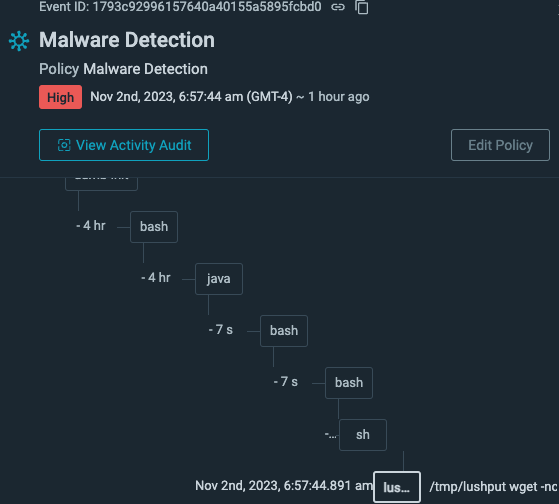
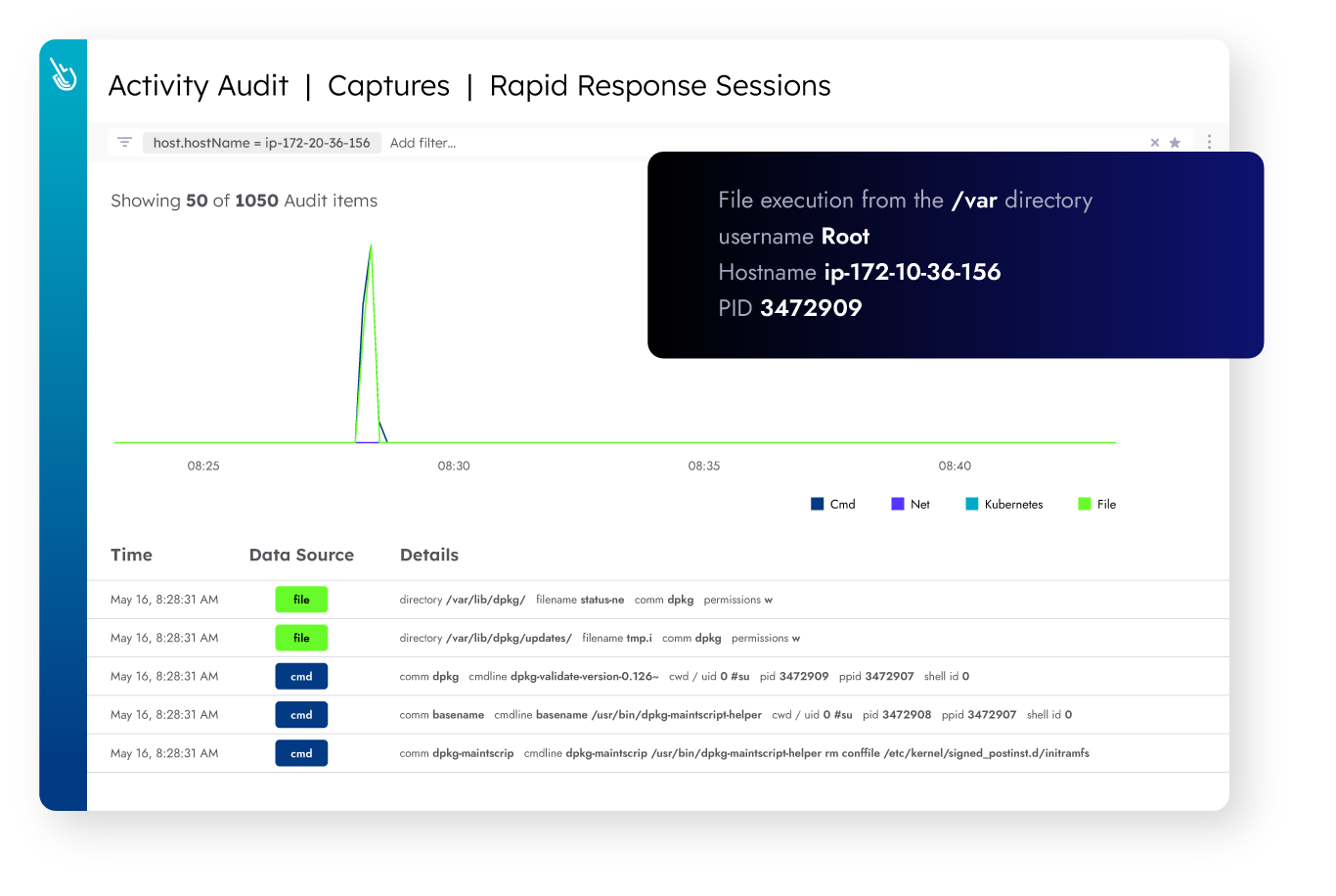
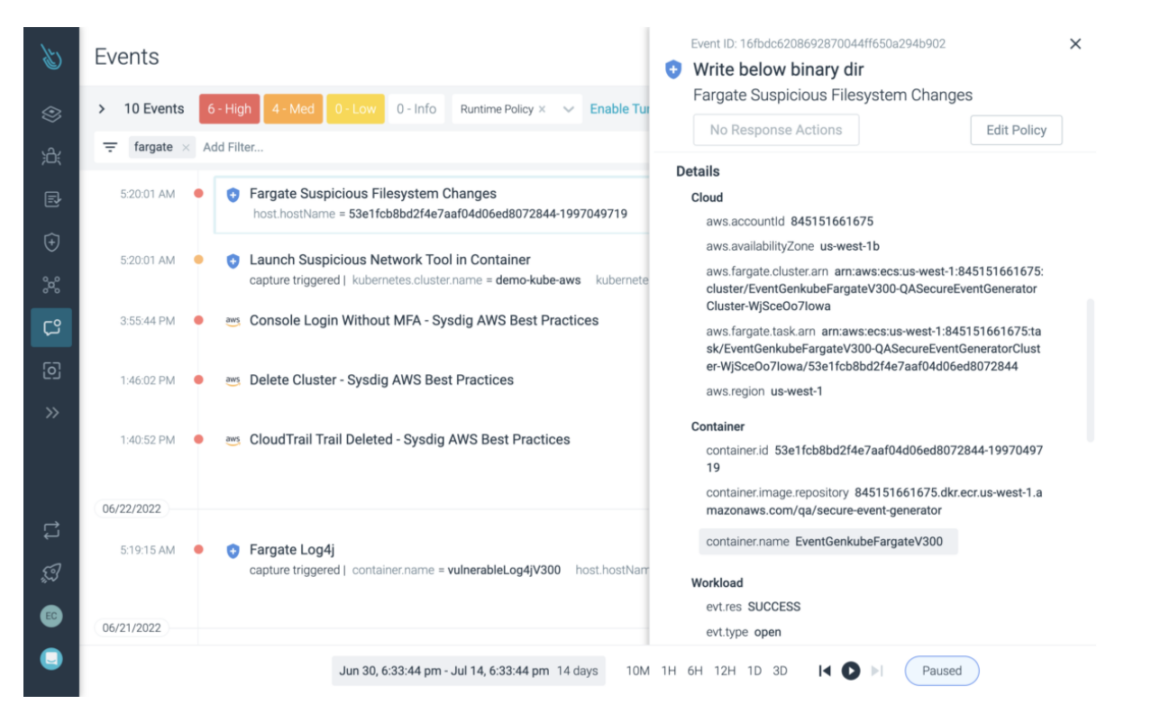
Automatically correlate insights across hosts, containers, and cloud activity for streamlined forensic triage and investigation. Capture every Linux system call and access rich context, including command executions, network connections, file access, and process creation, to quickly evaluate an event’s impact.
Flexible Response Options
Accelerate response with a variety of options that go beyond simply quarantining the entire host. Connect a remote shell within your environment to troubleshoot directly or stop/kill/pause individual containers. Proactively mitigate threats with actionable attack path analysis.
The Bridge for Security and
Dev Teams
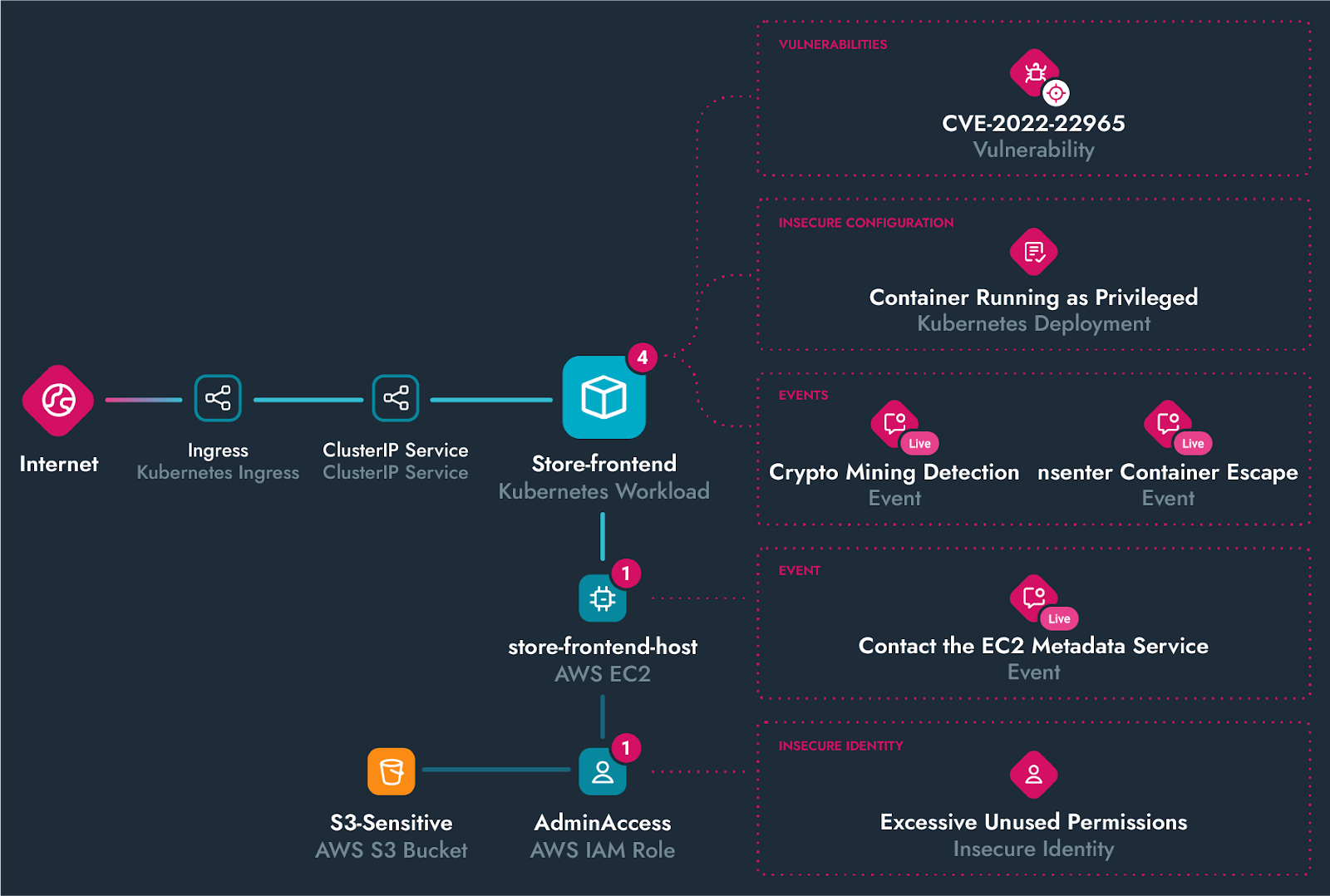
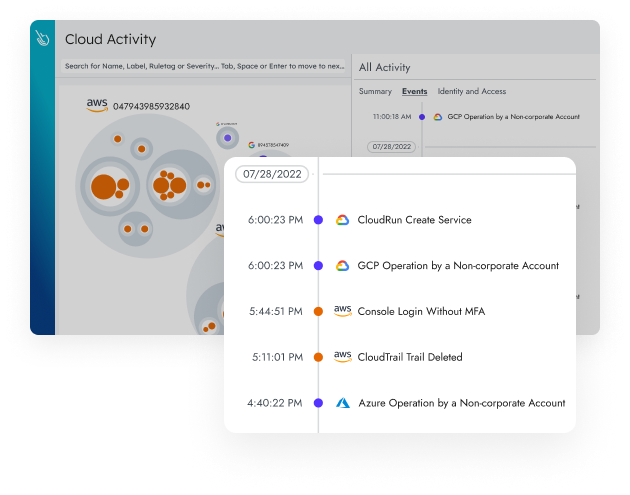
Sysdig’s end-to-end detection approach consolidates security across your entire cloud infrastructure, providing visibility across containers, hosts, cloud services, identities, and third-party apps.
Take the Next Step!
See how you can secure every second in the cloud.