Vulnerability Management
Full Life-Cycle
Agentless & Runtime
Vulnerability Management
Get the best of both worlds with agent and agentless scanning. Find and prioritize the most critical vulnerabilities that can be exploited at runtime. Simplify setup and scanning using an agentless approach to find vulnerabilities across your cloud environment.
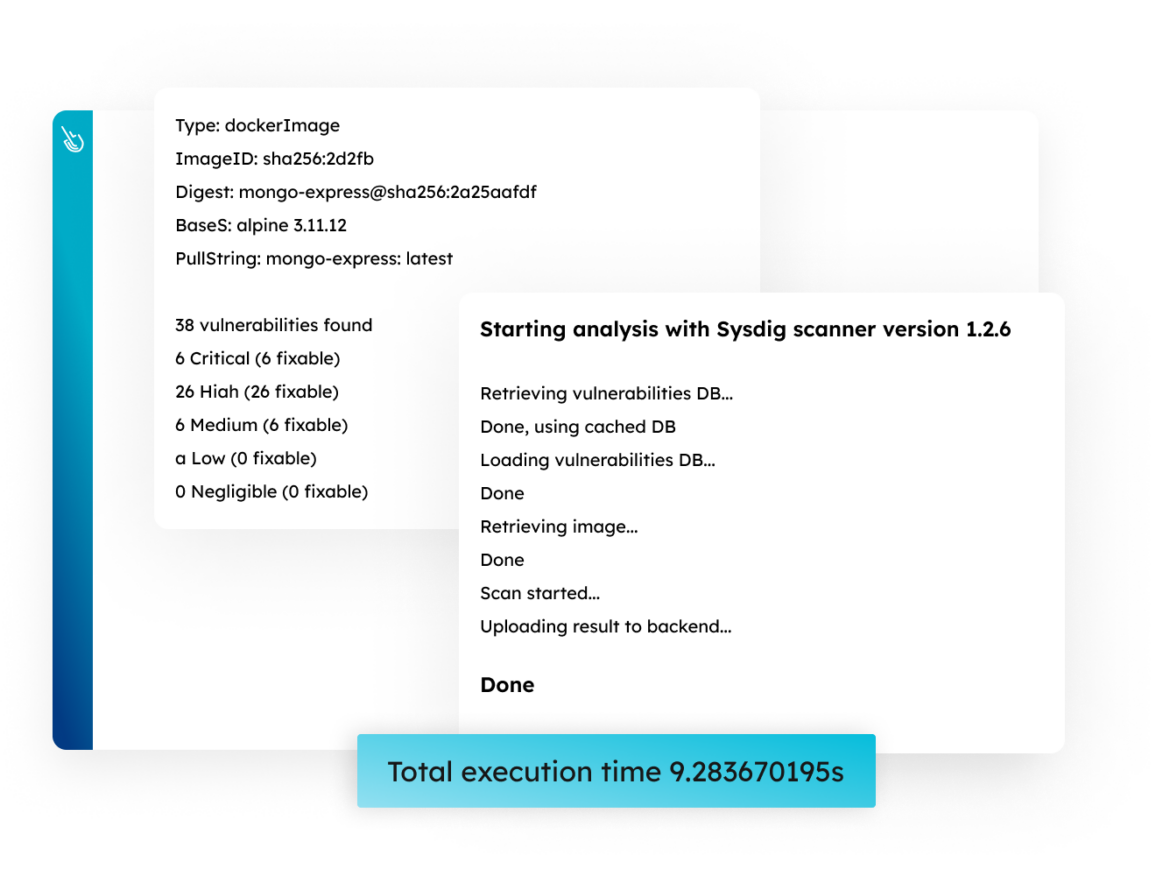
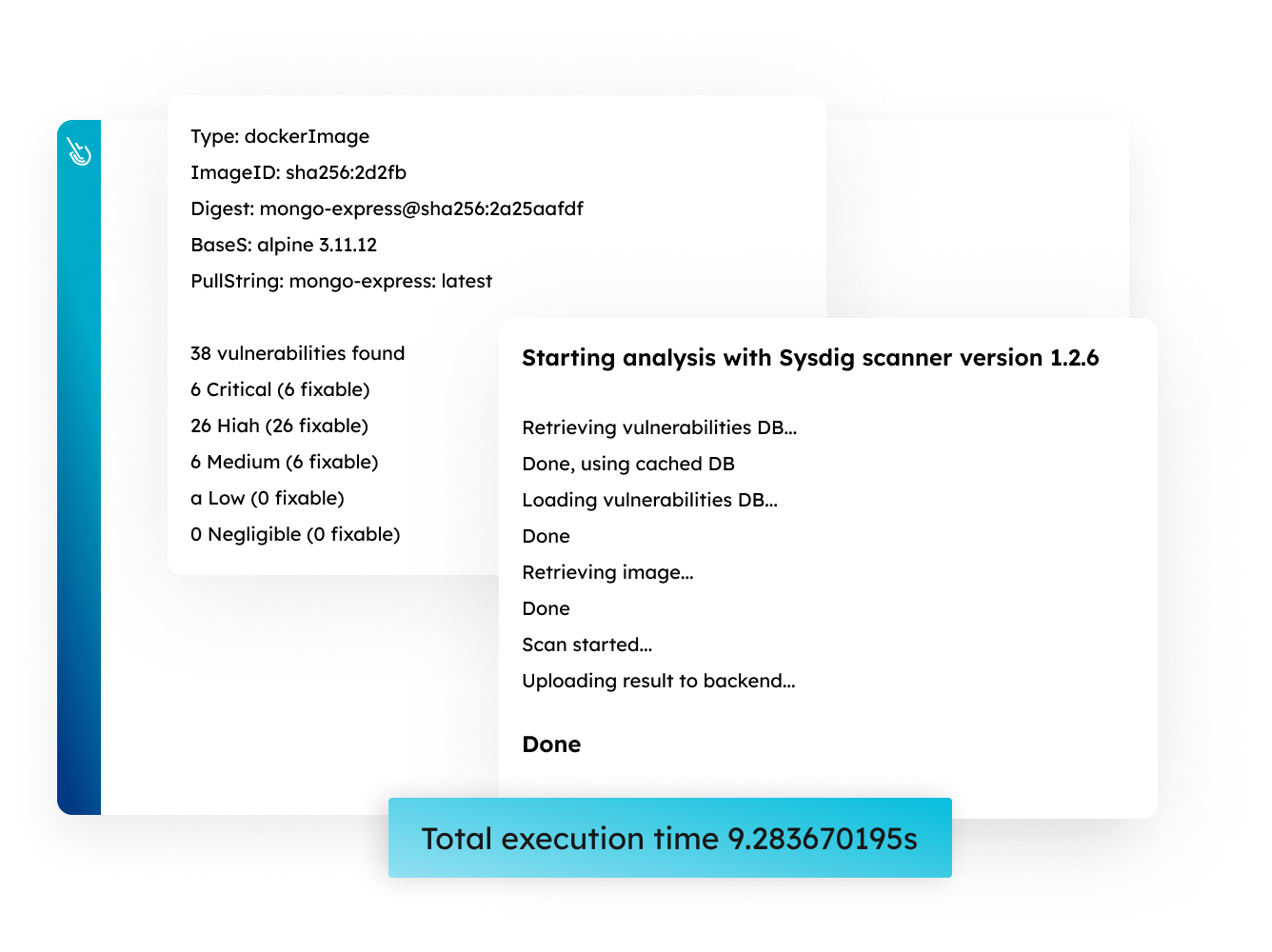
Scan, Prioritize, and Fix Critical Vulnerabilities Fast
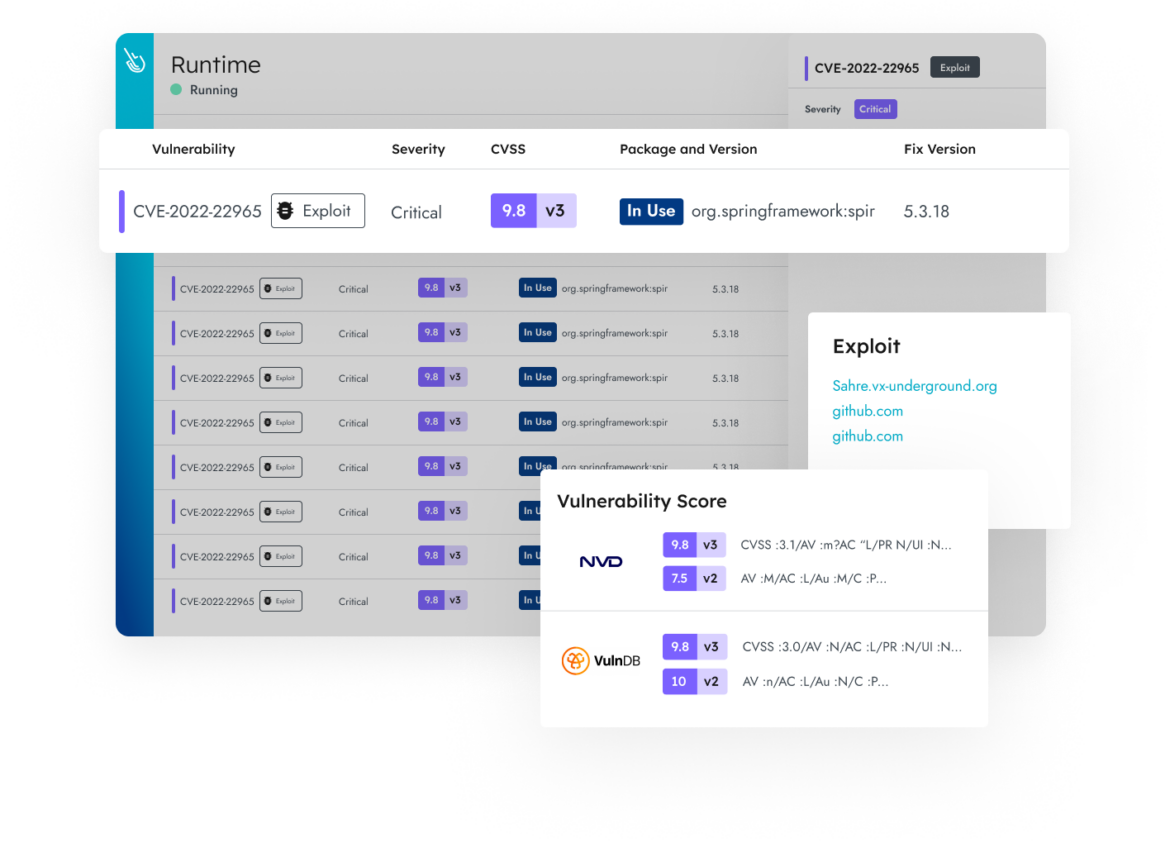
Get the best of both worlds. Simplify setup and maintenance with agentless host scanning for vulnerabilities. Save time and reduce noise by prioritizing vulnerabilities using runtime intelligence with an agent.
-
Reduce Noise and Boost Productivity
Filter 95% of the noise and make it easy for developers to fix the most critical packages.
-
Simplify Your Toolkit
Deploy and scan in seconds with a consolidated agent plus agentless solution.
-
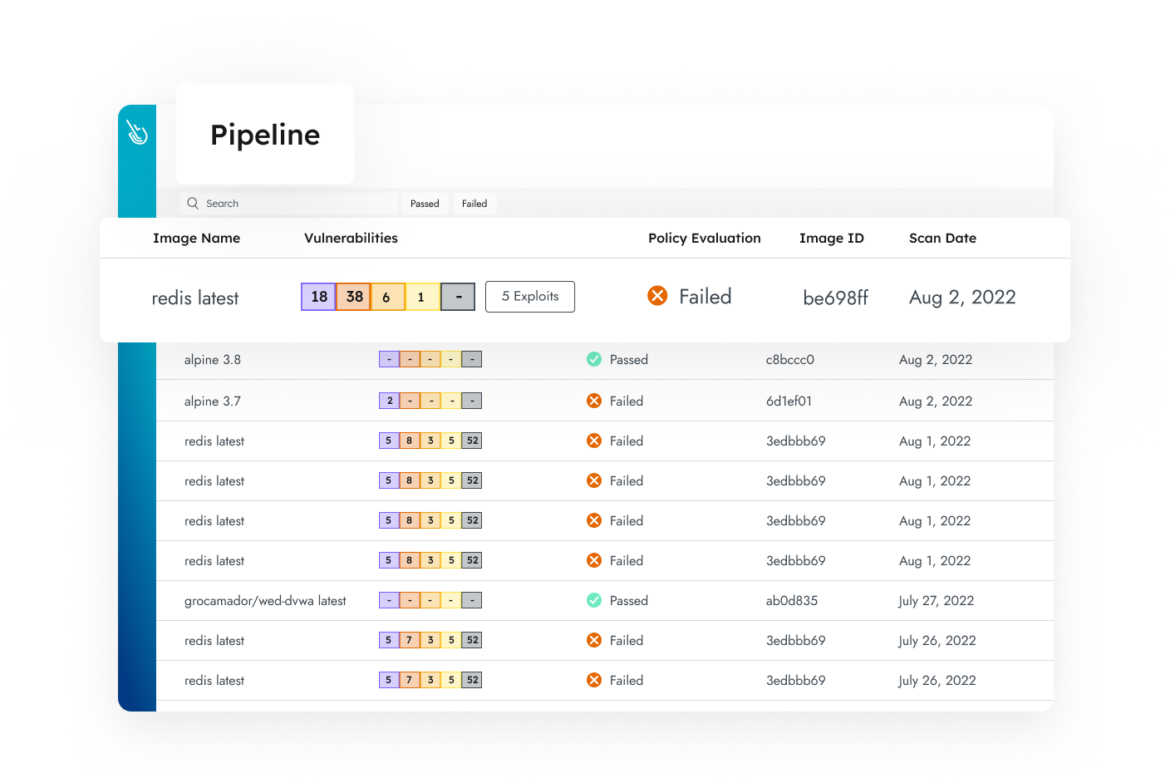
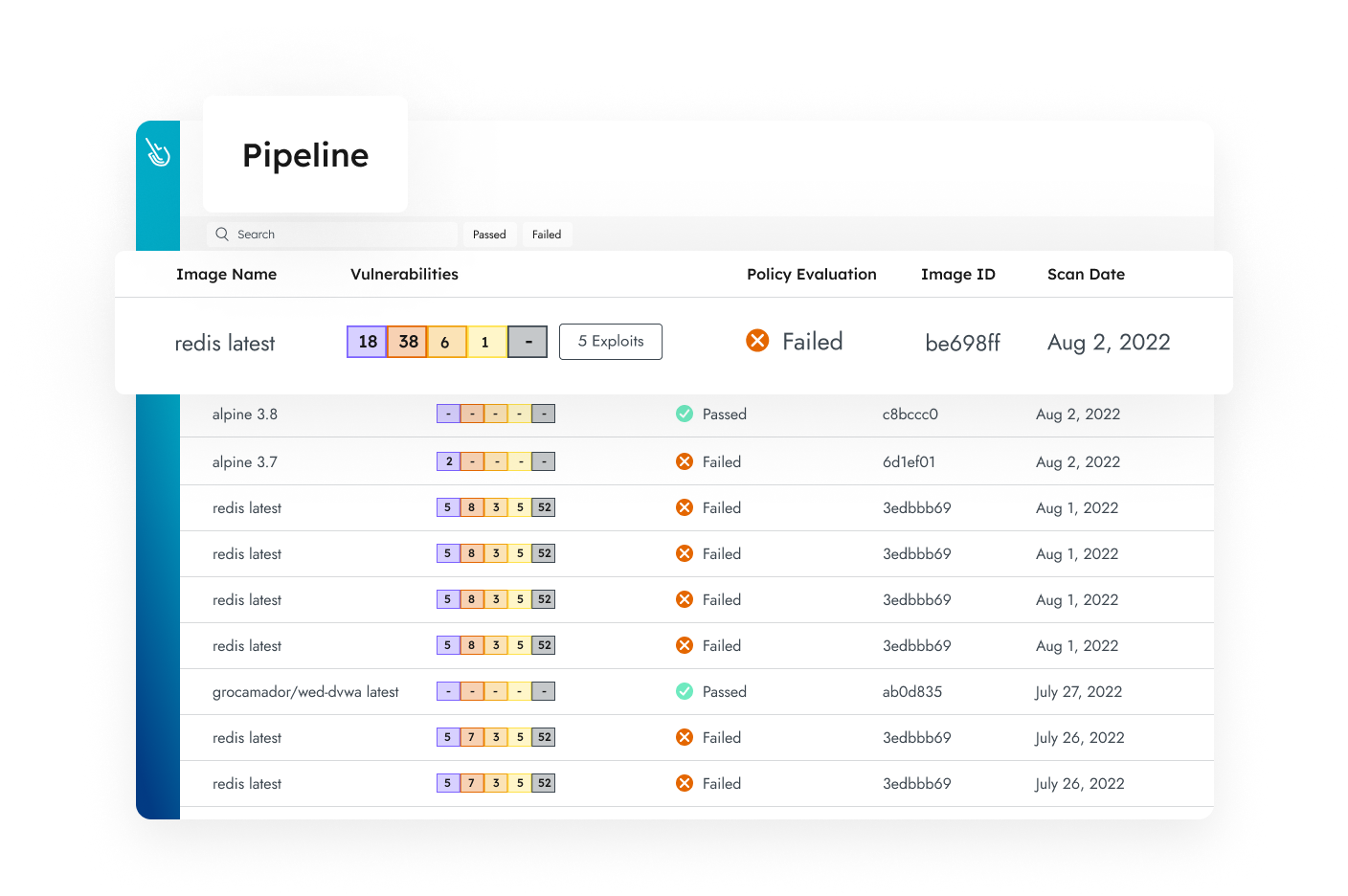
Secure the Entire Life Cycle
Secure your continuous integration/continuous delivery (CI/CD) pipeline from source to run.
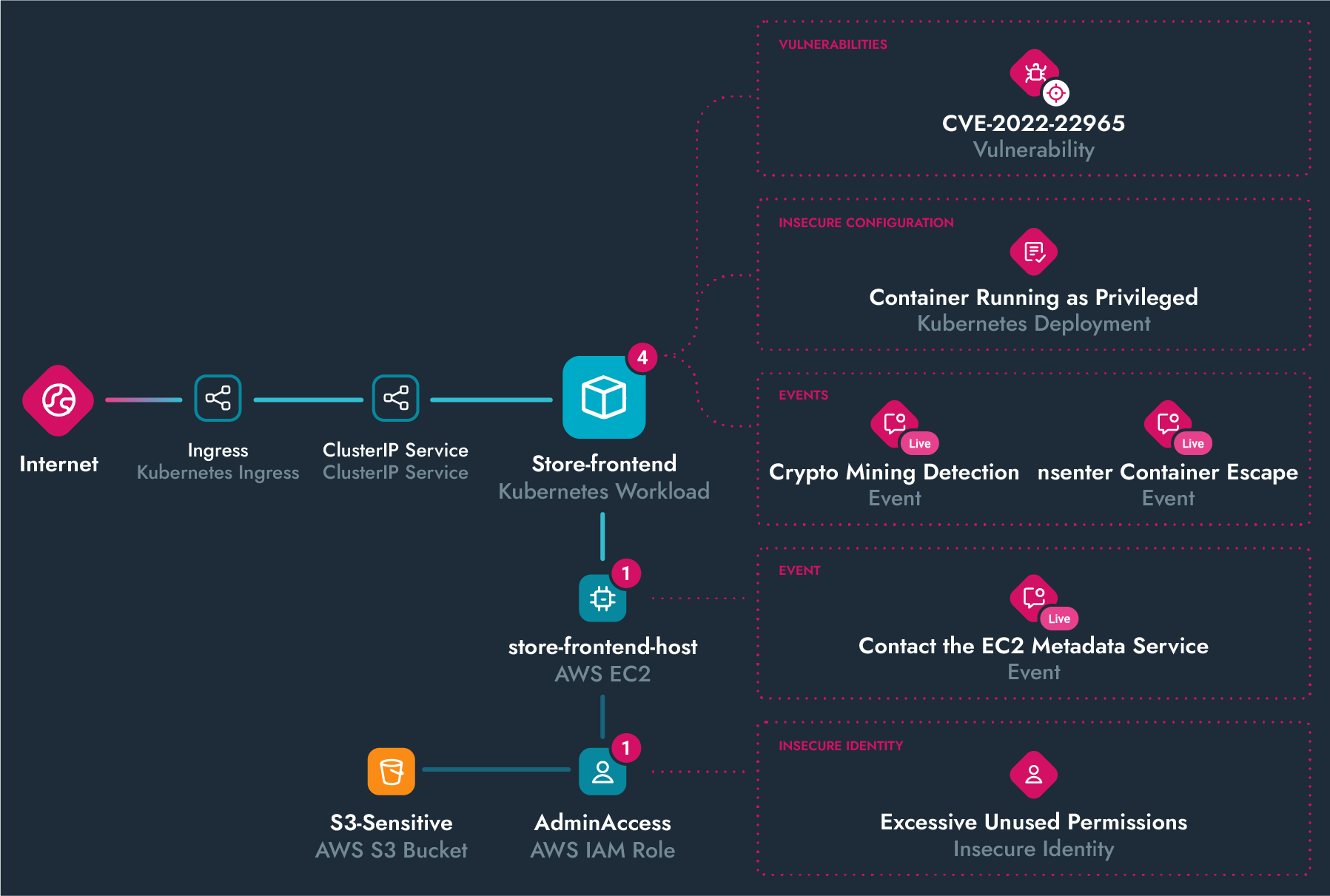
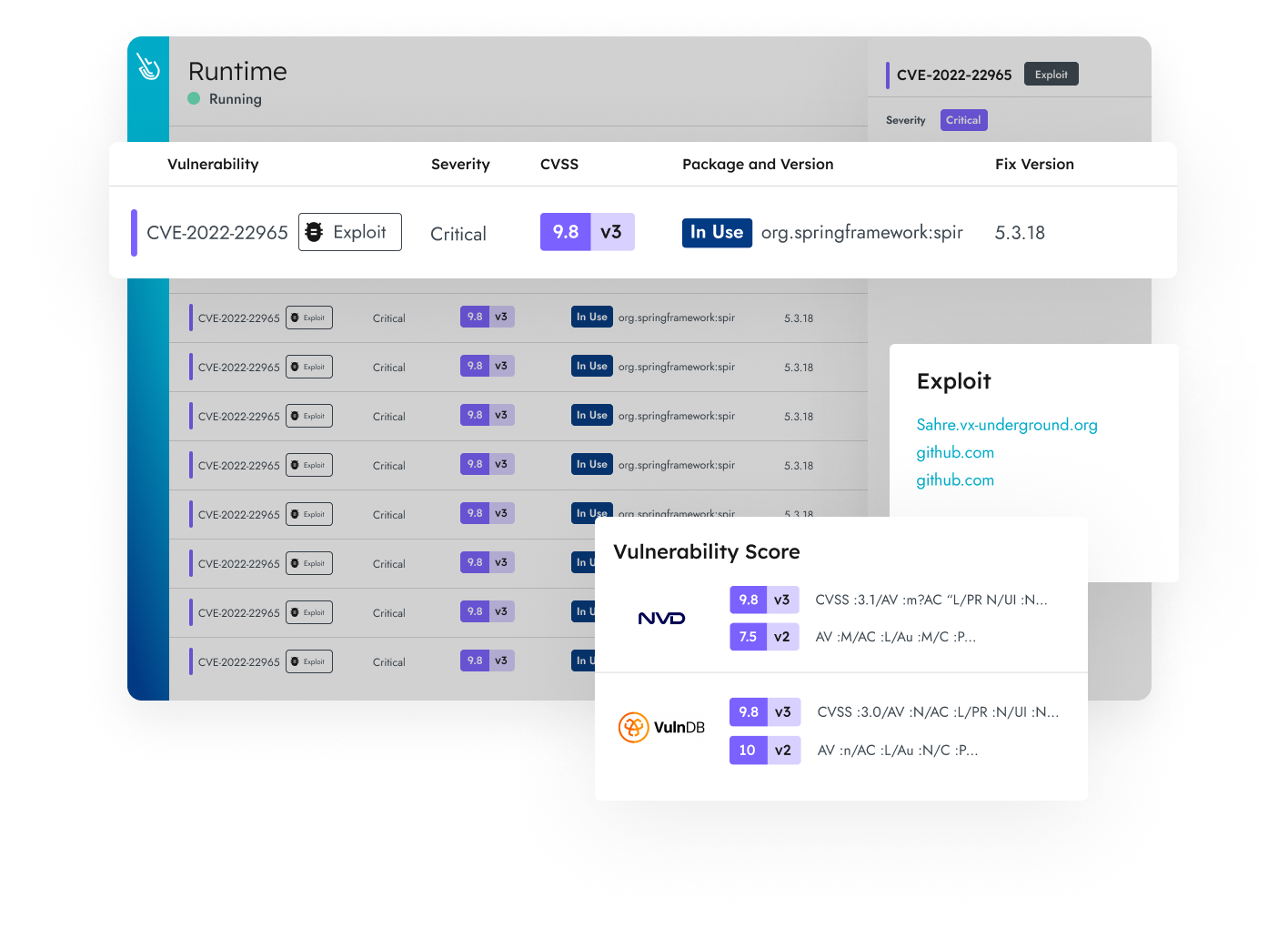
Uncover Hidden Risks on the Attack Path
The Sysdig cloud attack graph powered by runtime insights helps uncover the connections between in-use vulnerabilities, permissions, and real-time events to reveal the greatest risks.
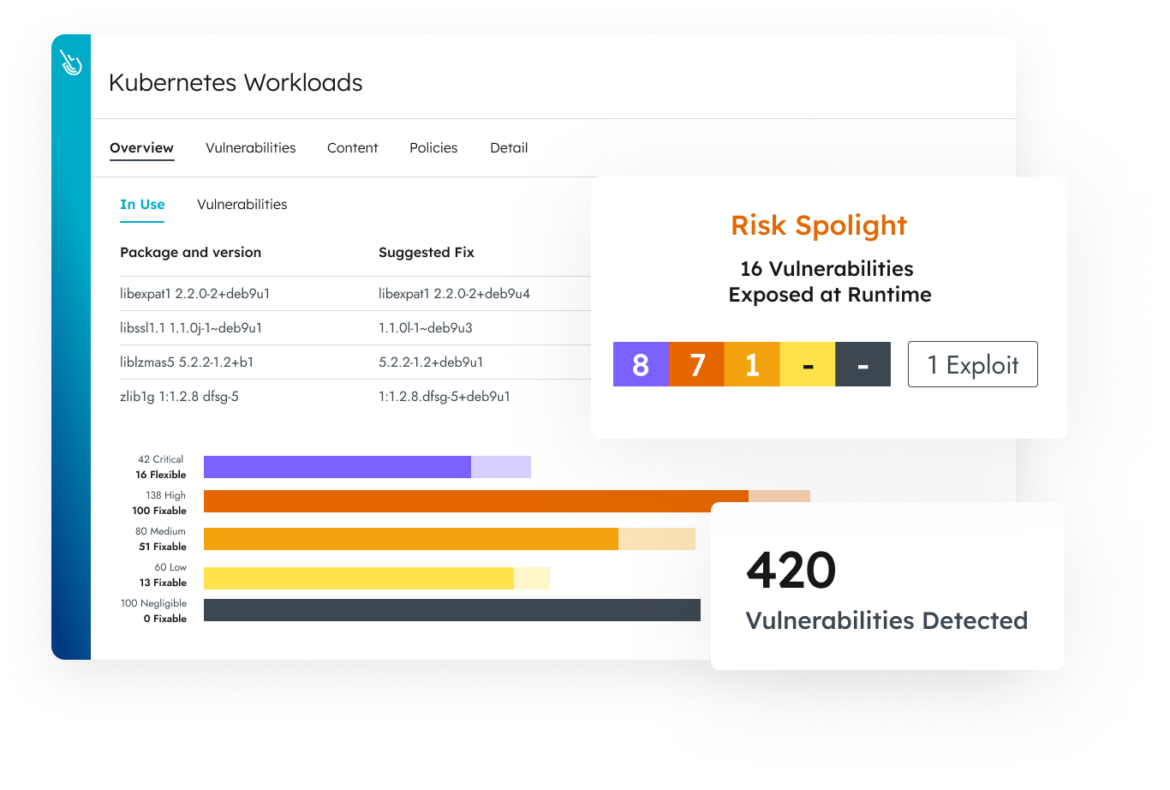
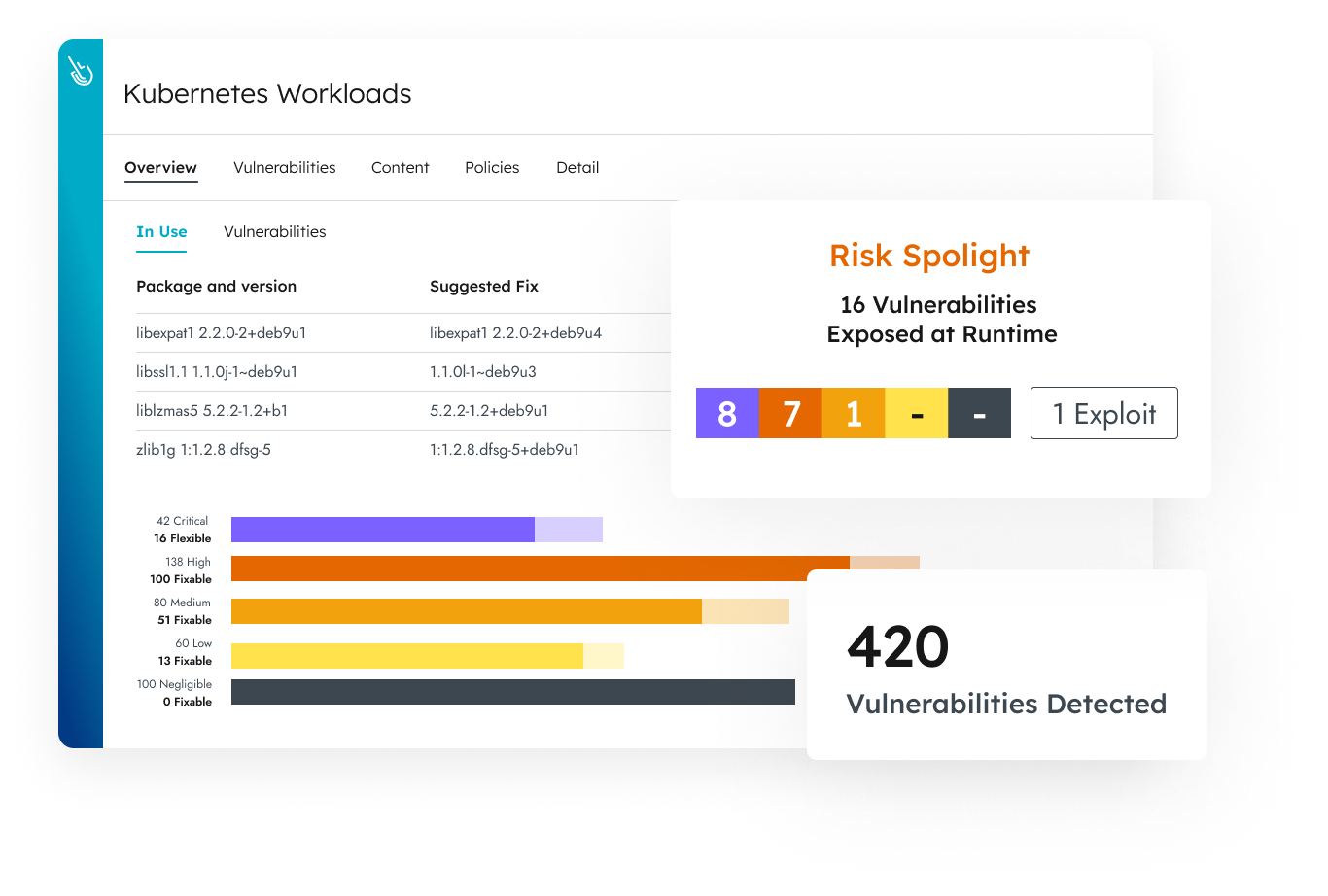
Shine Light on What’s Most Critical
Stop drowning in an ocean of vulnerability tasks. The Sysdig risk spotlight powered by runtime insights identifies in-use packages with the highest risks and helps you prioritize the most critical vulnerabilities to fix first.
Simplify Operations with Agentless Scanning
A frictionless setup allows you to start scanning for vulnerabilities in your cloud environment immediately. Gain better visibility into your cloud security posture, compliance violations, and highest risk items in seconds.
Arm SecOps and
Empower DevOps
Save Time and Get Real-Time Insights
Spend less time prioritizing vulnerabilities and get real-time insights on in-use packages and risks. Only Sysdig offers:
Featured Resources
Take the Next Step!
See how you can secure every second in the cloud.