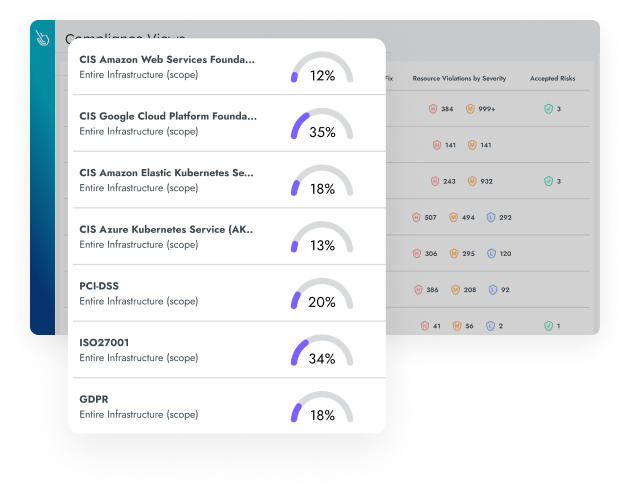
Cloud Security Posture Management (CSPM)
Reduce Cloud Risks
with Runtime Insights
Prioritize the most significant cloud risks. Combine context from runtime insights in real-time posture-drift detections and in-use permissions with static checks that flag misconfigurations and known vulnerabilities.
Identify, Prioritize, and Remediate Misconfigs at Cloud Speed
Sysdig goes beyond traditional CSPM solutions with runtime insights. Seamlessly triage risks, enhance mitigation effectiveness, and bolster your enterprise security strategy and posture with the power of real-time context.
-
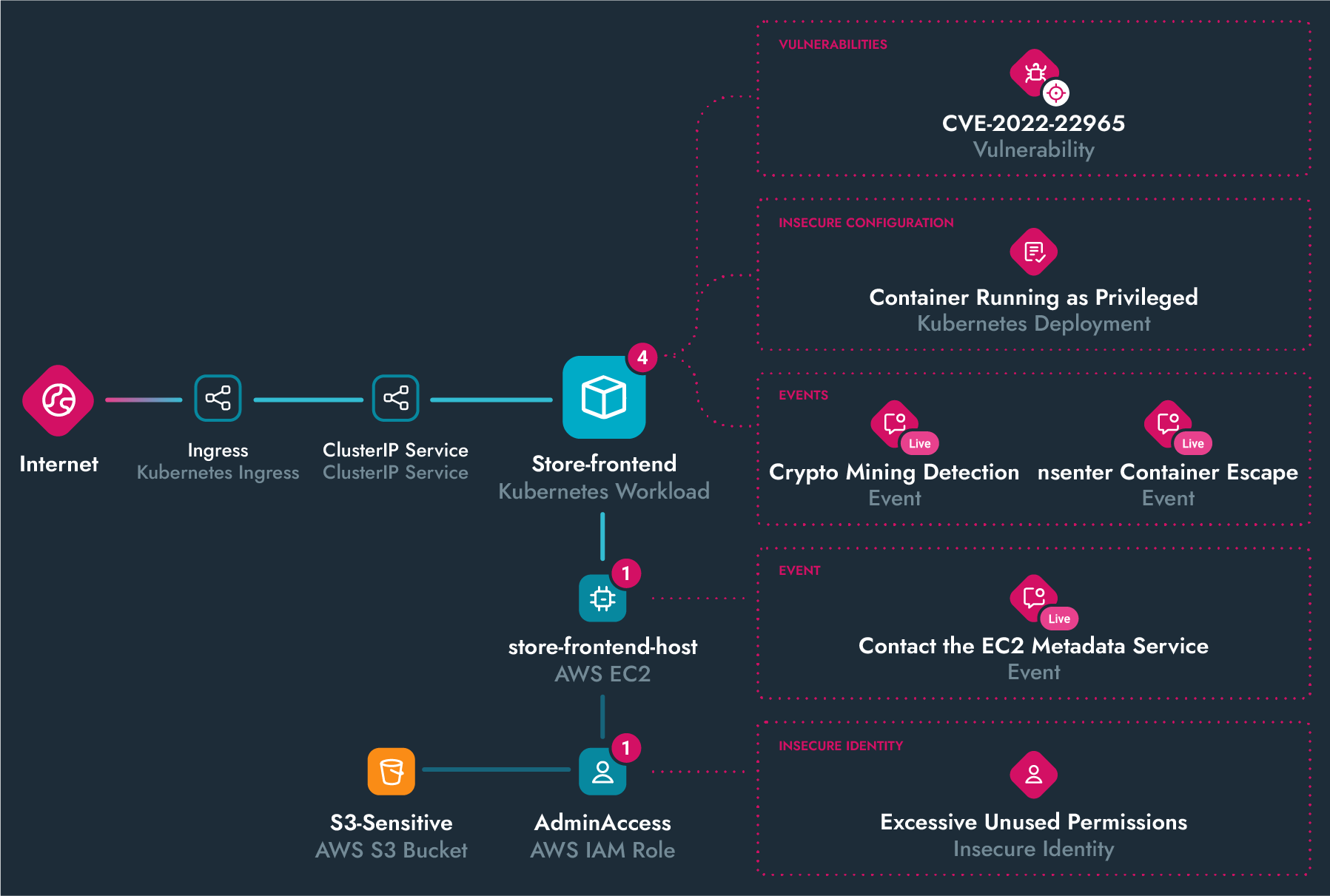
Cloud Attack Graph
Generate a prioritized list of all of your riskiest findings to harden your defense against cloud attacks.
-
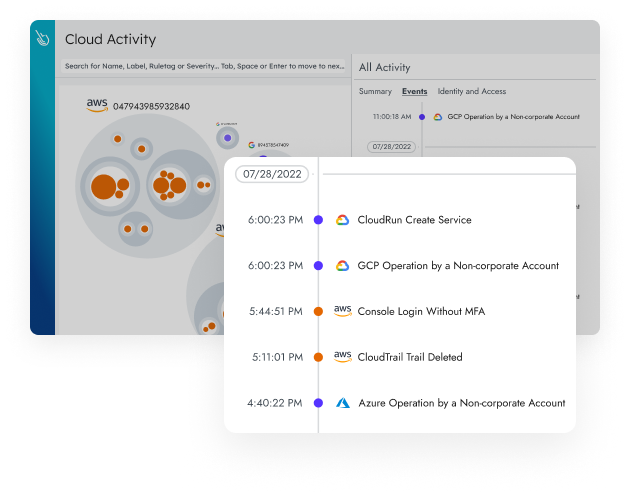
End-to-End Visibility
Gain a complete and dynamic perspective of your cloud resources with our cutting-edge AI-driven inventory, powered by runtime insights.
-
Depth and Breadth of Coverage
Combine agentless with agent-based deployments to cover greater use cases, providing context and visibility into the who/where/what.

Attack Path Analysis
Uncover hidden attack paths. Correlate assets with activity and visualize risks and exploitable links across resources. With runtime insights, real-time detections reveal active lateral movement, helping you stop attackers in their tracks.
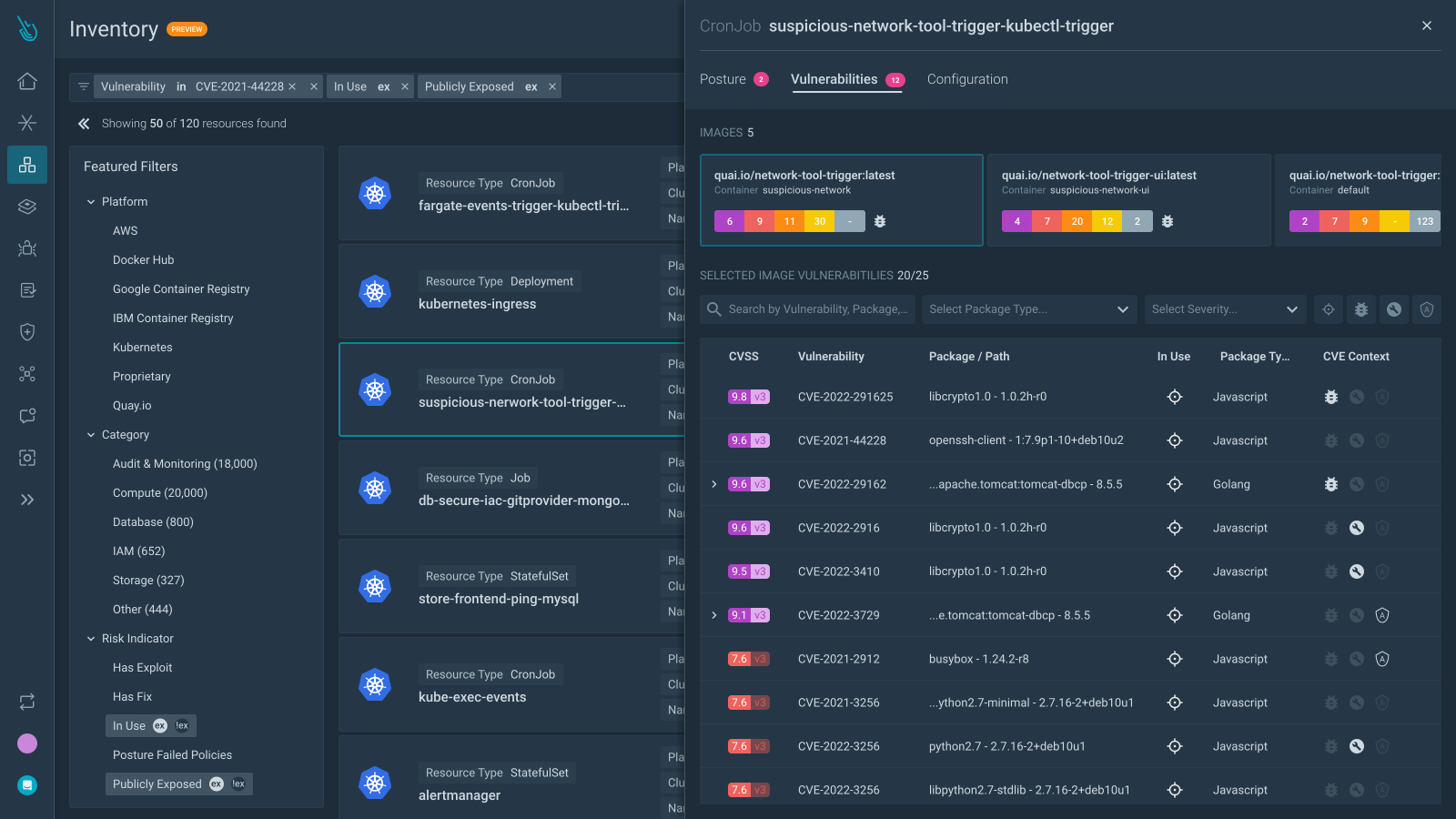
Dynamic Inventory Search
Search for compromised resources by combining various findings (For example: “Find all storage buckets that are publicly exposed to the internet with unblocked public access, and violate PCI standards”) to quickly check for exposure to high-severity misconfigurations, compliance violations, and vulnerabilities.
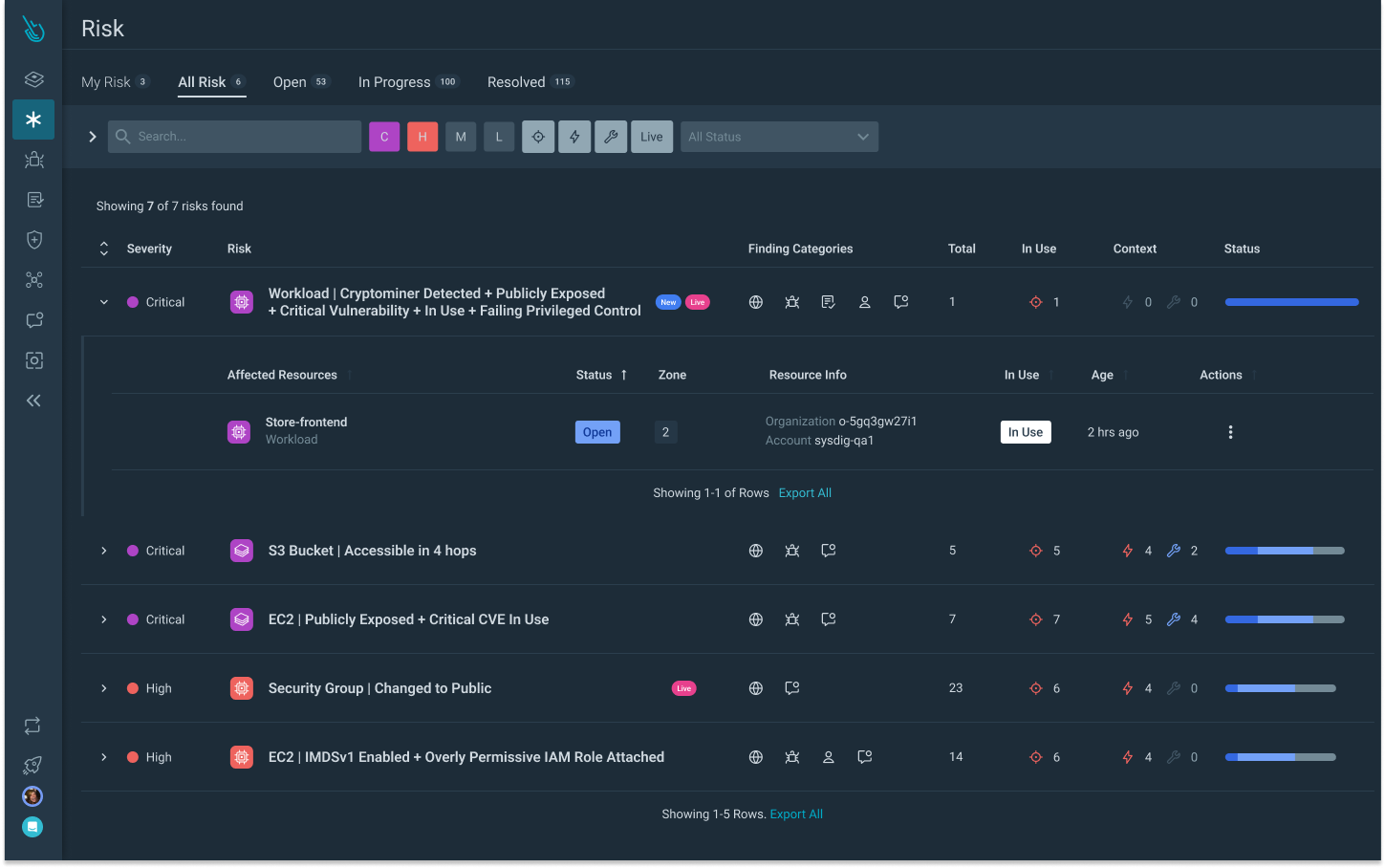
Risk Findings
Combine context from runtime insights such as in-use vulnerabilities and in-use permissions with static assessments, including misconfigurations and known security flaws, to help prioritize what matters most.
Better Security Posture from Runtime Insights
Static scanning of misconfigurations is not enough to prevent cloud attacks. Securing cloud-native environments at the speed at which the cloud operates requires accurate and up-to-date insights in real time.
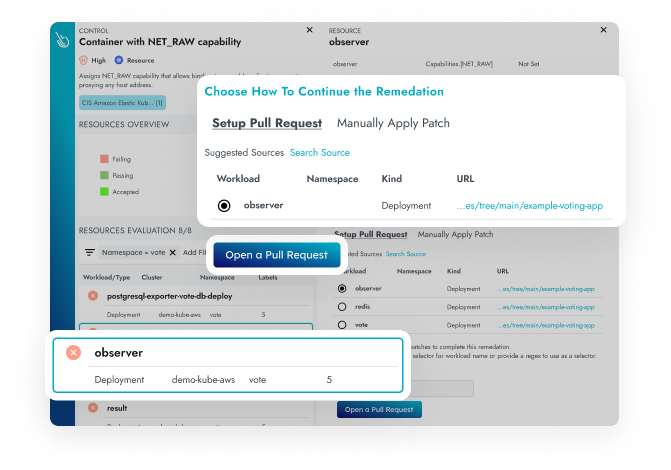
IaC Security for Cloud and Kubernetes
Prevent misconfigurations and enforce remediation of excessive permissions with recommended identity and access management policies. Automatically generate suggested configuration changes to infrastructure-as-code (IaC) artifacts that you can apply with a single click.
Runtime Insights that Enhance CSPM
Optimize your time prioritizing misconfigurations and get real-time insights on in-use permissions and risks. Only Sysdig offers:
Success Stories

“CSPM is Sysdig’s bread and butter, and that inspires confidence.”
Senior Infrastructure Security Engineer at BigCommerce
“Sysdig Secure comes into play on a big scale when convincing the auditors. GDPR is also a concern in the industry. Sysdig helps us see and inspect operations that could interfere with GDPR in the end.”
Head of Technical Operations at Gini
“With Sysdig, it’s simply night and day as to how quickly and accurately we can manage compliance. Even more importantly, we can save time and money, as well as avoid costs for being out of compliance.”
Security Architect, Beekeeper
Take the Next Step!
See how you can secure every second in the cloud.