Content
What Is Azure Kubernetes Service?
Azure Kubernetes Service (AKS) is a fully managed container orchestration service for Kubernetes clusters that is based on Microsoft Azure. Kubernetes has become a leading container management platform, which begs the question: who will manage your Kubernetes infrastructure?
AKS simplifies the deployment of managed Kubernetes clusters by offloading the operational overhead to Azure; thus, the user does not need to worry about the underlying computer infrastructure overheads. As a hosted Kubernetes service, Azure handles critical tasks like health monitoring and maintenance. You only manage and maintain the agent nodes, because the Kubernetes masters are controlled by Microsoft Azure. AKS is completely free, and you only have to pay for the agent nodes in your clusters, not the masters.
AKS offers an open source, fully managed Kubernetes container service, so even users without container orchestration expertise can easily deploy and manage containerized applications. The responsibilities of provisioning, resource scaling, and upgrading based on demand are offloaded to Azure, thereby allowing the DevOps team to focus on building and delivering applications faster. One of the main advantages of using AKS is its ability to unify the development and operations processes in a single platform, along with its serverless continuous integration and continuous deployment (CI/CD). This improves the overall cloud service experience for enterprises.
We cannot talk about cloud services without discussing security in the responsibility model. Having a managed service running in an AKS environment raises concerns about who is responsible for what – does responsibility lie with the user or the service provider? Whether it is security in the cloud or the security of the cloud, you need to consider various best practices when building, running, and deploying Kubernetes container applications with AKS. This guide will shed light on the features offered by AKS, the demands of AKS security, and the best practices for achieving AKS security.
AKS Features
As mentioned above, AKS provides a fully managed service by ensuring that Microsoft Azure takes care of the complex parts of running Kubernetes as well as the overall infrastructure. Some of the main features it provides include:
Security, Access, and Monitoring
AKS improves security and management by integrating Azure Active Directory (Azure AD) and using Kubernetes role-based access controls (RBAC) to monitor resource permissions. It also uses a centralized visibility dashboard to monitor the health status of the Kubernetes clusters and resources.
Identity and Security Management
AKS uses Kubernetes role-based access controls (RBAC) to help configure access to the Kubernetes clusters for monitored identity management and membership-based access into Kubernetes namespaces and resources. RBAC uses integrated sign-on features to ensure that Azure AD users and groups have the right permissions before being authenticated to access Kubernetes resources.
Integrated Logging and Monitoring
One key and common feature across cloud computing is the priority given to observability, monitoring, and logging. AKS uses Azure Monitor for Container Health to observe the health status of Kubernetes nodes, clusters, and controllers, as well as to collect log information on the performance metrics deployed within the container applications.
Clusters and Nodes
AKS runs Kubernetes clusters on Azure Virtual Machines (VMs), which enables you to mix different node pools, operating systems, and Windows Server containers. In addition, AKS nodes allow pods and nodes to be connected, cluster components to be upgraded, and GPUs to be used.
Azure Kubernetes Service Security
One of the concerns associated with cloud services is security – especially because it requires you to give some of the app management power to the cloud service provider. When building containerized applications to run on AKS, you need to ensure that containers are secure, which protects the end-to-end pipeline. As previously stated, Microsoft Azure is responsible for ensuring the security of the cloud, including components such as Microsoft Defender for Cloud, Active Directory, Azure Key Vault, network security groups, Azure Policy, and orchestrated cluster upgrades. Kubernetes, on the other hand, is responsible for security in the cloud, including components like pod security standards and secrets. The overall security of the supply chain protects both the registry and the built environment.
AKS is well supported by Microsoft Azure, so customers and users have the foundational tools and techniques to achieve regulatory and security compliance. It combines different security components (such as build security, registry security, cluster security, network security, and Kubernetes secrets, among others) to provide the best security practices. Some of the goals of AKS security include:
- Providing complete authorization and authentication
- Leveraging AKS Built-in Azure Policy to secure applications
- Making sure the AKS clusters run the latest OS security updates and Kubernetes releases
- Providing secure pod traffic and secure access to sensitive credentials
- Providing complete visibility into your application using the Microsoft Defender for Containers
With the understanding of the risks associated with unsecured cloud services, and in this case AKS, Microsoft Azure provides some of the best tools and practices that AKS users can leverage the existing components to ensure AKS security. The rest of this article breaks down the best practices for AKS security, and how users can apply them to their AKS environment, thus ensuring a more secure container environment.
AKS Security Best Practices
Cluster and Node Security: Secure Access to the API Server and Cluster Nodes
Microsoft provides, manages, and maintains the Kubernetes master components such as Clusters and Nodes, as part of the AKS managed service. AKS clusters each have their own single-tenant Kubernetes master that provides features such as the API Server, and Kubernetes Scheduler.
In AKS, the Kubernetes API server has a public IP and domain name. To ensure the security of the clusters and nodes, you need to restrict the API access by limiting its access to specific IP ranges or by creating private clusters within the Azure Virtual Network.
To control access to the API server, integrate the Azure role-based access control (RBAC), Kubernetes RBAC, and the Azure Active Directory (Azure AD). These controls ensure that scoped resources such as namespaces are granted the minimum access permissions, hence restricting access to the API server and providing a clear audit of the actions performed. The recommended best practice to ensure granular permissions is to use groups to restrict access to certain files and folders instead of using individual identities. For instance, use a group Azure AD membership to bind Kubernetes users and individual roles, upon which permissions are granted per user group.
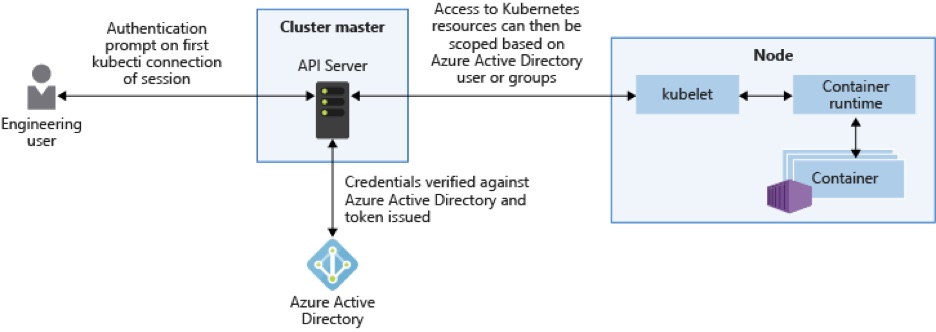
Source: Microsoft Docs
Secure Container Access to Resources
Just as you would limit user access, containers also need to be restricted to only access the necessary resources and processes. This includes limiting the access to the kind of actions containers can perform by granting them the least number of permissions, and ensuring the root access privilege is not used. When configuring applications, you can limit the risk of attack by ensuring that containers do not need escalated privileges or root access.
AKS contains built-in Kubernetes pod security contexts that define the capabilities of a pod. For example, you can configure pod security within the pod manifest by setting – allowPrivilegeEscalation: false. There is a whole section for ensuring pod security and its access to resources here.
Regular Update to the latest Kubernetes version
Kubernetes releases new features and new bug or security fixes quite regularly. As an AKS user, you need to ensure that the version of the Kubernetes within your cluster contains the current features and bug fixes. Once the Kubernetes releases are in beta status and are stable, they are recommended for production use such that the users can easily upgrade to new features in the release version.
AKS supports several versions of Kubernetes, whereby once a new patch version is introduced, the oldest patch version is retired; and this happens periodically. The Kubernetes release cycles are quite regular and predictable so users can regularly upgrade without encountering deployment breakages.
Before upgrading Kubernetes within your cluster, you first need to check the available versions for the cluster by running the example command below, within the Azure CLI.
az aks get-upgrades --resource-group myResourceGroup --name myAKSClusterCode language: JavaScript (javascript)Once you have identified the available Kubernetes versions, run the command below to upgrade your AKS cluster.
az aks upgradesThe best-recommended practice when upgrading Kubernetes is to first test the new version in patches, within the development test environment. This validates the compatibility of your existing workload to the Kubernetes version. It is also important to upgrade one cluster resource at a time especially when working with several clusters. This way, you can easily monitor the progressive impact or changes for each resource.
Run this command within your Azure CLI to upgrade one cluster at a time:
az aks upgrade --resource-group myResourceGroup --name myAKSCluster --Kubernetes-version KUBERNETES_VERSION Network Security
To ensure that AKS is secure and can connect with the on-premises networks, you can deploy the AKS cluster into the already existing Azure virtual network subnets. The virtual networks connect back to your on-premises networking using Azure Site-to-Site VPN or Express Route. You will also need to limit services access to the internal network connection by defining the Kubernetes ingress controllers with private and internal IP addresses. The image below illustrates how the different network security groups (NSGs), AKS clusters, and Web Application Firewall (WAF), effortlessly work together to provide security features and policies for an overall AKS network security posture.
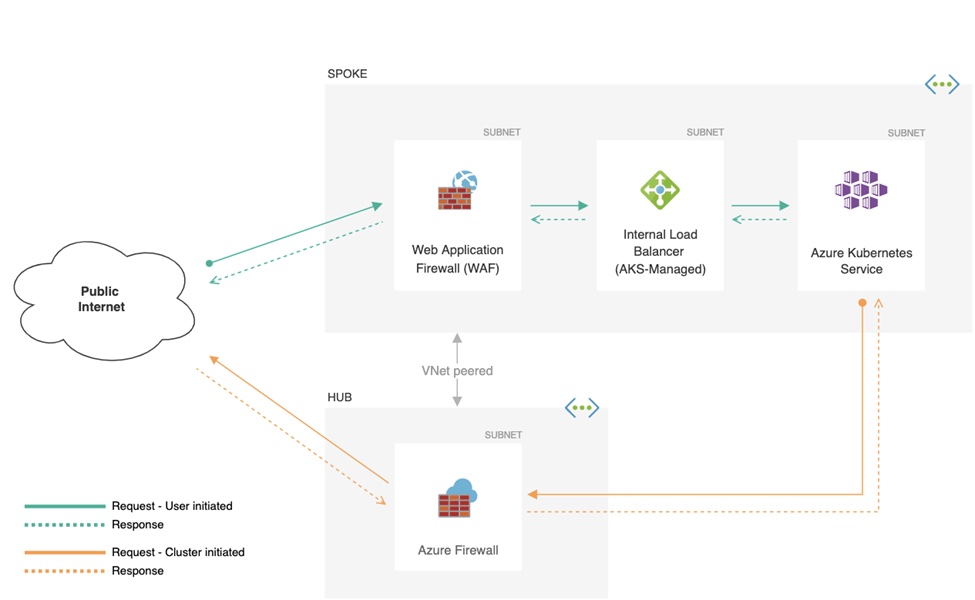
Source: Microsoft Docs
Azure AKS Monitoring and Observability
Azure Kubernetes Service (AKS) uses Azure Monitor to monitor its health and performance. Azure Monitor uses a collection of telemetry metrics to monitor, analyze and visualize trends related to alerting and critical performance issues. AKS generates platform metrics and resource logs that are used to monitor its basic health and performance. It also contains and enables the Container insights feature used within the managed Kubernetes clusters hosted on AKS to collectively monitor them. Container Insights provides interactive views and workbooks that analyze the collected data for a variety of monitoring scenarios.
As shown below, the container insights visualize a summary of the pod and cluster utilization, health, and performance.
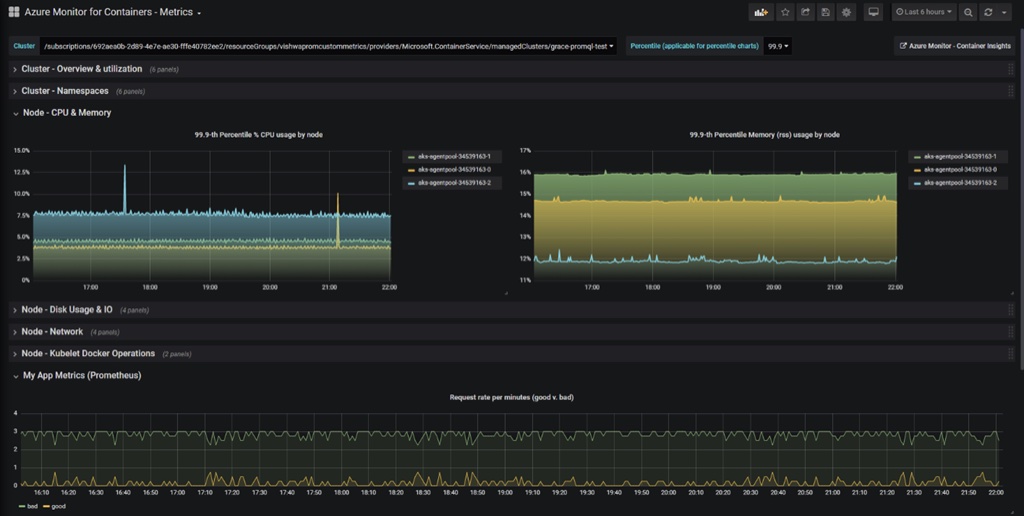
Source:Microsoft Docs
Using Sysdig Secure DevOps Platform to Secure Azure AKS
With the increased use of cloud computing in digitalization, it’s important to note that observability and monitoring are two of the most important best practices to follow while using cloud services. Because Azure AKS is such a vital tool for running Kubernetes container applications, it’s important to keep an eye on the AKS clusters. Sysdig provides two products to assist in audit logging: the Sysdig Secure Devops platform and the Sysdig Monitor.
The Sysdig Secure DevOps Platform provides comprehensive visibility and security built on an open-source foundation, allowing you to confidently execute apps on Azure Kubernetes Service (AKS). Scale easily using SaaS and DevOps connections that let you stay up with Kubernetes and the cloud’s dynamic nature.
Sysdig Monitor is also a Sysdig product that helps in ensuring cluster availability and capacity in Kubernetes. It is a unified platform used in container-and microservices-friendly architecture to deliver security, monitor, alert, and troubleshoot dynamic production environments.

