Content
VMware became famous as the company that brought virtual machines into data centers everywhere.
But today, VMware has also become a major player in the world of containers and Kubernetes. Indeed, one of VMware’s major virtualization platforms, vSphere, is now available with Kubernetes “baked in.” On top of this, VMware has invested in other tooling, like Tanzu Mission Control, to help manage Kubernetes in public, private, and hybrid cloud environments.
Keep reading for everything you need to know about using Kubernetes with VMware.
Can Kubernetes Run on VMware?
Over the past several years, VMware has invested substantially in tooling that makes it not just possible, but easy, to run Kubernetes clusters on top of VMware virtual machines.
This effort started with VMware’s acquisition of Pivotal (a Kubernetes vendor) and announcement of Project Pacific in 2019. It intensified with the release of vSphere 7 in 2020, which comes with Kubernetes support deeply integrated into the VM platform.
What this means is that if you use vSphere 7, you don’t need to do anything special to create and run Kubernetes clusters on the VMs that you manage via vSphere. Kubernetes is “built deeply into the very core of both ESXi and vCenter,” as VMware puts it. The company also says that you can get Kubernetes up and running in vSphere in “less than a couple of hours.”
Why to Run Kubernetes on VMware
VMware is certainly not the only way to host Kubernetes. There are a variety of other Kubernetes distributions available – some (like AWS EKS and Azure AKS) that run as public cloud services, and some that are infrastructure-agnostic.
Compared to most other approaches, however, running Kubernetes with VMware offers a few compelling advantages for certain use cases.
Orchestrate Containers Alongside VMs
Probably the most notable advantage of VMware Kubernetes is that VMware is a platform that gives equal weight to both containers and traditional VMs. Using Cloud Foundation and vSphere, you can set up and manage conventional VMs alongside Kubernetes clusters.
It’s possible to orchestrate VMs in Kubernetes using other tools, like KubeVirt. But in that case, your VMs end up being part of your Kubernetes cluster rather than running alongside it. VMware makes it easy to run VMs and containers separately while still managing them through a central platform.
Integrated Infrastructure
With VMware Kubernetes, all of the infrastructure that you need to operate a Kubernetes cluster – compute, storage, and networking – is available through a single platform. What’s more, as we show below, VMware provides a simple and automated process for provisioning that infrastructure into workload domains that can host a cluster.
Automated Kubernetes Setup
As we show below, most aspects of installing Kubernetes’s components on VMware are automated. That’s true on many other Kubernetes platforms, of course, but it’s nonetheless worth noting that VMware makes the Kubernetes setup process pretty simple.
GUI-Based Management
With VMware, most aspects of Kubernetes setup and management can be handled via the vSphere GUI. That’s an advantage if you hate kubectl and don’t want to manage everything on the CLI. (That said, you can still certainly use kubectl with your VMware clusters if you wish.)
Cloud-Agnostic
VMware can run in virtually any type of environment – in a single public cloud, in a multicloud setup, in a hybrid cloud, in a private cloud, or simply on-premises. By extension, VMware Kubernetes can run almost anywhere, too.
That’s not true of all Kubernetes platforms. Some, as we’ve noted, run only in certain public clouds.
Air-Gapping
VMware Kubernetes supports air-gapping, which means you can disconnect your clusters entirely from the Internet. That’s useful for use cases that require a high degree of security and privacy.
Many other Kubernetes platforms require constant Internet connectivity, so they lack air-gapping support.
Drawbacks of VMware Kubernetes
Of course, VMware Kubernetes is not the best solution for every use case. Potential drawback to consider include:
- Ecosystem dependency: Most of the VMware Kubernetes tooling is developed by VMware, and there’s less flexibility in terms of which open source components you can plug into your cluster. If you don’t want to be tied into the VMware ecosystem, you may not like VMware Kubernetes.
- VSphere dependency: As we’ve noted, VMware Kubernetes runs on top of vSphere. You can’t run VMware Kubernetes on its own. That may be a disadvantage if you want a lightweight Kubernetes stack.
- Complex tooling: Compared to other Kubernetes vendors, VMware has a relatively complex set of Kubernetes-related tools. Instead of packaging everything into a single platform, VMware has spread its tooling across Cloud Foundation, vSphere, and Tanzu. That’s not a problem if you already know the VMware ecosystem well. But it may be hard to understand which tools do what if you’re not very familiar with VMware in general.
So, Who Should Use VMware Kubernetes?
While VMware Kubernetes is a viable choice for a wide variety of Kubernetes use cases, it makes most sense if any of the following is true:
- Your business already uses VMware extensively to run VMs, and your teams have deep expertise in working with VMware tooling.
- You want a Kubernetes solution that supports any type of on-premises or cloud-based environment or architecture.
- VMs and containers are equal citizens in your organization, and you want to be able to manage them all through a central platform.
How to Kubernetes on VMware, Step by Step
We said above that Kubernetes is baked into VMware’s current platforms. Nonetheless, it’s not turned on automatically. You’ll need to follow a few steps – which you can perform in VMWare Cloud Foundation – to deploy Kubernetes clusters on top of VMware.
Create a Workload Domain
A workload domain is a software-defined set of compute, storage, and networking resources. Size the domain according to the resource needs of your Kubernetes workload.
Deploy an NSX Edge Cluster
The edge cluster manages networking between your cluster and external resources. It handles load balancing and NAT as part of this process.
Enable Kubernetes
With a workload domain in place and an edge cluster configured, you can deploy Kubernetes by enabling workload management in Cloud Foundation.
This process provisions VMs to operate as Kubernetes nodes, using VMware Tanzu as the control plane. It also pushes a Kubernetes runtime to the cluster so you can execute containers.
The Kubernetes deployment process is mostly automated. You won’t need to install components on VMs manually; VMware handles the tedious work for you.
Managing Containers on VMware Kubernetes
With a cluster set up, you can start deploying and managing containers on Kubernetes in the vSphere Web client:
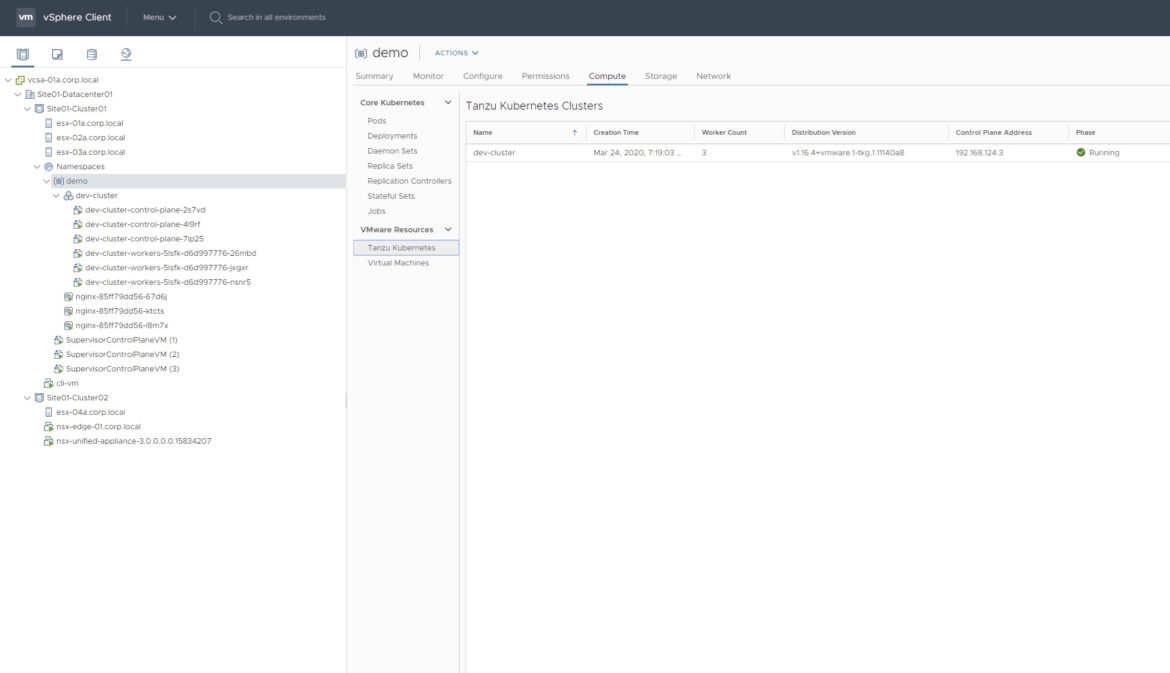
Source: https://blogs.vmware.com/vsphere/files/2020/03/4-Tanzu-Kubernetes-Cluster-View.png
As the screenshot shows, you can monitor the status of your clusters in vSphere. You can also configure and monitor Kubernetes resources like pods, DaemonSets, and ReplicaSets from the Web interface. Indeed, VMware provides an especially robust GUI for Kubernetes management.
If you prefer the command line, though, VMware has you covered, too. You can use kubectl to manage your Kubernetes environment on the command line just as you would in any type of Kubernetes environment.
Conclusion
Kubernetes is now a first-class citizen in the world of VMware. VMware’s Kubernetes tooling is not the simplest or the most lightweight; nonetheless, if you want to be able to manage both containers and virtual machines through a central platform – or if you want a totally infrastructure-agnostic way to deploy Kubernetes – Cloud Foundation, vSphere, and Tanzu are a great choice.

